2017-12-13 - LOKIBOT INFECTION FROM RTF EXPLOITING CVE-2017-11882
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-12-13-Lokibot-malspam-tracker.csv.zip 0.5 kB (485 bytes)
- 2017-12-13-Lokibot-malspam-tracker.csv (993 bytes)
- 2017-12-13-Lokibot-malspam-5-examples.zip 69.7 kB (69,676 bytes)
- 2017-12-12-Lokibot-malspam-1359-UTC.eml (57,498 bytes)
- 2017-12-12-Lokibot-malspam-1400-UTC.eml (57,498 bytes)
- 2017-12-12-Lokibot-malspam-1402-UTC.eml (57,498 bytes)
- 2017-12-12-Lokibot-malspam-1404-UTC.eml (57,497 bytes)
- 2017-12-12-Lokibot-malspam-1416-UTC.eml (57,498 bytes)
- 2017-12-13-Lokibot-infection-traffic.pcap.zip 381.7 kB (381,740 bytes)
- 2017-12-13-Lokibot-infection-traffic.pcap (926,390 bytes)
- 2017-12-13-malware-samples-from-Lokibot-investigation.zip 926.0 kB (925,996 bytes)
- 7571BA.exe (286,720 bytes)
- Order From Dekkogroup Canada.doc (40,229 bytes)
- em.exe (385,024 bytes)
- hp.exe (438,272 bytes)
- ki.exe (442,368 bytes)
- lj.exe (434,176 bytes)
NOTES:
- The RTF attachment (same in all emails) exploited CVE-2017-11882 and retrieved the follow-up executable for Lokibot from an SMB share at \\185.45.192[.]7\s\.
- These emails were practically identical, except for the times sent and the recipients.
WEB TRAFFIC BLOCK LIST
Indicators are not a block list. If you feel the need to block web traffic, I suggest the following domains and URLs:
- hxxp[:]//185.82.202[.]75/~zadmin/ap2/mime.php
EMAILS
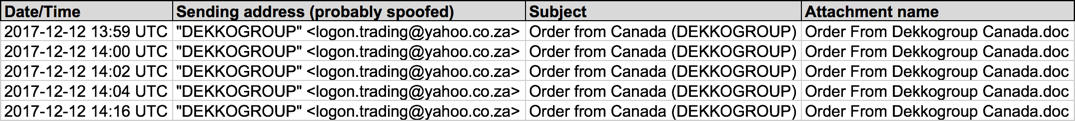
Shown above: Screenshot from the spreadsheet racker.
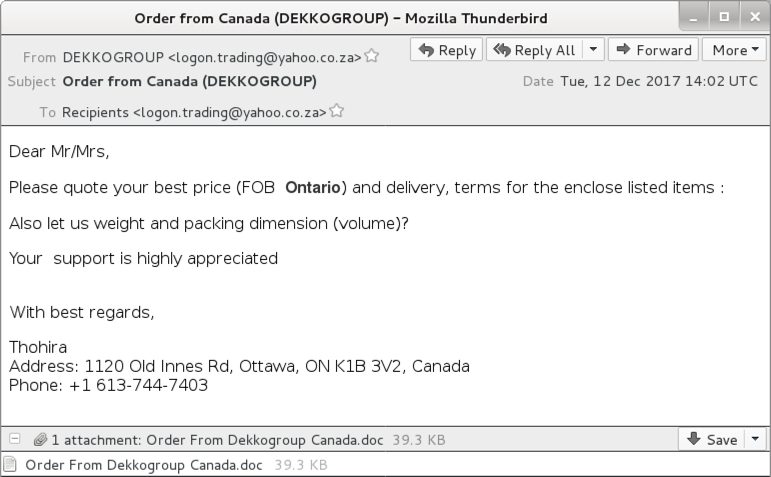
Shown above: Screenshot from one of the emails.
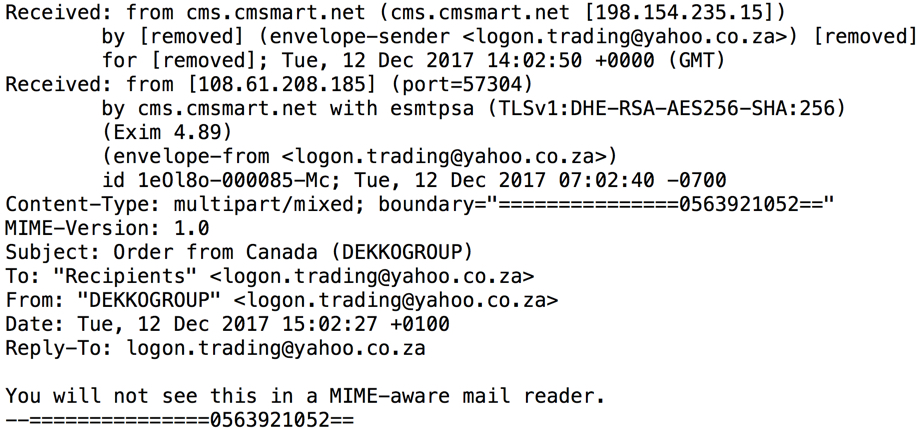
Shown above: Email headers from one of the emails.
