2018-07-05 - FAKE UPDATER TRAFFIC (CHTHONIC, DRIDEX, AND NETSUPPORT RAT)
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2018-07-05-fake-updater-traffic-4-pcaps-and-1-saz.zip 33.7 MB (33,724,937 bytes)
- 2018-07-05-fake-updater-malware-and-artifacts.zip 3.9 MB (3,910,507 bytes)
NOTES:
- Not much has changed in this campaign since an in-depth write-up about it back in April 2018 on the Malwarebytes blog (link).
- Special thanks to baberpervez2, who's kept me updated on recent compromised sites from this campaign.
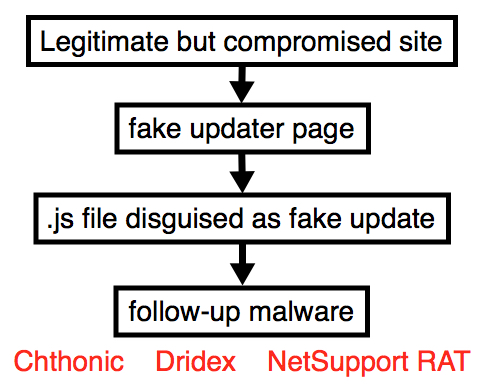
Shown above: Flow chart for this chain of events.
DETAILS
FAKE UPDATER PAGE TRAFFIC FOR .JS FILE DOWNLOAD: - 93.95.100[.]178 port 443 - four.sineadhollywoodnutt[.]com - fake update pages (Chrome, Firefox, Flash) over HTTPS - Dropbox link over HTTPS for initial .js file (fake Chrome, Firefox, or Flash update) EXAMPLES OF CALLBACK TRAFFIC GENERATED BY THE .JS FILE: - 93.95.100[.]138 port 80 - 7bb3e96a.login3.kimbrelelectric[.]com - POST /blank.gif - 93.95.100[.]138 port 80 - 7e1729f7.login3.kimbrelelectric[.]com - POST /blank.gif - 93.95.100[.]138 port 80 - 9dba52bd.login3.kimbrelelectric[.]com - POST /blank.gif - 93.95.100[.]138 port 80 - e4f9b946.login3.kimbrelelectric[.]com - POST /blank.gif POST-INFECTION TRAFFIC FROM FOLLOW-UP MALWARE ON 2018-07-04 (CHTHONIC): - 42.21.248[.]138 port 80 - atomary[.]bit - POST /en/ - 42.21.248[.]138 port 80 - atomary[.]bit - POST /en/www/ - 46.217.255[.]66 port 80 - trumplines[.]bit - POST /en/ - 79.121.73[.]1 port 80 - trumplines[.]bit - POST /en/ - 86.106.200[.]105 port 80 - trumplines[.]bit - POST /en/ - 112.72.10[.]10 port 80 - trumplines[.]bit - POST /en/ - 124.43.17[.]103 port 80 - trumplines[.]bit - POST /en/ - 143.208.165[.]42 port 80 - trumplines[.]bit - POST /en/ - various public IP addresses - TCP port 53 - DNS queries for atomary[.]bit, letit2[.]bit, siteeu[.]bit, and trumplines[.]bit - 204.16.247[.]108 port 80 - siteeu[.]bit - attempted TCP connections, but no response from the server - All DNS queries for letit2[.]bit returned "Server failure" message from the DNS servers POST-INFECTION TRAFFIC FROM FOLLOW-UP MALWARE IN THE 1ST RUN ON 2018-07-05 (DRIDEX): - 46.105.131[.]66 port 443 - SSL/TLS post-infection traffic - 67.206.193[.]182 port 443 - SSL/TLS post-infection traffic - 69.14.75[.]158 port 443 - SSL/TLS post-infection traffic - 76.79.62[.]150 port 443 - SSL/TLS post-infection traffic - 80.2.118[.]90 port 443 - SSL/TLS post-infection traffic - 81.130.208[.]120 port 443 - SSL/TLS post-infection traffic - 87.114.93[.]29 port 8443 - SSL/TLS post-infection traffic - 117.121.216[.]226 port 4443 - SSL/TLS post-infecion traffic - 185.236.77[.]228 port 443 - SSL/TLS post-infection traffic - 195.123.214[.]147 port 443 - SSL/TLS post-infection traffic - 206.15.68[.]148 port 443 - SSL/TLS post-infection traffic - 207.47.95[.]202 port 443 - SSL/TLS post-infection traffic POST-INFECTION TRAFFIC FROM FOLLOW-UP MALWARE IN THE 2ND AND 3RD RUNS ON 2018-07-05: - 93.179.68[.]25 port 443 - desjardinscourriel818654[.]pw - Downloaded components for NetSupport Manager RAT over HTTPS - 46.19.142[.]178 port 2259 - POST hxxp:[/]/46.19.142[.]178/fakeurl.htm - Netsupport Manager RAT callback traffic ASSOCITED MALWARE: - SHA256 hash: aba013bc68eb5e5c9c5a1aca686f2b56bd3fd558619217d70d22f3f3bdd4d4cc - File size: 39,000 bytes - File name: flashplayer_37.3.31_plugin.js - File description: fake Flash update from Dropbox link generated by fake Flash updater page on 2018-07-04 - SHA256 hash: 917a0891f2d97f0a574b24a285f5c99e59640c0cb00d39ff57ea73a9532c2d5f - File size: 43,300 bytes - File name: Chrome_72.3.32.js - File description: fake Chrome update from Dropbox link generated by fake Chrome updater page on 2018-07-05 - SHA256 hash: 12d1bf46e8a8cc31ec30815a62d863dd9bb92f5c79497f3a94d9d46a6b0742a2 - File size: 40,083 bytes - File name: Firefox_67.3.10.js - File description: fake Firefox update from Dropbox link generated by fake Firefox updater page on 2018-07-05 - SHA256 hash: beaed069bd9a361c9b5970e524ce39dbb30c4ed7c86542ccd6d737df2b676ba7 - File size: 39,175 bytes - File name: flashplayer_37.3.36_plugin.js - File description: fake Flash update from Dropbox link generated by fake Flash updater page on 2018-07-05 - SHA256 hash: d519c1659a884e541c52d8eb1c5135720315f3a31ac8bfbabc2a58e46c9b96e5 - File size: 374,272 bytes - File description: Final malware retrieved by .js file on 2018-07-04, Chthonic banking malware - SHA256 hash: 312f4107ff37dc988d99c5f56178708bb74a3906740cff4e337c0dde8f1e151d - File size: 196,608 bytes - File location: C:\Users\[username]\AppData\Roaming\52NedQ\irftp.exe - File description: Legitimate Microsoft system file for Infrared File Transfer Application. Normally at C:\Windows\System32\irftp.exe. Loads any file named WTSAPI32.DLL in the same directory. - SHA256 hash: e8a7bc669c36736e9694bdf280e0a51660e3b5a37de5a5b5b6985200b8a985a7 - File size: 630,784 bytes - File location: C:\Users\[username]\AppData\Roaming\52NedQ\WTSAPI32.dll - File description: Malicious Dridex DLL on 2018-07-05 loaded by legitimate file irftp.exe - SHA256 hash: cada4b19791441373580919fff89623489c7a1737857760b96cc3f0a08db8d59 - File size: 923,936 bytes - File location: C:\Users\[username]\AppData\Roaming\XN1vw\nvvsvc.exe - File description: Legitimate executable for NVIDIA Driver Helper Service, version 334.89. Normally at C:\Windows\System32\nvvsvc.exe. Loads any file named WTSAPI32.DLL in the same directory. - SHA256 hash: 22523b8311f1c70ad413c94eaf9a7cde8ca4c4661211ce8181e497ca0f530fcb - File size: 630,784 bytes - File location: C:\Users\[username]\AppData\Roaming\XN1vw\WTSAPI32.dll - File description: Malicious Dridex DLL on 2018-07-05 loaded by legitimate file irftp.exe - SHA256 hash: e914cce211dd9bfa331885d8176736059583906c15bd1b59391f61338ec3b55d - File size: 73,205 bytes - File location: C:\Users\[username]\AppData\Local\Temp\Update.js - File description: .js file used to retrieve the NetSupport Manager RAT components on 2018-07-05 - SHA256 hash: 4d24b359176389301c14a92607b5c26b8490c41e7e3a2abbc87510d1376f4a87cd - File size: 105,848 bytes - File location: C:\Users\[username]\AppData\Roaming\CodeIntegrity\client32.exe - File description: Executable for NetSupport Manger RAT on 2017-08-05. Not inherently malicious.
