2017-06-26 - HANCITOR INFECTION WITH ZLOADER
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-06-26-Hancitor-infection-with-ZLoader.pcap.zip 9.0 MB (9,043,926 bytes)
- 2017-06-26-Hancitor-infection-with-ZLoader.pcap (9,721,184 bytes)
- 2017-06-26-Hancitor-malspam-10-examples.zip 11.4 kB (11,447 bytes)
- 2017-06-26-Hancitor-malspam-1548-UTC.eml (1,924 bytes)
- 2017-06-26-Hancitor-malspam-1552-UTC.eml (1,925 bytes)
- 2017-06-26-Hancitor-malspam-1556-UTC.eml (1,931 bytes)
- 2017-06-26-Hancitor-malspam-1557-UTC.eml (1,922 bytes)
- 2017-06-26-Hancitor-malspam-1613-UTC.eml (1,924 bytes)
- 2017-06-26-Hancitor-malspam-1626-UTC.eml (1,930 bytes)
- 2017-06-26-Hancitor-malspam-1754-UTC.eml (1,924 bytes)
- 2017-06-26-Hancitor-malspam-1828-UTC.eml (1,927 bytes)
- 2017-06-26-Hancitor-malspam-1927-UTC.eml (1,927 bytes)
- 2017-06-26-Hancitor-malspam-1938-UTC.eml (1,933 bytes)
- 2017-06-26-malware-from-Hancitor-infection.zip 252.4 kB (252,387 bytes)
- BN5466.tmp (186,368 bytes)
- Invoice_yahoo.doc (221,696 bytes)
A BLOG POST AND SOME TWEETS COVERING THE 2017-06-26 WAVE OF #HANCITOR MALSPAM:
- @cheapbyte: #hancitor #malspam #phishing Hancitor Phishing links June 26, 2017 URLs in text on ghostbin.com (link)
- @James_inthe_box: This has all the same players as the "usual" #hancitor run: #zloader #pony and that weird #evilpony (link)
EMAILS
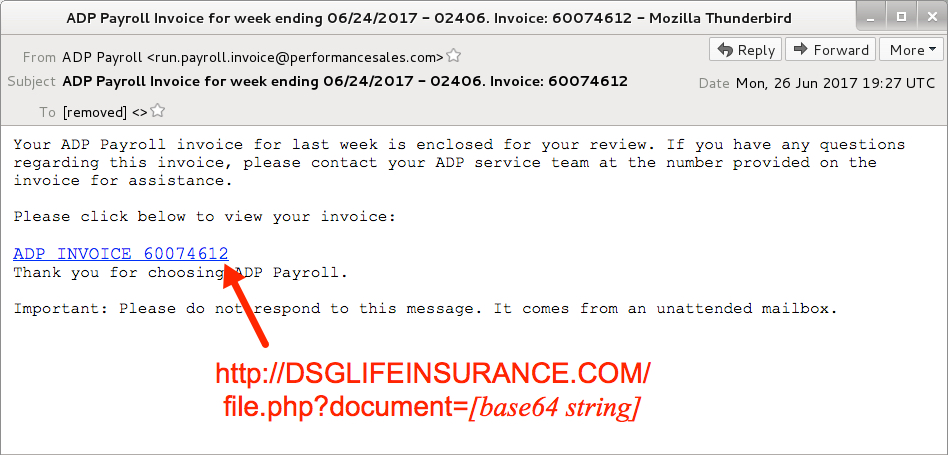
Shown above: Screenshot from one of the emails.
