2017-08-11 - "DIABLO6" VARIANT LOCKY RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-08-11-Locky-ransomware-email-tracker.csv.zip 1.1 kB (1,072 bytes)
NOTES:
- More malicious spam (malspam) pushing the "Diablo6" variant of Locky ransomware on Friday 2017-08-11.
- Unfortunately, I messed up the pcap and malware archives, so they aren't included for today's blog.
EMAILS
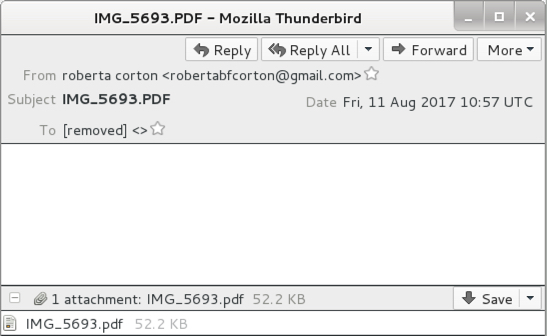
Shown above: An example of the emails.
10 EXAMPLES:
READ: DATE/TIME -- SENDING ADDRESS (SPOOFED) -- SUBJECT -- ATTACHMENT NAME (PDF) -- EMBEDDED .DOCM FILE
- 2017-08-11 10:47:58 UTC -- neva pavey <nevadJpavey@gmail[.]com> -- IMG_7128.PDF -- img_7128.pdf -- 20170811534.docm
- 2017-08-11 10:57:11 UTC -- roberta corton <robertabfcorton@gmail[.]com> -- IMG_5693.PDF -- img_5693.pdf -- 20170811912.docm
- 2017-08-11 11:12:04 UTC -- liza adair <lizasXzadair@gmail[.]com> -- IMG_2036.PDF -- img_2036.pdf -- 20170811855.docm
- 2017-08-11 11:12:41 UTC -- elba collis <elbabrcollis@gmail[.]com> -- IMG_3454.PDF -- img_3454.pdf -- 20170811668.docm
- 2017-08-11 11:16:18 UTC -- darla oldenburg <darlakGuoldenburg@gmail[.]com> -- IMG_9516.PDF -- img_9516.pdf -- 20170811213.docm
- 2017-08-11 11:16:20 UTC -- susanna rain <susannaeFrain@gmail[.]com> -- IMG_2401.PDF -- img_2401.pdf -- 20170811889.docm
- 2017-08-11 11:16:30 UTC -- zelma lockey <zelmaQWllockey@gmail[.]com> -- IMG_1714.PDF -- img_1714.pdf -- 20170811759.docm
- 2017-08-11 11:16:35 UTC -- elsie farragher <elsieEBJfarragher@gmail[.]com> -- IMG_9641.PDF -- img_9641.pdf -- 20170811955.docm
- 2017-08-11 11:16:36 UTC -- valarie paston <valarieXrpaston@gmail[.]com> -- IMG_8929.PDF -- img_8929.pdf -- 20170811891.docm
- 2017-08-11 11:29:53 UTC -- catherine wigmore <catherineTjLwigmore@gmail[.]com> -- IMG_5241.PDF -- img_5241.pdf -- 20170811227.docm
MALWARE
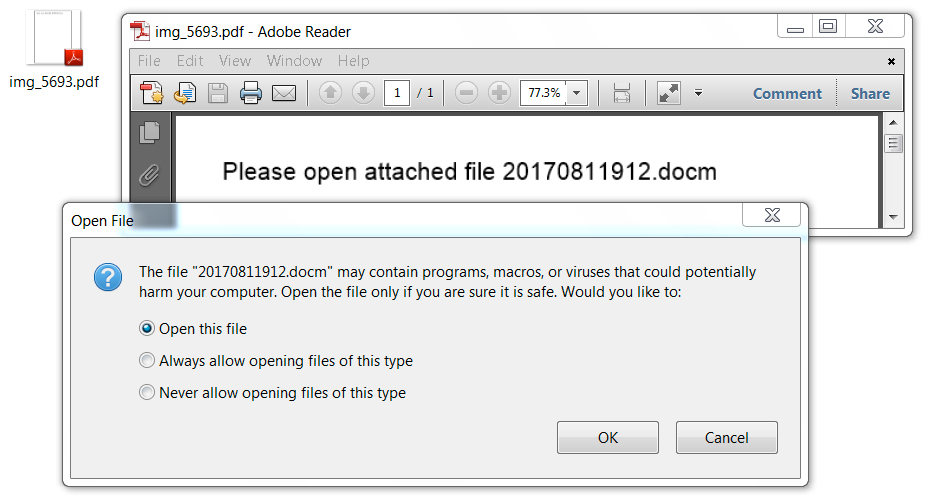
Shown above: An example of the PDF files attached to the malspam.
