2021-05-20 (THURSDAY) - HANCITOR WITH FICKER STEALER, COBALT STRIKE, & NETPING TOOL
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2021-05-20-Hancitor-IOCs.txt.zip 5.8 kB (5,752 bytes)
- 2021-05-20-Hancitor-malspam-38-examples.zip 96.5 kB (96,548 bytes)
- 2021-05-20-Hancitor-infection.pcap.zip 6.4 MB (6,420,455 bytes)
- 2021-05-20-Hancitor-malware.zip 11.7 MB (11,665,148 bytes)
REFERENCES:
NOTES:
- All zip archives on this site are password-protected. If you don't know the password, see the "about" page of this website.
- Victim's Active Directory (AD) environment from the pcap:
- Victim's LAN segment range: 10.7.5[.]0/24 (10.7.5[.]0 through 10.7.5[.]255
- Victim's Domain: stormruncreek[.]com
- Victim's Domain controller: 10.7.5[.]7 - StormRun-DC
- LAN segment gateway: 10.7.5[.]1
- LAN segment broadcast address: 10.7.5[.]255
IMAGES
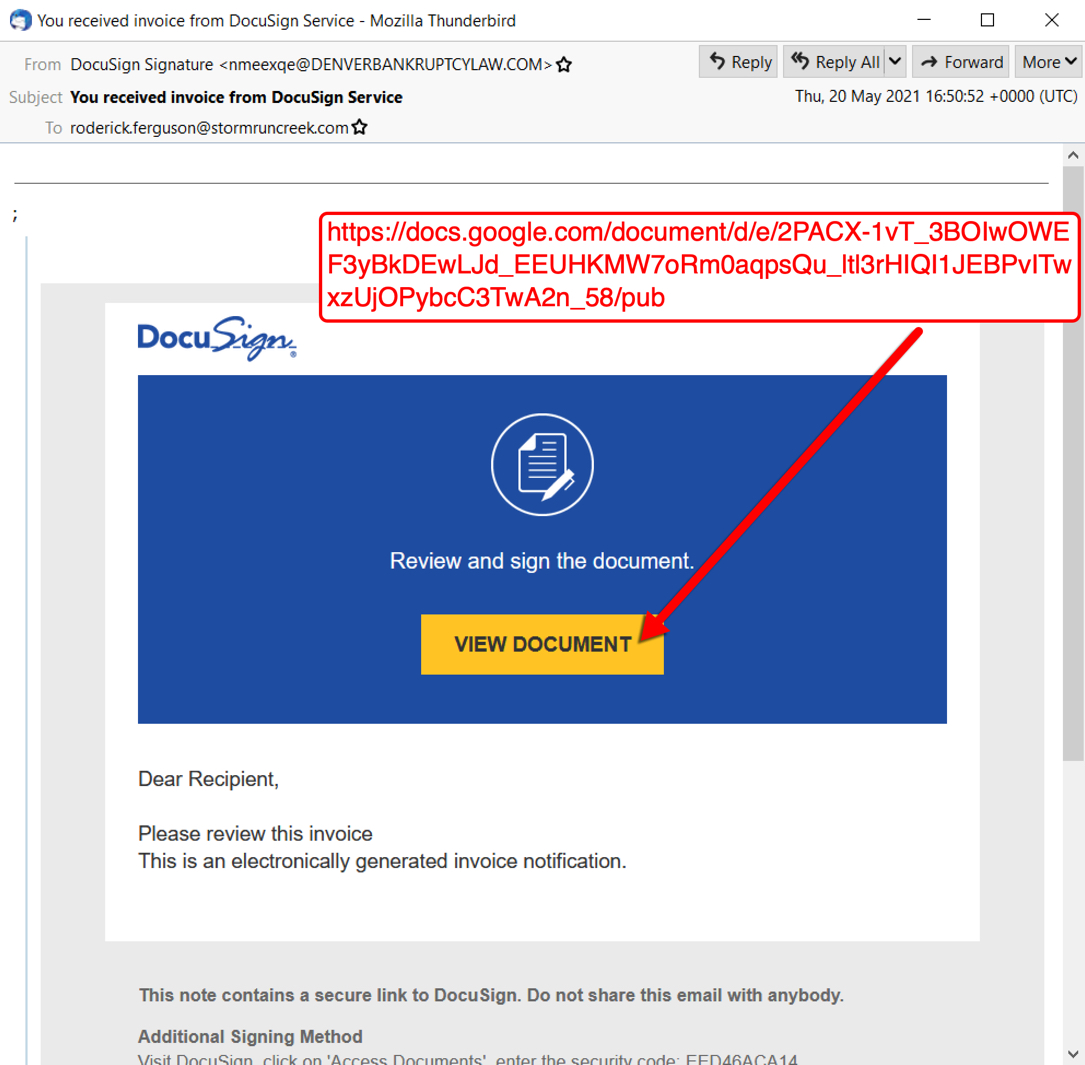
Shown above: Screenshot of DocuSign-themed Hancitor malspam with Google Docs link.
