2017-04-04 - HANCITOR INFECTION WITH ZLOADER
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-04-04-Hancitor-infection-with-ZLoader.pcap.zip 14.1 MB (14,103,472 bytes)
- 22017-04-04-Hancitor-infection-with-ZLoader.pcap (15,048,404 bytes)
- 2017-04-04-Hancitor-malspam-3-examples.zip 32.9 kB (3,293 bytes)
- 2017-04-04-Hancitor-malspam-1534-UTC.eml (1,471 bytes)
- 2017-04-04-Hancitor-malspam-1536-UTC.eml (1,471 bytes)
- 2017-04-04-Hancitor-malspam-1646-UTC.eml (1,472 bytes)
- 2017-04-04-malware-from-Hancitor-infection.zip 307.0 kB (307,038 bytes)
- 41592.exe (121,344 bytes)
- ADP_invoice_alexander.dixon.doc (221,696 bytes)
- BN40D7.tmp (170,496 bytes)
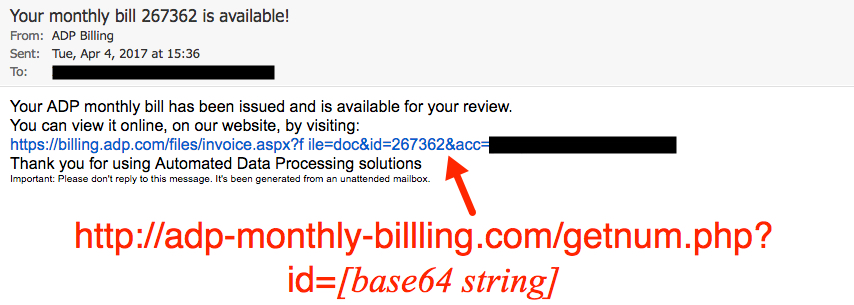
Shown above: Screen shot from one of the emails.
EMAIL HEADERS:
- Date/Time: Tuesday 2017-04-04 as early as 15:34 UTC
- From: (spoofed) "ADP Billing" <bill@adpm[.]com>
- Subject: Your monthly bill 267362 is available!
- Subject: Your monthly bill 362886 is available!
- Subject: Your monthly bill 201834 is available!
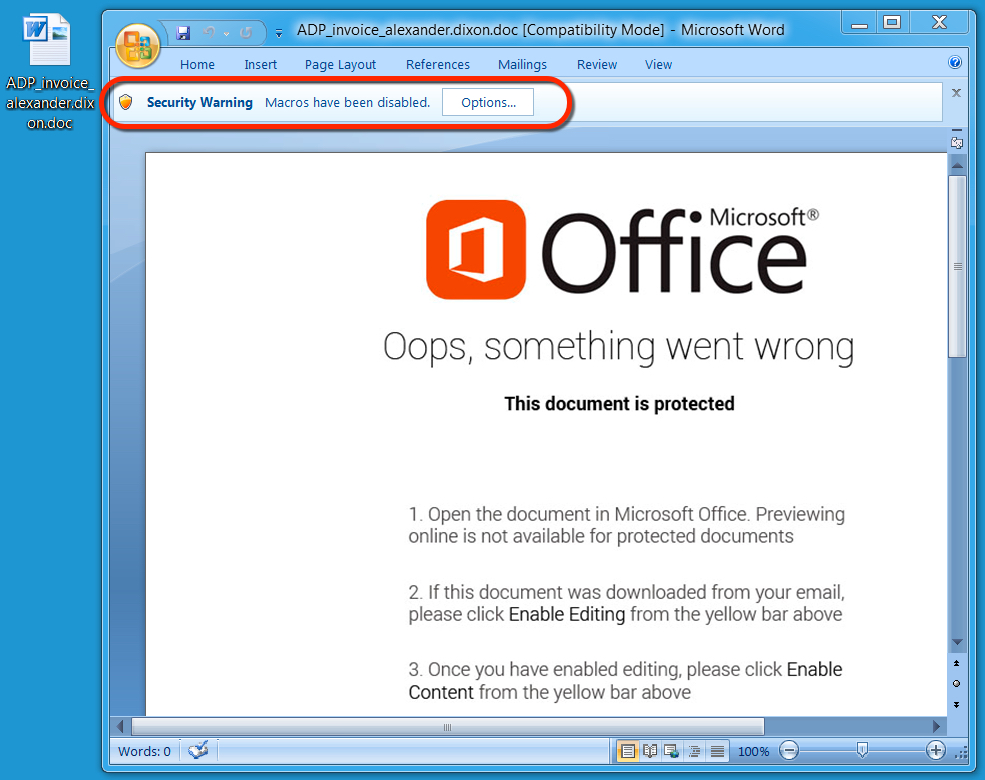
Shown above: Malicious Word document from link in the malspam.
