2020-05-27 - COVID19-THEMED WORD DOC PUSHES ICEDID (BOKBOT)
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2020-05-27-IOCs-for-IcedID-from-COVID19-themed-Word-doc.txt.zip 1.5 kB (1,533 bytes)
- 2020-05-27-IOCs-for-IcedID-from-COVID19-themed-Word-doc.txt (3,486 bytes)
- 2020-05-27-IcedID-infection-from-COVID19-themed-Word-doc.pcap.zip 3.8 MB (3,782,707 bytes)
- 2020-05-27-IcedID-infection-from-COVID19-themed-Word-doc.pcap (4,046,889 bytes)
- 2020-05-27-malware-and-artifacts-from-IcedID-from-COVID19-themed-Word-doc.zip 1.1 MB (1,099,248 bytes)
- 2020-05-27-scheduled-task-for-IcedID.txt (1,893 bytes)
- Latest_Updates_of_COVID19_26909.doc (172,476 bytes)
- Users/username/AppData/Local/Temp/~87772416.tmp (79,687 bytes)
- Users/username/AppData/Local/Temp/~87869421.exe (75,264 bytes)
- Users/username/AppData/Local/{473D8A8A-6339-839F-03A2-B10422617939}/Hanuac4.png (667,077 bytes)
- Users/username/AppData/Local/username/Joujkd2.exe (75,264 bytes)
- filelogger/JGHKDSE.exe (75,264 bytes)
- filelogger/weathp.dll (192,514 bytes)
NOTES:
- My infected Windows later re-infected itself with the same IcedID binary, which appeared in the user's AppData\Local\Temp directory (but not shown in my images below).
IMAGES
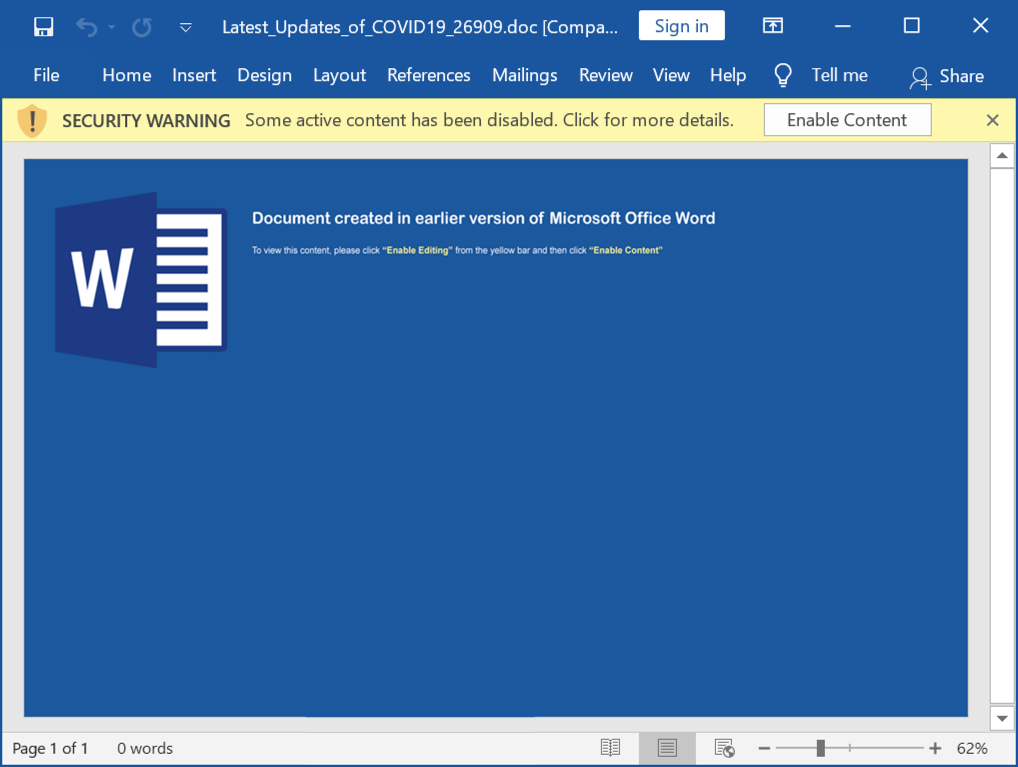
Shown above: Screenshot of the Word doc with malicious macros.
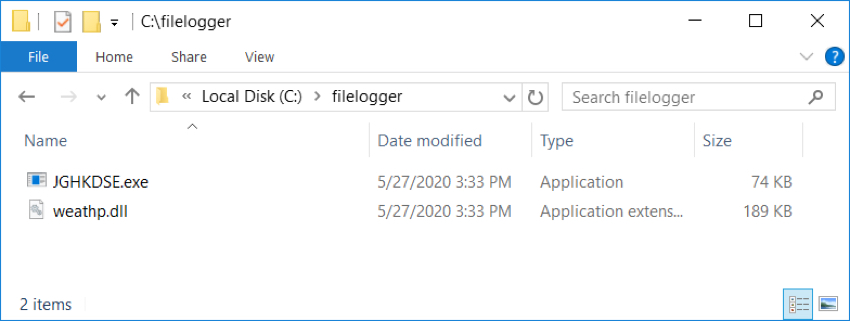
Shown above: DLL dropped after enabling macros, and the initial IcedID EXE that appeard immediated afterward.