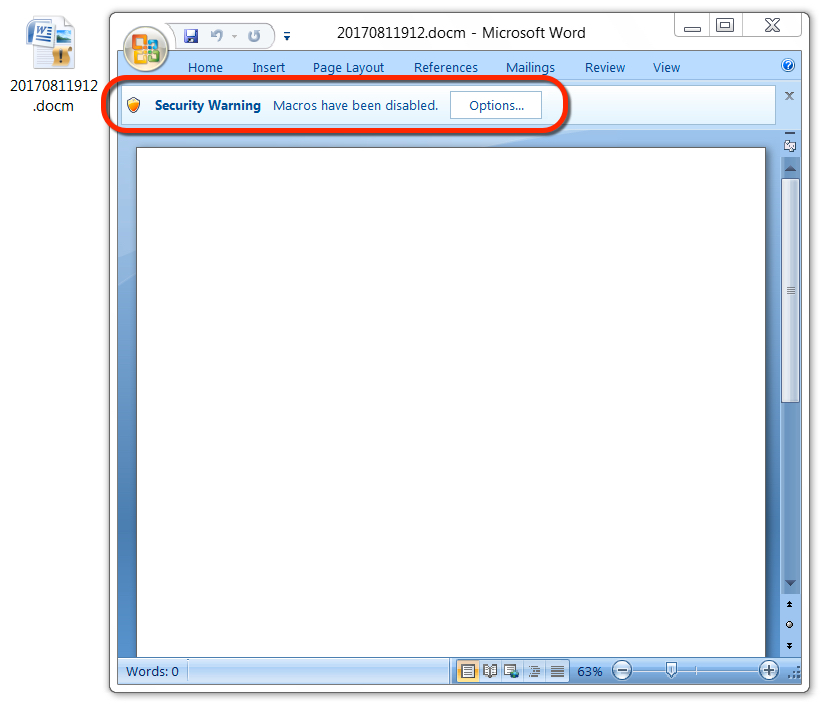
Shown above: An example of the embedded Word documents seen when opening the PDF files.
SHA256 HASHES FOR THE PDF ATTACHMENTS:
- 13c41fb93905eaea0f5958232f0646e951561c6cfab0943a73ca903b4a01503d - img_1714.pdf
- aa5ceec06696f1afe7096574bb978ab3f5a42d3a91f0ea82fe862e336454b10a - img_2036.pdf
- 97bbff94ef2ca6e433cc423523874eeb107b32ee91466e31659597d624397aba - img_2401.pdf
- 49ddb31b8115f45eb2d97f83b92e6b0008bf935e8e77bb116a6a1d79e5b7f204 - img_3454.pdf
- 8ff0d8996b3f90c3fe1509cc0175b3f8874ae272ca513be7f06643c54dd0fd52 - img_5241.pdf
- 8c356604d0a5b2b6f2b2726f3f2ea6ad8cf8e98595aac6876738199d2abf42d3 - img_5693.pdf
- ff876fc257b2c76172a1072872f389ecbd5f6e70742e068f122baf370952067a - img_7128.pdf
- 17d300e30546dfaa9171865181777b249035276bd9beb92126f7680dfadc3127 - img_8929.pdf
- 00f64482e9cfec2c7898d752e9864395073fc0467ff40e3b5ab1841a28d6979d - img_9516.pdf
- abacf1678440ab6a473629251716bf6e039d82a9e97c2d73e58f85f794613d9b - img_9641.pdf
SHA256 HASHES FOR THE EXTRACTED .DOCM FILES:
- 2e6d20c75e863b05b190eacb941b52345c97617021cba0c245e1f765329cf713 - 20170811213.docm
- eb0ed0a90913760203ec2e25cc19bfc35a61775a24359587d0dcdc57976523a7 - 20170811227.docm
- 3614b7b2d53140c5ffb8ba91e3dffa150aaba9a99b8829bbc07c024659094157 - 20170811534.docm
- 6862c65bb003e7b4843190df44c9d0dcfef53cd6b9aa0b66fba91f867bda7c0f - 20170811668.docm
- 0d7a5b55214e9875750f99123bab672a609bfaaaf566f938e13bcfd137e0103c - 20170811759.docm
- e3c0674e8f6373bf2ee844afd74082af0cb5a38de8aebc82aea0a797751120d4 - 20170811855.docm
