2018-08-17 - EMOTET INFECTION WITH TRICKBOT --> TRICKBOT SPREADS TO DC
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2018-08-17-Emotet-infection-with-Trickbot.pcap.zip 12.7 MB (12,686,614 bytes)
- 2018-08-17-malware-and-artifacts-from-Emotet-and-Trickbot.zip 5.2 MB (5,204,709 bytes)
NOTES:
- In my example, the follow-up Trickbot spread from my infected client (Alonzo-PC on 172.16.8[.]205) to its domain controller (Smokejacks-DC on 172.16.8[.]5).
- Looks like Trickbot updated its method of propagation from the client to the DC--the first time I've seen this method used by Trickbot.
- Before, I would clearly see the Trickbot binary sent over SMB from the infected client to the DC.
- Check here for an example of the way Trickbot moved to the DC previously.
- Today, the infected client used traffic over TCP port 445 to cause the DC to retrieve a Trickbot binary over HTTP to infect itself with.
- I'm not sure of the exact nature of this new Trickbot propagation, but you can see it in the pcap as shown in the images section below.
- I've included Trickbot's "Modules" directory from my infected Windows client in today's malware archive, in case anyone wants to dig deeper.
WEB TRAFFIC BLOCK LIST
Indicators are not a block list. If you feel the need to block web traffic, I suggest the following URLs and partial URLs:
- hxxp[:]//omlinux[.]com/889YJN/PAYROLL/Personal
- hxxp[:]//news.digirook[.]com/OH7l
- hxxp[:]//75.80.225[.]46:8443/whoami.php
- hxxp[:]//213.183.63[.]124/worming.png
- hxxp[:]//213.183.63[.]124/table.png
- hxxp[:]//213.183.63[.]124/radiance.png
- hxxp[:]//213.183.63[.]124/toler.png
- hxxp[:]//115.74.177[.]42:8082/del53/
- hxxp[:]//115.74.177[.]42:8082/jim292/
TRAFFIC
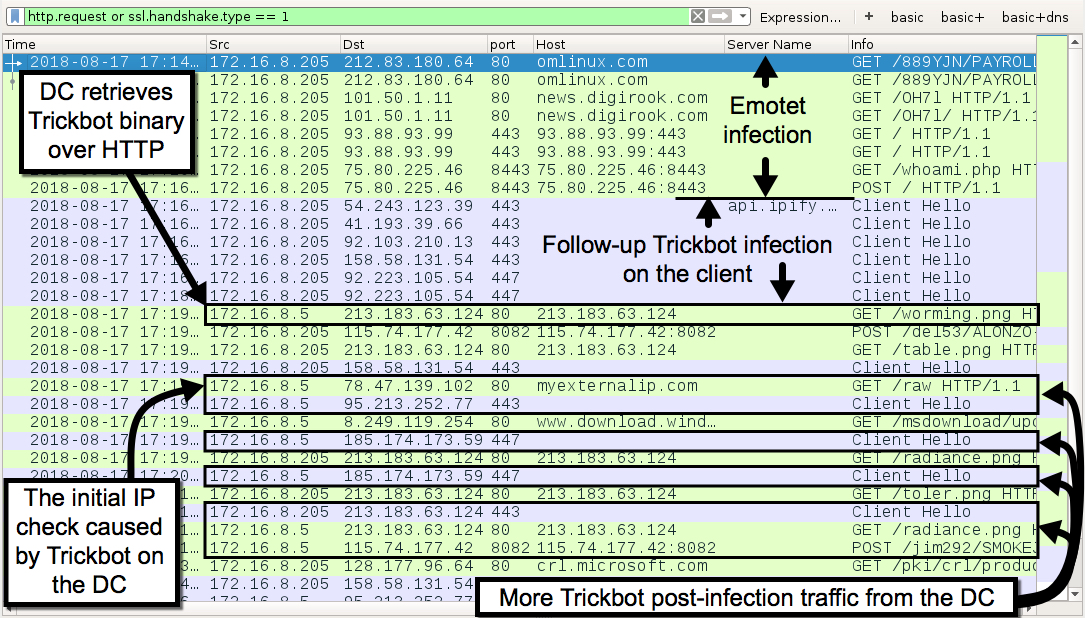
Shown above: Traffic from the infection filtered in Wireshark.
