2022-10-14 (FRIDAY) - BB02 QAKBOT (QBOT) INFECTION
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2022-10-14-bb02-Qakbot-IOCs.txt.zip 1.5 kB (1,491 bytes)
- 2022-10-14-Qakbot-bb02-malspam-2-examples.zip 4.1 kB (4,097 bytes)
- 2022-10-14-bb02-Qakbot-infection-traffic-carved-and-sanitized.pcap.zip 4.1 MB (4,095,234 bytes)
- 2022-10-14-bb02-Qakbot-malware.zip 1.2 MB (1,171,415 bytes)
IMAGES
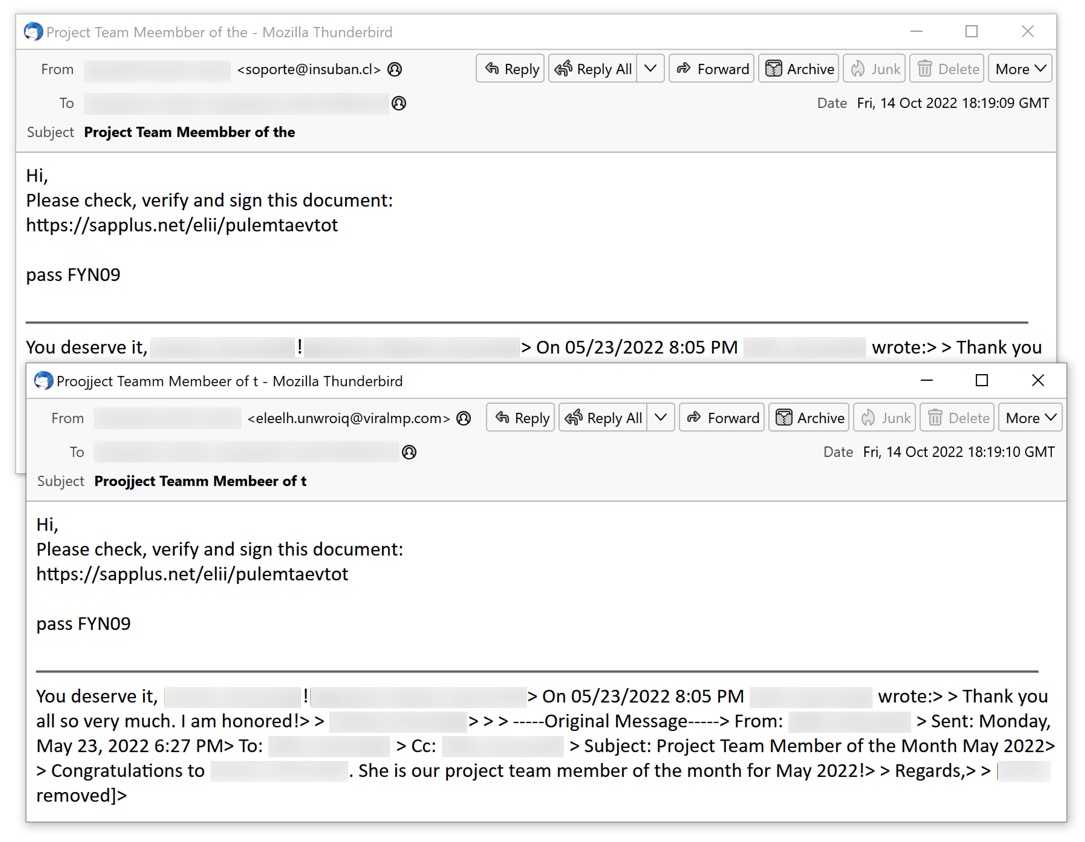
Shown above: Screenshot of the two malspam examples for bb02 malspam seen on Friday 2022-10-14.
