2018-06-19 - MALSPAM PUSHES EMOTET AND EMOTET PUSHES ICEDID
ASSOCIATED FILES:
- 2018-06-19-Emotet-malspam-36-examples.zip 475 kB (474,707 bytes)
- 2018-06-19-Emotet-infection-with-IcedID.pcap.zip 1.97 MB (1,965,579 bytes)
- 2018-06-19-malware-and-artifacts-from-Emotet-infection-with-IcedID.zip 930 kB (930,148 bytes)
NOTES:
- Emotet is still loading IcedID banking malware, like we saw yesterday.
EMAILS
DATE/TIME:
- Tuesday, 2018-06-19 as early as 10:58 through at least 22:10 UTC
DATA FROM 36 EMAIL EXAMPLES:
- Received: from 10.0.0[.]3 ([81.110.229[.]147])
- Received: from 10.0.0[.]5 ([197.188.221[.]68])
- Received: from 10.0.0[.]6 ([114.79.134[.]51])
- Received: from 10.0.0[.]6 ([221.163.32[.]101])
- Received: from 10.0.0[.]8 ([89.207.118[.]10])
- Received: from 10.0.0[.]9 ([190.164.138[.]172])
- Received: from 10.0.0[.]11 ([190.56.75[.]114])
- Received: from 10.0.0[.]12 ([190.85.64[.]22])
- Received: from 10.0.0[.]17 ([89.145.208[.]77])
- Received: from 10.0.0[.]17 ([221.163.32[.]101])
- Received: from 10.0.0[.]18 ([84.96.103[.]131])
- Received: from 10.0.0[.]18 ([111.119.192[.]38])
- Received: from 10.0.0[.]19 ([221.163.32[.]101])
- Received: from 10.0.0[.]21 ([89.24.242[.]103])
- Received: from 10.0.0[.]24 ([183.82.115[.]48])
- Received: from 10.0.0[.]24 ([189.165.179[.]105])
- Received: from 10.0.0[.]27 ([14.51.231[.]1])
- Received: from 10.0.0[.]28 ([37.47.12[.]205])
- Received: from 10.0.0[.]28 ([201.195.122[.]95])
- Received: from 10.0.0[.]30 ([213.196.137[.]6])
- Received: from 10.0.0[.]31 ([85.114.204[.]220])
- Received: from 10.0.0[.]36 ([212.156.91[.]142])
- Received: from 10.0.0[.]36 ([221.163.32[.]101])
- Received: from 10.0.0[.]37 ([194.168.211[.]218])
- Received: from 10.0.0[.]41 ([170.80.16[.]51])
- Received: from 10.0.0[.]42 ([176.22.253[.]218])
- Received: from 10.0.0[.]42 ([186.177.75[.]205])
- Received: from 10.0.0[.]45 ([36.34.121[.]154])
- Received: from 10.0.0[.]48 ([51.52.82[.]24])
- Received: from 10.0.0[.]49 ([14.51.231[.]1])
- Received: from 10.0.0[.]52 ([196.41.199[.]186])
- Received: from 10.0.0[.]54 ([14.51.231[.]1])
- Received: from 10.0.0[.]59 ([80.93.47[.]83])
- Received: from 10.0.0[.]59 ([101.99.59[.]114])
- Received: from 10.0.0[.]60 ([41.13.88[.]44])
- Received: from 10.0.0[.]60 ([119.153.172[.]143])
SPOOFED SENDING ADDRESSES:
- From: Amy Brink <[removed]@[removed]>
- From: Baljinder Singh <[removed]@[removed]>
- From: Bill Vanderford <[removed]@[removed]>
- From: Brad Smale <[removed]@[removed]>
- From: Brouillard, Jon <[removed]@[removed]>
- From: Cecilia Solomon <[removed]@[removed]>
- From: Dianna York <[removed]@[removed]>
- From: Eddie Carter <[removed]@[removed]>
- From: Full Name <[removed]@[removed]>
- From: Graham Young <[removed]@[removed]>
- From: InCorp (Compliance) <[removed]@[removed]>
- From: Intervia Transportes <[removed]@[removed]>
- From: Intuit <[removed]@[removed]>
- From: Intuit <[removed]@[removed]>
- From: Intuit Online Payroll Support Team <[removed]@[removed]>
