2018-02-12 - SEAMLESS CAMPAIGN RIG EK SENDS RAMNIT
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- Zip archive of the pcaps: 2018-02-12-Seamless-campaign-Rig-EK-sends-Ramnit-2-pcaps.zip 486.6 kB (486,554 bytes)
- 2018-02-12-Seamless-campaign-Rig-EK-sends-Ramnit-1st-run.pcap (294,386 bytes)
- 2018-02-12-Seamless-campaign-Rig-EK-sends-Ramnit-2nd-run.pcap (259,317 bytes)
- Zip archive of the artifacts and malware: 2018-02-12-Rig-EK-artifacts-and-Ramnit-malware.zip 297.0 kB (296,988 bytes)
- 2018-02-12-Rig-EK-artifact-u32.tmp.txt (1,141 bytes)
- 2018-02-12-Rig-EK-flash-exploit.swf (13,174 bytes)
- 2018-02-12-Rig-EK-landing-page-1st-run.txt (95,694 bytes)
- 2018-02-12-Rig-EK-landing-page-2nd-run.txt (95,634 bytes)
- 2018-02-12-Seamless-campaign-Rig-EK-payload-Ramnit-1st-run.exe (186,368 bytes)
- 2018-02-12-Seamless-campaign-Rig-EK-payload-Ramnit-2nd-run.exe (186,368 bytes)
SOME DOCUMENTATION ON THE SEAMLESS CAMPAIGN:
- 2017-03-29 - Cisco Umbrella Blog - 'Seamless' campaign delivers Ramnit via Rig EK
- 2017-05-11 - ISC Diary - Seamless Campaign using Rig Exploit Kit to send Ramnit Trojan
- 2017-05-17 through 2018-01-16 - Malware Breakdown - various blog posts on the Seamless campaign
- 2017-06-02 - Malware-Traffic-Analysis.net - Seamless campaign continues using Rig EK to send Ramnit
- 2017-08-25 - Malware-Traffic-Analysis.net - Seamless campaign Rig EK sends Ramnit
- 2017-09-07 through 2017-11-10 - Broadanalysis.com - various blog posts titled: Rig Exploit Kit via Seamless malvertising delivers Ramnit banking malware
- 2017-12-04 - MalwareBytes blog - Seamless campaign serves RIG EK via Punycode
- 2017-12-25 - traffic.moe - Seamless->RigEK->Ramnit
- 2018-01-02 - www.nao-sec.org - Analyzing Ramnit used in Seamless campaign
- 2018-01-09 - traffic.moe - Seamless->RigEK->Ramnit
- 2018-01-25 - traffic.moe - Seamless->RigEK->Ramnit
- 2018-01-26 - traffic.moe - Seamless->RigEK->Ramnit
- 2018-01-29 - Malware-Traffic-Analysis.net - Three days of Seamless campaign Rig EK pushing Gandcrab ransomware
- 2018-01-30 - traffic.moe - Seamless->RigEK->Ramnit
WEB TRAFFIC BLOCK LIST
Indicators are not a block list. If you feel the need to block web traffic, I suggest the following domains:
- bugi1man[.]info
- hshshshsussiiwuwyw[.]com
- chceoqemftwldiucf[.]com
- ghnsonrgujyymhvvg[.]com
- swwqmpjpvdbxsjos[.]com
- usrfyjueaneumqx[.]com
- gjvublwgk[.]com
- ejnpulri[.]com
- ahghbjoutgpituoybn[.]com
- bnibihajibsrqvycxv[.]com
- cakmbyctbvnnadmly[.]com
- eakrbfndtxvub[.]com
- ejnpulri[.]com
- fpbagtcbmcdcyeu[.]com
- qdxbgtalumvj[.]com
- rikbrsqoyjjpb[.]com
- sxavjnfrwwrq[.]com
- toersratxvnjtsaqdp[.]com
- tykjmixnmdpcukb[.]com
- ufylrewmo[.]com
- uwyarxuxharsm[.]com
- wqxufotucvawktbqx[.]com
- xeanmjcieuxgr[.]com
TRAFFIC
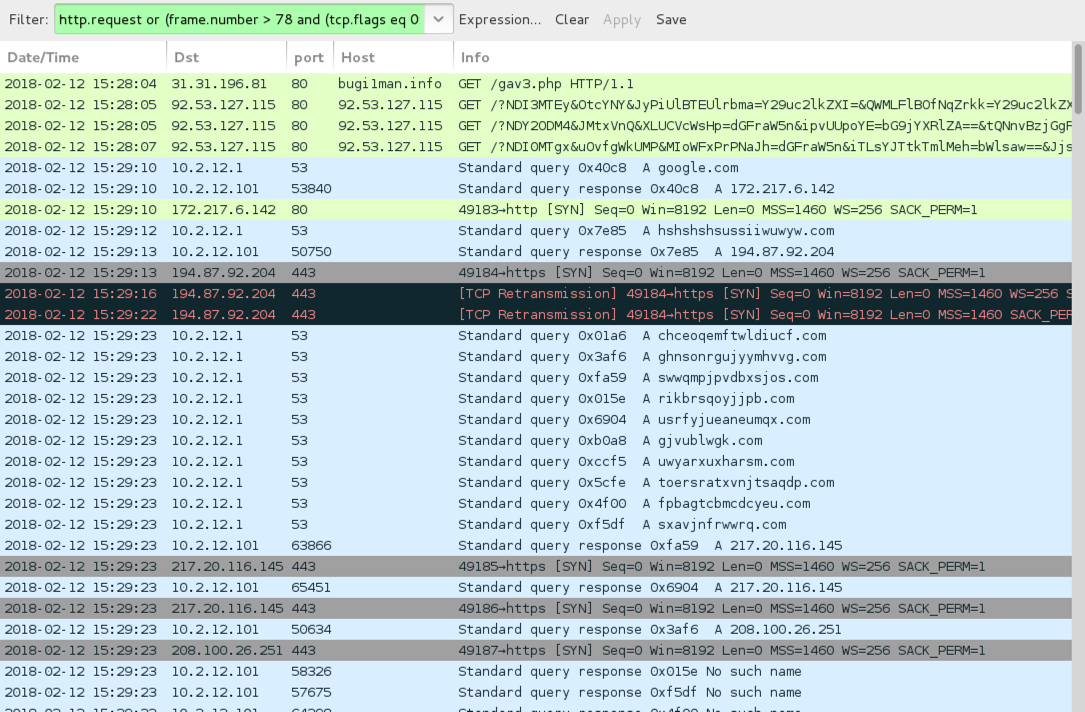
Shown above: Infection traffic in Wireshark (1st pcap).