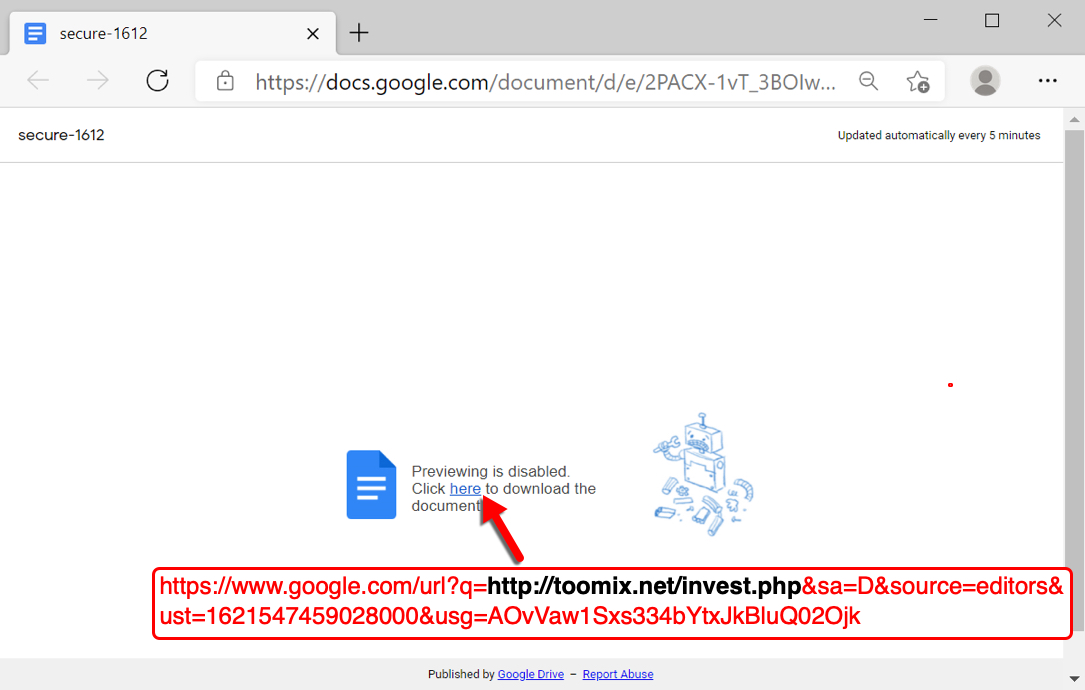
Shown above: Google docs link in a web browser.
