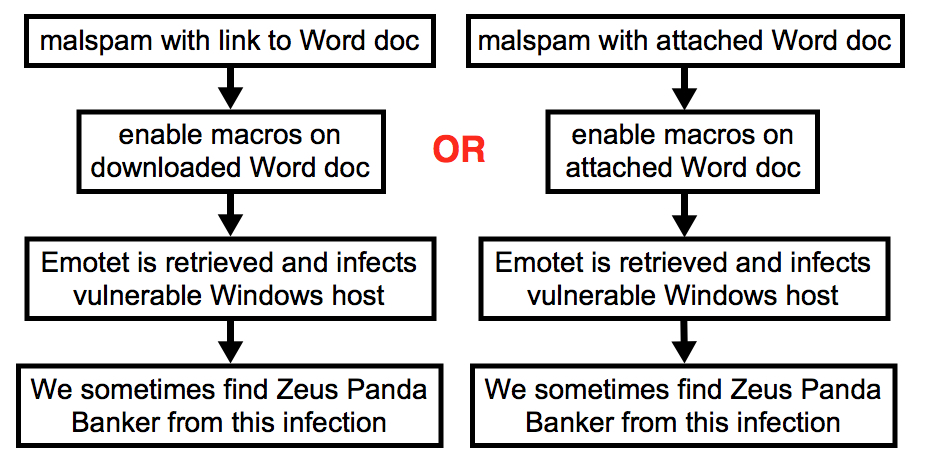
2018-06-12 - EMOTET INFECTION WITH ZEUS PANDA BANKER
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2018-06-12-Emotet-malspam-10-examples.zip 70.6 kB (70,623 bytes)
- 2018-06-12-Emotet-malspam-1258-UTC.eml (1,446 bytes)
- 2018-06-12-Emotet-malspam-1614-UTC.eml (1,784 bytes)
- 2018-06-12-Emotet-malspam-1626-UTC.eml (1,209 bytes)
- 2018-06-12-Emotet-malspam-1749-UTC.eml (1,182 bytes)
- 2018-06-12-Emotet-malspam-1818-UTC.eml (1,355 bytes)
- 2018-06-12-Emotet-malspam-1821-UTC.eml (1,743 bytes)
- 2018-06-12-Emotet-malspam-1936-UTC.eml (134,520 bytes)
- 2018-06-12-Emotet-malspam-1940-UTC.eml (1,286 bytes)
- 2018-06-12-Emotet-malspam-2038-UTC.eml (1,000 bytes)
- 2018-06-12-Emotet-malspam-2046-UTC.eml (845 bytes)
- 2018-06-12-Emotet-infection-with-Zeus-Panda-Banker.pcap.zip 3.8 MB (3,838,820 bytes)
- 2018-06-12-Emotet-infection-with-Zeus-Panda-Banker.pcap (4,823,683 bytes)/li>
- 2018-06-12-malware-from-Emotet-infection.zip 1.1 MB (1,139,305 bytes)
- 2018-06-12-Emotet-executable-1-of-5.exe (274,432 bytes)
- 2018-06-12-Emotet-executable-2-of-5.exe (143,360 bytes)
- 2018-06-12-Emotet-executable-3-of-5.exe (143,360 bytes)
- 2018-06-12-Emotet-executable-4-of-5.exe (143,360 bytes)
- 2018-06-12-Emotet-executable-5-of-5.exe (287,744 bytes)
- 2018-06-12-Word-document-with-macro-for-emotet-1-of-12.doc (104,448 bytes)
- 2018-06-12-Word-document-with-macro-for-emotet-10-of-12.doc (123,648 bytes)
- 2018-06-12-Word-document-with-macro-for-emotet-11-of-12.doc (96,000 bytes)
- 2018-06-12-Word-document-with-macro-for-emotet-12-of-12.doc (99,840 bytes)
- 2018-06-12-Word-document-with-macro-for-emotet-2-of-12.doc (92,416 bytes)
- 2018-06-12-Word-document-with-macro-for-emotet-3-of-12.doc (119,296 bytes)
- 2018-06-12-Word-document-with-macro-for-emotet-4-of-12.doc (110,336 bytes)
- 2018-06-12-Word-document-with-macro-for-emotet-5-of-12.doc (98,048 bytes)
- 2018-06-12-Word-document-with-macro-for-emotet-6-of-12.doc (104,192 bytes)
- 2018-06-12-Word-document-with-macro-for-emotet-7-of-12.doc (94,976 bytes)
- 2018-06-12-Word-document-with-macro-for-emotet-8-of-12.doc (123,392 bytes)
- 2018-06-12-Word-document-with-macro-for-emotet-9-of-12.doc (91,136 bytes)
- 2018-06-12-Zeus-Panda-Banker-caused-by-Emotet-infection.exe (275,456 bytes)
Shown above: Sometimes there's also a PDF document when we see an attached Word document. In this case, the PDF document was harmless.