- From: Intuit Online Payroll Support Team <[removed]@[removed]>
- From: Intuit Payroll <[removed]@[removed]>
- From: Intuit Payroll Services <[removed]@[removed]>
- From: IRS <Transcript@treasury.gov> <[removed]@[removed]>
- From: IRS Online <[removed]@[removed]>
- From: IRS.gov <[removed]@[removed]>
- From: Jeff McGuire <[removed]@[removed]>
- From: Joanna Muniz <[removed]@[removed]>
- From: Joe Duplan <[removed]@[removed]>
- From: Jordan Leichty <[removed]@[removed]>
- From: Joseph Zita <[removed]@[removed]>
- From: Laura McCraven <[removed]@[removed]>
- From: Lesa Pujol <[removed]@[removed]>
- From: Letty Turner <[removed]@[removed]>
- From: Luis Zapata <[removed]@[removed]>
- From: Micheal Martin <[removed]@[removed]>
- From: Minuteman Press Bohemia <[removed]@[removed]>
- From: Nick Bozzacco <[removed]@[removed]>
- From: Owens, Ashley <[removed]@[removed]>
- From: Robert James <[removed]@[removed]>
- From: Valentin Lucero <[removed]@[removed]>
SUBJECT LINES:
- Subject: 52100758447015
- Subject: ACCOUNT#61631831-Intervia Transportes
- Subject: ACCOUNT#949501-Nick Bozzacco
- Subject: ACCOUNT#9739040-Owens, Ashley
- Subject: Auditor of State - Notification of EFT Deposit
- Subject: B4 2018 Payroll
- Subject: Bill Vanderford: 07708
- Subject: Direct Deposit Notice
- Subject: Eddie Carter Past Due invoice
- Subject: eftps payroll 751309
- Subject: HRI Monthly Invoice
- Subject: Invoice 06.19.18
- Subject: Invoice 2301321
- Subject: Invoice 577360 from Dianna York
- Subject: Invoice 9333482
- Subject: Invoice from Cecilia Solomon
- Subject: Invoices
- Subject: IRS Record of Account Transcript from June 20, 2018
- Subject: IRS Tax Account Transcript
- Subject: IRS Verification of Non-filing Letter
- Subject: J8 2018 Payroll
- Subject: Lesa Pujol Invoice # 34301969526 06/19/2018
- Subject: Luis Zapata Invoice # 0571582518 06/20/2018
- Subject: New Invoice / KZ47787 / OP# 64519
- Subject: New Invoice / SS10118 / ZM# 14318
- Subject: New Payroll Co.
- Subject: Payroll Tax Payment
- Subject: Please pull invoice 07961
- Subject: Please pull invoice 94405
- Subject: Services / 06.19.18 / New Customer / KU
- Subject: Services / 06.19.18 / New Customer / YD
- Subject: tracking number and invoice of your order
- Subject: Valentin Lucero invoice
ATTACHMENT NAMES FROM EMAILS WITHOUT LINKS:
- Attachment name: 52100758447015.doc
- Attachment name: 52100758447015.pdf
- Attachment name: B4 2018 Payroll.doc
- Attachment name: B4 2018 Payroll.pdf
- Attachment name: eftps payroll 751309.doc
- Attachment name: eftps payroll 751309.pdf
- Attachment name: IRS_2815754_06202018.doc
- Attachment name: Tax Account Transcript.pdf
- Attachment name: J8 2018 Payroll.doc
- Attachment name: J8 2018 Payroll.pdf
- Attachment name: New Payroll Co..doc
- Attachment name: New Payroll Co..pdf
- Attachment name: Payroll Tax Payment.doc
- Attachment name: Payroll Tax Payment.pdf
TRAFFIC
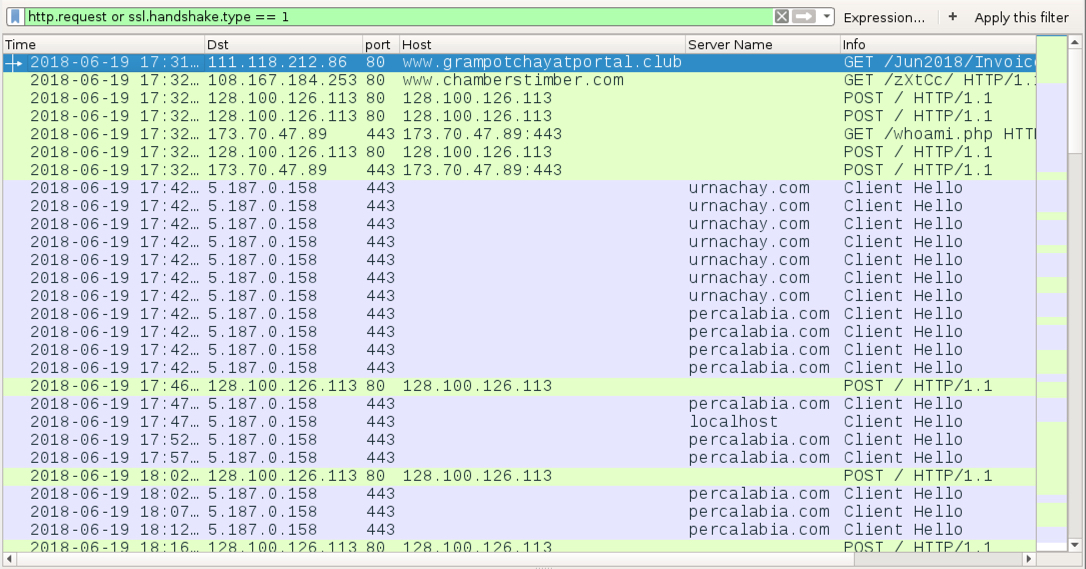
Shown above: Traffic from an Emotet infection filtered in Wireshark also shows IcedID traffic.