EMAIL HEADERS:
- Date: Monday 2017-06-26 as early as 15:48 UTC through at least 19:38 UTC
- From: "ADP Payroll" <run.payroll.invoice@performancesales[.]com>
- Subject: ADP Payroll Invoice for week ending 06/24/2017 - 02406. Invoice: 01068880
- Subject: ADP Payroll Invoice for week ending 06/24/2017 - 02406. Invoice: 05866353
- Subject: ADP Payroll Invoice for week ending 06/24/2017 - 02406. Invoice: 13104356
- Subject: ADP Payroll Invoice for week ending 06/24/2017 - 02406. Invoice: 43710578
- Subject: ADP Payroll Invoice for week ending 06/24/2017 - 02406. Invoice: 46575423
- Subject: ADP Payroll Invoice for week ending 06/24/2017 - 02406. Invoice: 55157316
- Subject: ADP Payroll Invoice for week ending 06/24/2017 - 02406. Invoice: 58861681
- Subject: ADP Payroll Invoice for week ending 06/24/2017 - 02406. Invoice: 60074612
- Subject: ADP Payroll Invoice for week ending 06/24/2017 - 02406. Invoice: 60511545
- Subject: ADP Payroll Invoice for week ending 06/24/2017 - 02406. Invoice: 88040420
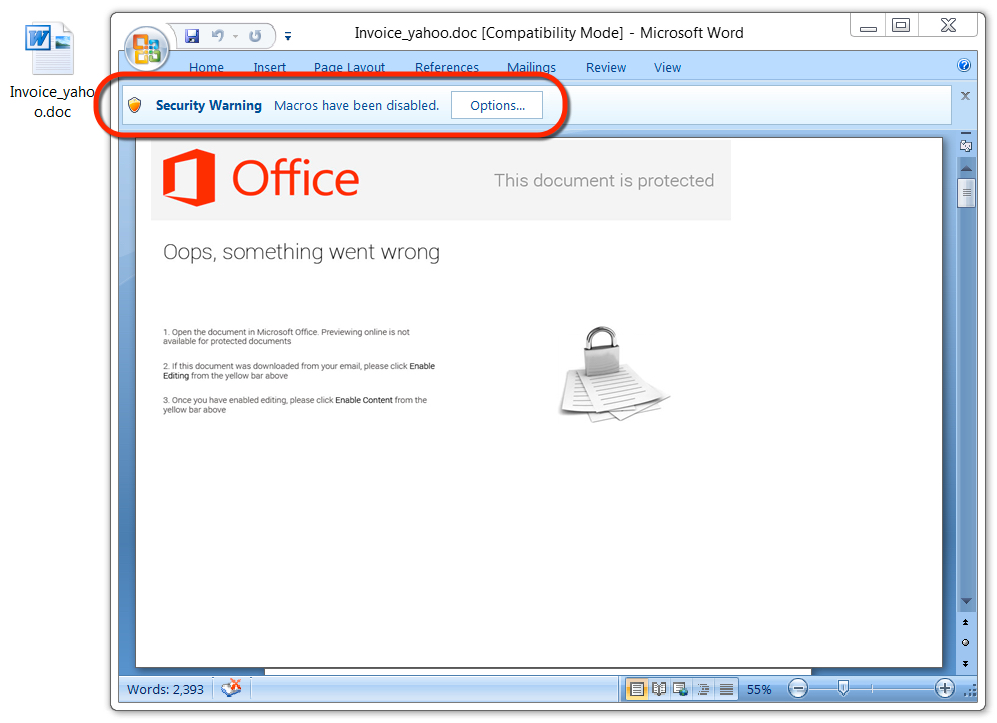
Shown above: Malicious Word document from link in the malspam.
