2021-06-01 (TUESDAY) - HANCITOR WITH COBALT STRIKE AND NETPING TOOL ACTIVITY
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2021-06-01-Hancitor-IOCs.txt.zip 4.1 kB (4,136 bytes)
- 2021-06-01-Hancitor-malspam-21-examples.zip 53.2 kB (53,192 bytes)
- 2021-06-01-Hancitor-with-Cobalt-Stike-and-netping-tool.pcap.zip 7.6 MB (7,578,021 bytes)
- 2021-06-01-Hancitor-and-Cobalt-Strike-malware.zip 3.8 MB (3,755,266 bytes)
NOTES:
- Reference: Hancitor's Use of Cobalt Strike and a Noisy Network Ping Tool
- Reference: Wireshark Tutorial: Examining Traffic from Hancitor Infections
IMAGES
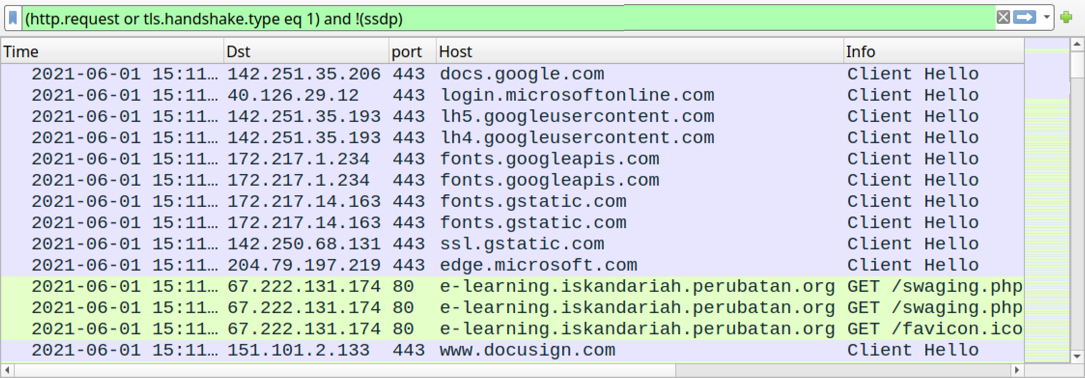
Shown above: Traffic from the infection filtered in Wireshark - part 1 of 3: going to a Google docs link from one of the emails.
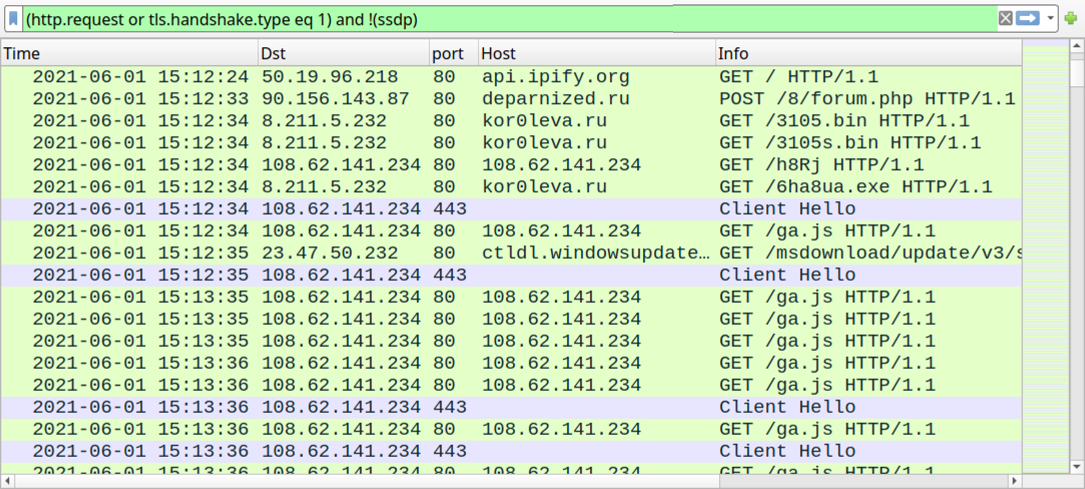
Shown above: Traffic from the infection filtered in Wireshark - part 2 of 3: Hancitor and Cobalt Strike activity starts.
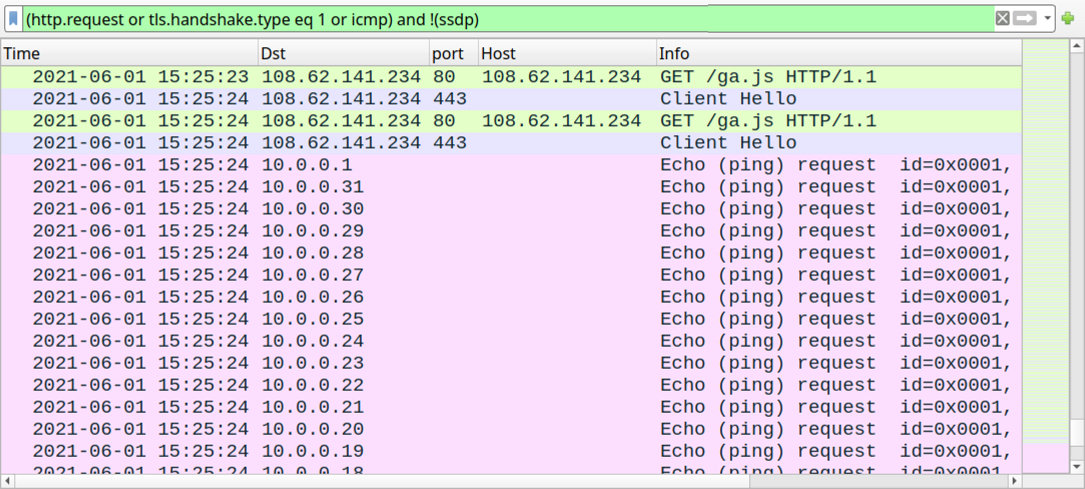
Shown above: Traffic from the infection filtered in Wireshark - part 3 of 3: netping tool activity starts.
Click here to return to the main page.