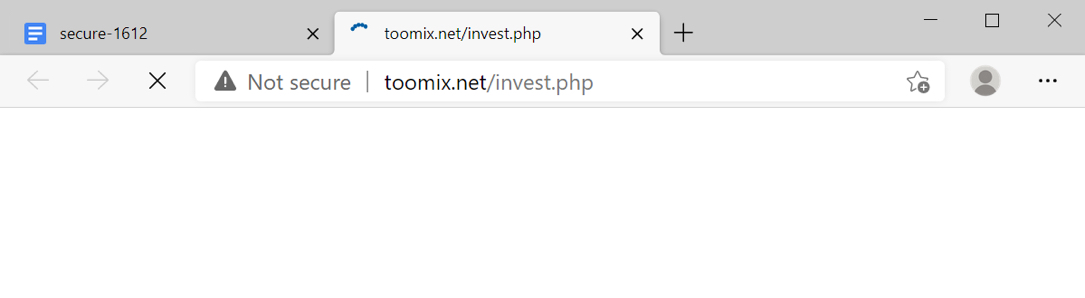
Shown above: Google docs link causes traffic to toomix[.]net that will return a Hancitor Word doc.
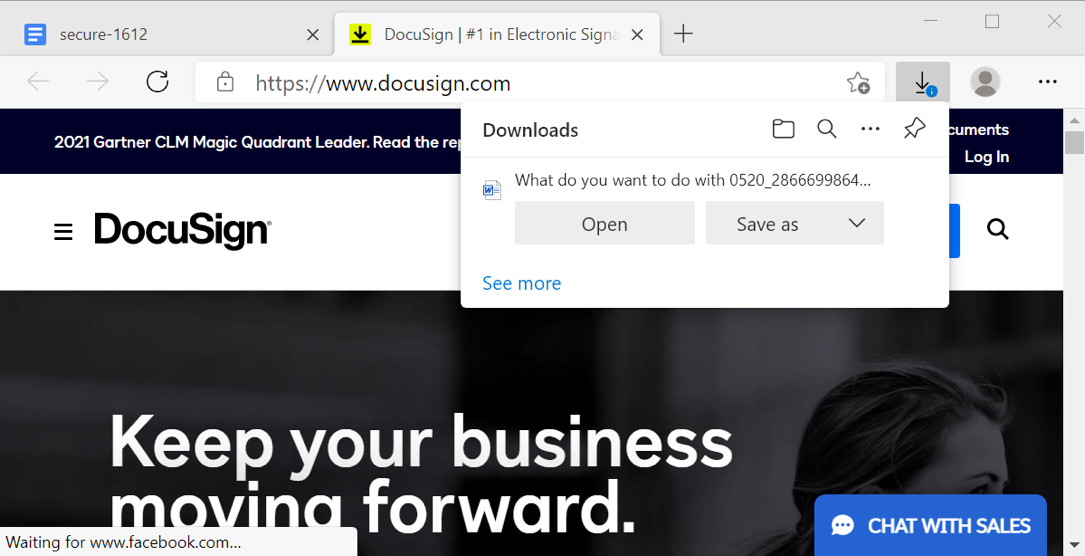
Shown above: Browser offers Word document for download then redirects to the real DocuSign site.