IMAGES
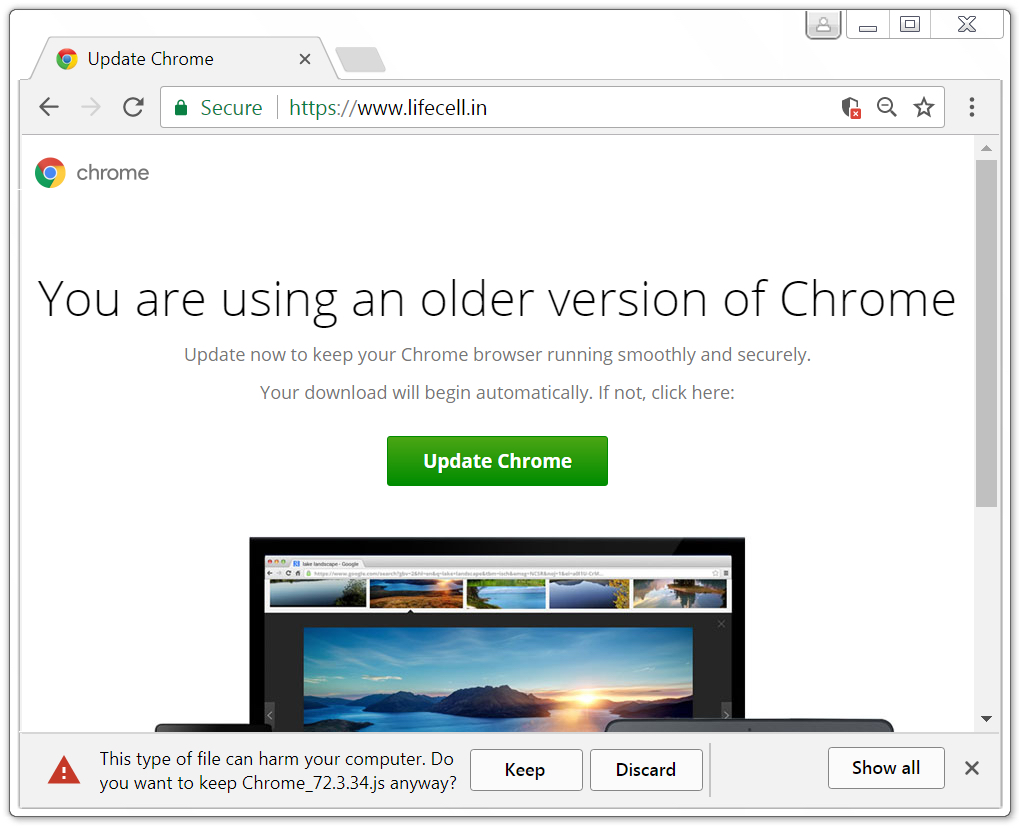
Shown above: Running across an infected website when using Chrome.
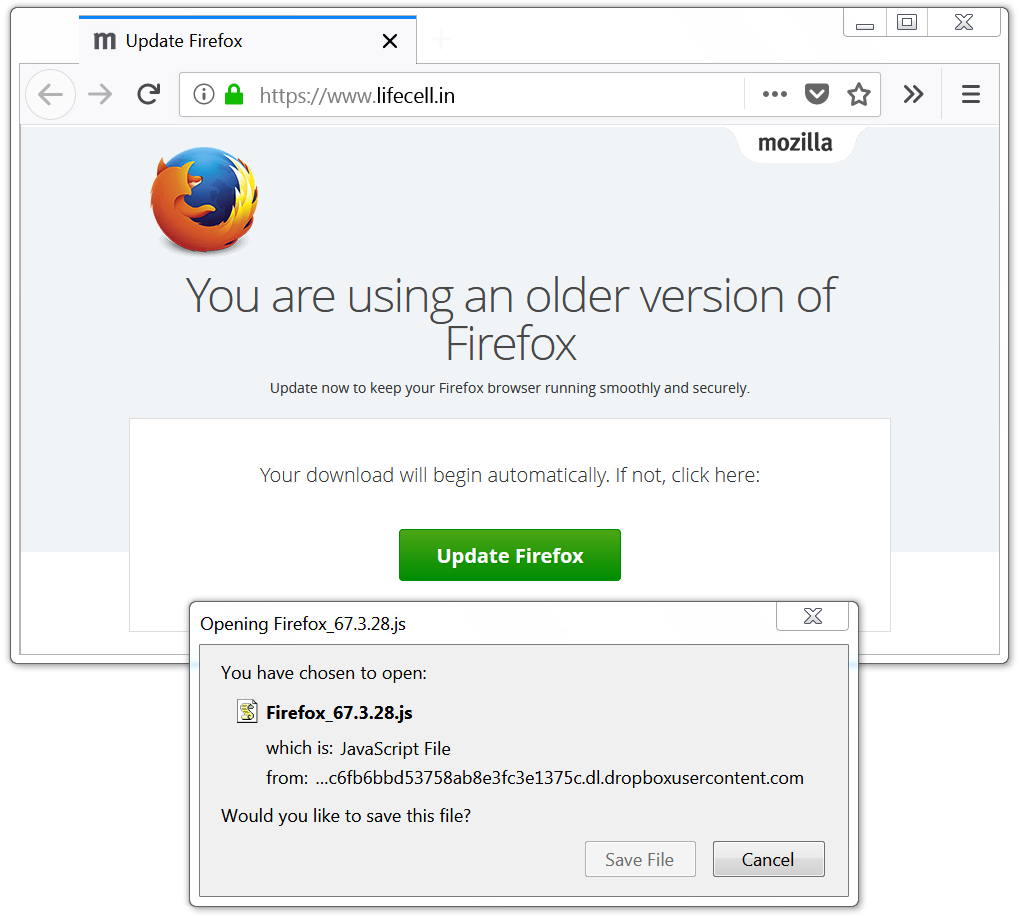
Shown above: Running across an infected website when using Firefox.
