2017-06-02 - SEAMLESS CAMPAIGN CONTINUES USING RIG EK TO SEND RAMNIT
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- Z2017-06-02-Seamless-Rig-EK-sends-Ramnit-2-pcaps.zip 2.0 MB (2,028,664 bytes)
- 2017-06-02-Seamless-Rig-EK-sends-Ramnit-1st-run.pcap (1,309,272 bytes)
- 2017-06-02-Seamless-Rig-EK-sends-Ramnit-2nd-run.pcap (1,070,828 bytes)
- 2017-06-02-Seamless-Rig-EK-sends-Ramnit-malware-and-artifacts.zip 258.0 kB (257,987 bytes)
- 2017-06-02-Rig-EK-landing-page-1st-run.txt (26,904 bytes)
- 2017-06-02-Rig-EK-landing-page-2nd-run.txt (26,901 bytes)
- 2017-06-02-Seamless-Rig-EK-payload-Ramnit-1st-run.exe (162,816 bytes)
- 2017-06-02-Seamless-Rig-EK-payload-Ramnit-2nd-run.exe (162,816 bytes)
NOTES:
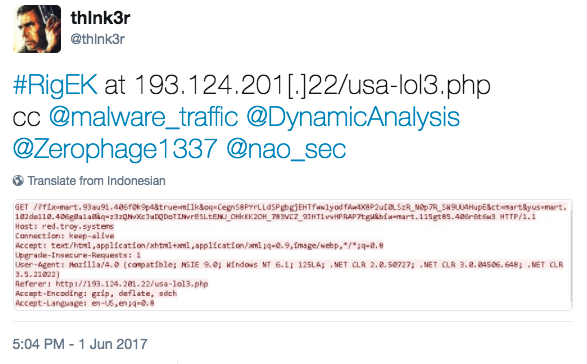
- Thanks to @thlnk3r tweeting about a referer for Rig EK from the Seamless campaign.
- As @nao_sec reported earlier today, it appears Rig EK is no longer using Flash exploits starting sometime on 2017-06-01 (link to tweet).
ADDITIONAL INFO:
- 2017-05-11 - ISC Diary - Seamless Campaign using Rig Exploit Kit to send Ramnit Trojan
Shown above: Tweet from @thlnk3r yesterday with a Seamless campaign URL.
TRAFFIC
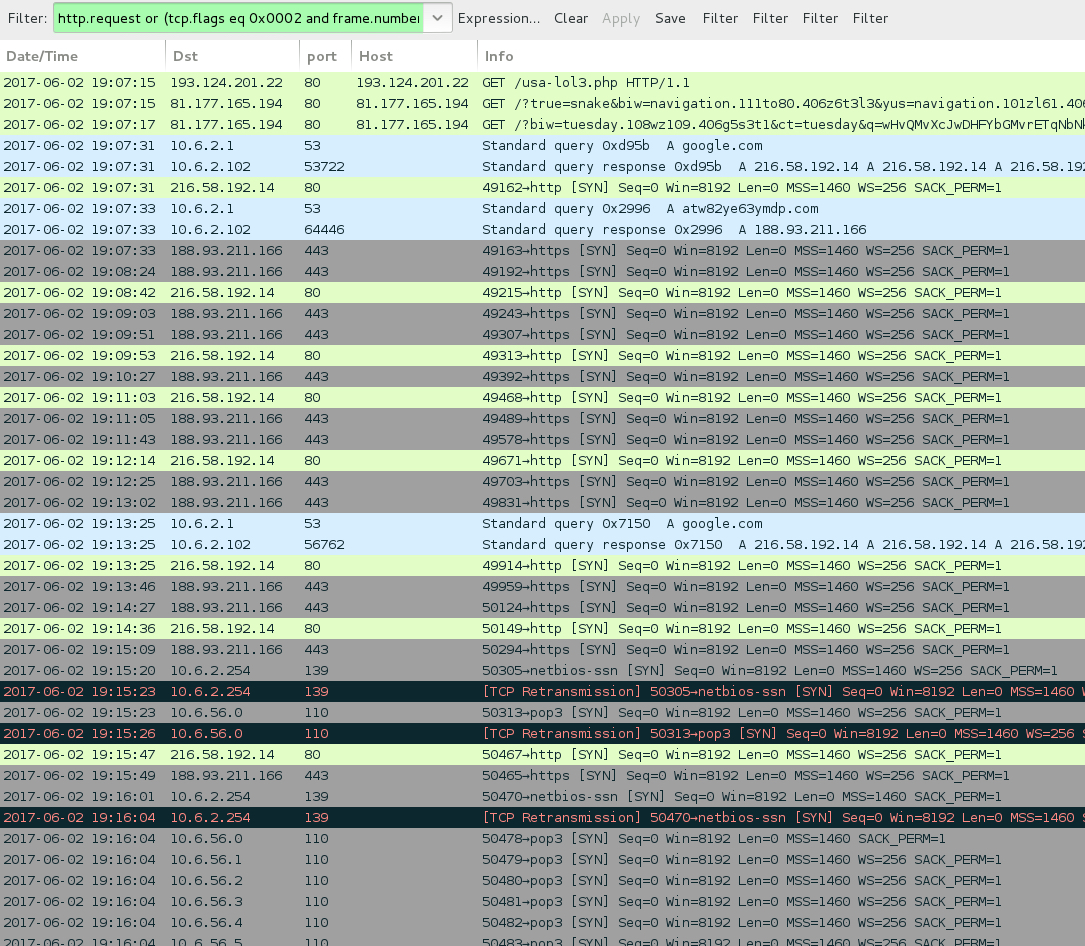
Shown above: Traffic from the 1st run filtered in Wireshark.