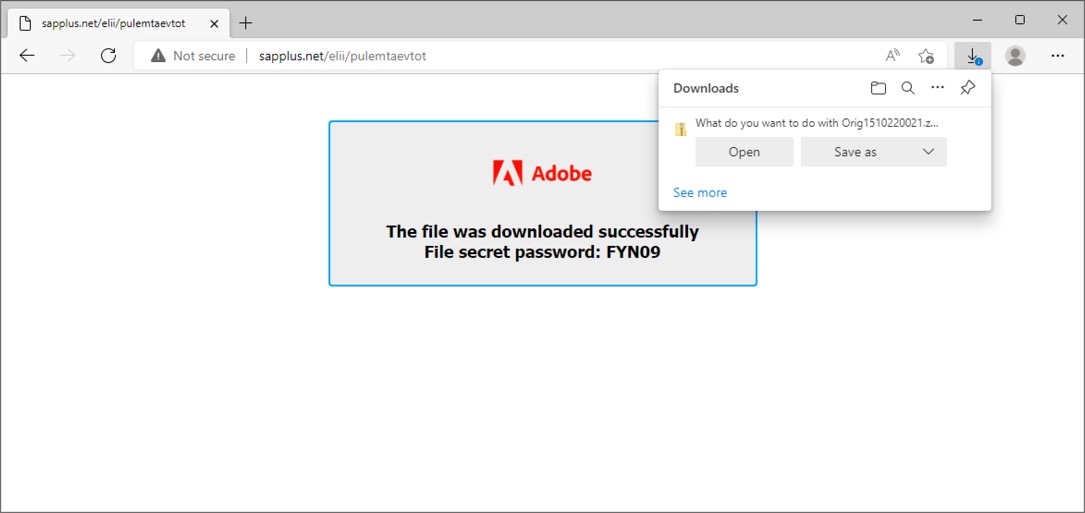
Shown above: Web browser after entering link from the email (entered as "http" instead of "https" URL).
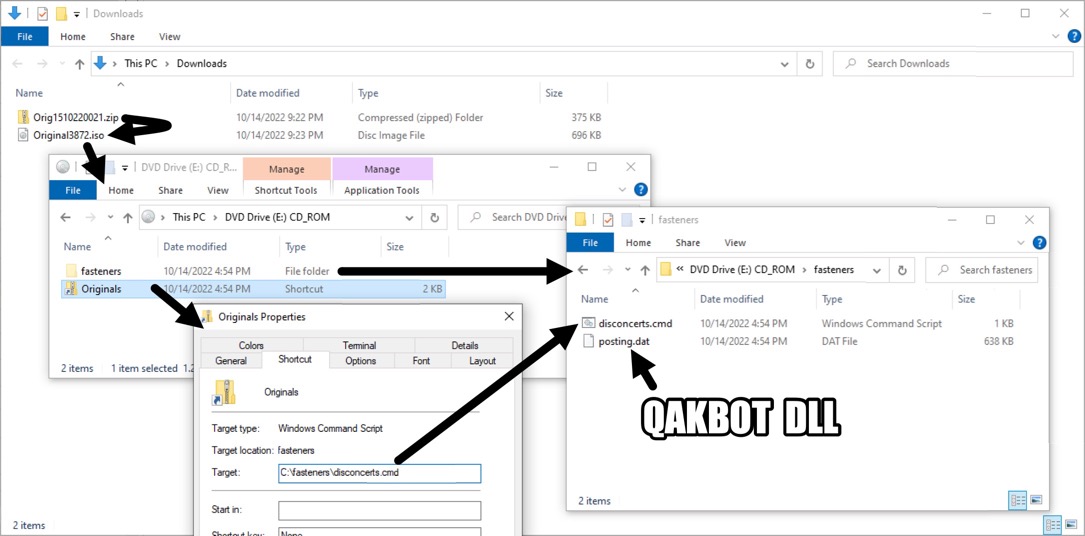
Shown above: Downloaded zip archive and contents of extracted ISO image.
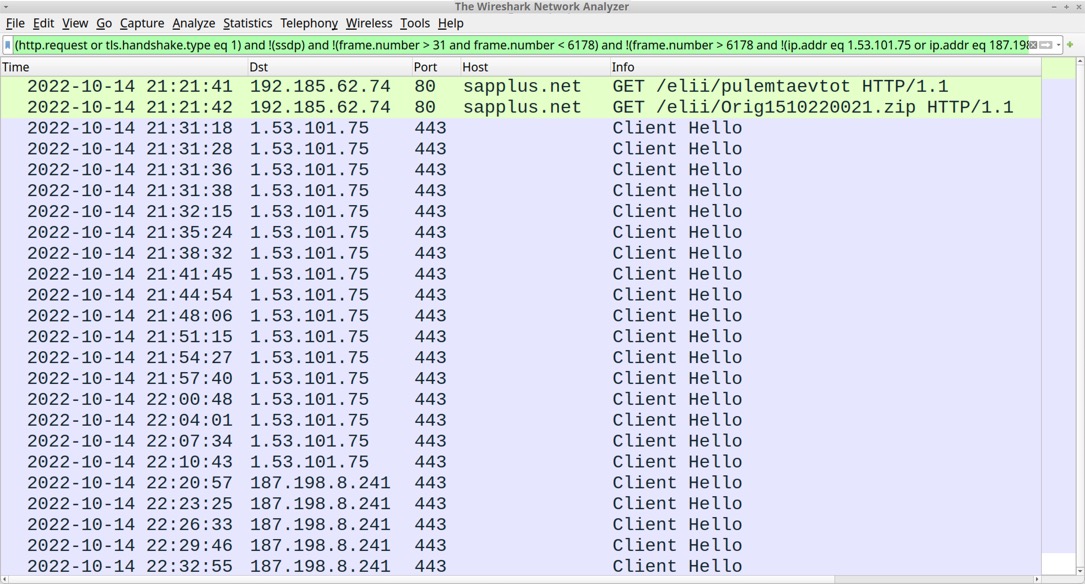
Shown above: Traffic from the infection filtered in Wireshark.
