2020-06-25 - RESUME-THEMED MALSPAM PUSHING ZLOADER
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2020-06-25-resume-themed-ZLoader-infection-IOCs.txt.zip 1.1 kB (1,109 bytes)
- 2020-06-25-resume-themed-malspam-example.eml.zip 514 kB (514,030 bytes)
- 2020-06-25-ZLoader-infection-traffic.pcap.zip 5.7 MB (5,690,277 bytes)
- 2020-06-25-ZLoader-malware-and-artifacts.zip 949 kB (949,282 bytes)
NOTE:
- I also wrote an ISC diary on this about two weeks ago on 2020-06-10: link.
IMAGES
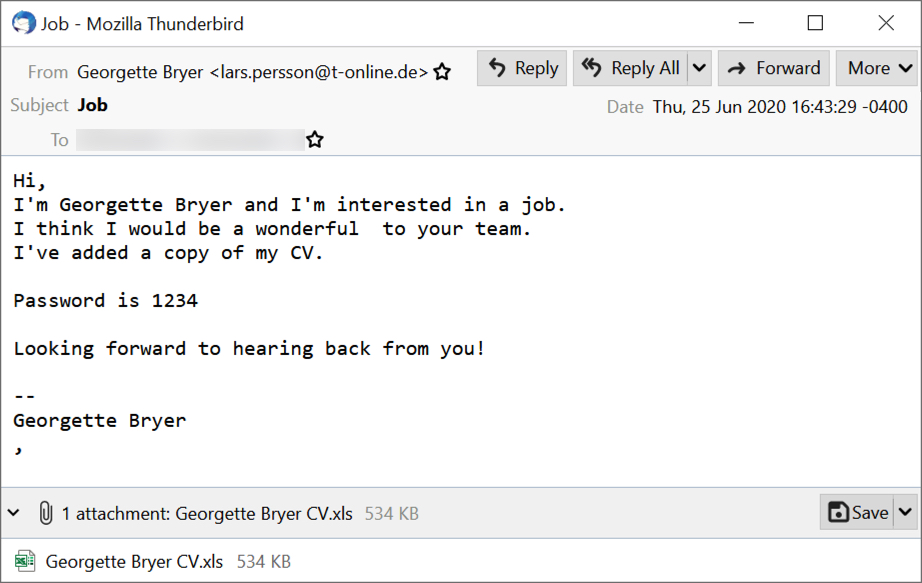
Shown above: Screenshot of the malspam example.
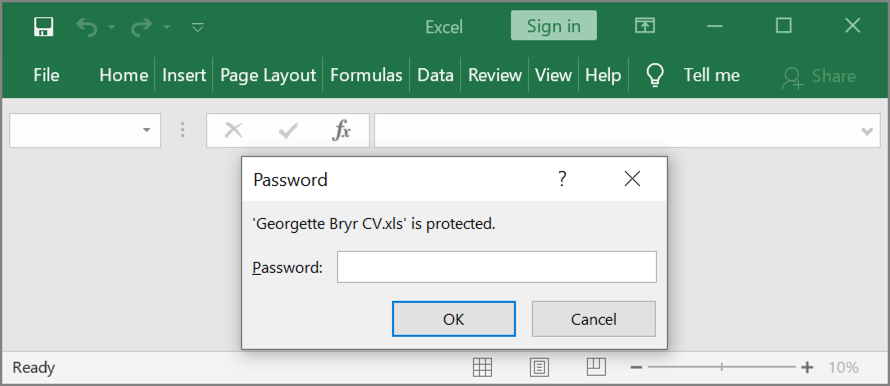
Shown above: Opening the attached spreadsheet requires password from the message text.