INITIAL EMOTET INFECTION TRAFFIC:
- 212.83.180[.]64 port 80 - omlinux[.]com - GET /889YJN/PAYROLL/Personal
- 212.83.180[.]64 port 80 - omlinux[.]com - GET /889YJN/PAYROLL/Personal/
- 101.50.1[.]11 port 80 - news.digirook[.]com - GET /OH7l
- 101.50.1[.]11 port 80 - news.digirook[.]com - GET /OH7l/
- 203.94.66[.]109 port 8080 - attempted TCP connections but no response from the server
- 93.88.93[.]99 port 443 - 93.88.93[.]99:443 - GET /
- 68.187.50[.]160 port 80 - attempted TCP connections but no response from the server
- 75.80.225[.]46 port 8443 - 75.80.225[.]46:8443 - GET /whoami.php
- 75.80.225[.]46 port 8443 - 75.80.225[.]46:8443 - POST /
TRICKBOT INFECTION TRAFFIC CAUSED BY THE EMOTET INFECTION:
- port 443 - api.ipify[.]org - IP address check by the infected Windows client over HTTPS
- port 80 - myexternalip[.]com - GET /raw (IP address check by the infected DC)
- 41.193.39[.]66 port 443 - HTTPS/SSL/TLS traffic
- 92.103.210[.]13 port 443 - HTTPS/SSL/TLS traffic
- 92.223.105[.]54 port 447 - HTTPS/SSL/TLS traffic
- 95.213.252[.]77 port 443 - HTTPS/SSL/TLS traffic
- 158.58.131[.]54 port 443 - HTTPS/SSL/TLS traffic
- 185.174.173[.]59 port 447 - HTTPS/SSL/TLS traffic
- 213.183.63[.]124 port 443 - HTTPS/SSL/TLS traffic
- 213.183.63[.]124 port 80 - 213.183.63[.]124 - GET /worming.png
- 213.183.63[.]124 port 80 - 213.183.63[.]124 - GET /table.png