LINKS FROM EMAILS WITHOUT ATTACHMENTS FOR THE INITIAL WORD DOCUMENT:
- hxxp[:]//frcs[.]com[.]br/New-Order-Upcoming/HRI-Monthly-Invoice/
- hxxp[:]//www.740745[.]ru/DOC/Pay-Invoice/
- hxxp[:]//www.agencjainternauta[.]pl/Client/Invoice-7464068889-06-19-2018/
- hxxp[:]//www.akademiawandy[.]pl/ACCOUNT/Invoice-007258077-061918/
- hxxp[:]//www.alexdejesus[.]us/Statement/Invoice/
- hxxp[:]//www.alkdev.thechronostime[.]com/Client/Past-Due-invoice/
- hxxp[:]//www.armanitour[.]com/Client/84677/
- hxxp[:]//www.arthysexpress[.]com[.]br/ACCOUNT/Invoice-06739/
- hxxp[:]//www.bynoet[.]com/Client/Direct-Deposit-Notice/
- hxxp[:]//www.colinhardy[.]com/multimedia/Statement/Invoice-174348/
- hxxp[:]//www.conscious-investor[.]com/multimedia/Statement/Invoice/
- hxxp[:]//www.da-pietro[.]com/ACCOUNT/Payment/
- hxxp[:]//www.dajabon24horas[.]com/IRS-Transcripts-046/3/
- hxxp[:]//www.danzaclassicamilano[.]com/Payment-and-address/HRI-Monthly-Invoice/
- hxxp[:]//www.digitalsewapoint[.]com/Jun2018/Pay-Invoice/
- hxxp[:]//www.dradarlinydiaz[.]com/OVERDUE-ACCOUNT/Services-06-19-18-New-Customer-ST/
- hxxp[:]//www.drive.lemeunier[.]fr/Client/Invoice-3986739/
- hxxp[:]//www.e-market[.]com[.]ua/IRS-TRANSCRIPTS-07M/65/
- hxxp[:]//www.exploretour[.]in/FILE/Auditor-of-State-Notification-of-EFT-Deposit/
- hxxp[:]//www.ezfastcashpersonalloans[.]com/OVERDUE-ACCOUNT/New-Invoice-OI5452-BG-6486/
- hxxp[:]//www.gcardriving[.]com/New-Order-Upcoming/New-Invoice-IS34079-DO-04649/
- hxxp[:]//www.gojukai[.]co/INVOICE-STATUS/HRI-Monthly-Invoice/
- hxxp[:]//www.grampotchayatportal[.]club/Jun2018/Invoice-6750042/
- hxxp[:]//www.gregsmoneyreview[.]com/Payment-and-address/Please-pull-invoice-21639/
- hxxp[:]//www.hjocreations[.]com/ACCOUNT/tracking-number-and-invoice-of-your-order/
- hxxp[:]//www.homeandtell[.]com/OVERDUE-ACCOUNT/Invoice-00663986061-06-19-2018/
- hxxp[:]//www.khaolakstationtour[.]com/DOC/Invoice-343147/
- hxxp[:]//www.krasr.skrollx[.]com[.]np/Purchase/Invoice-7247579851-06-19-2018/
- hxxp[:]//www.papabubbleksa[.]com/Client/Pay-Invoice/
URLS GENERATED BY WORD MACROS FOR EMOTET MALWARE BINARY:
- hxxp[:]//denaros[.]pl/Data/ZA4l/
- hxxp[:]//ontracksolutions[.]com/767Egih/
- hxxp[:]//www.2ip[.]ru.net/Rf53U/
- hxxp[:]//www.alifhost[.]com/6Msp/
- hxxp[:]//www.bandicapital[.]com/c8CouZB/
- hxxp[:]//www.chamberstimber[.]com/zXtCc/
- hxxp[:]//www.corapersianas[.]com/h3ZJ/
- hxxp[:]//www.dekhoresellers.tk/PZlh/