- 2e8831cf3eca71865a58c2865fecc6bece87f541fcf944fc796ce1aa6aa70e8c - 20170811889.docm
- f5378e724624f99a954cacbe8271097929bc9893d3482438ec31c00e7f27c1e0 - 20170811891.docm
- 1fc0a74fb513152d020c061a4f0a9c7a8fa3c929f7d733059c99eed5eef33a65 - 20170811912.docm
- 686a55e7f8f6c53fe520e9172ee298f2d4bf7c50cdfe0d39d4ab746754eabf7f - 20170811955.docm
MALWARE RETRIEVED FROM INFECTED HOST:
- SHA256 hash: 5606e9dc4ab113749953687adac6ddb7b19c864f6431bdcf0c5b0e2a98cca39e
File size: 620,544 bytes
File location: C:\Users\[username]\AppData\Local\Temp\agraba8.exe
File description: Locky ransomware (Diablo6 variant)
TRAFFIC
URLS FROM THE WORD MACROS FILES TO DOWNLOAD LOCKY RANSOMWARE:
- 3e[.]com[.]pt - GET /JbhbUsfs
- 6tricksguides[.]com - GET /JbhbUsfs
- accuflowfloors[.]com - GET /JbhbUsfs
- acurcioefilhos[.]pt - GET /JbhbUsfs
- grossert[.]de - GET /JbhbUsfs
- love.chuanmeiker[.]com - GET /JbhbUsfs
- nancywillems[.]nl - GET /JbhbUsfs
- nerdydroid[.]com - GET /JbhbUsfs
- rtozottosdossder[.]net - GET /af/JbhbUsfs
- seoulhome[.]net - GET /JbhbUsfs
- starsafety[.]net - GET /JbhbUsfs
LOCKY POST-INFECTION TRAFFIC:
- 91.219.28[.]39 port 80 - 91.219.28[.]39 - GET /checkupdate [Locky ransomware callback]
- 188.127.239[.]17 port 80 - TCP connection attempts, but no reply from the server [Locky ransowmare callback noted in my lab environment]
- g46mbrrzpfszonuk[.]onion - Tor domain for Locky decryptor
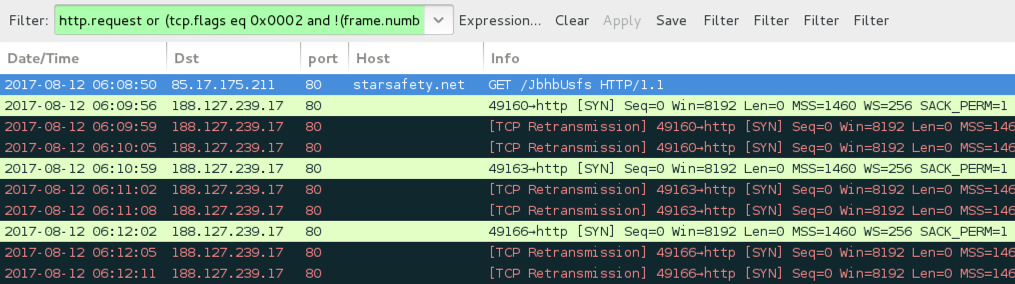
Shown above: Traffic from the infection filtered in Wireshark.
