2017-12-13 - HANCITOR INFECTION WITH ICEDID
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-12-13-Hancitor-infection-with-IcedID.pcap.zip 689.0 kB (688,956 bytes)
- 2017-12-13-Hancitor-infection-with-IcedID.pcap (961,426 bytes)
- 2017-12-13-Hancitor-malspam-10-examples.txt.zip 3.9 kB (3,916 bytes)
- 2017-12-13-Hancitor-malspam-10-examples.txt (86,603 bytes)
- 2017-12-13-malware-from-Hancitor-infection.zip 465.1 kB (465,109 bytes)
- 2017-12-13-Hancitor-maldoc-eFax_979268.doc (257,024 bytes)
- 2017-12-13-IcedID-banking-Trojan-theatctaa.exe (765,952 bytes)
NOTES:
- Today, post-infection malware from Hancitor malspam includes the Iced ID banking Trojan.
- It's been switching between Zeus Panda Banker and IcedID banking Trojan during the past two weeks or so.
- Of course, there's still Pony and Evil Pony (both fileless) also downloaded by Hancitor from the Word document macro.
- As always, thanks to @_jsoo_, @James_inthe_box, and others who contributed to the Twitter thread today.
- @James_inthe_box published additional indicators (link) that I've included in this report.
WEB TRAFFIC BLOCK LIST
Indicators are not a block list. If you feel the need to block web traffic, I suggest the following domains and URLs:
- employup[.]net
- indycareerhubcarrier[.]com
- indycareerhubcarrier[.]net
- indycareerfuture[.]com
- indycareerhubrexnord[.]com
- indycareerhubrexnord[.]net
- leapindy[.]com
- leapindy[.]net
- leapindy[.]org
- youthworksindy[.]org
- hxxp[:]//ancerapastanesi[.]com[.]tr/wp-content/plugins/posts-in-sidebar/1
- hxxp[:]//ancerapastanesi[.]com[.]tr/wp-content/plugins/posts-in-sidebar/2
- hxxp[:]//ancerapastanesi[.]com[.]tr/wp-content/plugins/posts-in-sidebar/3
- hxxp[:]//doudoukids[.]com/wp-content/plugins/wp-super-cache/1
- hxxp[:]//doudoukids[.]com/wp-content/plugins/wp-super-cache/2
- hxxp[:]//doudoukids[.]com/wp-content/plugins/wp-super-cache/3
- hxxp[:]//swiss-medical-int[.]ch/system/1
- hxxp[:]//swiss-medical-int[.]ch/system/2
- hxxp[:]//swiss-medical-int[.]ch/system/3
- hxxp[:]//swiss-vision[.]com/includes/1
- hxxp[:]//swiss-vision[.]com/includes/2