It merely had text stating "Payroll reports are attached to this e-mail."
WEB TRAFFIC BLOCK LIST
URLS FROM THE MALSPAM TO RETRIEVE THE WORD DOCS:
- hxxp[:]//aussiescanners[.]com/IRS-Tax-Transcipts-June-2018-1745/
- hxxp[:]//dapinha[.]com[.]br/IRS-Tax-Transcipts-041L/82/
- hxxp[:]//dekarlos[.]com/IRS-Tax-Transcipts-048B/96/
- hxxp[:]//ekolab[.]by/Client/Invoice-70872717-Invoice-date-061218-Order-no-5545897287/
- hxxp[:]//frayd[.]com/IRS-Transcripts-068/1/
- hxxp[:]//josephdutton[.]com/Client/Emailing-H667564FV-45577/
- hxxp[:]//parisel[.]pl/ACCOUNT/Past-Due-invoice/
- hxxp[:]//planitsolutions[.]co[.]nz/IRS-Tax-Transcipts-062018-004S/13/
- hxxp[:]//reidsprite[.]com/UPS-US-INV-00F/7/
- hxxp[:]//the-grizz[.]com/gallery/g2data/IRS-Tax-Transcipts-062018-01/8/
- hxxp[:]//vodaless[.]net/IRS-Letters-06G/90/
- hxxp[:]//wevik[.]hu/IRS-Accounts-Transcipts-062018-0991/
- hxxp[:]//www.1-stomatolog[.]ru/FILE/Invoice-18520036589-06-12-2018/
- hxxp[:]//www.1.adborod.z8[.]ru/IRS-Letters-062018-002/54/
- hxxp[:]//www.2.u0135364.z8[.]ru/ACCOUNT/Customer-Invoice-SB-36047325/
- hxxp[:]//www.180daystohappy[.]com/IRS-Letters-074X/1/
- hxxp[:]//www.acbor[.]org/IRS-Letters-050/5/
- hxxp[:]//www.accuratedna[.]net/IRS-Transcripts-017P/48/
- hxxp[:]//www.actionpackedcomics[.]ca/IRS-Tax-Transcipts-715/
- hxxp[:]//www.actvideo[.]fr/IRS-TRANSCRIPTS-646/
- hxxp[:]//www.adcanudosnh[.]com[.]br/IRS-Accounts-Transcipts-430/
- hxxp[:]//www.adebeo[.]co[.]in/IRS-Accounts-Transcipts-3429/
- hxxp[:]//www.airseaexpressshipping[.]com/STATUS/Invoices/
- hxxp[:]//www.alanyaetkinegitim[.]com/UPS-Invoices-06122018-049/5/
- hxxp[:]//www.almokhtarco[.]com/IRS-Tax-Transcipts-June-2018-09/9/
- hxxp[:]//www.andreykalmykov[.]com/IRS-Transcripts-062018-028/79/
- hxxp[:]//www.aninaslodge[.]com/ACCOUNT/Account-03721/
- hxxp[:]//www.arj.zov-duha[.]ru/IRS-TRANSCRIPTS-085/67/
- hxxp[:]//www.askalmostanything[.]com/STATUS/Invoices/
- hxxp[:]//www.ateliestudia[.]ru/IRS-Accounts-Transcipts-957/