EMAIL INFORMATION:
- Date/Time: Tuesday 2017-12-12 as early as 13:59 UTC through at least 14:16 UTC
- Received: from cms.cmsmart[.]net (cms.cmsmart[.]net [198.154.235[.]15])
- From: "DEKKOGROUP" <logon.trading@yahoo[.]co[.]za>
- Subject: Order from Canada (DEKKOGROUP)
- Attachment name: Order From Dekkogroup Canada.doc
Shown above: RTF attachment from one of the emails.
TRAFFIC
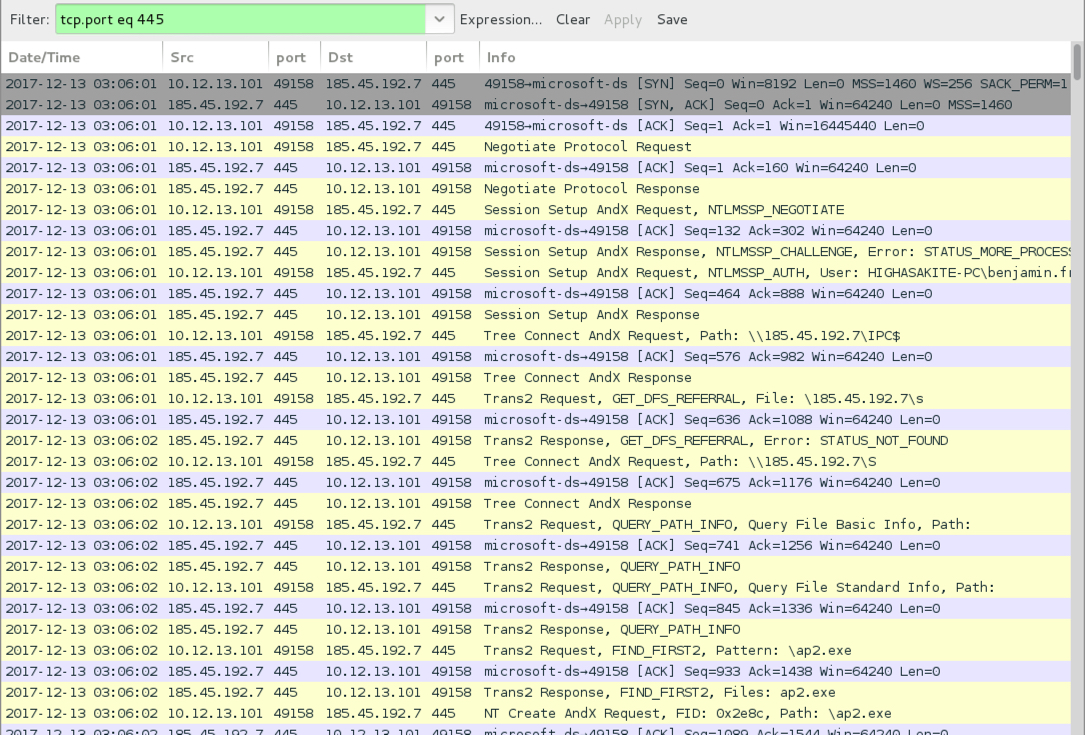
Shown above: SMB traffic from the infected Windows host filtered in Wireshark.
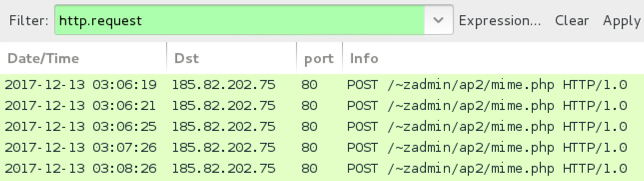
Shown above: HTTP traffic from the infected Windows host filtered in Wireshark.