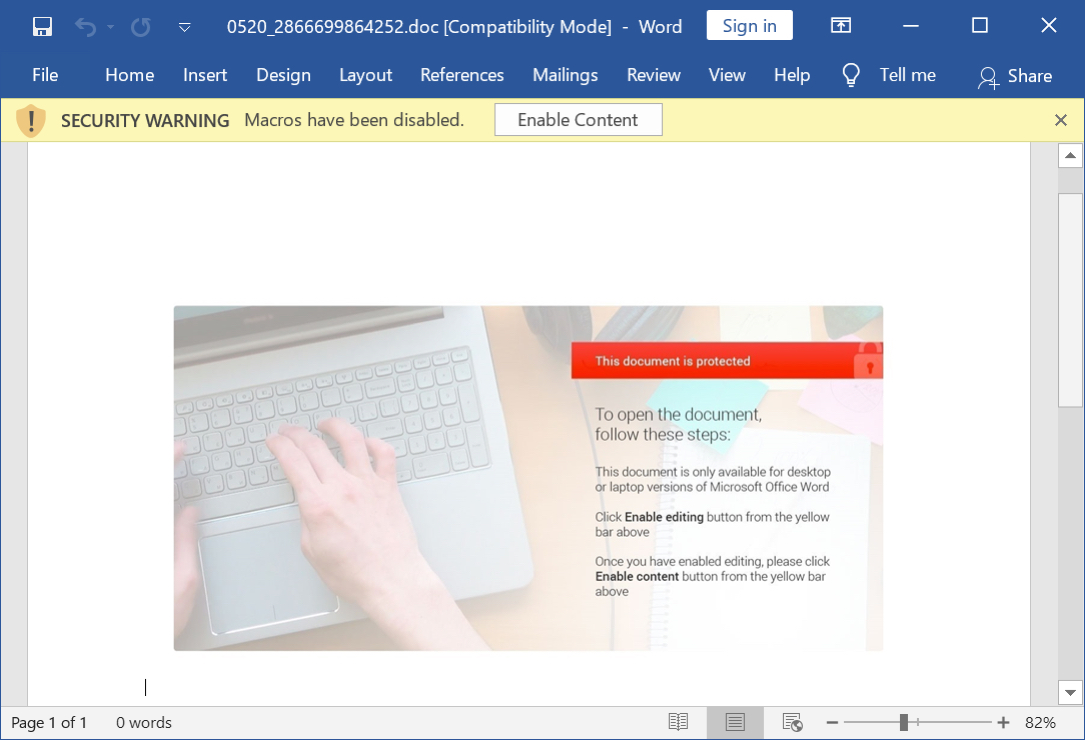
Shown above: Screenshot of a downloaded Word document with macros for Hancitor.
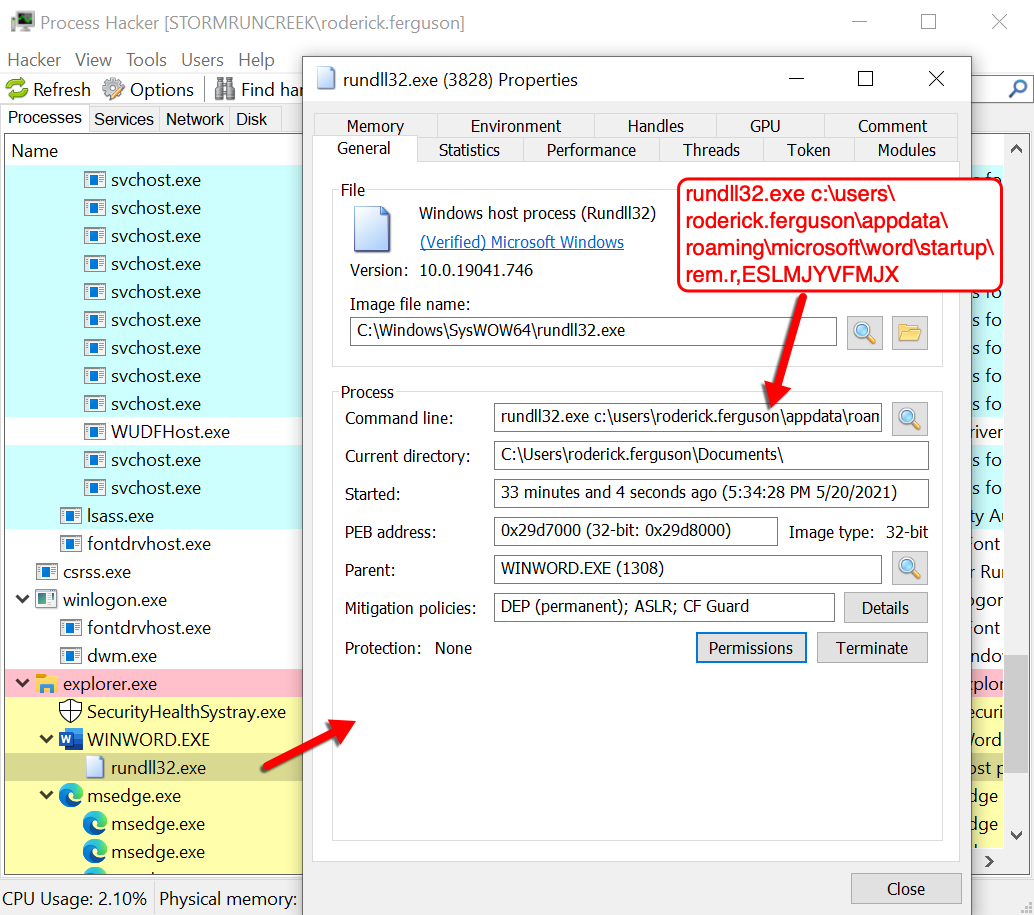
Shown above: Process for the Hancitor DLL file reveals how it uses rundll32.exe to run.