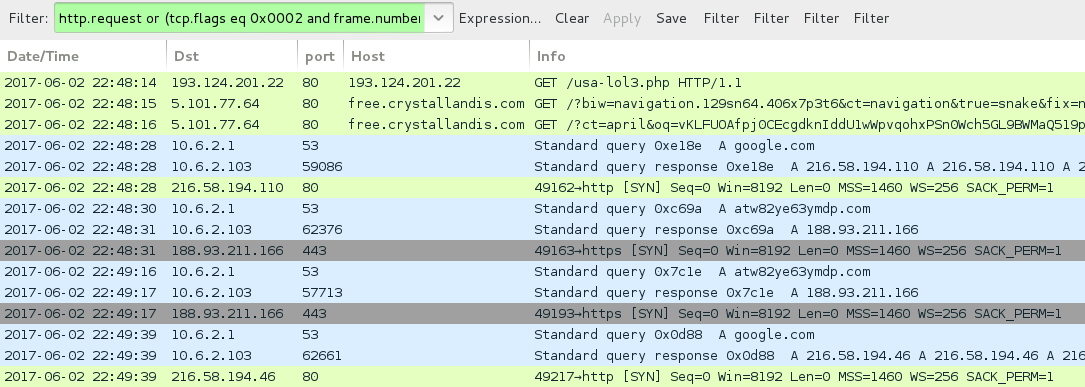
Shown above: Traffic from the 2nd run filtered in Wireshark.
ASSOCIATED DOMAINS:
- 81.177.165[.]194 port 80 - 81.177.165[.]194 - Rig EK (1st run)
- 5.101.77[.]64 port 80 - free.crystallandis[.]com - Rig EK (2nd run)
- 188.93.211[.]166 port 443 - atw82ye63ymdp[.]com - HTTPS/SSL/TLS traffic caused by Ramnit
- Attempted connectivity checks to google[.]com
- Scans to other IP addresses internally (10.6.0[.]0/16) targeting TCP ports 110 (POP3) and 139 (NBNS)
FILE HASHES
MALWARE PAYLOAD (RAMNIT) - 1ST RUN:
- SHA256 hash: 1cec6181f1959c0f74b97ccefc9506b9447061d970dabc5c7e0688e9547b71a2
- File size: 162,816 bytes
- File location: C:\Users\[username]\AppData\Local\Temp\[random numbers and letters].exe
MALWARE PAYLOAD (RAMNIT) - 2ND RUN:
- SHA256 hash: c9907e55f0d5592ff335d35708baeb186e11300df90aa3aef1a142344ecc493f
- File size: 162,816 bytes
- File location: C:\Users\[username]\AppData\Local\Temp\[random numbers and letters].exe
OTHER IMAGES
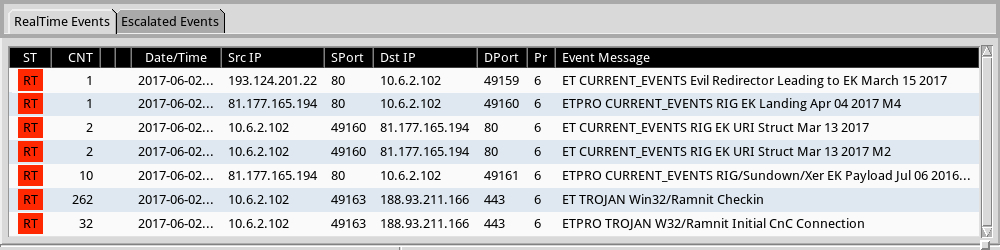
Shown above: Some alerts on the traffic from the Emerging Threats and ETPRO rulesets using Sguil and tcpreplay on Security Onion.
Click here to return to the main page.