2019-02-07 - INFO STEALER (AGENT TESLA) THAT USES FTP TO EXFILTRATE DATA
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- Zip archive of the infection traffic: 2019-02-07-cred-stealer-via-FTP-traffic.pcap.zip 1.4 MB (1,364,164 bytes)
- 2019-02-07-cred-stealer-via-FTP-traffic.pcap (1,822,495 bytes)
- AL5THvvehvvvajyc.exe (906,920 bytes)
NOTES:
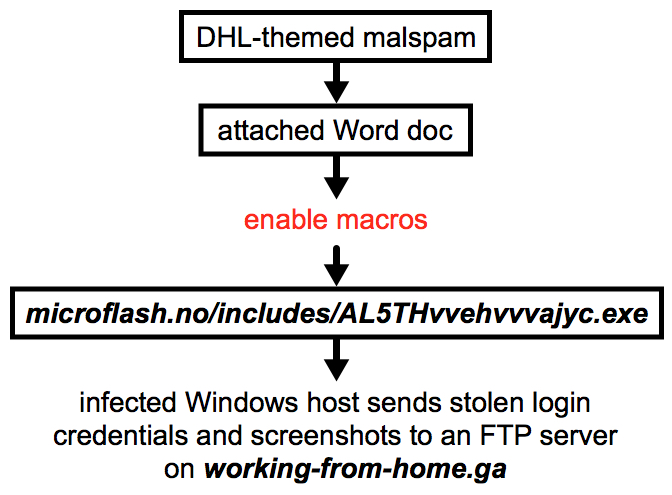
- Today I found an executable file called by macros from a Word document attached to DHL-themed malicious spam (malspam).
- Unfortunately, I cannot provide any further information on the malspam or Word document.
- But the traffic was interesting enough that I wanted to post a blog on it.
- The malware took about 37 minutes before it generated any post-infection traffic.
- Every 20 minutes after the initial password exfiltration, my infected lab host sent a screenshot of its desktop to an FTP server on working-from-home[.]ga.
- Update: This seems to be AgentTesla (Agent Tesla) or an AgentTesla variant.
Shown above: Flow chart for this infection chain.
WEB TRAFFIC BLOCK LIST
Indicators are not a block list. If you feel the need to block Internet traffic, I suggest the following:
- hxxp[:]//microflash[.]no/includes/AL5THvvehvvvajyc.exe
- FTP traffic to working-from-home[.]ga (domain appears to have a legitimate website)
TRAFFIC
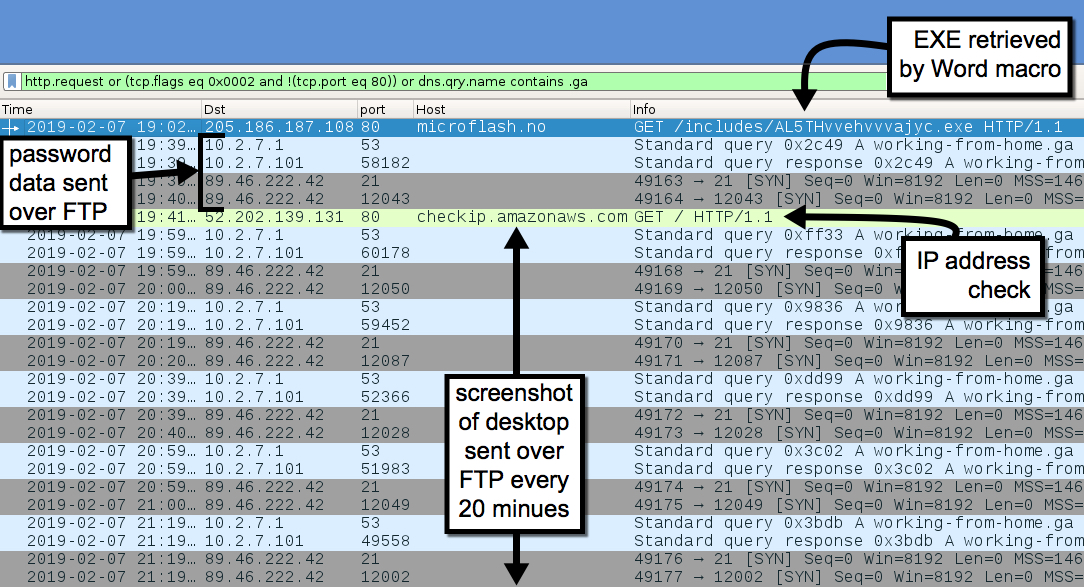
Shown above: Infection traffic filtered in Wireshark.
