2018-02-28 - HANCITOR INFECTION WITH ZEUS PANDA BANKER
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- Zip archive of the traffic: 2018-02-28-Hancitor-malspam-infection-pcaps.zip 931.6 kB (931,569 bytes)
- 2018-02-28-Hancitor-infection-with-Zeus-Panda-Banker-1st-run.pcap (327,381 bytes)
- 2018-02-28-Hancitor-infection-with-Zeus-Panda-Banker-2nd-run.pcap (309,891 bytes)
- 2018-02-28-Hancitor-infection-with-Zeus-Panda-Banker-3rd-run.pcap (421,314 bytes)
- Zip archive of the emails: 2018-02-28-Hancitor-malspam-20-examples.txt.zip 5.5 kB (5,535 bytes)
- 2018-02-28-Hancitor-malspam-20-examples.txt (80,869 bytes)
- Zip archive of the malware: 2018-02-28-malware-from-Hancitor-infections.zip 266.3 kB (266,386 bytes)
- 2018-02-28-Hancitor-maldoc-fax_933254.doc (240,640 bytes)
- 2018-02-28-Zeus-Panda-Banker.exe (188,928 bytes)
NOTES:
- I updated the hosts file in my Windows lab hosts to generate infection traffic with some (but not all) of the alternate domains used in the initial callback and follow-up downloads.
- Still seeing Pony, Evil Pony (both resident in memory), and Zeus Panda Banker (saved to disk) as the follow-up malware.
WEB TRAFFIC BLOCK LIST
Indicators are not a block list. If you feel the need to block web traffic, I suggest the following domains and URLs:
- hnimanagement[.]com
- hnimgmt[.]com
- hnimgt[.]com
- kastarmgt[.]com
- kastarqsr[.]com
- myyogaberry[.]com
- starcorpinc[.]com
- thorsolberg[.]com
- yobe[.]me
- yoga-berry[.]com
- caledkedwron[.]com
- gotletmoked[.]ru
- ningtoftcaso[.]ru
- hxxp[:]//hestfitness[.]com/lib/flex/uploader/1
- hxxp[:]//hestfitness[.]com/lib/flex/uploader/2
- hxxp[:]//hestfitness[.]com/lib/flex/uploader/4
- hxxp[:]//gomezespejel[.]net/examples/1
- hxxp[:]//gomezespejel[.]net/examples/2
- hxxp[:]//gomezespejel[.]net/examples/4
- hxxp[:]//nectarsinc[.]com/wp-content/plugins/siteorigin-panels/settings/1
- hxxp[:]//nectarsinc[.]com/wp-content/plugins/siteorigin-panels/settings/2
- hxxp[:]//nectarsinc[.]com/wp-content/plugins/siteorigin-panels/settings/4
- ofhahertit[.]com
EMAILS
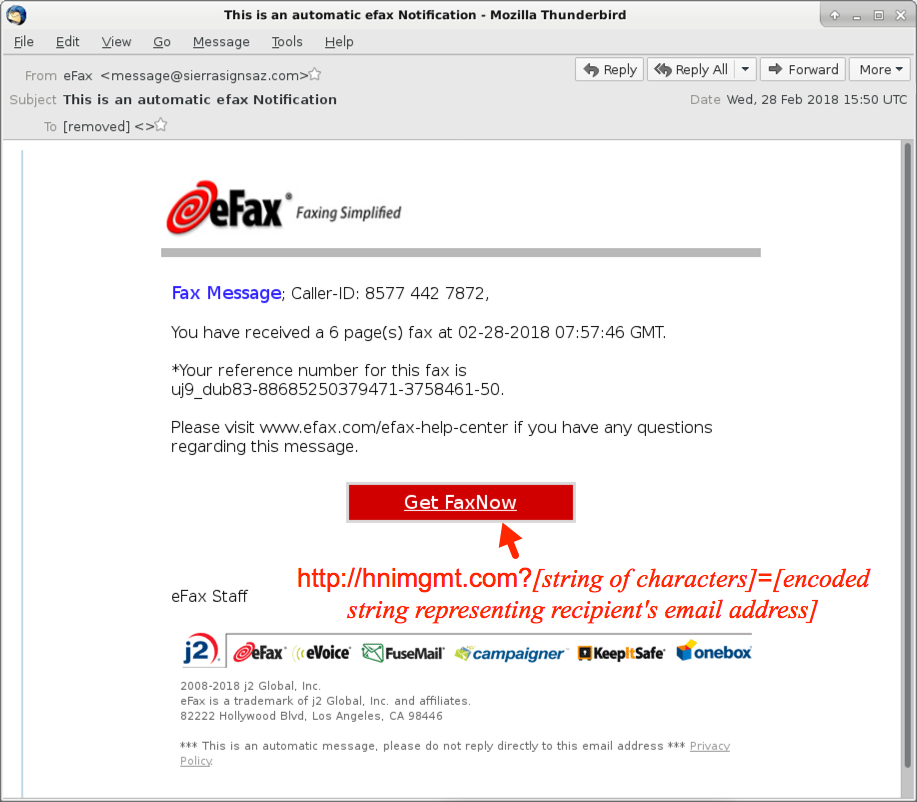
Shown above: Screenshot from one of the emails.