IMAGES
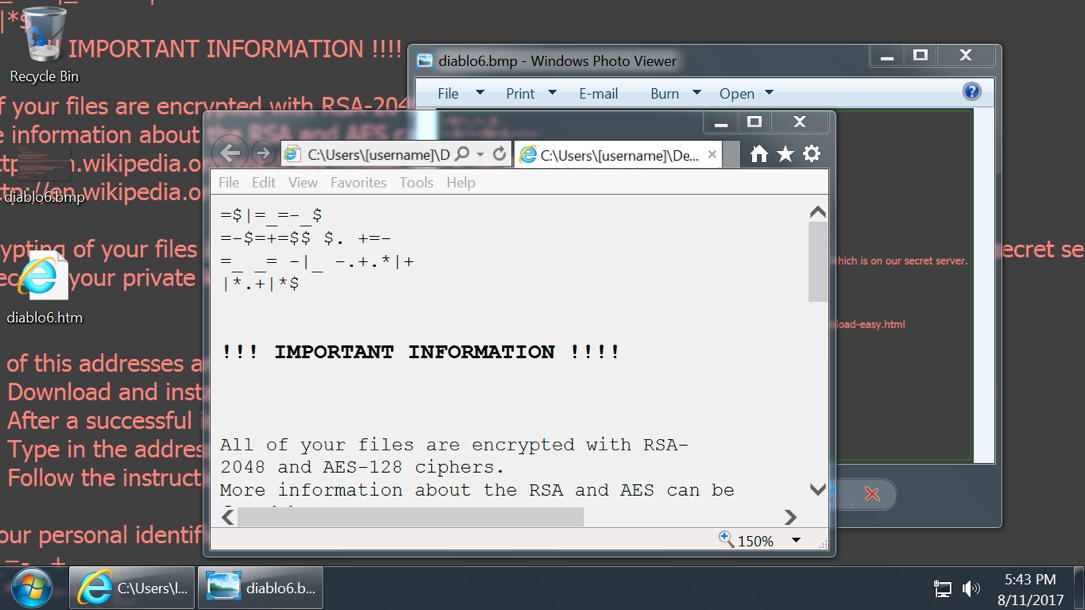
Shown above: Desktop of an infected Windows host.
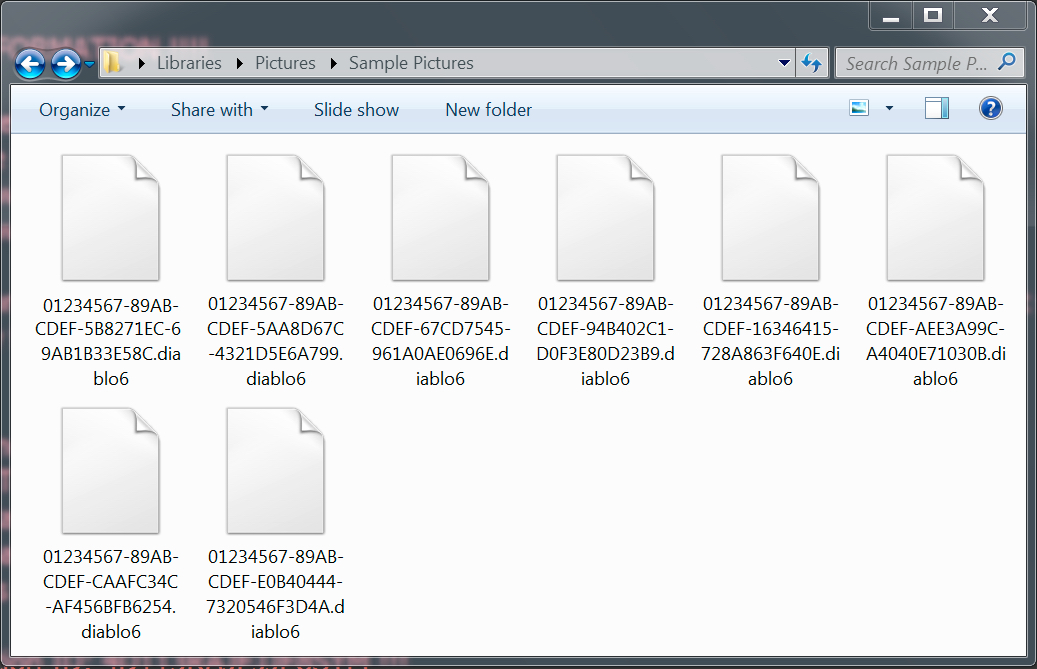
Shown above: Encrypted files have .diablo6 as the file extension.