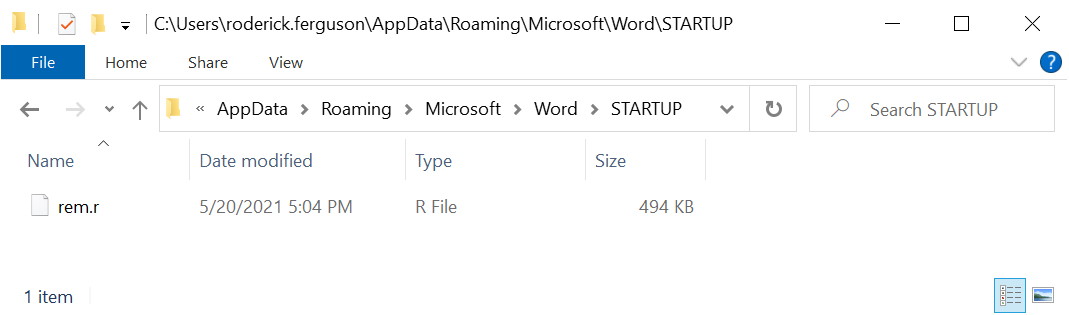
Shown above: Hancitor DLL saved to the infected Windows host.
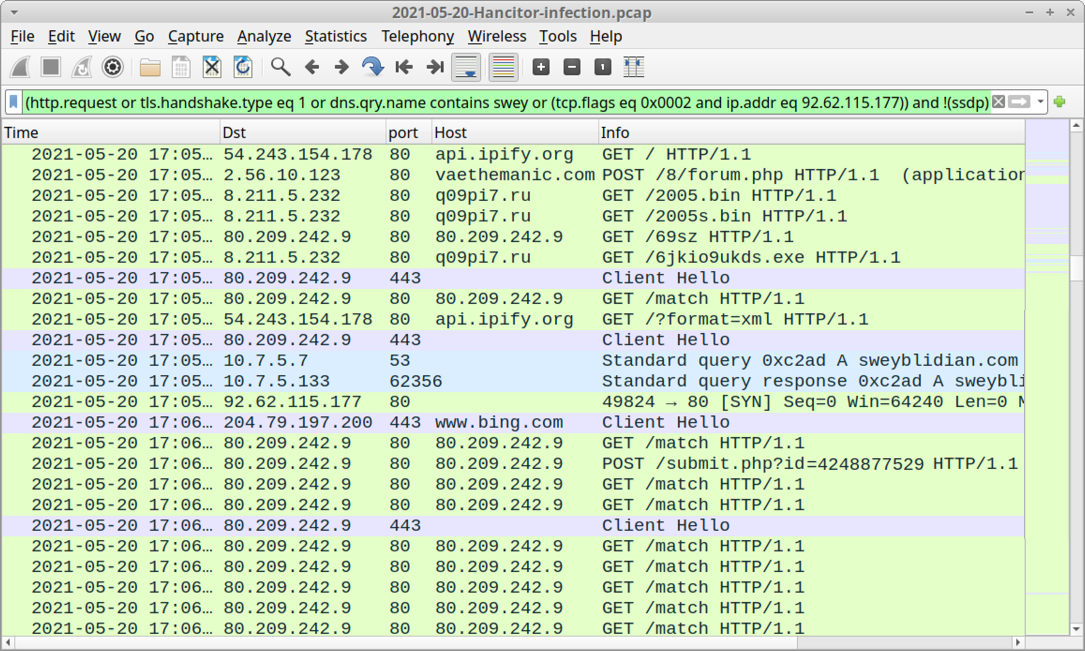
Shown above: Traffic from the infection filtered in Wireshark showing indicators of Hancitor, Ficker Stealer, and Cobalt Strike.