2022-10-14 (FRIDAY) BB02 QAKBOT (QBOT) INFECTION INFECTION CHAIN: - email --> link --> password-protected zip --> ISO --> Windows shortcut runs installer DLL --> Qakbot C2 LINK IN THE EMAIL: - hxxps://sapplus[.]net/elii/pulemtaevtot FILES FROM LINK IN THE EMAIL: - SHA256 hash: 7dcc02a5947410627d94c50ed37a500335ccd9d7b30cd540e174457096a54a1e - File size: 383,936 bytes - File name: Orig1510220021.zip - File location: hxxps[:]//sapplus[.]net/elii/Orig1510220021.zip - File description: Password-protected zip archive downloaded through link in the email - Password: FYN09 - SHA256 hash: f1b6767c8be1d9d0083dcc041469a5404e16ce96c60a62f76de7a88de873e0c5 - File size: 712,704 bytes - File name: Original3872.iso - File description: ISO image extracted from the above zip archive CONTENTS OF THE ISO IMAGE: - SHA256 hash: 200a604f819bcedd10258f4f58b30e1e36780a9e91c0686a1f08b4c144cc217d - File size: 1,259 bytes - File name: Originals.lnk - File description: Windows shortcut (only visible file in the ISO image) - SHA256 hash: 070272bda35f495343673b51cf871ae9e49b1aa0d3276aacc826b63768b8a860 - File size: 313 bytes - File name: fasteners\disconcerts.cmd - File description: .cmd batch script run by the above Windows shortcut - SHA256 hash: bc672fe23b19898032b312ab849d781cfd450966e17f571b8e31a0328f2bafe8 - File size: 653,312 bytes - File name: fasteners\posting.dat - File description: Windows DLL file for Qakbot, distribution tag: bb02 - Run method: regsvr32.exe [filename] TRAFFIC FROM AN INFECTED WINDOWS HOST: WEB PAGE FOR AND DELIVERY OF PASSWORD-PROTECTED ZIP ARCHIVE: - 192.185.62[.]74 port 80 - sapplus[.]net - GET /elii/pulemtaevtot - 192.185.62[.]74 port 80 - sapplus[.]net - GET /elii/Orig1510220021.zip - Note: Link from the emails was https, but used http URL for this infection. QAKBOT C2 TRAFFIC: - 1.53.101[.]75 port 443 - HTTPS traffic (TLSv1.2) - 125.20.84[.]122 port 443 - TCP connection attempts unsuccessful - 220.123.29[.]76 port 443 - TCP connection attempts unsuccessful - 197.204.233[.]216 port 443 - TCP connection attempts unsuccessful - 45.230.169[.]132 port 443 - TCP connection attempts unsuccessful - 104.233.202[.]195 port 443 - TCP connection attempts unsuccessful - 187.198.8[.]241 port 443 - HTTPS traffic (TLSv1.2) CERTIFICATE ISSUER DATA FOR QAKBOT C2 SERVER AT 1.53.101.75: - id-at-countryName=GB - id-at-stateOrProvinceName=AZ - id-at-localityName=Akfth - id-at-organizationName=Flibo Tdelirie Ouiopi LLC. - id-at-commonName=sxeuiqecowj[.]net CERTIFICATE ISSUER DATA FOR QAKBOT C2 SERVER AT 187.198.8.241: - id-at-countryName=DE - id-at-stateOrProvinceName=QE - id-at-localityName=Otcsvjgcu Zsu - id-at-organizationName=Oiumeicn Bteu Yphap Aenejfcom LLC. - id-at-commonName=sageiaeuz[.]us
Click here to return to the main page.