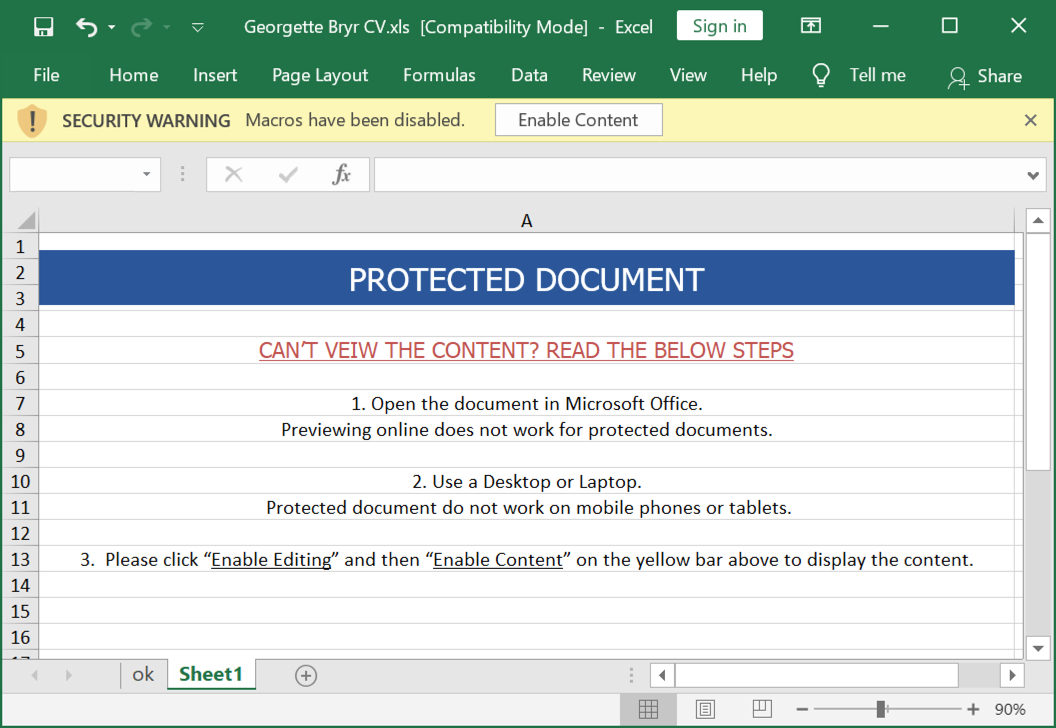
Shown above: Screenshot of the spreadsheet.
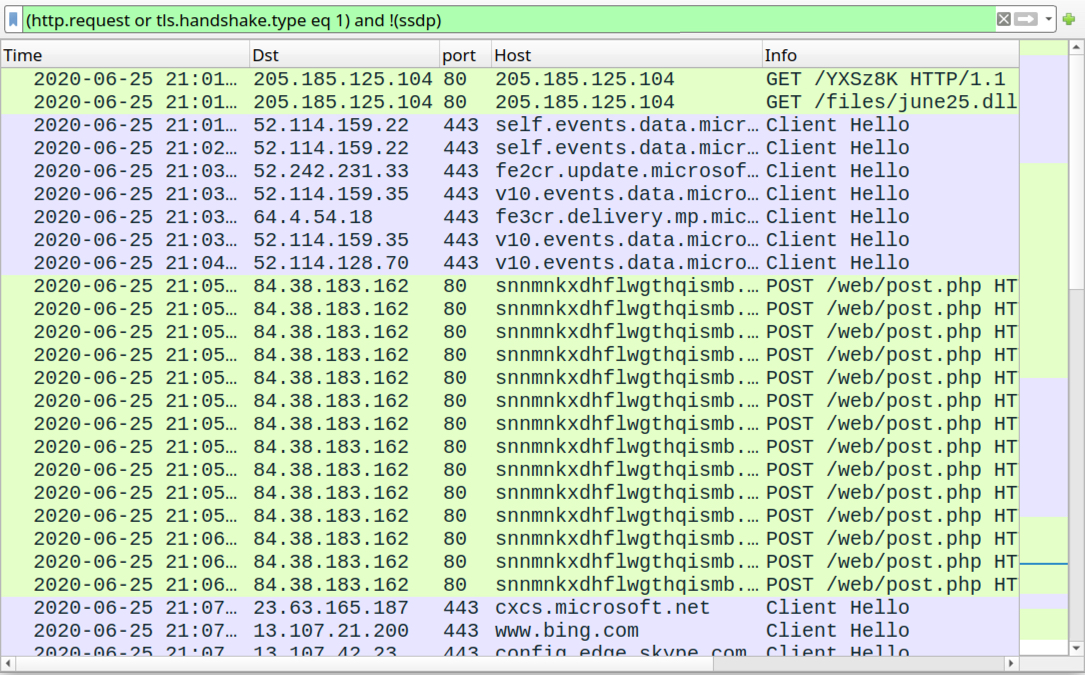
Shown above: Traffic from an infection filtered in Wireshark.
