2017-01-31 - "BLANK SLATE" CAMPAIGN SENDS CERBER RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-01-31-Cerber-ransomware-infections-3-pcaps.zip 887.9 kB (887,943 bytes)
- 2017-01-31-Blank-Slate-malspam-tracker.csv.zip 1.0 kB (974 bytes)
- 2017-01-31-Blank-Slate-emails-and-Cerber-ransomware.zip 1.4 MB (1,426,125 bytes)
NOTES:
- For background on this campaign, see the Palo Alto Networks Unit 42 Blog: "Blank Slate" Campaign Takes Advantage of Hosting Providers to Spread Ransomware.
EMAILS
EMAILS GATHERED:
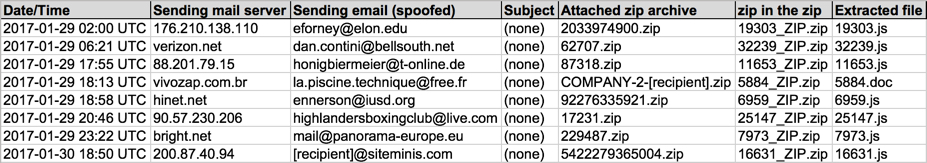
Shown above: Spreadsheet tracker, part 1 of 2.
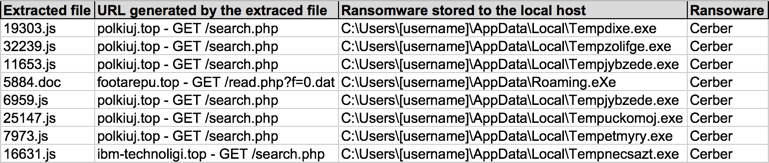
Shown above: Spreadsheet tracker, part 2 of 2.
(Read: Date/Time -- Sending mail server -- Sending address (spoofed) -- Attachment -- Extracted file)
- 2017-01-29 02:00 UTC -- 176.210.138[.]110 -- eforney@elon[.]edu -- 2033974900.zip -- 19303.js
- 2017-01-29 06:21 UTC -- verizon[.]net -- dan.contini@bellsouth[.]net -- 62707.zip -- 32239.js
- 2017-01-29 17:55 UTC -- 88.201.79[.]15 -- honigbiermeier@t-online[.]de -- 87318.zip -- 11653.js
- 2017-01-29 18:13 UTC -- vivozap[.]com[.]br -- la.piscine.technique@free[.]fr -- COMPANY-2-[recipient].zip -- 5884.doc
- 2017-01-29 18:58 UTC -- hinet[.]net -- ennerson@iusd[.]org -- 92276335921.zip -- 6959.js
- 2017-01-29 20:46 UTC -- 90.57.230[.]206 -- highlandersboxingclub@live[.]com -- 17231.zip -- 25147.js
- 2017-01-29 23:22 UTC -- bright[.]net -- mail@panorama-europe[.]eu -- 229487.zip -- 7973.js
- 2017-01-30 18:50 UTC -- 200.87.40[.]94 -- [recipient]@siteminis[.]com -- 5422279365004.zip -- 16631.js
ATTACHED ZIP ARCHIVES AND EXTRACTED FILES
SHA256 HASHES FOR THE EMAIL ATTACHMENTS:
- 423a6281a7fc407c8175c17387f4112b25fd0e1eae44b2dde989214078ec814a - 17231.zip (5,003 bytes)