- hxxp[:]//www.disrepairclaims[.]com/haLhb0U/
- hxxp[:]//www.donloadlagu[.]co/EcR7wcI/
- hxxp[:]//www.duanbatdongsanvincity[.]com/xwe85du/
- hxxp[:]//www.geo-sign[.]com/cvXDJ/
- hxxp[:]//www.gorkemgursoy[.]com/atElK90/
- hxxp[:]//www.ismetotokaporta[.]com/wROkQ/
- hxxp[:]//www.kirpich-servis16[.]ru/dz5QD/
EMOTET INFECTION TRAFFIC FROM MY INFECTED LAB HOST:
- 111.118.212[.]86 port 80 - www.grampotchayatportal[.]club - GET /Jun2018/Invoice-6750042/
- 108.167.184[.]253 port 80 - www.chamberstimber[.]com - GET /zXtCc/
- 128.100.126[.]113 port 80 - 128.100.126[.]113 - POST /
- 173.70.47[.]89 port 443 - 173.70.47[.]89:443 - GET /whoami.php
- 173.70.47[.]89 port 443 - 173.70.47[.]89:443 - POST /
- 47.188.131[.]94 port 443 - 47.188.131[.]94:443 - POST /
- 76.72.225[.]30 port 465 - 76.72.225[.]30:465 - POST /
- 164.160.161[.]118 port 8080 - 164.160.161[.]118:8080 - POST /
- 46.4.100[.]178 port 8080 - 46.4.100[.]178:8080 - POST /
- 23.239.2[.]11 port 8080 - 23.239.2[.]11:8080 - POST /
- 66.76.26[.]33 port 8080 - 66.76.26[.]33:8080 - POST /
- 24.217.117[.]217 port 80 - 24.217.117[.]217 - POST /
- 75.152.52[.]109 port 8080 - 75.152.52[.]109:8080 - POST /
- 217.91.43[.]150 port 7080 - 217.91.43[.]150:7080 - POST /
- 189.236.94[.]20 port 995 - 189.236.94[.]20:995 - POST /
- 24.119.116[.]230 port 990 - 24.119.116[.]230:990 - POST /
- 96.94.189[.]130 port 443 - 96.94.189[.]130:443 - POST /
- 72.45.212[.]62 port 8080 - 72.45.212[.]62:8080 - POST /
- 70.184.125[.]132 port 8080 - 70.184.125[.]132:8080 - POST /
- 206.255.140[.]203 port 80 - 206.255.140[.]203 - POST /
- 121.50.43[.]110 port 8080 - TCP SYN packets, but no response from the server
- 216.105.170[.]139 port 4143 - TCP SYN packets, but no response from the server
- 46.38.238[.]8 port 8080 - TCP SYN packets, but no response from the server
- 178.62.103[.]94 port 8080 - TCP SYN packets, but no response from the server
- 78.47.182[.]42 port 8080 - TCP SYN packets, but no response from the server
- 184.186.78[.]177 port 80 - TCP SYN packets, but no response from the server
- 209.64.82[.]90 port 465 - TCP SYN packets, but no response from the server
- 194.88.246[.]242 port 443 - TCP SYN packets, but no response from the server
ICEDID TRAFFIC FROM MY INFECTED LAB HOST:
- 5.187.0[.]158 port 443 - urnachay[.]com - HTTPS/SSL/TLS traffic
- 5.187.0[.]158 port 443 - percalabia[.]com - HTTPS/SSL/TLS traffic