- 213.183.63[.]124 port 80 - 213.183.63[.]124 - GET /radiance.png
- 213.183.63[.]124 port 80 - 213.183.63[.]124 - GET /toler.png
- 115.74.177[.]42 port 8082 - 115.74.177[.]42:8082 - POST /del53/ALONZO-PC_W617601.[string of hex characters]/90
- 115.74.177[.]42 port 8082 - 115.74.177[.]42:8082 - POST /jim292/SMOKEJACKS-DC_W617601.[string of hex characters]/90
FILE HASHES
MALWARE FROM THE INFECTED WINDOWS HOSTS:
- SHA256 hash: 087f08fbe83404627bbf5e72a0a01ea8f8279120ffa726e5b54767cb2d234266
File size: 87,424 bytes
File description: Downloaded Word doc with macro for Emotet
- SHA256 hash: 69a0e2965831b04fc57d3026088131717e60651620d698aa03f427cb91bb3536
File size: 159,744 bytes
File description: Emotet malware binary
- SHA256 hash: c5bee1f88fdf6e5318e98e2fe1458403e44fdb67714ed45608ba1fc8cc3d1259
File size: 460,800 bytes
File description: Trickbot on infected client, gtag: del53
- SHA256 hash: d856b764fa5be66e9149eea203131200c9e5bd292e0afd9ba81998994d7322a6
File size: 539,136 bytes
File description: Trickbot on infected DC, gtag: jim292
IMAGES
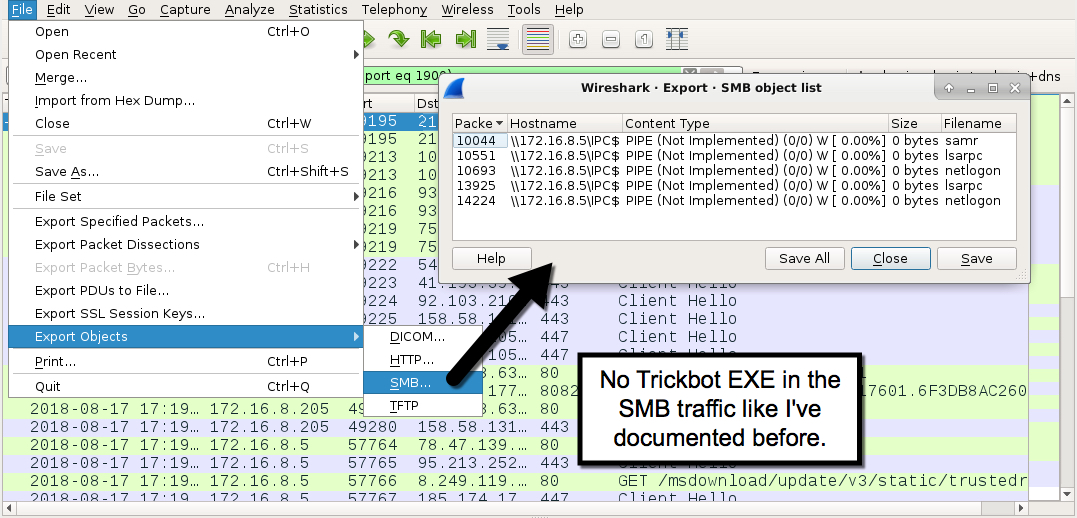
Shown above: No Trickbot EXE in the SMB traffic from client to DC like I've documented before.
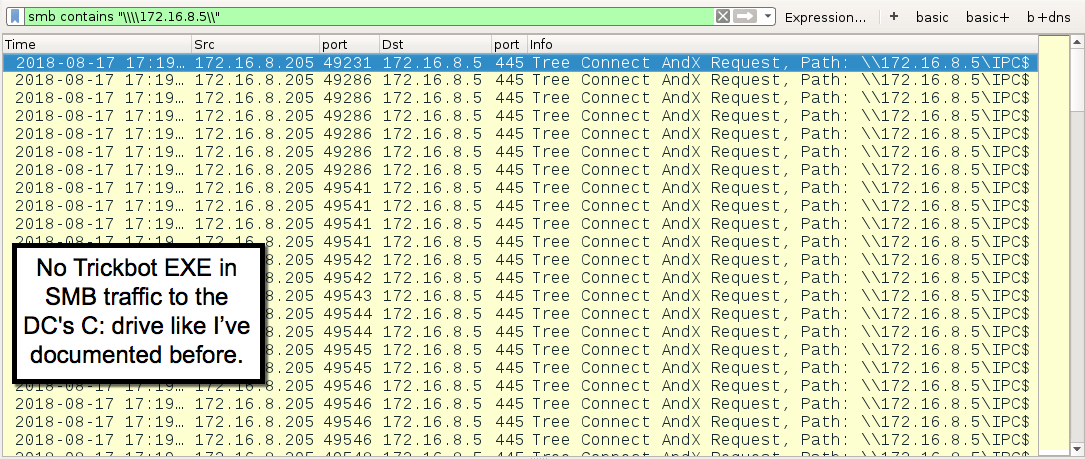
Shown above: No SMB traffic from the client to DC's C$ drive like I've documented before.