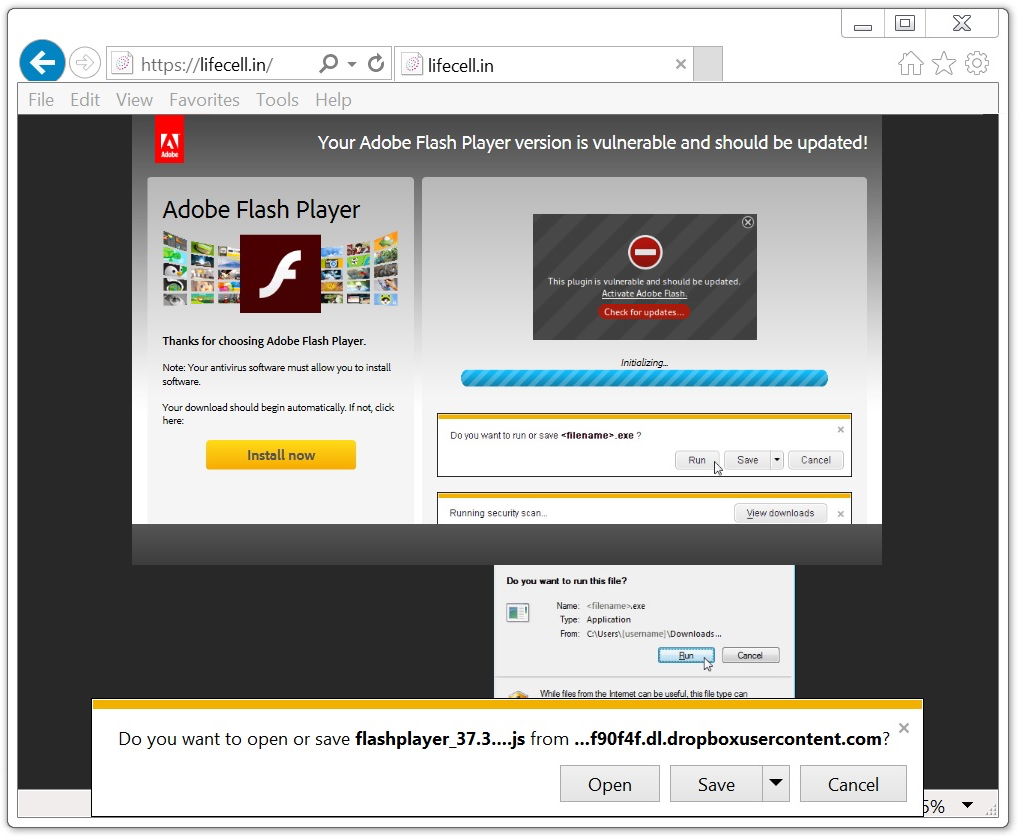
Shown above: Running across an infected website when using Internet Explorer.
