2020-10-16 - TA551 (SHATHAK) WORD DOCS PUSH ICEDID
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2020-10-16-TA551-IOCs-for-IcedID.txt.zip 3.6 kB (3,648 bytes)
- 2020-10-16-TA551-Word-docs-20-examples.zip 2.1 MB (2,089,871 bytes)
- 2020-10-16-TA551-Word-doc-pushes-IcedID.pcap.zip 2.4 MB (2,384,796 bytes)
- 2020-10-16-TA551-installer-DLL-for-IcedID-15-examples.zip 1.5 MB (1,517,422 bytes)
- 2020-10-16-malware-and-artifacts-from-an-infection.zip 1.0 MB (1,007,907 bytes)
IMAGES
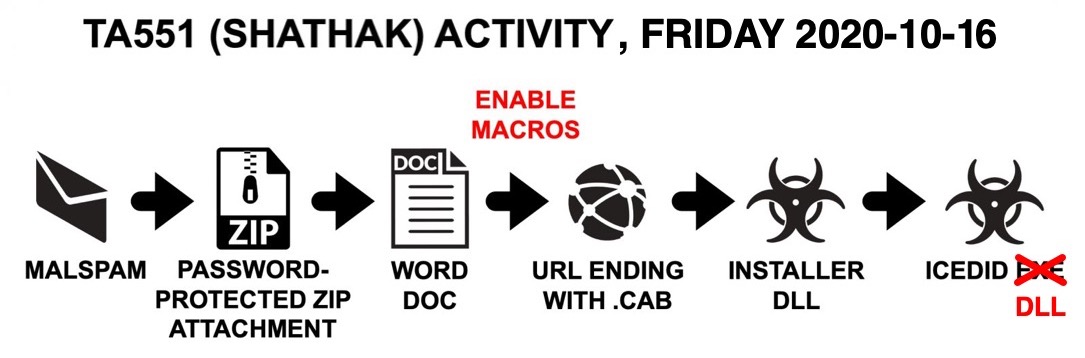
Shown above: Flow chart for today's infection chain.
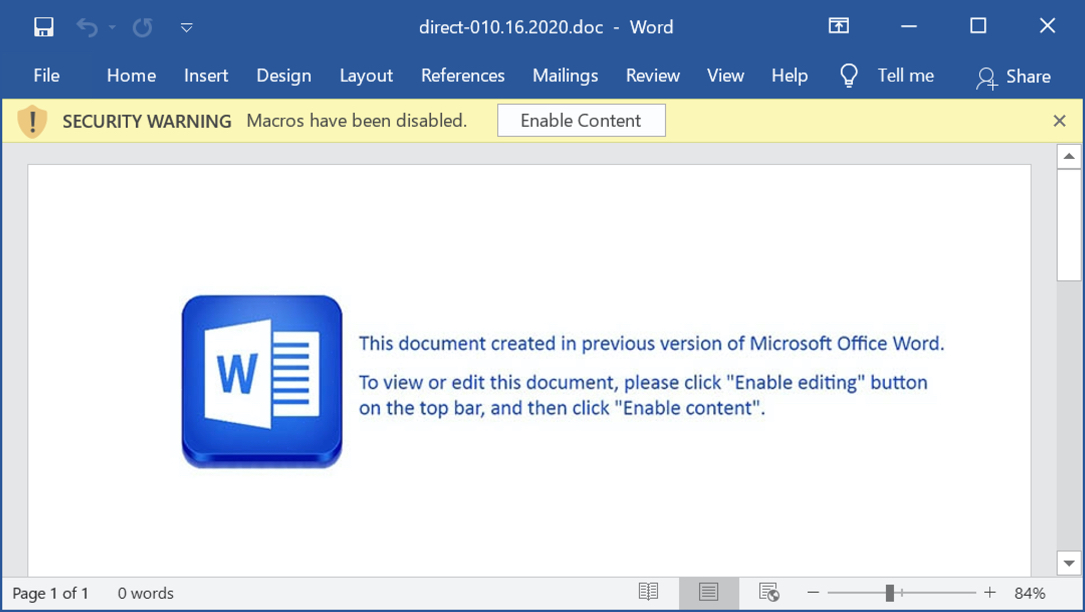
Shown above: Screenshot from one of the Word documents.