TRAFFIC
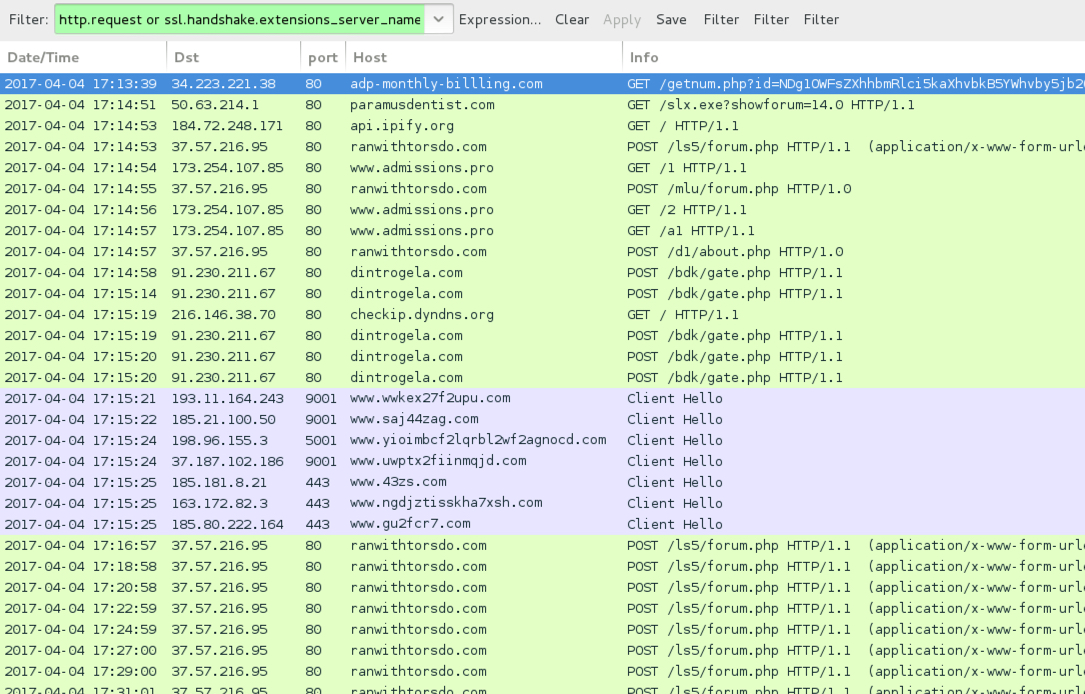
Shown above: Traffic from the infection filtered in Wireshark.
HTTP REQUEST FOR THE INITIAL DOCUMENT:
- 34.223.221[.]38 port 80 - adp-monthly-billling[.]com - GET /getnum.php?id=[base64 string]
POST-INFECTION TRAFFIC:
- 50.63.214[.]1 port 80 - paramusdentist[.]com - GET /slx.exe?showforum=14.0
- 173.254.107[.]85 port 80 - www.admissions[.]pro - GET /1
- 173.254.107[.]85 port 80 - www.admissions[.]pro - GET /2
- 173.254.107[.]85 port 80 - www.admissions[.]pro - GET /a1
- 37.57.216[.]95 port 80 - ranwithtorsdo[.]com - POST /ls5/forum.php
- 37.57.216[.]95 port 80 - ranwithtorsdo[.]com - POST /mlu/forum.php
- 37.57.216[.]95 port 80 - ranwithtorsdo[.]com - POST /d1/about.php
- 91.230.211[.]67 port 80 - dintrogela[.]com - POST /bdk/gate.php
- api.ipify[.]org - GET /
- checkip.dyndns[.]org - GET /
FILE HASHES
WORD DOCUMENT FROM LINK IN THE EMAIL:
- SHA256 hash: a2753d6705682999b37953492918635da5b92cad577a93efb80fe7a6008f10f5
File location: ADP_invoice_alexander.dixon.doc
File description: Hancitor maldoc
MALWARE FROM THE INFECTED HOST:
- SHA256 hash: 12c4432c58c692d4f39f35fa7a5c638e922e1fe63ea24636d9ee43f90d5d8af7
File location: C:\Users\[username]\AppData\Local\Temp\41592.exe
File description: Hancitor binary
- SHA256 hash: 0a6b1ac5472a554e6d72bee875b7b7cdf85c9c1c8765b4f395c8847f47cc5043
File location: C:\Users\[username]\AppData\Local\Temp\BN40D7.tmp
File description: DELoader/ZLoader
IMAGES
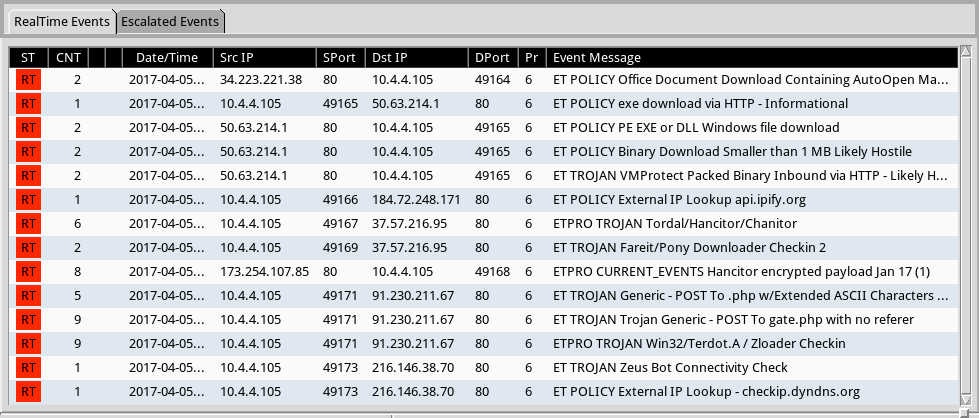
Shown above: Some alerts on the traffic from the Emerging Threats Pro (ETPRO) ruleset using Sguil on Security Onion.
Click here to return to the main page.