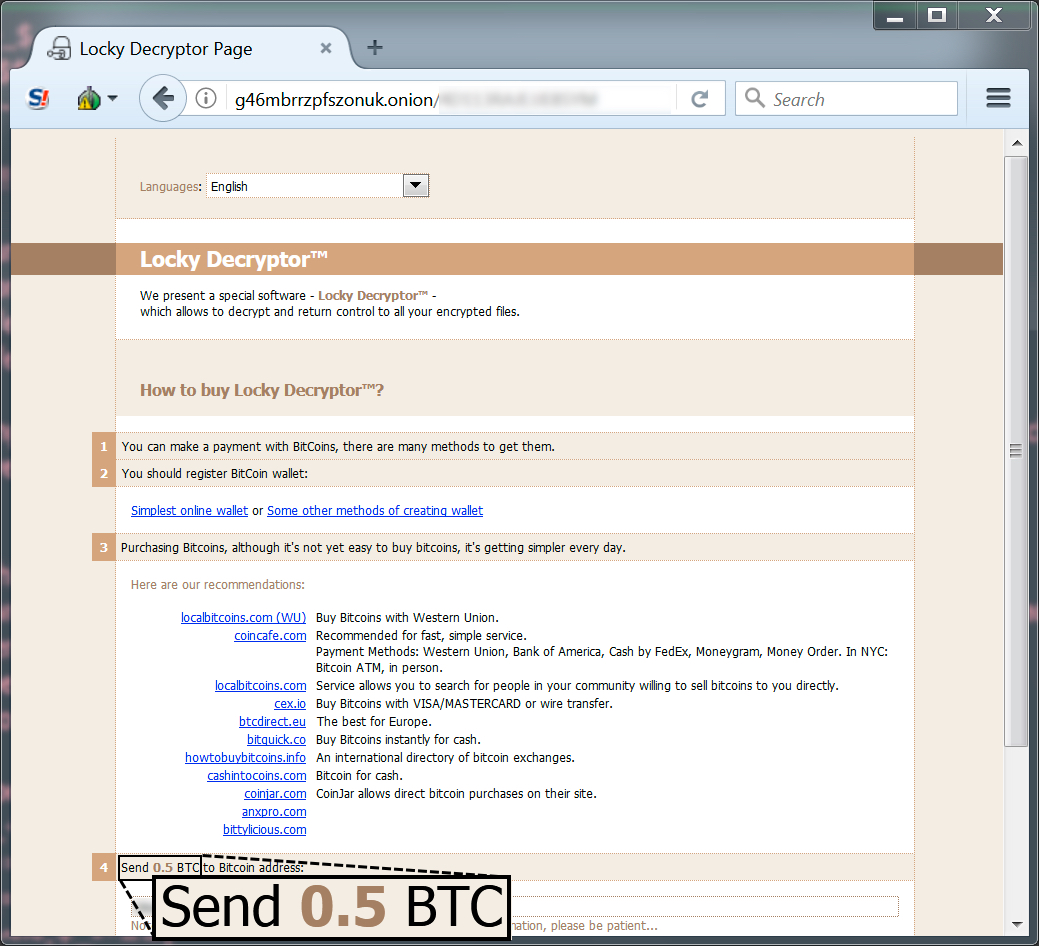
Shown above: Screen shot of the Locky decryptor asking 0.5 bitcoin for the ransom payment.
Click here to return to the main page.