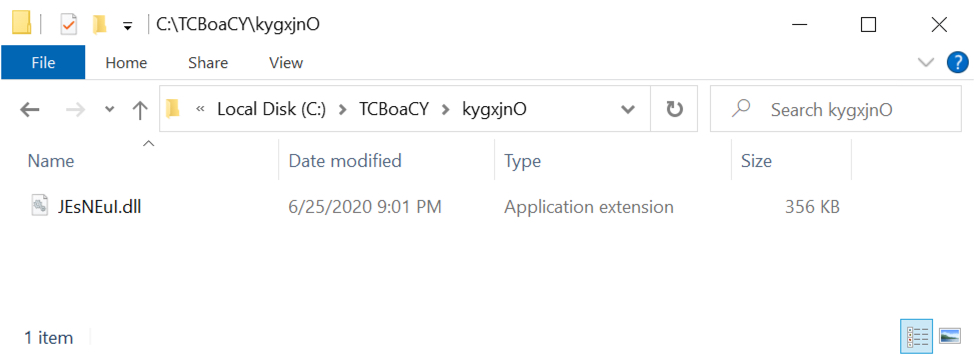
Shown above: Initial location of the ZLoader DLL.
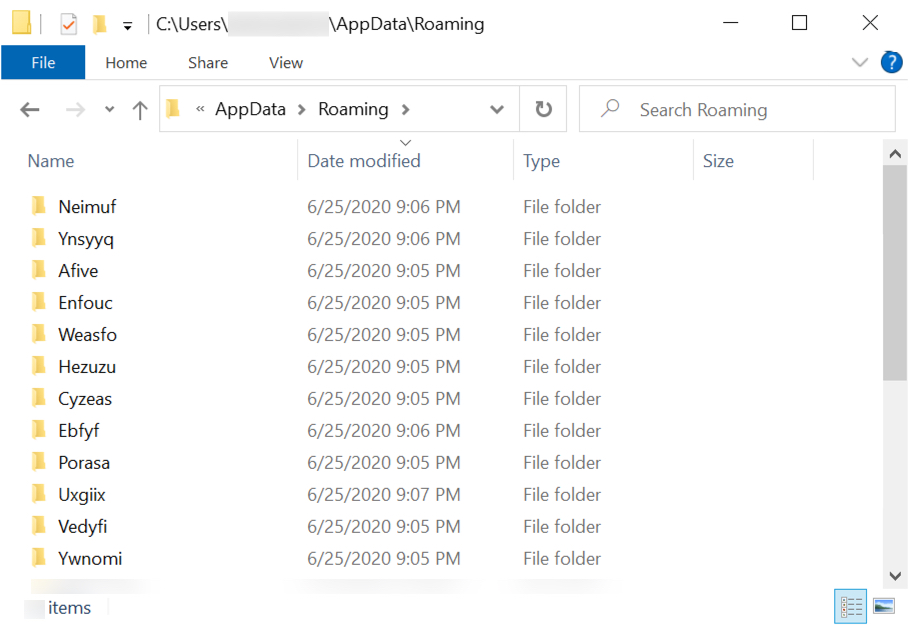
Shown above: Decoy folders created by ZLoader.
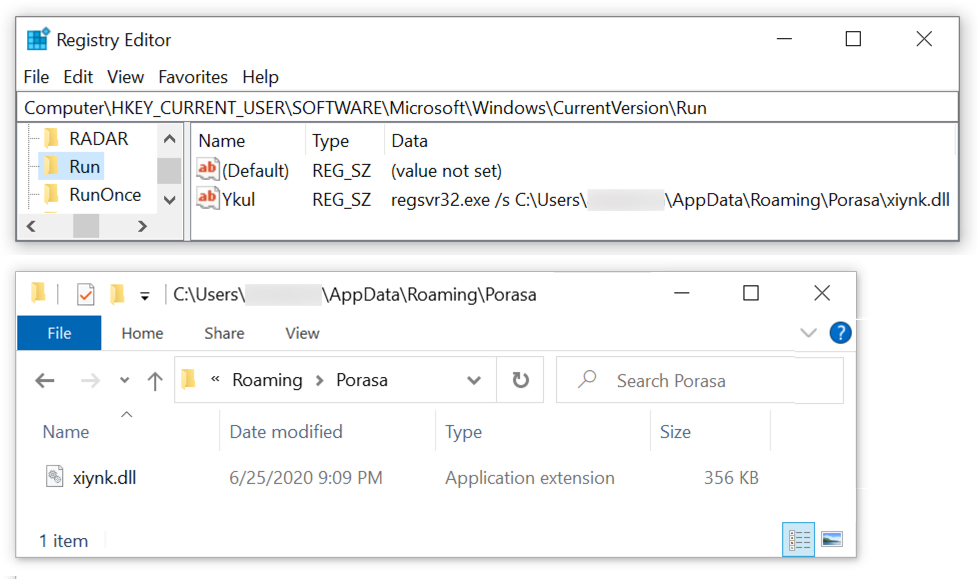
Shown above: ZLoader persistent on the infected Windows host.
Click here to return to the main page.