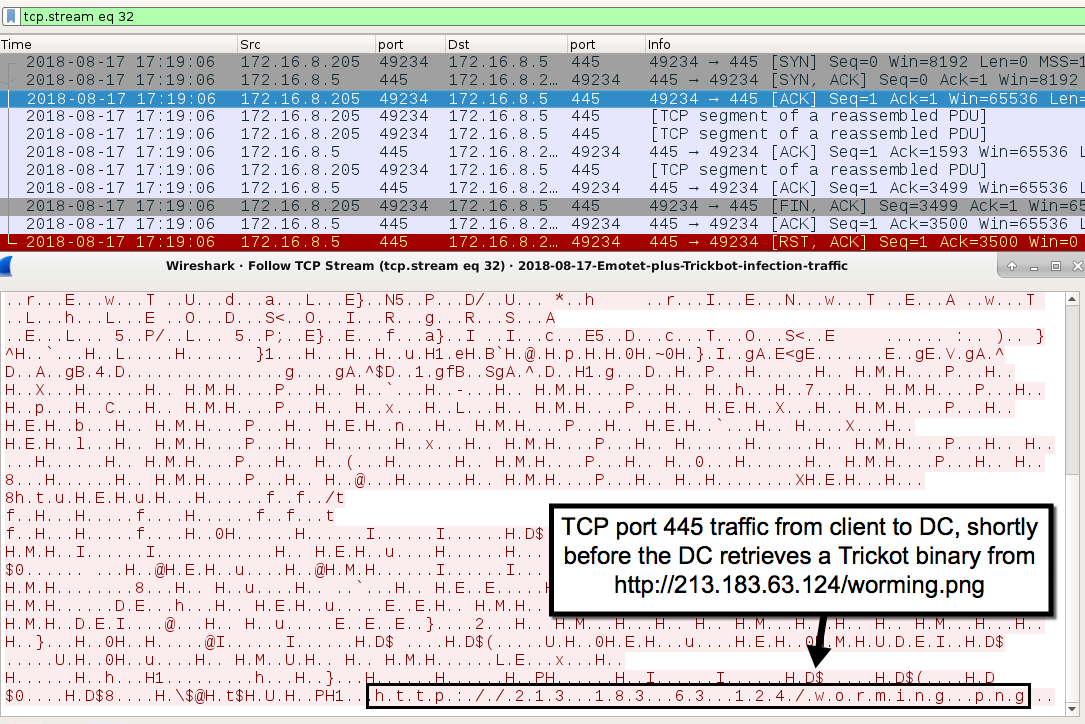
Shown above: Before the DC retrieves Trickbot from 213.183.63.124/worming.png, we see the URL in traffic over TCP port 445 from the infected client to the DC.
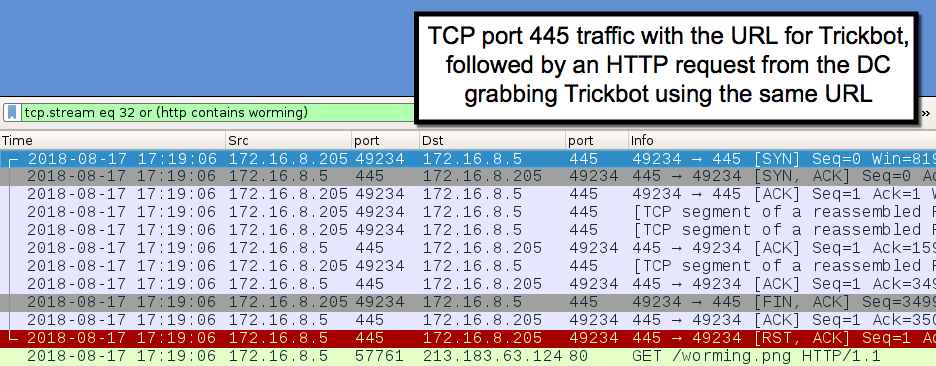
Shown above: That TCP port 445 caused the DC to retrieve the Trickbot binary from 213.183.63.124/worming.png and infect itself with it.
As I mentioned earlier, check here for an example of the way Trickbot moved to the DC previously.
Click here to return to the main page.