ASSOCIATED TRAFFIC:
- 185.45.192[.]7 port 445 - SMB traffic to retrieve follow-up malware
- 185.82.202[.]75 port 80 - 185.82.202[.]75 - POST /~zadmin/ap2/mime.php HTTP/1.0 [Lokibot C2 traffic]
FILE HASHES
MALWARE RETRIEVED FROM THE INFECTED WINDOWS HOST:
- SHA256 hash: ff18b96950d524bf9aa0f377588663afa4a36ec1cf23002c2a894d688012416f
File size: 40,229 bytes
File name: Order From Dekkogroup Canada.doc
File description: Email attachment - RTF utilizing exploit for CVE-2017-11882
- SHA256 hash: 9cdbdc5b917a4e8be41b8ec3fee3a59d2aafd5303857f43a61cd36bcae874cd7
File size: 286,720 bytes
File location: \\185.45.192[.]7\s\ap2.exe
File location: C:\Users\[username]\AppData\Roaming\C72387\7571BA.exe
File description: Lokibot malware
MALWARE FROM THE SMB SHARE:
- SHA256 hash: ece8a4c89bc1819d5432ade73397a56da106c6131644c9191a6af970495b6d94 - File name: em.exe
- SHA256 hash: e93ebe7de46db32e94604d20ea9bff6b67bf052120137cc4f60055bdaf1ca671 - File name: hp.exe
- SHA256 hash: ba8db59040f89e13a3164f5a2f0a5c3297e221b79ef057922e86fa49a6f99c21 - File name: ki.exe
- SHA256 hash: cb3700f2905106ae90f229afd9917e2a58b9df89052601d2a9781d06f098d90a - File name: lj.exe
- ppt.exe - a legitimate version of PuTTY
IMAGES
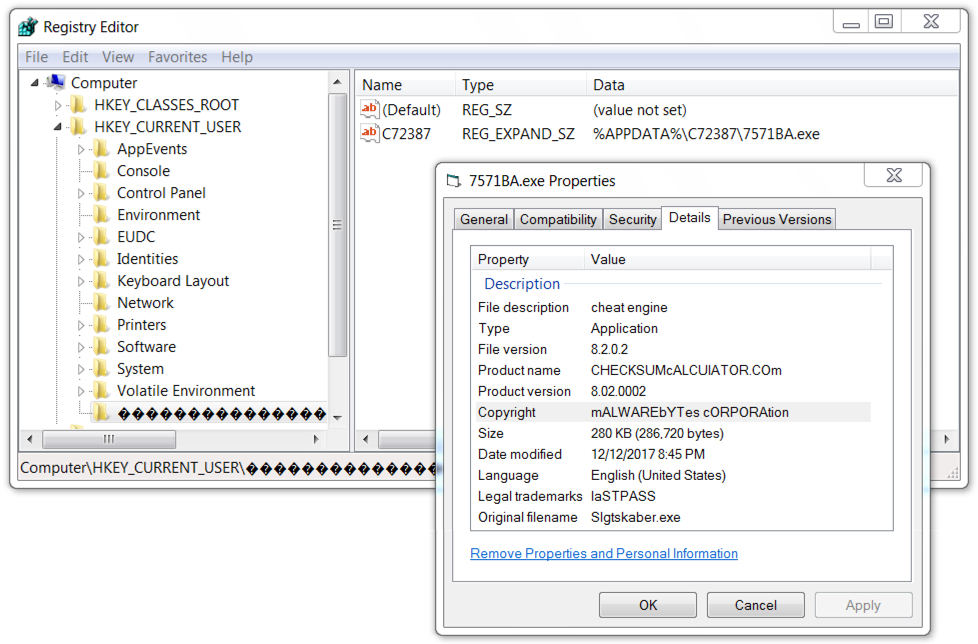
Shown above: Lokibot malware persistent on the infected host.
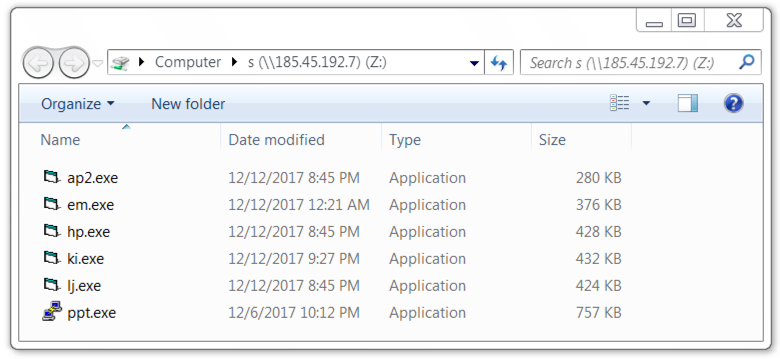
Shown above: Connecting to \\185.45.192[.]7\s as a shared drive on a Windows host.
Click here to return to the main page.