- hxxp[:]//www.autokosmetykicartec[.]pl/IRS-Transcripts-013/2/
- hxxp[:]//www.bathoff[.]ru/STATUS/Account-99386/
- hxxp[:]//www.bergzitat[.]de/IRS-Tax-Transcipts-June-2018-040/15/
- hxxp[:]//www.beta.salon[.]mn/Client/Invoice-981475/
- hxxp[:]//www.beyhannakliyat[.]com/FILE/invoice/
- hxxp[:]//www.bilberrymarketing[.]ca/IRS-Accounts-Transcipts-June-2018-02O/6/
- hxxp[:]//www.blci[.]info/INV/
- hxxp[:]//www.boxbomba.nichost[.]ru/IRS-Letters-04E/0/
- hxxp[:]//www.campusbowling[.]com[.]tr/Invoice-Corrections-12/June/2018/
- hxxp[:]//www.caritaszambia[.]org/ACCOUNT/Services-06-12-18-New-Customer-DC/
- hxxp[:]//www.carpexhaliyikama[.]net/IRS-Letters-062018-2806/
- hxxp[:]//www.catering.quoteprovider[.]com/IRS-Tax-Transcipts-04/32/
- hxxp[:]//www.cecconi[.]com[.]br/DOC/Invoice-602577/
- hxxp[:]//www.ciptasemula[.]com/ACCOUNT/Invoice-528134/
- hxxp[:]//www.con-sentidos[.]com/IRS-Transcripts-June-2018-577/
- hxxp[:]//www.corpus-delicti[.]com/Client/Emailing-B28901NZ-20555/
- hxxp[:]//www.correo.kable[.]cl/STATUS/Invoice-860186/
- hxxp[:]//www.crm.pandoravietnam[.]com/IRS-TRANSCRIPTS-02/8/
- hxxp[:]//www.cuaabshanquoc[.]vn/ACCOUNT/Invoice-422182162-Invoice-date-061218-Order-no-97935570232/
- hxxp[:]//www.demo2.arkan[.]ru/IRS-Tax-Transcipts-062018-030/6/
- hxxp[:]//www.dev.klastcarpet[.]com/IRS-TRANSCRIPTS-June-2018-088/8/
- hxxp[:]//www.dulichmyviet[.]com[.]vn/STATUS/New-Invoice-LR52783-FP-52816/
- hxxp[:]//www.ealammadarisna[.]com/IRS-Tax-Transcipts-04T/48/
- hxxp[:]//www.efs-euro-finanz-service[.]de/IRS-Letters-3869/
- hxxp[:]//www.elearn.efesmoldova[.]md/IRS-Tax-Transcipts-June-2018-04Y/3/
- hxxp[:]//www.en.chubakhangal[.]mn/FILE/Invoice-082673/
- hxxp[:]//www.euro-finanz-service-ag[.]de/IRS-Accounts-Transcipts-June-2018-04/48/
- hxxp[:]//www.followmetalk[.]com/Open-invoices/
- hxxp[:]//www.followmetalkbeta.okoyemedia[.]com/DOC/invoice/
- hxxp[:]//www.ingles.natal[.]br/FILE/New-Invoice-ZW5031-ST-0547/