TRAFFIC FROM AN INFECTED WINDOWS HOST:
- 205.186.187[.]108 port 80 - microflash[.]no - GET /includes/AL5THvvehvvvajyc.exe
- 89.46.222[.]42 port 21 - working-from-home[.]ga - FTP control traffic
- 89.46.222[.]42 various ports - working-from-home[.]ga - FTP data traffic
- port 80 - checkip.amazonaws[.]com - GET / (IP address check by the infected host, not inherently malicious)
FILE HASHES
MALICIOUS EXECUTABLE:
- SHA256 hash: 72505cc347af0524c7f22ca97cb2547b7d51a1764ec43d1de7679c1072622c11
File size: 906,920 bytes
File location: hxxp[:]//microflash[.]no/includes/AL5THvvehvvvajyc.exe
Original file name: HERISSON.exe
Digital Signature Signer Name: CasterLevel
Digital Signature Signer Email: Not available
Name of signer: Symantec SHA256 TimeStamping Signer - G3
Signing time: Tuesday 2019-02-04 13:24:21 UTC
File description: Infostealer that uses FTP
IMAGES
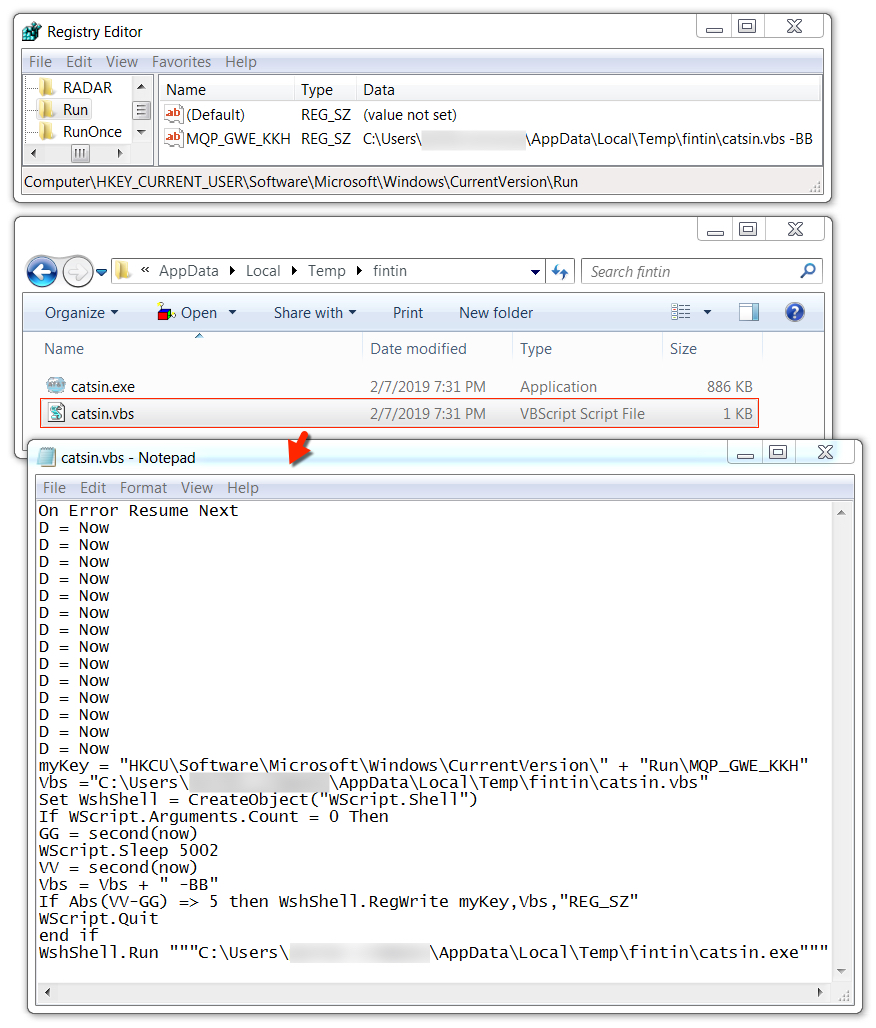
Shown above: Malware persistent on the infected Windows host.