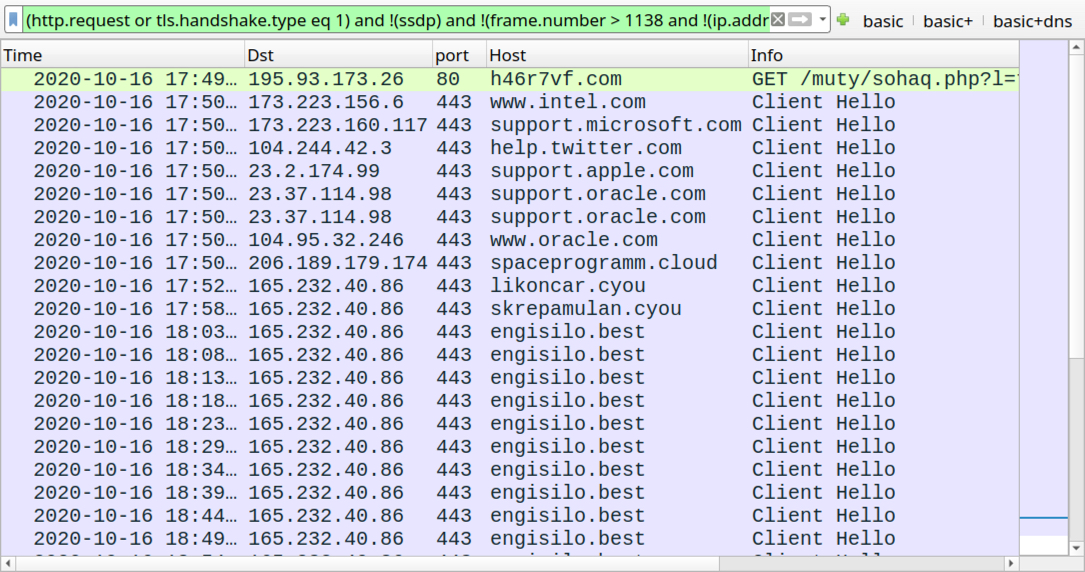
Shown above: Traffic from an infection filtered in Wireshark.
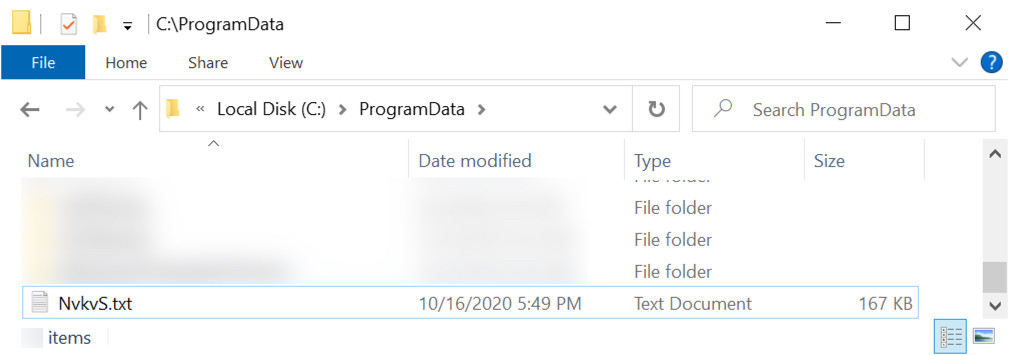
Shown above: Location of installer DLLs for today (different names, but the same .txt file extension and same directory).
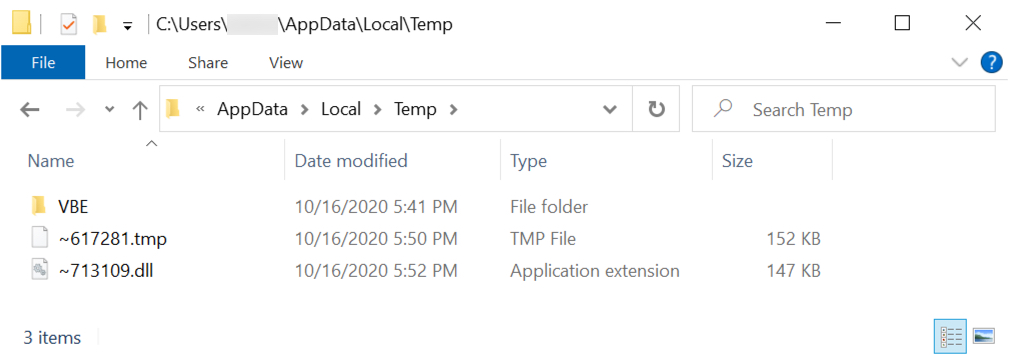
Shown above: PNG image with encoded data saved with .tmp file extension and used to create IcedID malware DLL.