- hxxp[:]//www.invoice.mobileaps[.]in/IRS-Letters-091Y/0/
- hxxp[:]//www.itswitch[.]nl/FILE/Auditor-of-State-Notification-of-EFT-Deposit/
- hxxp[:]//www.mbsou37[.]ru/FILE/ACCOUNT468852/
- hxxp[:]//www.precisionpaintingandrepairsinc[.]com/IRS-Accounts-Transcipts-062018-021U/4/
- hxxp[:]//www.redridgeumc[.]org/DOC/Services-06-13-18-New-Customer-OC/
- hxxp[:]//www.triboteen[.]com[.]br/IRS-Tax-Transcipts-June-2018-8815/
- hxxp[:]//www.vacationhotels[.]xyz/IRS-Accounts-Transcipts-070A/43/
- hxxp[:]//www.yeditepeofset[.]com/Past-Due-Invoices/
URLS GENERATED BY THE WORD MACROS TO RETRIEVE EMOTET:
- hxxp[:]//airmaxx[.]rs/wIdY/
- hxxp[:]//alpinewebgroup[.]com/A1gkl/
- hxxp[:]//djivi[.]nl/iZoD/
- hxxp[:]//eclatpro[.]com/tleyLN/
- hxxp[:]//matthewbarley[.]com/o8LZnI/
- hxxp[:]//nepapiano[.]com/VBrs/
- hxxp[:]//rosehill[.]hu/ooOCqD/
- hxxp[:]//scd[.]com[.]gt/J7cczqWI5n/
- hxxp[:]//simp-consulting[.]pl/biuro/1GGaf/
- hxxp[:]//soo[.]sg/dbs/media/sJUjDl/
- hxxp[:]//spearllc[.]com/_dsn/h54alb/
- hxxp[:]//teplokratiya[.]ru/giG1isC/
- hxxp[:]//webuzmani[.]net/xNVuSEwKz3/
- hxxp[:]//www.2015at-thru-hike[.]com/MvvjrZZ/
- hxxp[:]//www.360detail[.]com/Rxx00P5AtM/
- hxxp[:]//www.4outdoor[.]net/SnDJHLp/
- hxxp[:]//www.adanawebseo[.]net/0ijCv/
- hxxp[:]//www.avant-yug[.]ru/Av8E0EygP/
- hxxp[:]//www.baskentfirinmakina[.]com/rQc2XGvbQ/
- hxxp[:]//www.bostik[.]com[.]ro/6koI2ip/
- hxxp[:]//www.depilation38[.]ru/DA4z/
- hxxp[:]//www.englishcenter[.]ru/Ev5NVc/
- hxxp[:]//www.erginmobilya[.]com/l9bBskaj5L/
- hxxp[:]//www.etravel[.]su/x1LyKWdm/
- hxxp[:]//www.fcpe81370[.]fr/FlpKcz/
- hxxp[:]//www.india9am[.]com/wp-content/zPEGxIfwd/
- hxxp[:]//www.planetariy[.]com/rlbOcvuh/
- hxxp[:]//www.thecyberconxion[.]com/PUqUUe/
- hxxp[:]//xn--k1acdflk8dk[.]xn--p1ai/DAA4WB/
DOMAIN FOR HTTPS/SSL/TLS TRAFFIC CAUSED BY ZEUS PANDA BANKER:
- adshiepkhach[.]top
EMAILS
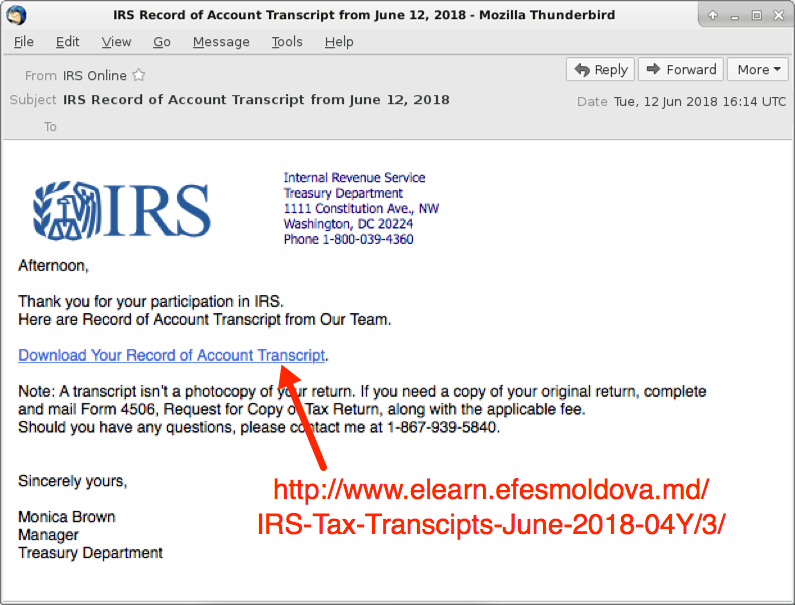
Shown above: Example of the IRS-themed Emotet malspam.
