2020-04-15 - HANCITOR MALSPAM AND INFECTION TRAFFIC
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2020-04-15-Hancitor-IOCs.txt.zip 2.1 kB (2,121 bytes)
- 2020-04-15-Hancitor-IOCs.txt (4,930 bytes)
- 2020-04-15-Hancitor-malspam-4-examples.zip 17.4 kB (17,419 bytes)
- 2020-04-14-Hancitor-malspam-1510-UTC.eml (22,040 bytes)
- 2020-04-14-Hancitor-malspam-1943-UTC.eml (21,879 bytes)
- 2020-04-14-Hancitor-malspam-2230-UTC.eml (22,015 bytes)
- 2020-04-15-Hancitor-malspam-0259-UTC.eml (23,553 bytes)
- 2020-04-15-Hancitor-infection-3-pcaps.zip 761 kB (761,109 bytes)
- 2020-04-15-Hancitor-infection-1st-run.pcap (364,230 bytes)
- 2020-04-15-Hancitor-infection-2nd-run.pcap (352,767 bytes)
- 2020-04-15-Hancitor-infection-3rd-run.pcap (353,861 bytes)
- 2020-04-15-Hancitor-malware.zip 696 kB (696,136 bytes)
- coverage_BR432_2483.zip (81,482 bytes)
- coverage_BR432.xls (142,341 bytes)
- coverage_CT367_7450.zip (81,483 bytes)
- coverage_CT367.xls (142,341 bytes)
- coverage_FD830_6487.zip (81,482 bytes)
- coverage_FD830.xls (142,341 bytes)
- coverage_VD432_4302.zip (81,481 bytes)
- coverage_VD432.xls (142,341 bytes)
- tpeyoft.ocx (84,480 bytes)
IMAGES
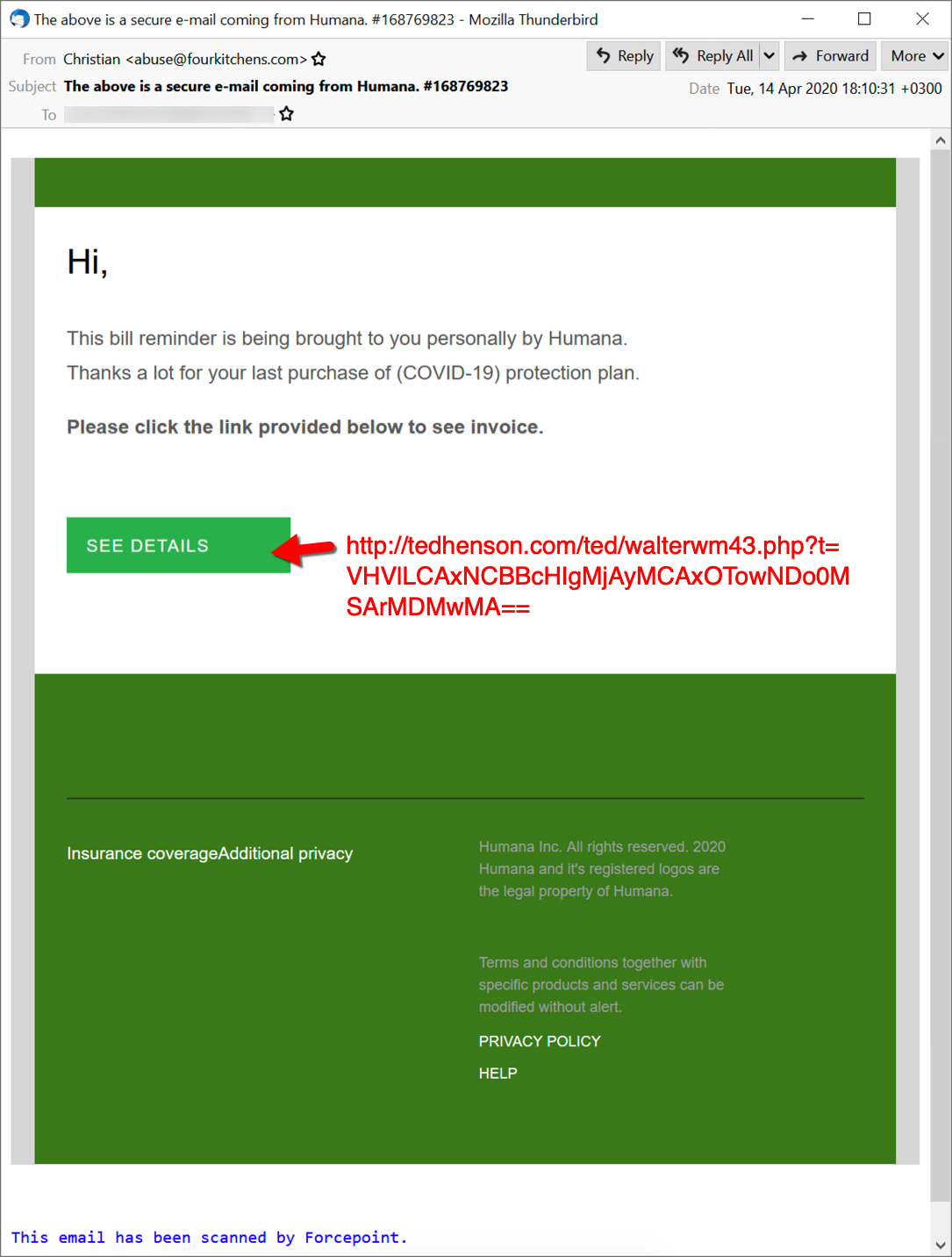
Shown above: Screenshot from one of the emails pushing Hancitor.
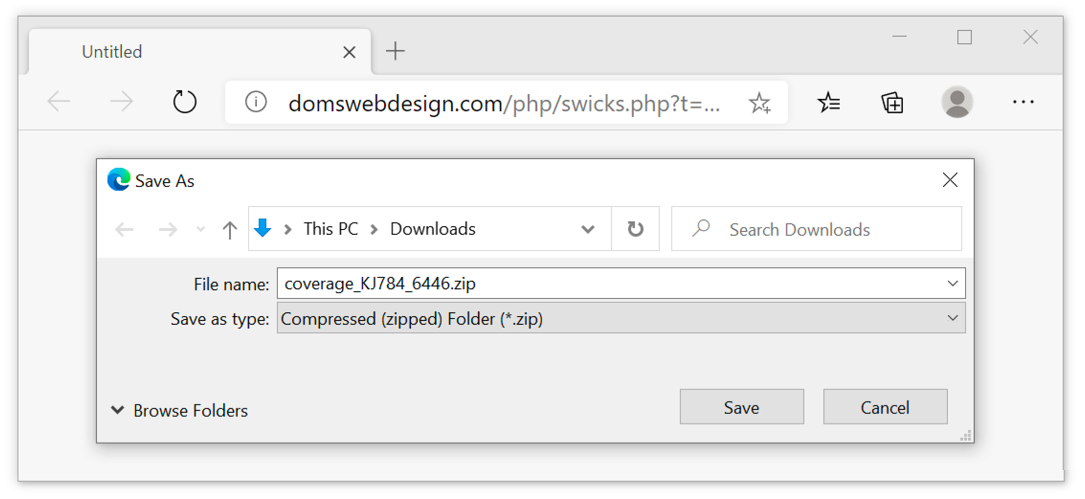
Shown above: Downloading the initial zip archive from one of the email links.