INFECTION TRAFFIC:
- 31.31.196[.]81 port 80 - bugi1man[.]info - GET /gav3.php (Seamless gate)
- 188.225.56[.]169 port 80 - 188.225.56[.]169 - Rig EK (1st run)
- 92.53.127[.]115 port 80 - 92.53.127[.]115 - Rig EK (2nd run)
- Attempted connections to google[.]com
- 194.87.92[.]204 port 443 - hshshshsussiiwuwyw[.]com - Attempted TCP connections but RST from server
- 194.87.146[.]72 port 443 - chceoqemftwldiucf[.]com - Ramnit post-infection traffic
- 208.100.26[.]251 port 443 - ghnsonrgujyymhvvg[.]com - Ramnit post-infection traffic
- 217.20.116[.]145 port 443 - swwqmpjpvdbxsjos[.]com - Ramnit post-infection traffic
- 217.20.116[.]145 port 443 - usrfyjueaneumqx[.]com - Ramnit post-infection traffic
- 87.106.190[.]153 port 443 - gjvublwgk[.]com - Ramnit post-infection traffic
- 89.185.44[.]100 port 443 - ejnpulri[.]com - Ramnit post-infection traffic
- 195.22.26[.]248 port 443 - ejnpulri[.]com - Ramnit post-infection traffic
SOME OF THE OTHER DOMAINS CALLED BY THE INFECTED HOST (DID NOT RESOLVE):
- ahghbjoutgpituoybn[.]com
- bnibihajibsrqvycxv[.]com
- cakmbyctbvnnadmly[.]com
- eakrbfndtxvub[.]com
- ejnpulri[.]com
- fpbagtcbmcdcyeu[.]com
- qdxbgtalumvj[.]com
- rikbrsqoyjjpb[.]com
- sxavjnfrwwrq[.]com
- toersratxvnjtsaqdp[.]com
- tykjmixnmdpcukb[.]com
- ufylrewmo[.]com
- uwyarxuxharsm[.]com
- wqxufotucvawktbqx[.]com
- xeanmjcieuxgr[.]com
MALWARE
RIG EK FLASH EXPLOIT:
- SHA256 hash: 68ae3f4f654914fab02b9afe5b658adca6a653f77f8ba54279d6df8433ee197f
File size: 13,174 bytes
SEAMLESS CAMPAIGN RIG EK PAYLOAD - RAMNIT (1ST RUN):
- SHA256 hash: af29c1c00c004fd9830ea22e0cf6bdb29e567ed251272212249d4f1123f61ce1
File size: 186,368 bytes
SEAMLESS CAMPAIGN RIG EK PAYLOAD - RAMNIT (2ND RUN):
- SHA256 hash: 10630f443af5b69a04edbe699d81cd5eeaf7fd235d4dfdd1c8ff49c672db47bb
File size: 186,368 bytes
IMAGES
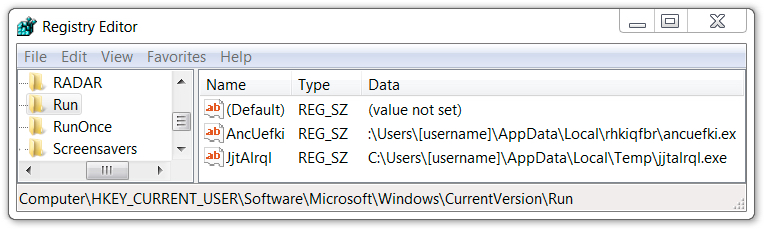
Shown above: Registry key on the infected Windows host updated for malware persistence.
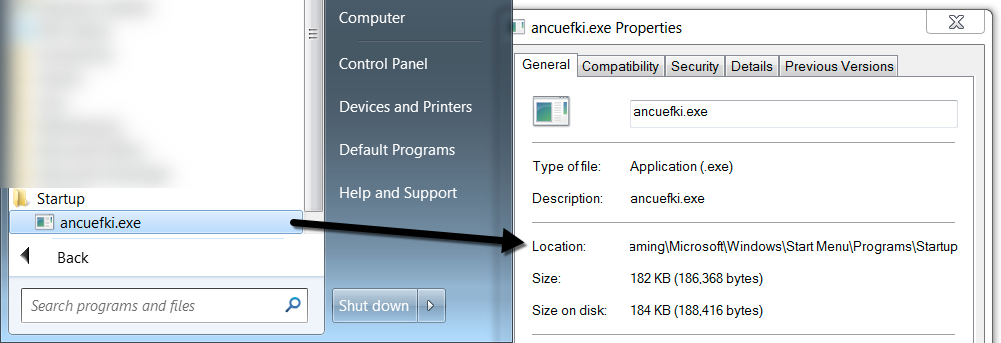
Shown above: Another copy of Ramnit in the Startup folert in the Start Menu.
Click here to return to the main page.