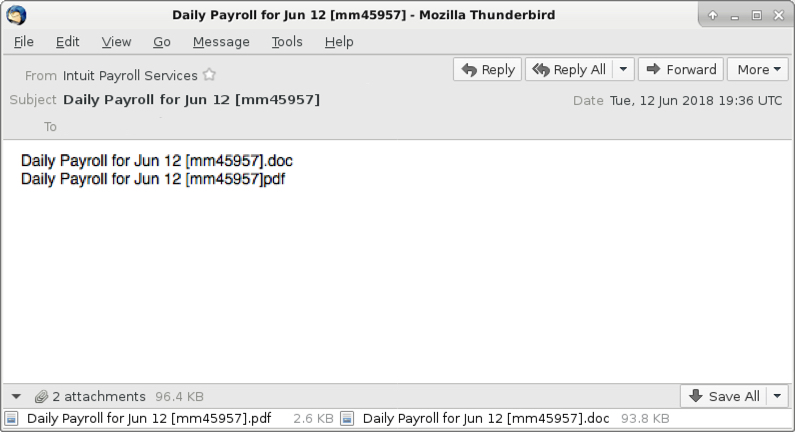
Shown above: Example of Emotet malspam with an attached Word doc instead of a link.
DATA FROM 10 EMAIL EXAMPLES OF THE MALSPAM:
- Date/Time: Tuesday, 2018-06-12 12:58 UTC
- Received: from 10.0.0[.]61 ([103.55.184[.]7])
- From: IRS <Press@treasury[.]gov> <[removed]@[removed]>
- Subject: IRS Record of Account Transcript from 06/12/2018
- Link for malware: hxxp[:]//vodaless[.]net/IRS-Letters-06G/90/
- Date/Time: Tuesday, 2018-06-12 16:14 UTC
- Received: from 10.0.0[.]61 ([187.217.187[.]162])
- From: IRS Online <[removed]@[removed]>
- Subject: IRS Record of Account Transcript from June 12, 2018
- Link for malware: hxxp[:]//www.elearn.efesmoldova[.]md/IRS-Tax-Transcipts-June-2018-04Y/3/
- Date/Time: Tuesday, 2018-06-12 16:26 UTC
- Received: from ([189.134.228[.]12])
- From: IRS Online Center <[removed]@[removed]>
- Subject: IRS Tax Account Transcript
- Link for malware: hxxp[:]//www.bergzitat[.]de/IRS-Tax-Transcipts-June-2018-040/15/
- Date/Time: Tuesday, 2018-06-12 17:49 UTC
- Received: from 10.0.0[.]48 ([221.163.32[.]101])
- From: IRS <Press@treasury[.]gov> <[removed]@[removed]>
- Subject: IRS Wage and Income Transcript from 06/12/2018
- Link for malware: hxxp[:]//www.actionpackedcomics[.]ca/IRS-Tax-Transcipts-715/
- Date/Time: Tuesday, 2018-06-12 18:18 UTC
- Received: from 10.0.0[.]12 ([197.89.246[.]228])
- From: Internal Revenue Service Online <[removed]@[removed]>
- Subject: IRS Tax Return Transcript from 06/12/2018
- Link for malware: hxxp[:]//www.dev.klastcarpet[.]com/IRS-TRANSCRIPTS-June-2018-088/8/
- Date/Time: Tuesday, 2018-06-12 18:21 UTC
- Received: from 10.0.0[.]17 ([201.174.80[.]210])
- From: IRS <irsonline@treasury[.]gov> <[removed]@[removed]>
- Subject: IRS Record of Account Transcript
- Link for malware: hxxp[:]//wevik[.]hu/IRS-Accounts-Transcipts-062018-0991/
- Date/Time: Tuesday, 2018-06-12 19:36 UTC
- Received: from 10.0.0[.]33 ([221.163.32[.]101])
- From: Intuit Payroll Services <[removed]@[removed]>
- Subject: Daily Payroll for Jun 12 [mm45957]
- Attachment name: Daily Payroll for Jun 12 [mm45957].pdf
- Attachment name: Daily Payroll for Jun 12 [mm45957].doc
- Date/Time: Tuesday, 2018-06-12 19:40 UTC
- Received: from 10.0.0[.]57 ([221.163.32[.]101])
- From: IRS[.]gov <[removed]@[removed]>
- Subject: IRS Tax Account Transcript
- Link for malware: hxxp[:]//the-grizz[.]com/gallery/g2data/IRS-Tax-Transcipts-062018-01/8/
- Date/Time: Tuesday, 2018-06-12 20:38 UTC
- Received: from ([170.238.239[.]38])
- From: Casee Snook <[removed]@[removed]>
- Subject: Auditor of State - Notification of EFT Deposit
- Link for malware: hxxp[:]//www.2.u0135364.z8[.]ru/ACCOUNT/Customer-Invoice-SB-36047325/
- Date/Time: Tuesday, 2018-06-12 20:46 UTC
- Received: from ([221.163.32[.]101])
- From: Tom Burt <[removed]@[removed]>
- Subject: Payment
- Link for malware: hxxp[:]//www.redridgeumc[.]org/DOC/Services-06-13-18-New-Customer-OC/

Shown above: One of the downloaded (or attached) Word docs.