- 5.187.0[.]158 port 443 - localhost - HTTPS/SSL/TLS traffic
MALWARE
MALWARE RETRIEVED FROM MY INFECTED WINDOWS HOST:
- SHA256 hash: f315565e9c9b5b80b563a607e590043cc635b06cc0fbffc790bbd8d5d196445f
File size: 110,080 bytes
File name: BVS-INV-9563373426884.doc (random file name)
File description: downloaded Word doc with macro for Emotet
- SHA256 hash: f6593f554c18488432c63b6a75f94cce4716b108bc98a6a5ed8e5f4d3d7cfc09
File size: 126,976 bytes
File location: C:\Users\[username]\AppData\Local\Microsoft\Windows\[random characters].exe
File description: Emotet malware binary
- SHA256 hash: 3a39f8e54b67df24588649974e5535f1f061facfc46a85cc374004277ada1bce
File size: 618,496 bytes
File location: C:\Users\[username]\AppData\Local\Microsoft\[random characters].exe
File description: IcedID banking malware downloaded by Emotet
SHA256 HASHES FOR ATTACHED WORD DOCS WITH MACROS FOR EMOTET:
- fb54ddaebb4f790021fda660e02d49c66cab5a46a017b502b271901363e9996d - 52100758447015.doc
- 1cf030bcdb50f7b4922a46ffc6ce21c7c2df04abfef9efd3c2472cbaffc522c3 - B4 2018 Payroll.doc
- 7b696aac4ddf28871435c9266fd58b1c46a9f8ae4ee9355409523d8a66e1aaf7 - IRS_2815754_06202018.doc
- 91c7ceb775de65af8655cfcfe14b3c4a2d1467c85b7d2d359801cc0d82af2604 - J8 2018 Payroll.doc
- d0613e9f2d8b5fce56e12790cf3c85df58275983ca8a9cf0805c938e981927cb - New Payroll Co..doc
- 024fa6958f0c60ce90ec87c349c3a010e4301927c66333c2fc167c165dcb5142 - Payroll Tax Payment.doc
- 024fa6958f0c60ce90ec87c349c3a010e4301927c66333c2fc167c165dcb5142 - eftps payroll 751309.doc
SHA256 HASHES FOR ATTACHED PDF FILES (NOT MALICIOUS):
- 6f943dba193993272bd74b98daf3897e99452b97008e66d9e25819edb8893418 - 52100758447015.pdf
- 3f5df1d296ec9820bda8f0ce78e6e215dee85b86f5b73c0ceff828dca68795a6 - B4 2018 Payroll.pdf
- e9e083859e99cf25df4af24a9e68afc241b9437ee644e8c06954858ea1ba6923 - J8 2018 Payroll.pdf
- be5378b850ae2353b7b8f92e9f487de94a580ebe89823923ebfe61b1aa42cfa5 - New Payroll Co..pdf
- dbe5b8483034772fd9a55492f498bbcf5bb9bba0fcd785df771371bae8b580db - Payroll Tax Payment.pdf
- 90444004309e799c55abdcb76e62747182972ec701d5acaae507411911877679 - eftps payroll 751309.pdf
- 2fcaae6cac9508c7b0c2180fcb6054aaefe37aa3cdc03a592fde1ef35298efc6 - Tax Account Transcript.pdf
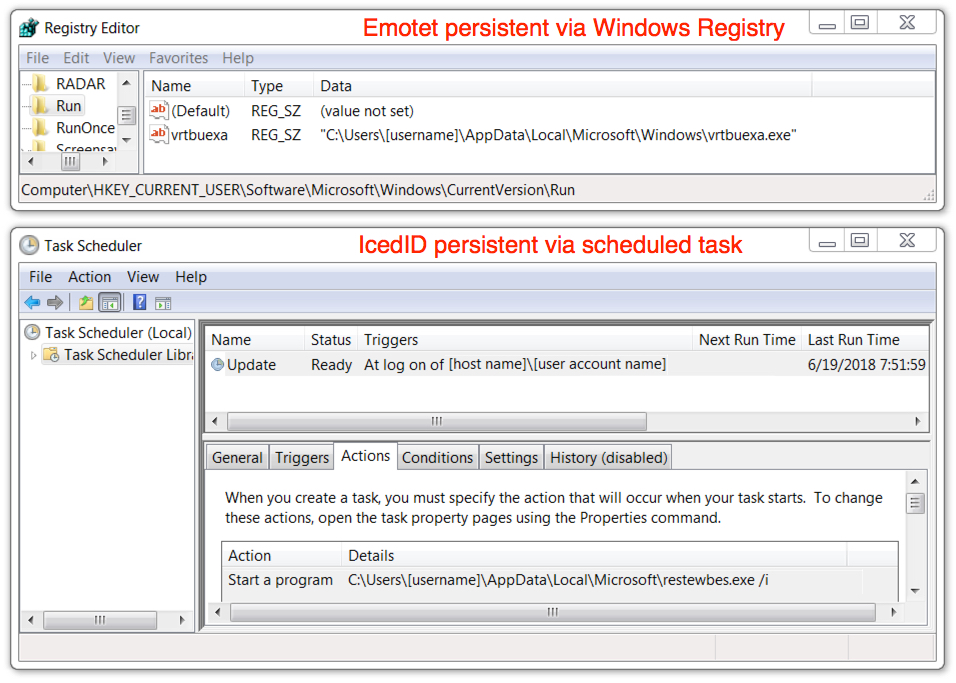
Shown above: Malware from this infection persistent on the infected Windows host.
Click here to return to the main page.