- hxxp[:]//swiss-vision[.]com/includes/3
- hxxp[:]//www.tridenttechnolabs[.]com/wp-content/plugins/waving-portfolio/1
- hxxp[:]//www.tridenttechnolabs[.]com/wp-content/plugins/waving-portfolio/2
- hxxp[:]//www.tridenttechnolabs[.]com/wp-content/plugins/waving-portfolio/3
- cilysitma[.]com
- hersandsinref[.]ru
- inleftwronhes[.]ru
- arcadyflyff[.]com
- binncu[.]net
- cupicratings[.]com
- freegameshacks[.]net
- gordondeen[.]net
EMAILS
Shown above: Screenshot from one of the emails.
Shown above: Screenshot from another one of the emails.
EMAIL HEADERS:
- Date/Time: Wednesday 2017-12-13 as early as 15:43 UTC through at least 17:32 UTC
- Received: from pdtechnologiesinc[.]com ([184.156.42[.]122])
- Received: from autumnfire[.]com ([216.174.138[.]18])
- Received: from autumnfire[.]com ([23.31.119[.]241])
- Received: from autumnfire[.]com ([66.55.14[.]10])
- Received: from autumnfire[.]com ([70.195.213[.]212])
- Received: from autumnfire[.]com ([8.46.162[.]38])
- Received: from autumnfire[.]com ([184.169.59[.]9])
- Received: from autumnfire[.]com ([205.201.68[.]70])
- Received: from autumnfire[.]com ([97.90.191[.]214])
- Received: from autumnfire[.]com ([74.205.144[.]158])
- From: "eFax.com" <efax@pdtechnologiesinc[.]com>
- From: "eFax Inc" <efax@autumnfire[.]com>
- Subject: New incoming fax from 1-610-411-3668 on Wed, 13 Dec 2017 09:41:52 -0600
- Subject: New incoming fax from 1-390-527-4832
- Subject: New incoming fax from 1-390-231-0704 on Wed, 13 Dec 2017 09:12:07 -0700
- Subject: New incoming fax from 1-390-230-4874 on Wed, 13 Dec 2017 10:27:55 -0600
- Subject: New incoming fax from 1-390-741-6256 on Wed, 13 Dec 2017 10:36:27 -0600
- Subject: New incoming fax from 1-390-042-4444
- Subject: New incoming fax from 1-390-730-5172
- Subject: New incoming fax from 1-390-751-6837
- Subject: New incoming fax from 1-390-737-2538
- Subject: New incoming fax from 1-390-368-5265
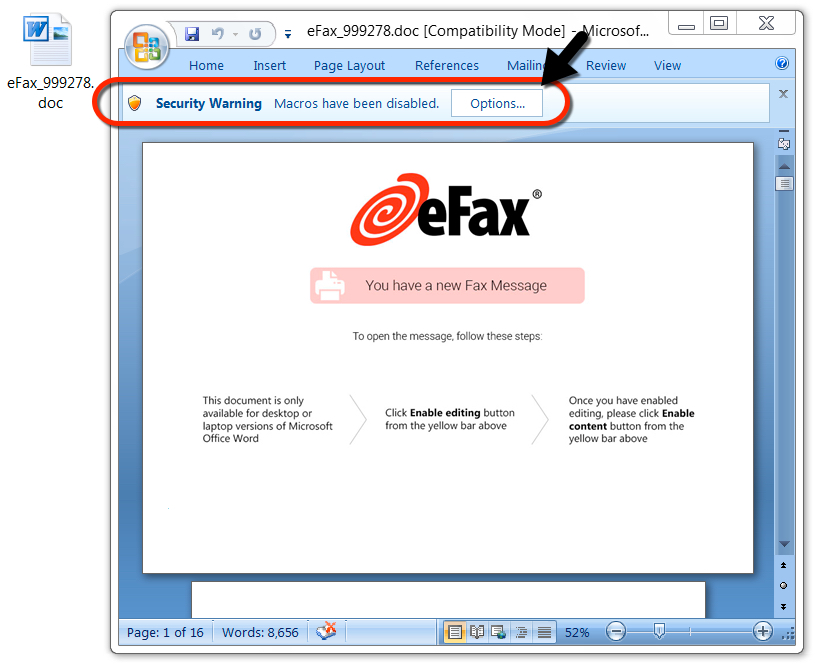
Shown above: Malicious Word document from link in the malspam.
TRAFFIC
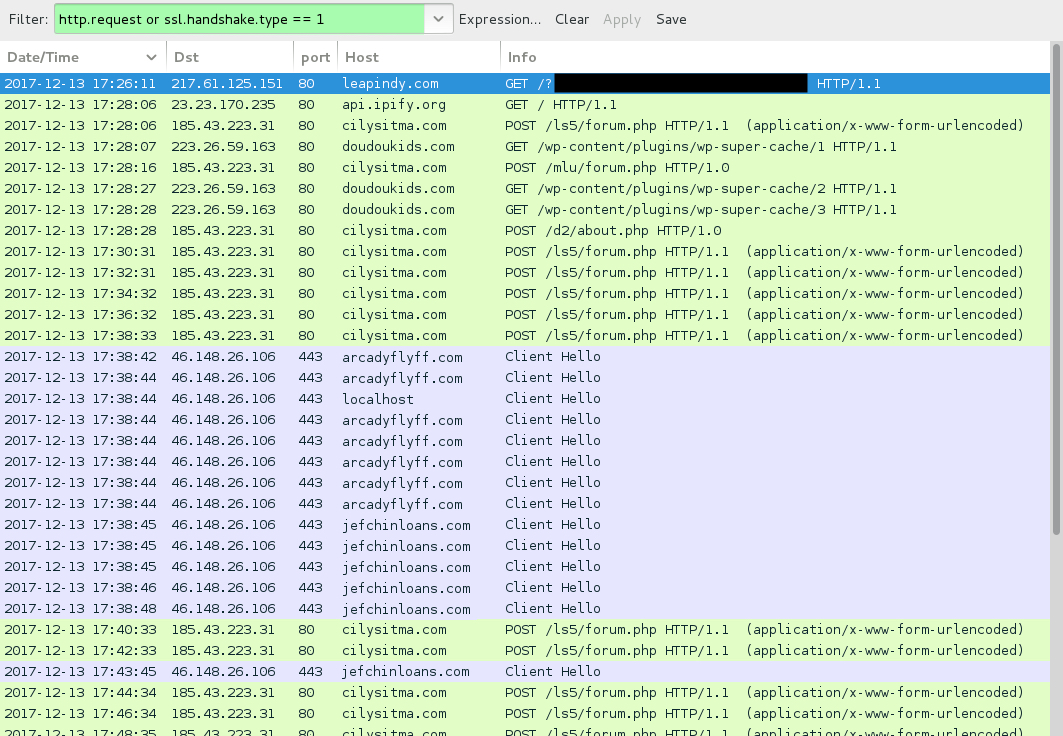
Shown above: Traffic from an infection filtered in Wireshark.