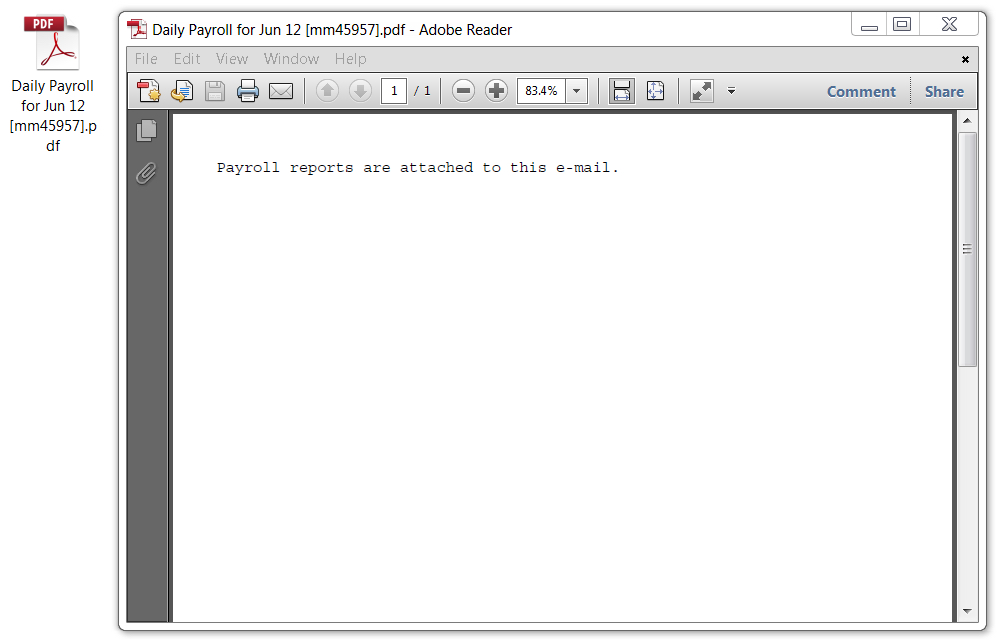
Shown above: The attached PDF file from that one malspam message.
INFECTION TRAFFIC
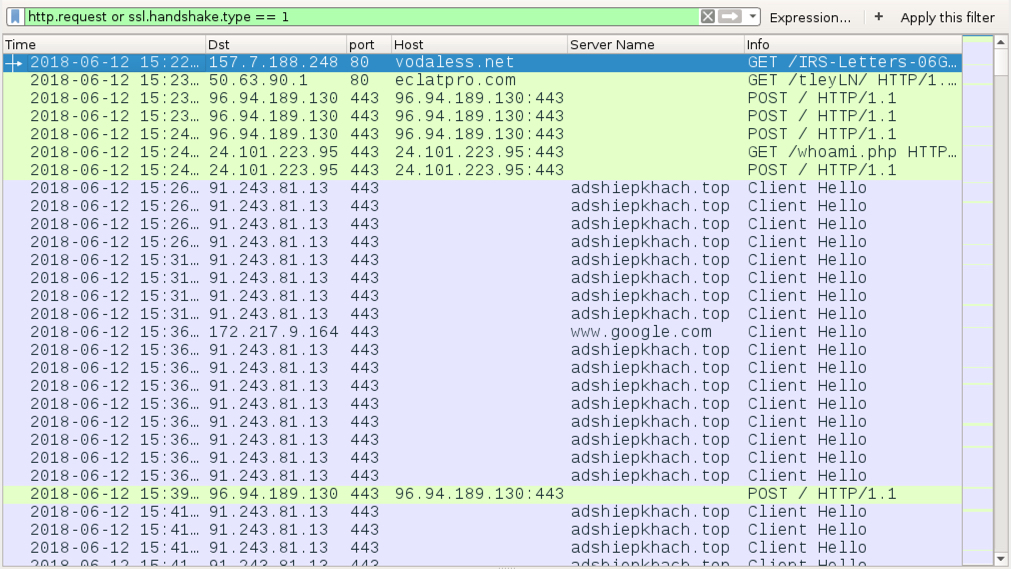
Shown above: Traffic from an infection filtered in Wireshark.