EMAIL HEADERS:
- Date/Time: Wednesday 2018-02-28 as early as 15:50 UTC through at least 19:25 UTC
- Received: from ([68.62.127[.]160])
- Received: from cgmdev[.]com ([73.58.50[.]32])
- Received: from cgmdev[.]com ([74.87.9[.]154])
- Received: from cgmdev[.]com ([96.84.215[.]1])
- Received: from cgmdev[.]com ([207.228.111[.]162])
- Received: from hillusa[.]com ([24.167.98[.]71])
- Received: from hillusa[.]com ([63.116.5[.]146])
- Received: from hillusa[.]com ([67.52.197[.]46])
- Received: from hillusa[.]com ([108.58.46[.]222])
- Received: from hillusa[.]com ([184.70.252[.]186])
- Received: from mtytocn[.]com ([96.88.9[.]57])
- Received: from mtytocn[.]com ([108.228.169[.]90])
- Received: from sierrasignsaz[.]com ([23.25.119[.]25])
- Received: from sierrasignsaz[.]com ([24.29.19[.]205])
- Received: from sierrasignsaz[.]com ([45.50.34[.]188])
- Received: from sierrasignsaz[.]com ([70.168.199[.]133])
- Received: from sierrasignsaz[.]com ([72.24.104[.]186])
- Received: from sierrasignsaz[.]com ([74.113.59[.]181])
- Received: from sierrasignsaz[.]com ([98.187.252[.]218])
- Received: from sierrasignsaz[.]com ([206.116.57[.]53])
- From: "eFax , Inc." <message@cgmdev[.]com>
- From: "eFax , Inc." <message@hillusa[.]com>
- From: "eFax , Inc." <message@sierrasignsaz[.]com>
- From: "eFax " <message@hillusa[.]com>
- From: "eFax " <message@mtytocn[.]com>
- From: "eFax " <message@sierrasignsaz[.]com>
- From: "eFax j2 Global, Inc." <message@cgmdev[.]com>
- From: "eFax j2 Global, Inc." <message@hillusa[.]com>
- From: "eFax j2 Global, Inc." <message@sierrasignsaz[.]com>
- From: "eFax j2 Global" <message@cgmdev[.]com>
- From: "eFax j2 Global" <message@hillusa[.]com>
- From: "eFax j2 Global" <message@mtytocn[.]com>
- From: "eFax j2 Global" <message@sierrasignsaz[.]com>
- Subject: This is an automatic eFax Notice
- Subject: This is an automatic efax Notification
- Subject: This is an electronic eFax Notice
- Subject: This is an electronic efax Notification
- Subject: This is efax Notice
- Subject: This is eFax Notification
- Subject: You have received efax Message
- Subject: You've got eFax Notice
- Subject: You've got eFax Notification
- Subject: You've received eFax Message
- Subject: You've received efax Notification
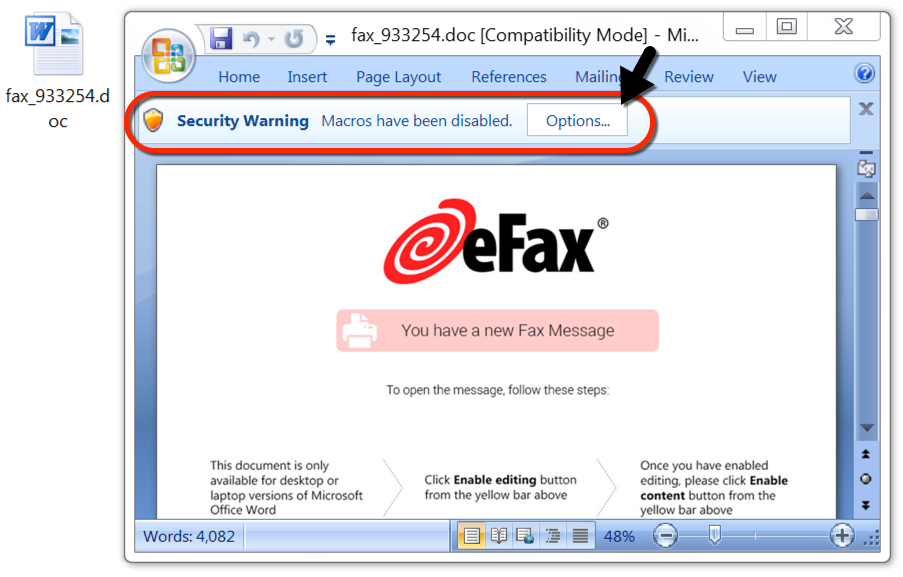
Shown above: Malicious Word document downloaded from a link in the malspam.