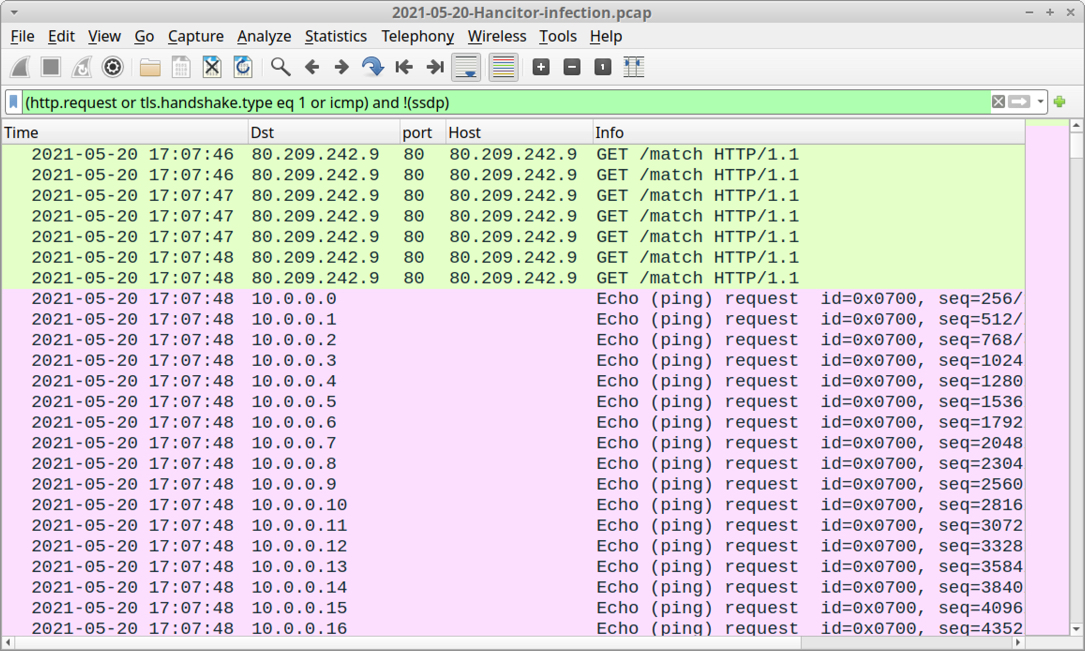
Shown above: Start of ICMP ping traffic caused by the netping tool.