TRAFFIC FROM AN INFECTED WINDOWS HOST:
- 157.7.188[.]248 port 80 - vodaless[.]net - GET /IRS-Letters-06G/90/
- 50.63.90[.]1 port 80 - eclatpro[.]com - GET /tleyLN/
- 96.94.189[.]130 port 443 - 96.94.189[.]130:443 - POST /
- 24.101.223[.]95 port 443 - 24.101.223[.]95:443 - GET /whoami.php
- 24.101.223[.]95 port 443 - 24.101.223[.]95:443 - POST /
- 91.243.81[.]13 port 443 - adshiepkhach[.]top - HTTPS/SSL/TLS traffi caused by Zeus Panda Banker
- port 443 - www.google[.]com HTTP traffic, probable connectivity check by Zeus Panda Banker
SHA256 HASHES
DOWNLOADED WORD DOCUMENTS FROM LINKS IN THE MALSPAM:
- ebf030cd38a70fa41a826b7088087b52efdd4407c4be970dc45ab8faef76abfa - 104,448 bytes
- f7856f18306d10f6092e7d92b9356281924772e1172edf178629315dbb9301f8 - 92,416 bytes
- dbe16dee3023204ea81db1f4e08616a196768747ab83ab4d3a7aac3798299d72 - 119,296 bytes
- 8ec72da4cf9af5fbea85fdb17b2ccf8907f175708646515357408d81162b47b6 - 110,336 bytes
- b7f938aa350836740c0e76952d93cee15abfe803c9bf907664778019c37552e2 - 98,048 bytes
- c59c3380e301afe2d89848495d4f6172c9c4676757cb90bec5c85884b5a48d15 - 104,192 bytes
- 076b70645074ab55b7c0bcd8402b735b2326e37e21b089e2f1f453bddd43cbc9 - 94,976 bytes
- f2e119823ecb7aa1bfc1286c5115061268c68c7e00a1ae824af2f0fa3afe7b4e - 123,392 bytes
- 425e9188fd47060854e19992b264523cd19015da0970d3ae813750d7ab25187b - 91,136 bytes
- 829c31836b32433ad3879ec43f24c3f947496fba59d0f2dcaa7bf43478d6b927 - 123,648 bytes
- 85295d10ca74ba0b7074c5d50f114f3fa0f719a78a464be55474d52832bb04d8 - 96,000 bytes
- 3e0ee7c4e6bf9b8f14a5448b1d2156a8a489ae80b0b9bb6c205b79b2bc93a2e0 - 99,840 bytes
EMOTET EXECUTABLE FILES RETRIEVED BY THE WORD MARCOS:
- 42ea2e697bca96965ee39dd666229438fa433e97451f4c9cd5b6a6fdf105bcf3 - 274,432 bytes
- 8e6abdbee16746ed9871ae0a6717d207d1554b4ff9f86e5e53131438670fa702 - 143,360 bytes
- 91d0f65b0e9f62ccb7817030967cde51c8f4806a8acec6deabec39c7d8adb416 - 143,360 bytes
- ebe4ed8c191c7c09e706d9409b49f559fb8ab85ecf4966963c7f1a434e54e99d - 143,360 bytes
- ece2a89aa4bdb318370bc75458d7d790791d7b46287888d40b555e3b7726b228 - 287,744 bytes
ZEUS PANDA BANKER SEEN DURING EMOTET INFECTION:
- 333aff311b07c5cbedfb618ff902b0dd663c0ba50b2dc8a2a590e9409cb9bc3c - 275,456 bytes
Click here to return to the main page.