TRAFFIC
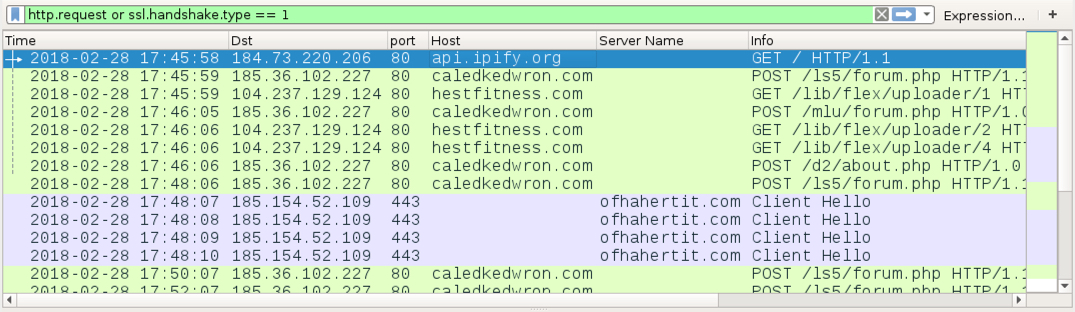
Shown above: Traffic from an infection filtered in Wireshark.
LINKS IN THE EMAILS TO THE WORD DOCUMENT:
- hxxp[:]//hnimanagement[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//hnimgmt[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//hnimgt[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//kastarmgt[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//kastarqsr[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//myyogaberry[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//starcorpinc[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//thorsolberg[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//yobe[.]me?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//yoga-berry[.]com?[string of characters]=[encoded string representing recipient's email address]
NETWORK TRAFFIC FROM MY INFECTED LAB HOSTS:
- 185.36.102[.]227 port 80 - caledkedwron[.]com - POST /ls5/forum.php
- 185.36.102[.]227 port 80 - caledkedwron[.]com - POST /mlu/forum.php
- 185.36.102[.]227 port 80 - caledkedwron[.]com - POST /d2/about.php
- 104.237.129[.]124 port 80 - hestfitness[.]com - GET /lib/flex/uploader/1
- 104.237.129[.]124 port 80 - hestfitness[.]com - GET /lib/flex/uploader/2
- 104.237.129[.]124 port 80 - hestfitness[.]com - GET /lib/flex/uploader/4
- 185.154.52[.]109 port 443 - ofhahertit[.]com - HTTPS/SSL/TLS traffic from Zeus Panda Banker
- 91.214.119[.]59 port 80 - gotletmoked[.]ru - POST /ls5/forum.php
- 91.214.119[.]59 port 80 - gotletmoked[.]ru - POST /mlu/forum.php
- 91.214.119[.]59 port 80 - gotletmoked[.]ru - POST /d2/about.php
- 173.247.253[.]159 port 80 - gomezespejel[.]net - GET /examples/1
- 173.247.253[.]159 port 80 - gomezespejel[.]net - GET /examples/2
- 173.247.253[.]159 port 80 - gomezespejel[.]net - GET /examples/4
- 185.154.52[.]109 port 443 - ofhahertit[.]com - HTTPS/SSL/TLS traffic from Zeus Panda Banker
- 78.155.220[.]218 port 80 - ningtoftcaso[.]ru - POST /ls5/forum.php
- 78.155.220[.]218 port 80 - ningtoftcaso[.]ru - POST /mlu/forum.php
- 78.155.220[.]218 port 80 - ningtoftcaso[.]ru - POST /d2/about.php
- 192.254.233[.]176 port 80 - nectarsinc[.]com - GET /wp-content/plugins/siteorigin-panels/settings/1
- 192.254.233[.]176 port 80 - nectarsinc[.]com - GET /wp-content/plugins/siteorigin-panels/settings/2
- 192.254.233[.]176 port 80 - nectarsinc[.]com - GET /wp-content/plugins/siteorigin-panels/settings/4
- 185.154.52[.]109 port 443 - ofhahertit[.]com - HTTPS/SSL/TLS traffic from Zeus Panda Banker
FILE HASHES
MALWARE RETRIEVED FROM AN INFECTED WINDOWS HOST:
- SHA256 hash: 5209e6d4028b82cd1a59b737ea34a69cfa924a0d690c57b52eaeb2d31868d88f
File size: 240,640 bytes
File name: fax_933254.doc [any six random digits for the numbers]
File description: Word document with macro for Hancitor
- SHA256 hash: d04124e357f6755e21cd36fefccfd7eec1a09148f41aaea25cbd326690bd4f23
File size: 188,928 bytes
File location: C:\Users\[username]\AppData\Local\[existing directory path]\[random name].exe
File description: Zeus Panda Banker
Click here to return to the main page.