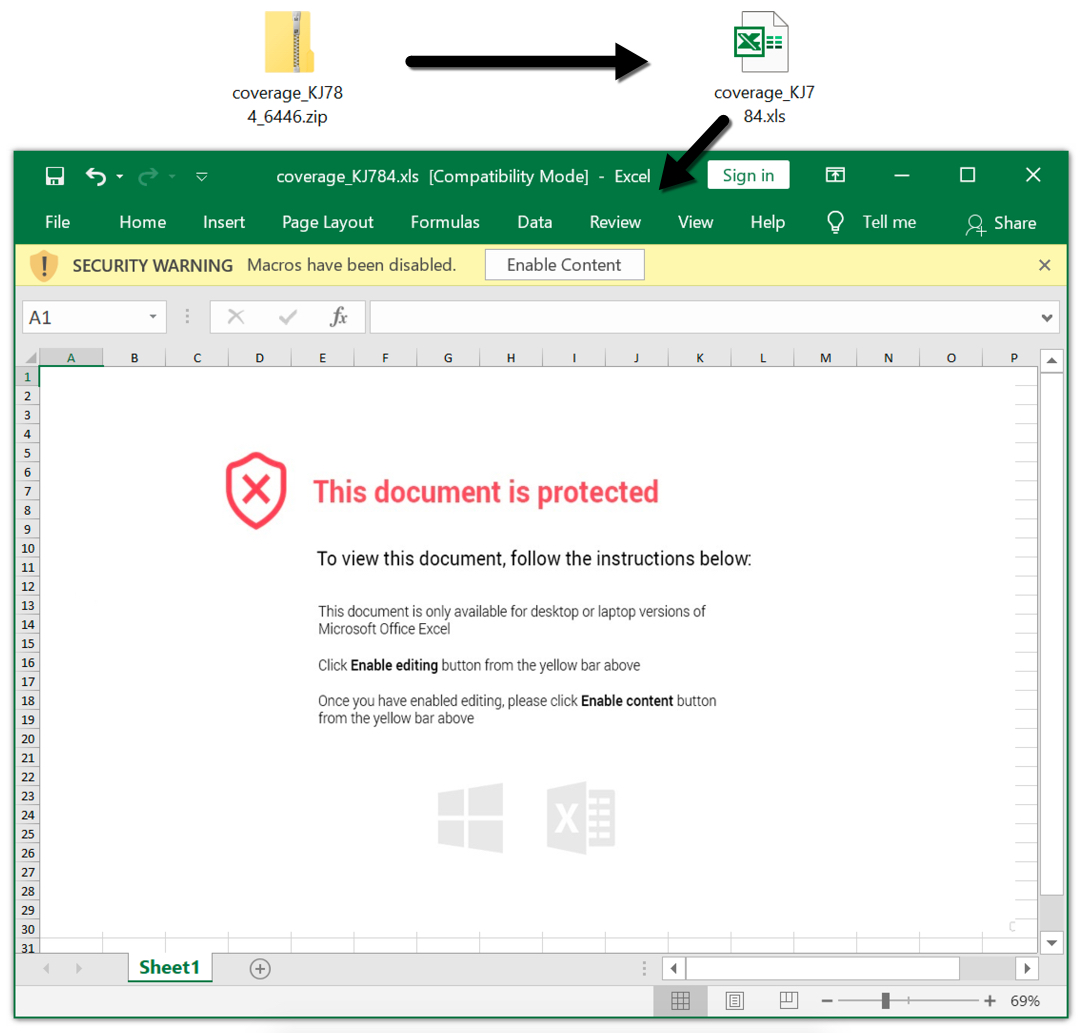
Shown above: From zip archive to extracted Excel spreadsheet.