LINKS IN THE EMAILS TO THE WORD DOCUMENT:
- hxxp[:]//employup[.]net/?[encoded string]=[encoded string representing recipient's email address]
- hxxp[:]//indycareerhubcarrier[.]com/?[encoded string]=[encoded string representing recipient's email address]
- hxxp[:]//indycareerhubcarrier[.]net/?[encoded string]=[encoded string representing recipient's email address]
- hxxp[:]//indycareerfuture[.]com/?[encoded string]=[encoded string representing recipient's email address]
- hxxp[:]//indycareerhubrexnord[.]com/?[encoded string]=[encoded string representing recipient's email address]
- hxxp[:]//indycareerhubrexnord[.]net/?[encoded string]=[encoded string representing recipient's email address]
- hxxp[:]//leapindy[.]com/?[encoded string]=[encoded string representing recipient's email address]
- hxxp[:]//leapindy[.]net/?[encoded string]=[encoded string representing recipient's email address]
- hxxp[:]//leapindy[.]org/?[encoded string]=[encoded string representing recipient's email address]
- hxxp[:]//youthworksindy[.]org/?[encoded string]=[encoded string representing recipient's email address]
NETWORK TRAFFIC FROM MY INFECTED LAB HOST:
- 217.61.125[.]151 port 80 - leapindy[.]com - GET /?[encoded string that includes data for recipient's email address]
- api.ipify[.]org - GET /
- 185.43.223[.]31 port 80 - cilysitma[.]com - POST /ls5/forum.php
- 185.43.223[.]31 port 80 - cilysitma[.]com - POST /mlu/forum.php
- 185.43.223[.]31 port 80 - cilysitma[.]com - POST /d2/about.php
- 223.26.59[.]163 port 80 - doudoukids[.]com - GET /wp-content/plugins/wp-super-cache/1
- 223.26.59[.]163 port 80 - doudoukids[.]com - GET /wp-content/plugins/wp-super-cache/2
- 223.26.59[.]163 port 80 - doudoukids[.]com - GET /wp-content/plugins/wp-super-cache/3
- 46.148.26[.]106 port 443 - arcadyflyff[.]com - HTTPS/SSL/TLS traffic from IcedID banking Trojan
- 46.148.26[.]106 port 443 - localhost - HTTPS/SSL/TLS traffic from IcedID banking Trojan
- 46.148.26[.]106 port 443 - jefchinloans[.]com - HTTPS/SSL/TLS traffic from IcedID banking Trojan
FILE HASHES
MALWARE RETRIEVED FROM THE INFECTED HOST:
- SHA256 hash: 4a2e03b591495b6ad0ec6442e483857625e866b27c6f71117d0a06fe79e072c3
File size: 257,024 bytes
File name: eFax_999278.doc
File description: Word document with macro for Hancitor
- SHA256 hash: e405334639b3b6a30689156d8273ddccdeba959cca268061d4cacb995b96be79
File size: 765,952 bytes
File location: C:\Users\[username]\AppData\Local\Temp\BN2EAD.tmp
File location: C:\Users\[username]\AppData\Local\hemansgol\theatctaa.exe
File description: IcedID banking Trojan
IMAGES
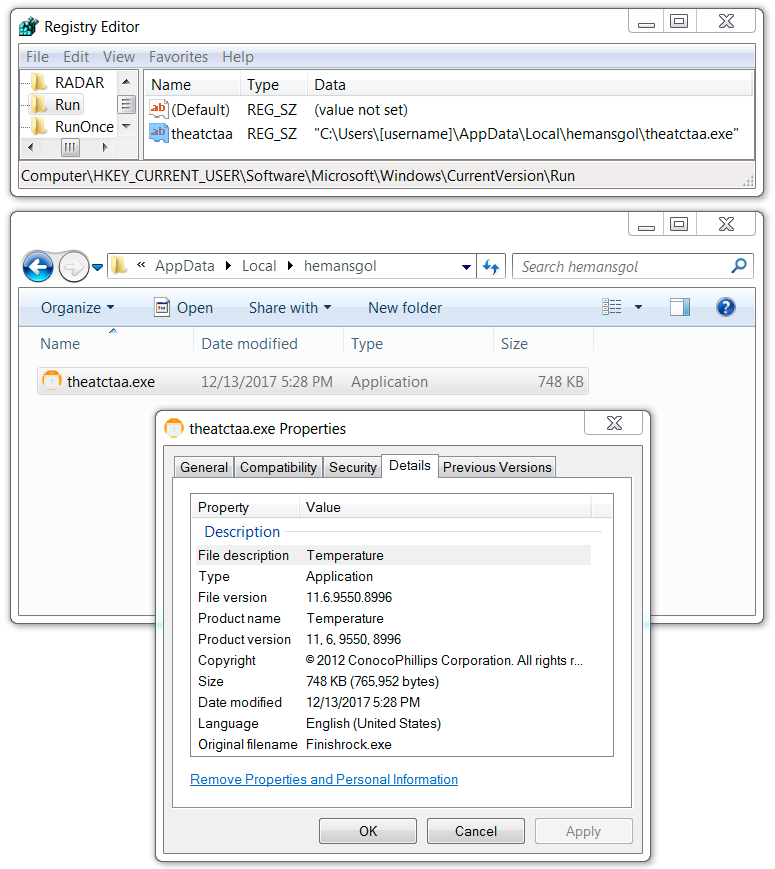
Shown above: IcedID banking Trojan persistent on the infected Windows host.
Click here to return to the main page.