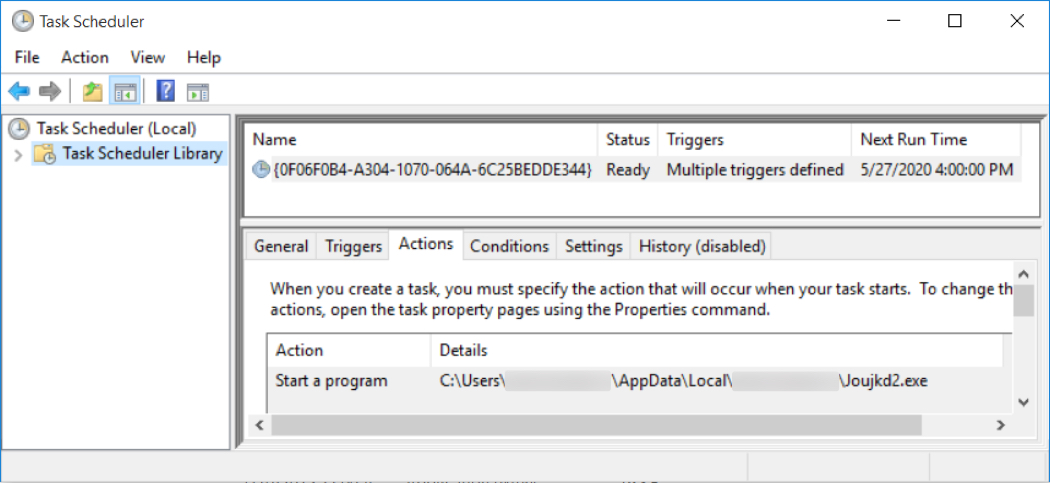
Shown above: Scheduled task to keep IcedID persistent.
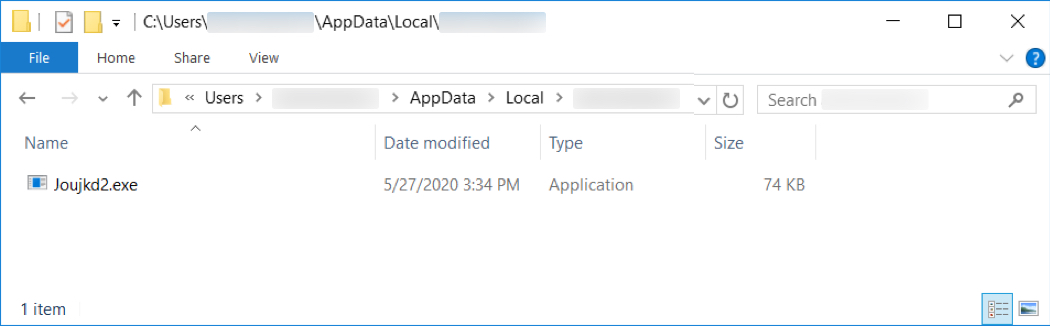
Shown above: Location of the persistent IcedID executable.
Shown above: PNG image containing encoded data associated with the IcedID infection.
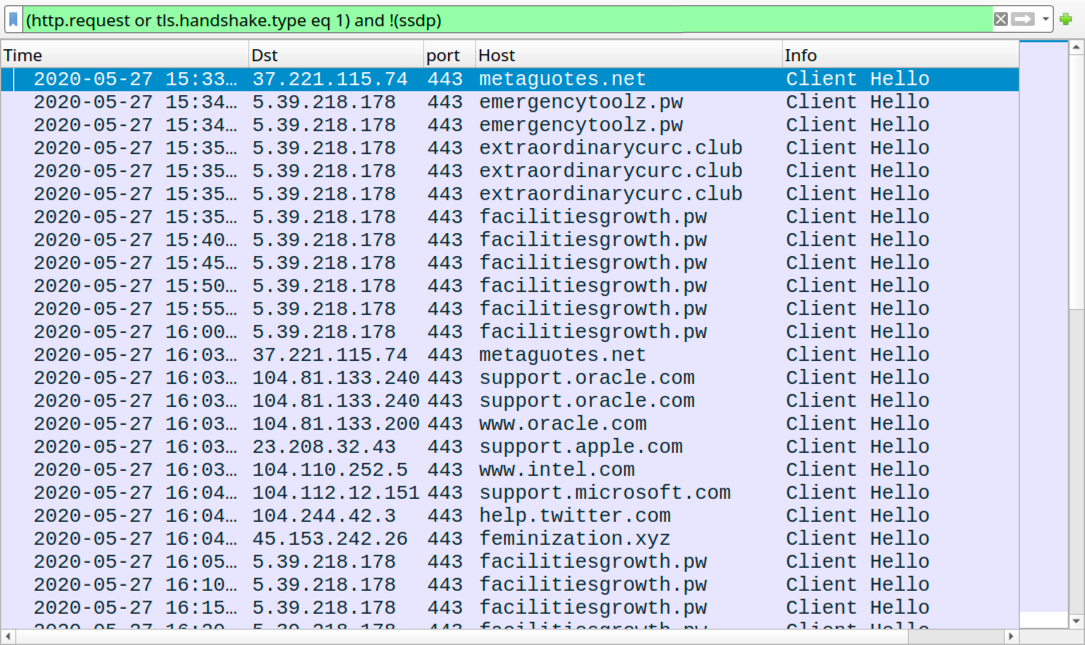
Shown above: Traffic from the infection filtered in Wireshark.
Click here to return to the main page.