TRAFFIC
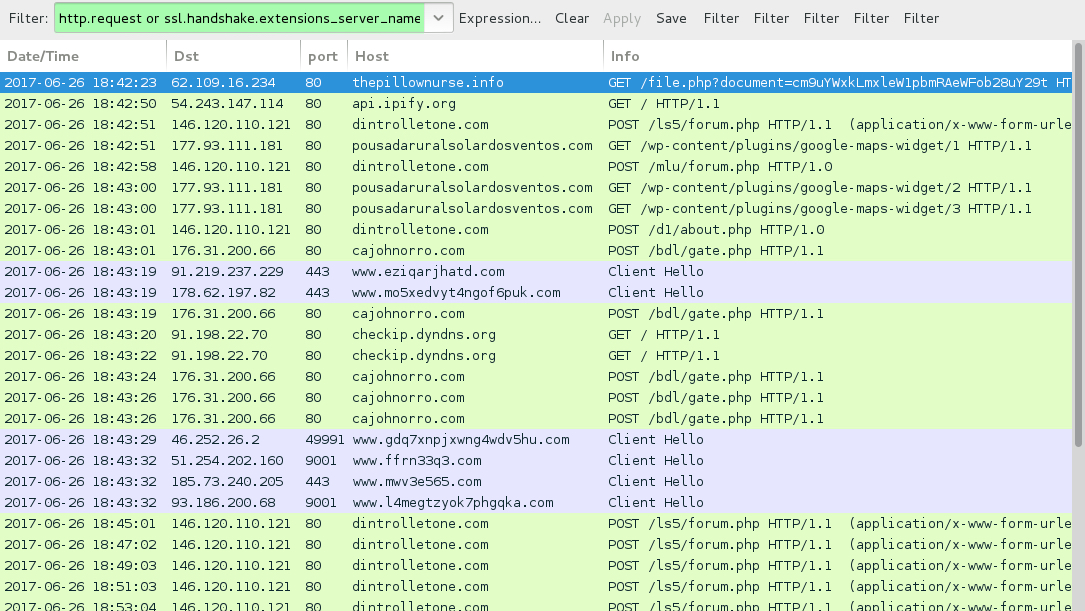
Shown above: Traffic from the infection filtered in Wireshark.
HTTP REQUESTS FOR THE WORD DOCUMENT:
- DSGLIFEINSURANCE[.]COM - GET /viewdoc/file.php?document=[base64 string]
- DSGWELLNESS365[.]COM - GET /viewdoc/file.php?document=[base64 string]
- ENROLLNOWONLINE[.]COM - GET /viewdoc/file.php?document=[base64 string]
- FORTWORTHHEALTHEXCHANGE[.]COM - GET /viewdoc/file.php?document=[base64 string]
- thepillownurse[.]info - GET /viewdoc/file.php?document=[base64 string]
NAME FOR THE MALICIOUS WORD DOCUMENTS:
- Invoice_[recipient's email domain, minus the suffix].doc
POST-INFECTION TRAFFIC FROM MY ONE INFECTED HOST:
- 146.120.110[.]121 port 80 - dintrolletone[.]com - POST /ls5/forum.php
- 146.120.110[.]121 port 80 - dintrolletone[.]com - POST /mlu/forum.php
- 146.120.110[.]121 port 80 - dintrolletone[.]com - POST /d1/about.php
- 177.93.111[.]181 port 80 - pousadaruralsolardosventos[.]com - GET /wp-content/plugins/google-maps-widget/1
- 177.93.111[.]181 port 80 - pousadaruralsolardosventos[.]com - GET /wp-content/plugins/google-maps-widget/2
- 177.93.111[.]181 port 80 - pousadaruralsolardosventos[.]com - GET /wp-content/plugins/google-maps-widget/3
- 176.31.200[.]66 port 80 - cajohnorro[.]com - POST /bdl/gate.php
- api.ipify[.]org - GET /
- checkip.dyndns[.]org - GET /
- Various IP addresses on various TCP ports - Tor traffic
FILE HASHES
WORD DOCUMENT FROM LINK IN THE EMAIL:
- SHA256 hash: f9efadc1f2ff65179f005704fafaf63b7d8f6d9bb6be3e08329126634df2d333
File name: Invoice_yahoo.doc
File size: 221,696 bytes
File description: Hancitor maldoc
MALWARE RETRIEVED FROM THE INFECTED HOST:
- SHA256 hash: 99ca5f7573cfb2f0c6bbc8b544ef67900a371de4ceed532569e0c4ae10a56859
File location: C:\Users\[username]\AppData\Local\Temp\BN5466.tmp
File size: 186,368 bytes
File description: DELoader/ZLoader
Click here to return to the main page.