- 20aae649e8e2505971736bc746126e2ef5380b8a1d1b5df389d0a6216fd975b8 - 2033974900.zip (4,120 bytes)
- 33a3c443b1ce4aa64fc850d0eb84b10b53d3d3e8dc6f33265d6cae8170ea143f - 229487.zip (5,780 bytes)
- 33b30ec07a2fd20cfde1b5515cef801546c6bceefc7d92473ccea1301f35185c - 5422279365004.zip (6,560 bytes)
- 863fa74055f9f410e897405196bce1749b91cf26d35f0158a8933edbcdf04433 - 62707.zip (2,791 bytes)
- 0d436f3a33b0f271461f2d43bc3dbb3126ee9b185f3583ec5a42de2d867c5c1a - 87318.zip (3,195 bytes)
- 66d063086c5312ed36c1a68e12d93d750fc53943b1517acc641f3ccf606f8a0f - 92276335921.zip (3,190 bytes)
- 836ef24ec9697cae96a9479374b93384323ea4b47baf487eb8ee370f24d67385 - COMPANY-2-[recipient].zip (60,852 bytes)
SHA256 HASHES FOR THE EXTRACTED WORD DOCUMENT AND .JS FILES:
- 3bf4ec3e1792207bef35434f481114a68e6f3fb0d1828171fa6c339e389df75c - 11653.js (10,747 bytes)
- 21048b243d1eb1e0e9c24b277db13a1b2b1e7e77ed4b5b254754ad02f8f9ea47 - 16631.js (21,552 bytes)
- 13f19590bd15df49677e859a6acd14aa409f4bf0a6cb34d036f5d1ad4d9d65b3 - 19303.js (14,560 bytes)
- 7f7237ee738349473ccf926b0d5338a4d015c58e9c18a81981923911e464e868 - 25147.js (16,127 bytes)
- 343f85fb8d91c723acdfd78f92310538b3492c0fd87283311f37aac626739c28 - 32239.js (7,839 bytes)
- bf87804e1f9e09d29f3515b52d11a1a69cda9ca2efb1cb814cd4cb91449eeeda - 5884.doc (146,944 bytes)
- 3bf4ec3e1792207bef35434f481114a68e6f3fb0d1828171fa6c339e389df75c - 6959.js (10,747 bytes)
- d846a22c7e09123eec77b10f4d1499b0e65f14056ecb09214d25624a90ac6b59 - 7973.js (25,627 bytes)
TRAFFIC
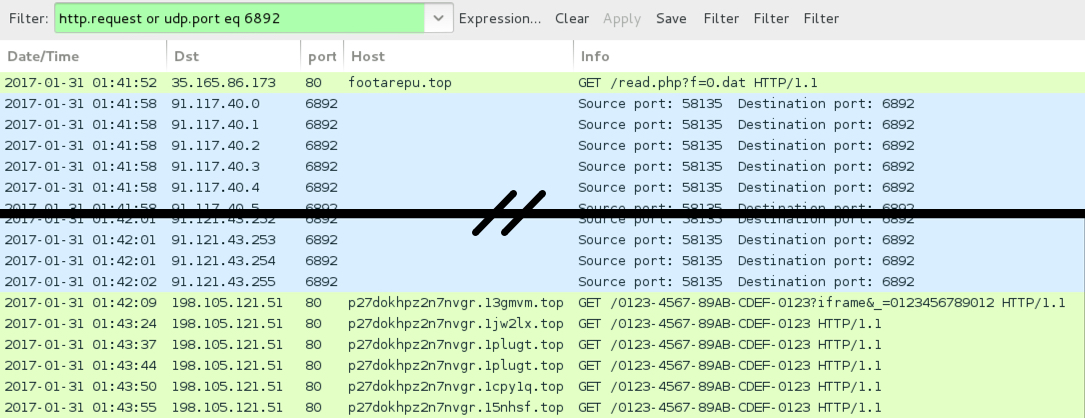
Shown above: Pcap of the infection traffic (1 of 3).
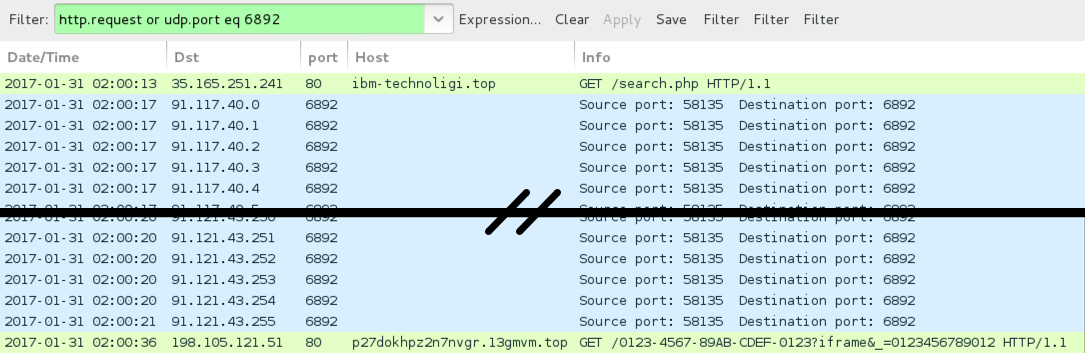
Shown above: Pcap of the infection traffic (2 of 3).
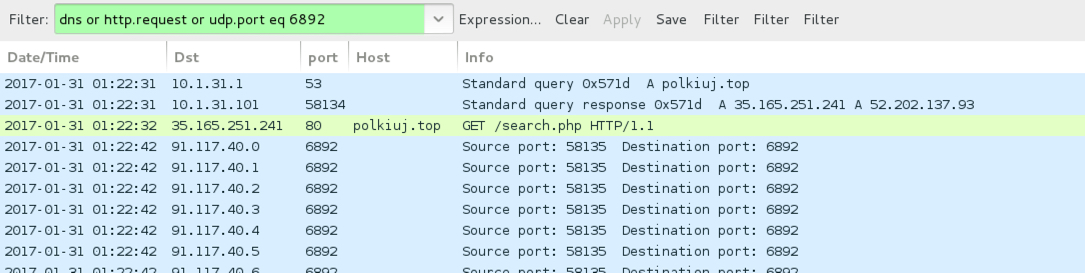
Shown above: Pcap of the infection traffic (3 of 3).