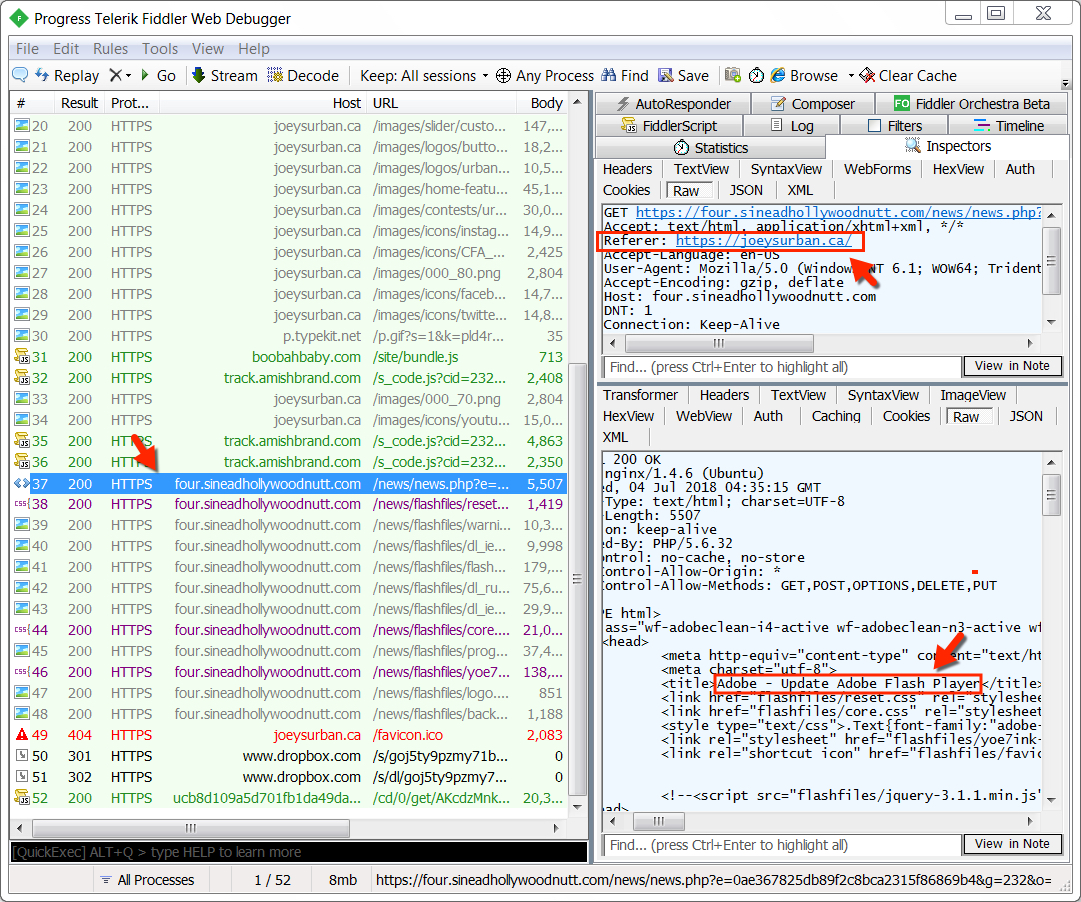
Shown above: Info from a Fiddler web proxy capture showing the HTTPS traffic.
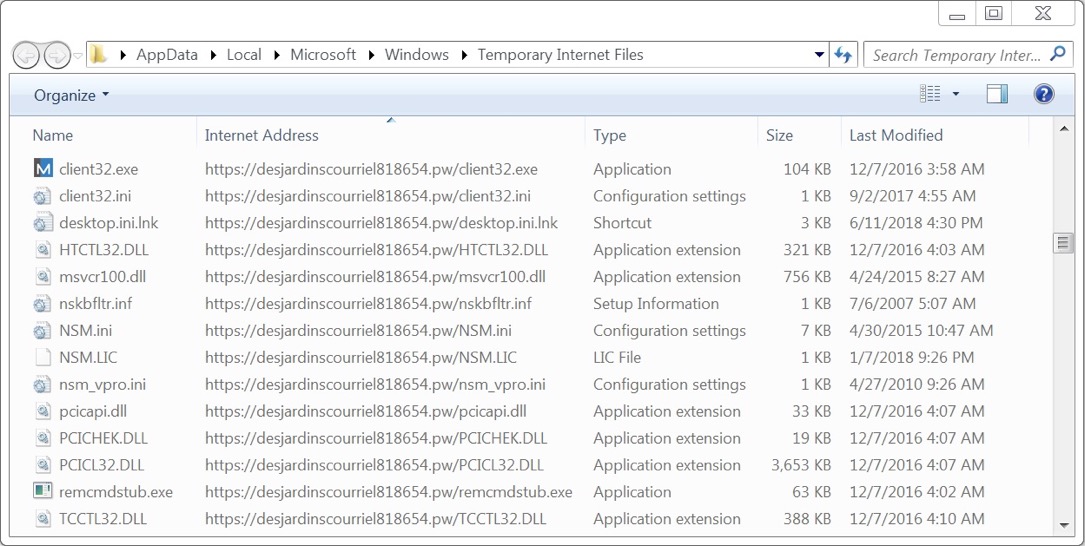
Shown above: Some HTTPS traffic when the NetSupport Manager RAT was sent.
Click here to return to the main page.