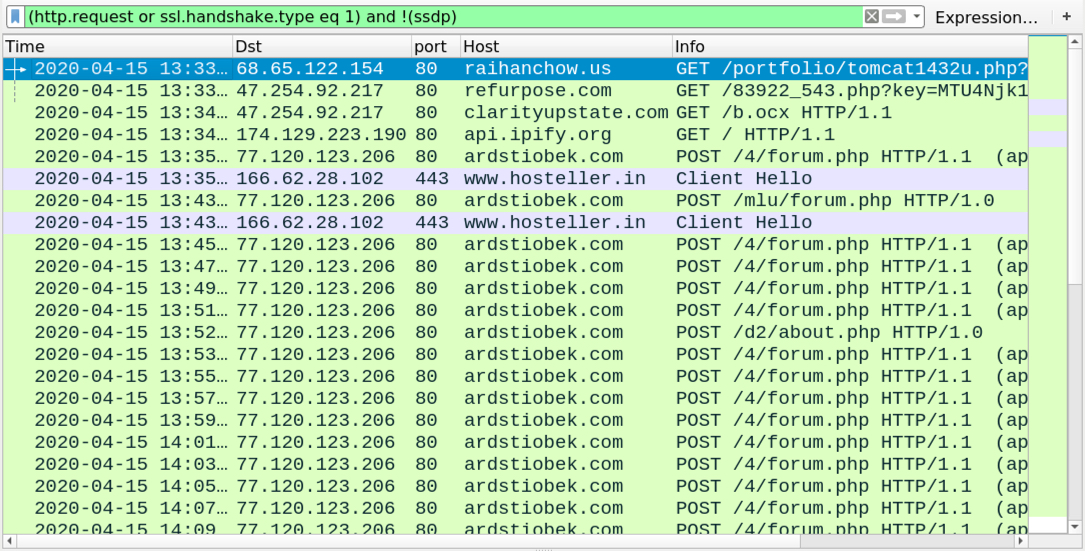
Shown above: Traffic from an infection filtered in Wireshark.
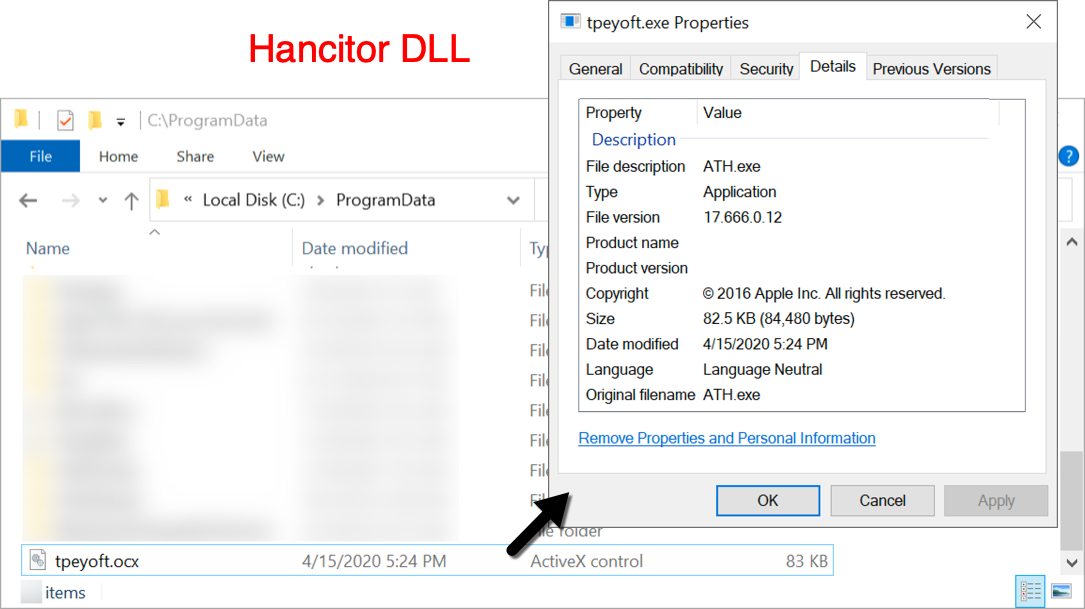
Shown above: Hancitor DLL on an infected Windows host.
Click here to return to the main page.