HTTP REQUESTS FOR CERBER RANSOMWARE:
- 35.165.86[.]173 port 80 - footarepu[.]top - GET /read.php?f=0.dat
- 35.165.251[.]241 port 80 - ibm-technoligi[.]top - GET /search.php
- 35.165.251[.]241 port 80 - polkiuj[.]top - GET /search.php
CERBER RANSOMWARE POST-INFECTION TRAFFIC:
- 91.117.40[.]0 to 91.117.40[.]31 (91.117.40[.]0/27) UDP port 6892 - Cerber ransomware post-infection UDP traffic
- 91.119.40[.]0 to 91.119.40[.]31 (91.119.40[.]0/27) UDP port 6892 - Cerber ransomware post-infection UDP traffic
- 91.121.40[.]0 to 91.121.43[.]255 (91.239.24[.]0/22) UDP port 6892 - Cerber ransomware post-infection UDP traffic
- 198.105.121[.]51 port 80 - p27dokhpz2n7nvgr.13gmvm[.]top - HTTP post-infection traffic from Cerber decryption link
- 198.105.121[.]51 port 80 - p27dokhpz2n7nvgr.1jw2lx[.]top - HTTP post-infection traffic from Cerber decryption link
- 198.105.121[.]51 port 80 - p27dokhpz2n7nvgr.1plugt[.]top - HTTP post-infection traffic from Cerber decryption link
- 198.105.121[.]51 port 80 - p27dokhpz2n7nvgr.1plugt[.]top - HTTP post-infection traffic from Cerber decryption link
- 198.105.121[.]51 port 80 - p27dokhpz2n7nvgr.1cpy1q[.]top - HTTP post-infection traffic from Cerber decryption link
- 198.105.121[.]51 port 80 - p27dokhpz2n7nvgr.15nhsf[.]top - HTTP post-infection traffic from Cerber decryption link
MALWARE
CERBER RANSOMWARE SAMPLES:
- 52f203c7051ad72b7ec55c5c35bd1efb1a6ff327a0d3bb675196abc6538f276b - Roaming.eXe (665,321 bytes)
- 7e99f3b1ed0427e2a3b004b427b8fee3a8d648cb990ba98ca88bb6c605174115 - Tempnecsazt.exe (422,272 bytes)
- 9cc8007854e0d7d40bab3e19ceece3e82444ccaa409fafea16d797bb3f9b2b56 - Tempzolifge.exe (422,272 bytes)
IMAGES
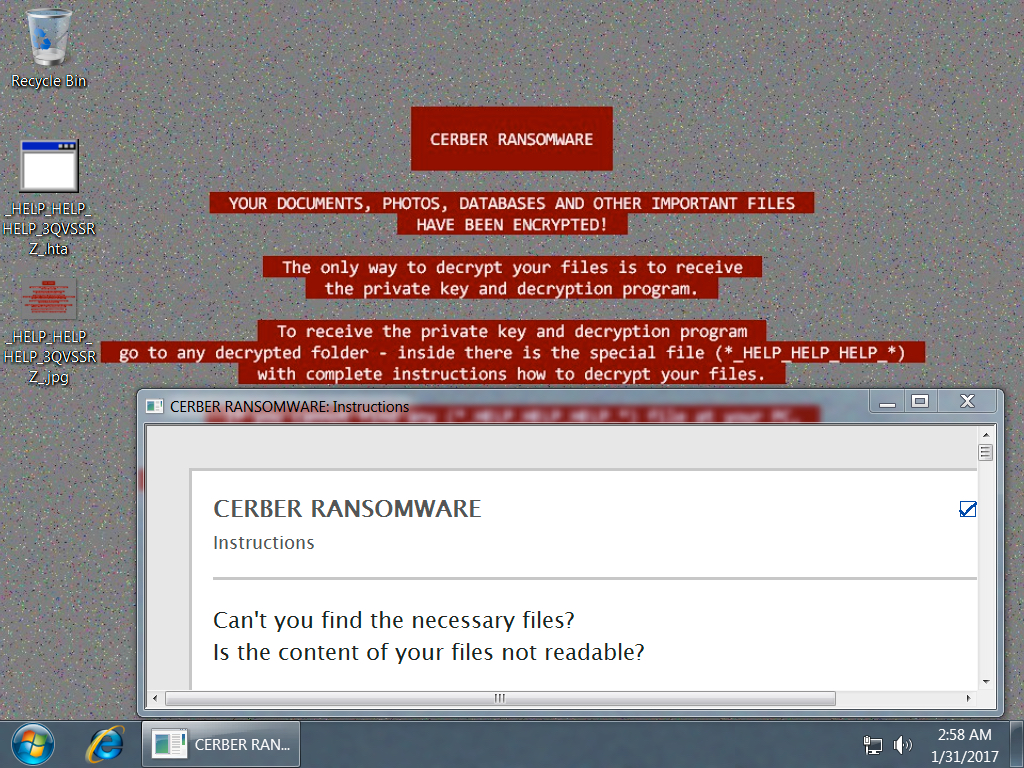
Shown above: Screenshot of an infected Windows host after rebooting.
Click here to return to the main page.