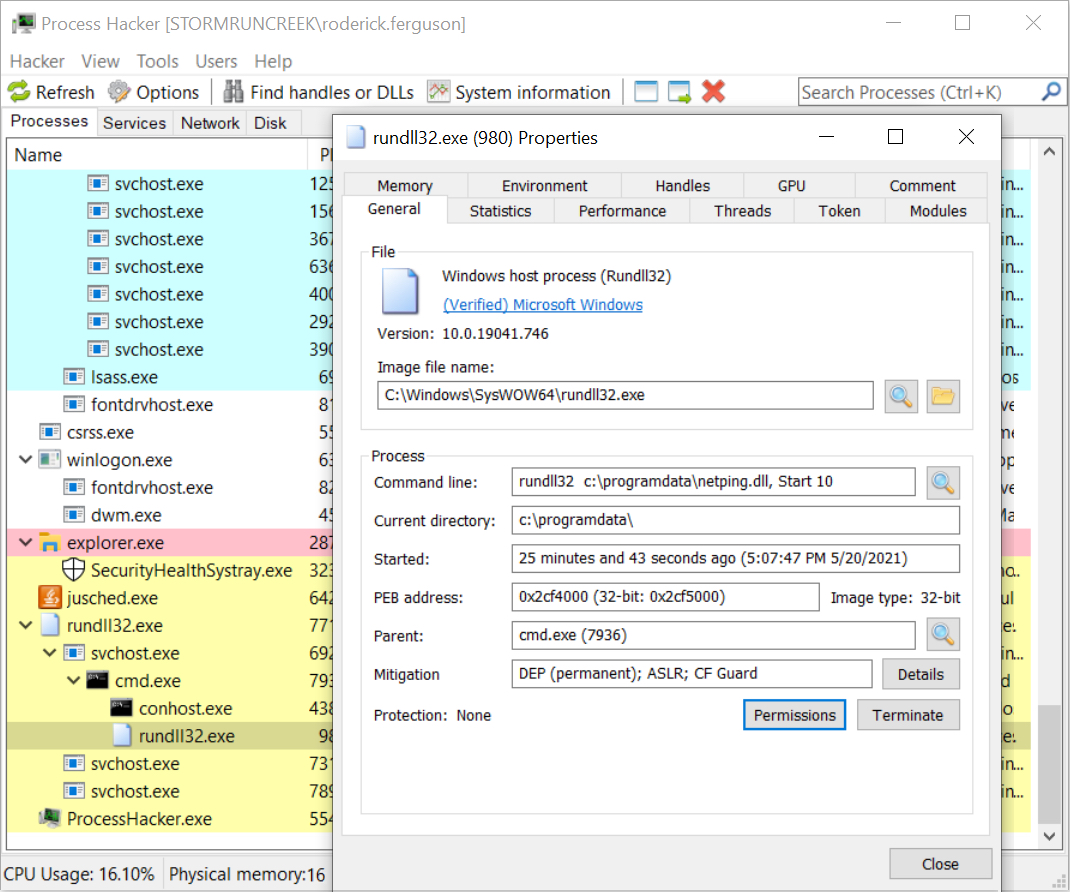
Shown above: Process from the netping tool reveals how it uses rundll32.exe to run.
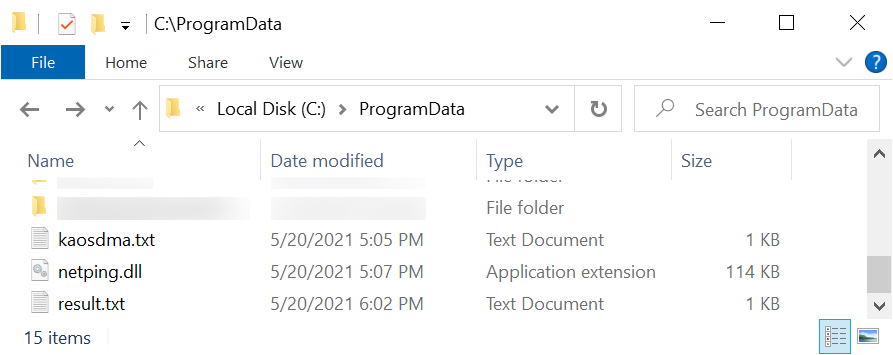
Shown above: Two artifacts from the infection related to the netping tool (kaosdma.txt contains the public IP of the infected host).
Click here to return to the main page.