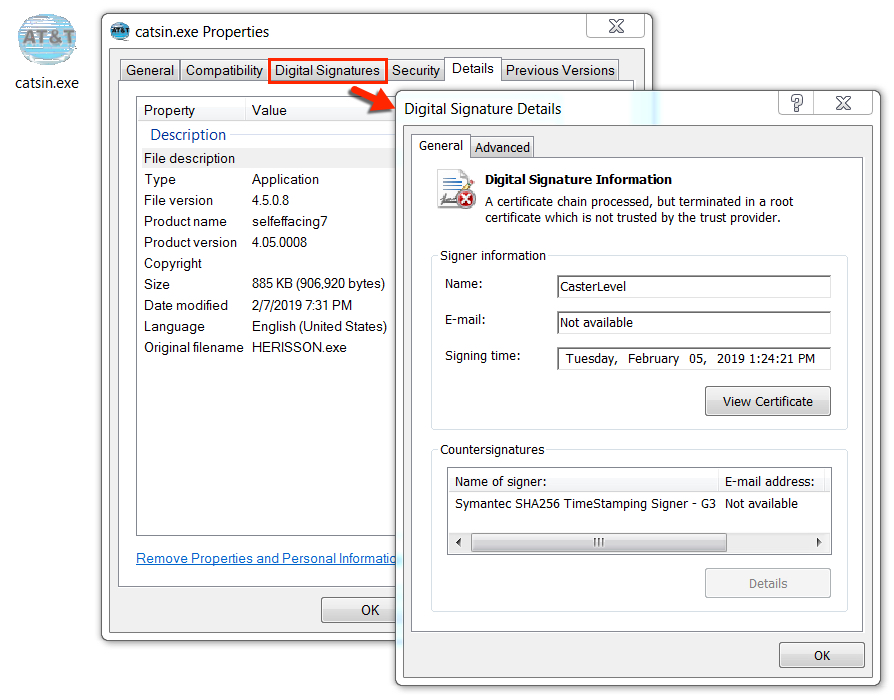
Shown above: More information on the malicious executable.
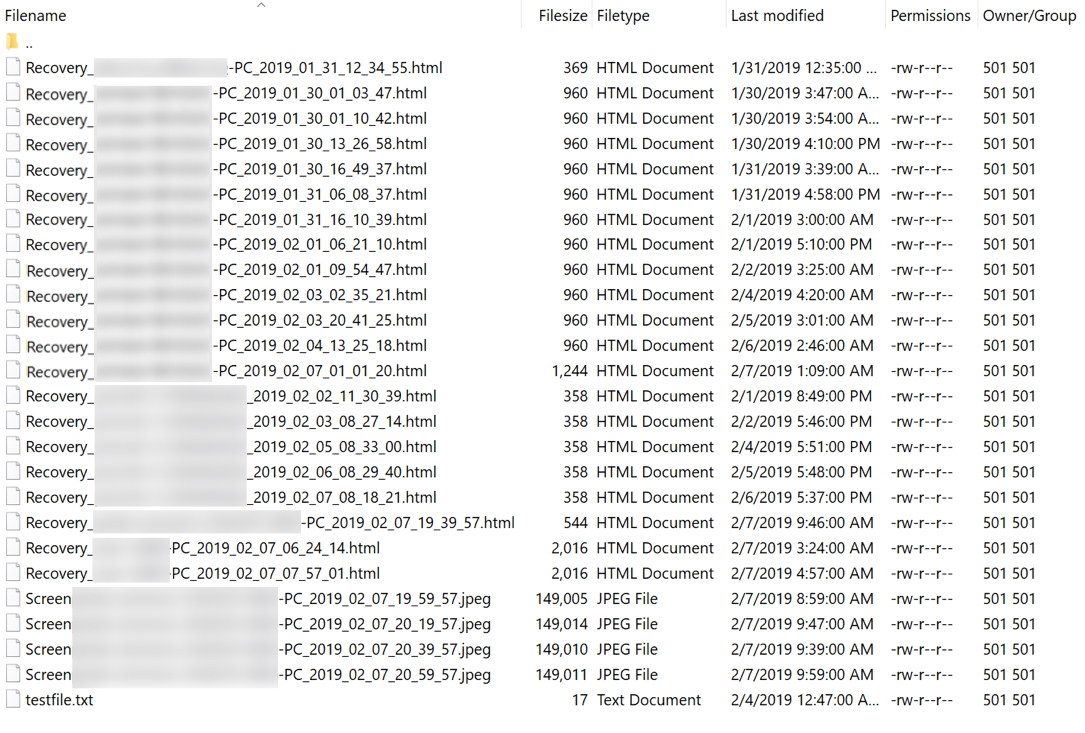
Shown above: Files on the FTP server the malware sent stolen credentials to. The JPEG files are screenshots from my infected Windows host. Looks like this FTP server
was used for stolen credentials as early as 2019-01-30.
Click here to return to the main page.