2021-04-0239 (FRIDAY) - ICEDID (BOKBOT) INFECTION FROM ZIPPED JS FILE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2021-04-23-IcedID-IOCs.txt.zip 1.5 kB (1,526 bytes)
- 2021-04-23-IcedID-IOCs.txt (2,931 bytes)
- 2021-04-23-IcedID-infection-traffic.zip 3.0 MB (2,952,177 bytes)
- 2021-04-23-part-1-JS-file-retrieves-installer-DLL.pcap (373,748 bytes)
- 2021-04-23-part-2-installer-DLL-causes-IcedID-infection.pcap (2,795,244 bytes)
- 2021-04-23-IcedID-malware-and-artifacts.zip 899 kB (898,561 bytes)
- 2021-04-23-fake-gzip-binary-from-federallissimus.casa.bin (414,027 bytes)
- 2021-04-23-scheduled-task-for-IcedID.txt (3,798 bytes)
- HpYzy.dat (101,907 bytes)
- StolenImages_Evidence.js (20,077 bytes)
- StolenImages_Evidence.zip (6,834 bytes)
- haxeolno.dll (72,704 bytes)
- license.dat (341,098 bytes)
- pencil_x64.dat (72,704 bytes)
REFERENCES:
- https://www.binarydefense.com/icedid-gziploader-analysis/
- https://aaqeel01.wordpress.com/2021/04/09/icedid-analysis/
- https://www.microsoft.com/security/blog/2021/04/09/investigating-a-unique-form-of-email-delivery-for-icedid-malware/
IMAGES
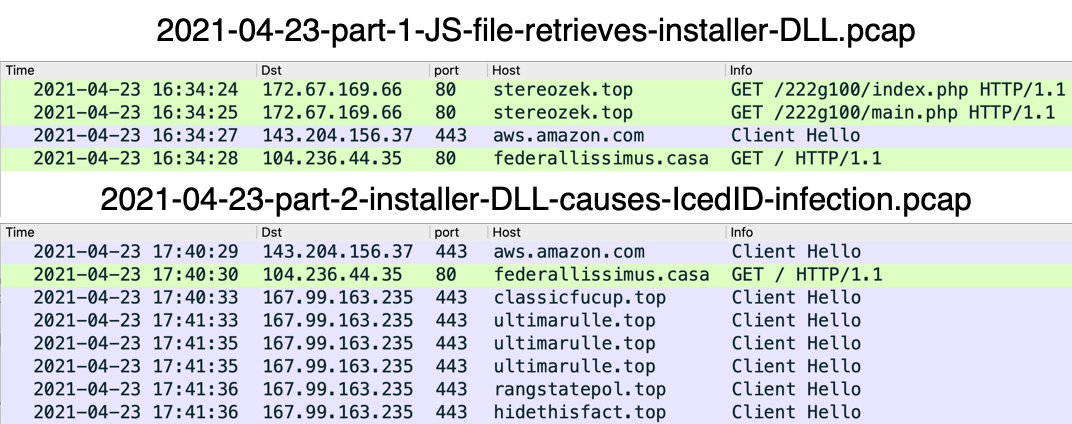
Shown above: Traffic from the pcaps filtered in Wireshark.
Click here to return to the main page.