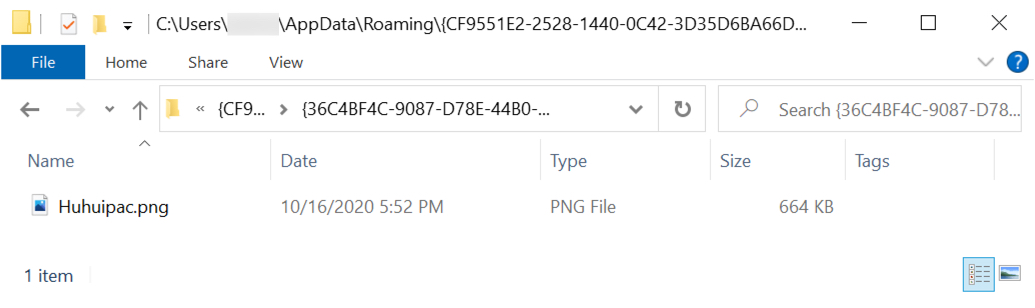
Shown above: Another PNG image with encoded data created after IcedID DLL from the \AppData\Local\Temp directory was run.
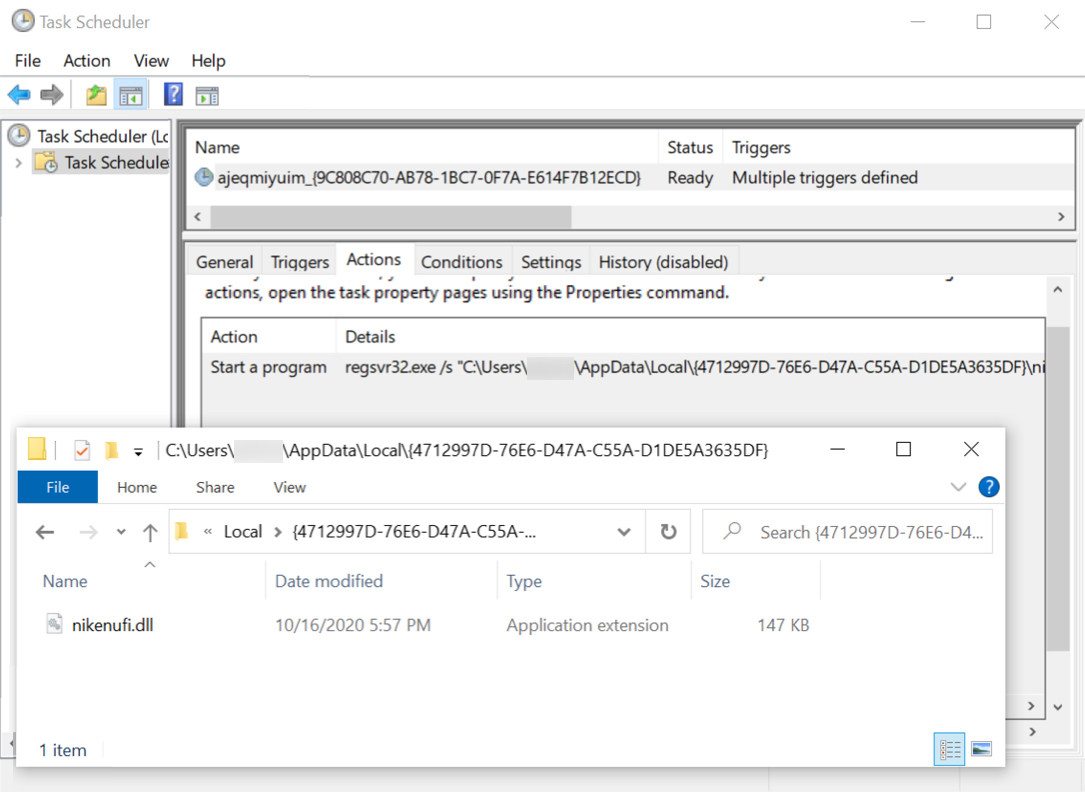
Shown above: IcedID DLL made persistent on an infected Windows host.
Click here to return to the main page.
