2022-12-09 (FRIDAY) - HTML SMUGGLING LEADS TO QAKBOT (QBOT), DISTRIBUTION/BOTNET TAG: AZD
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
NOTES:
- The HTML file used for smuggling was posted to VirusTotal today, and create/modify dates for the disk image & its content are all 2022-12-09.
ASSOCIATED FILES:
- 2022-12-09-IOCs-for-azd-Qakbot.txt.zip 2.6 kB (2,642 bytes)
- 2022-12-09-azd-Qakbot-infection-traffic-carved-and-santized.pcap.zip 1.9 MB (1,929,146 bytes)
- 2022-12-09-azd-Qakbot-malware-and-artifacts.zip 2.0 MB (1,968,315 bytes)
IMAGES
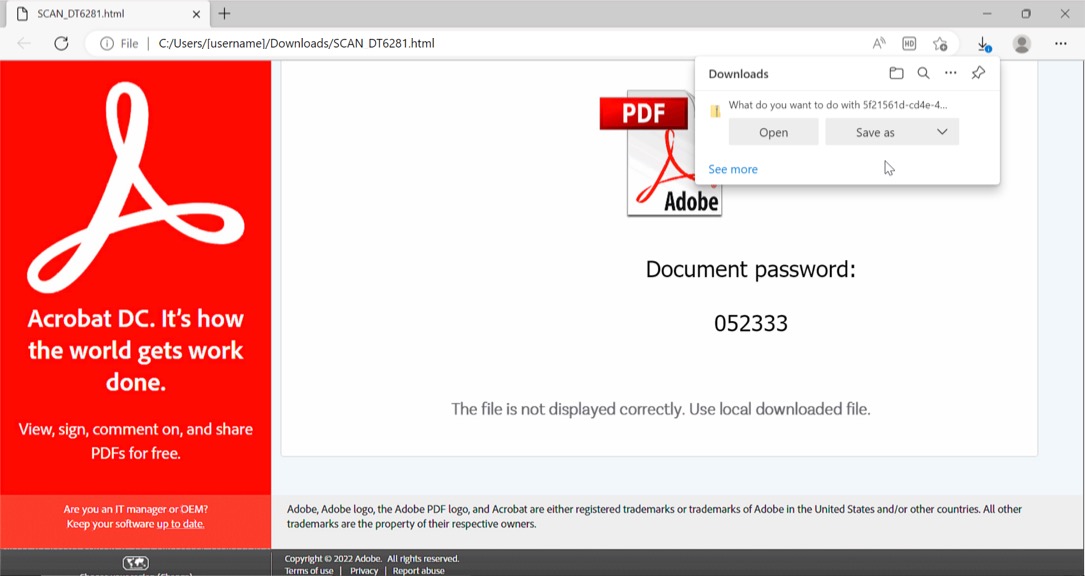
Shown above: HTML file opened in Microsoft Edge web browser.
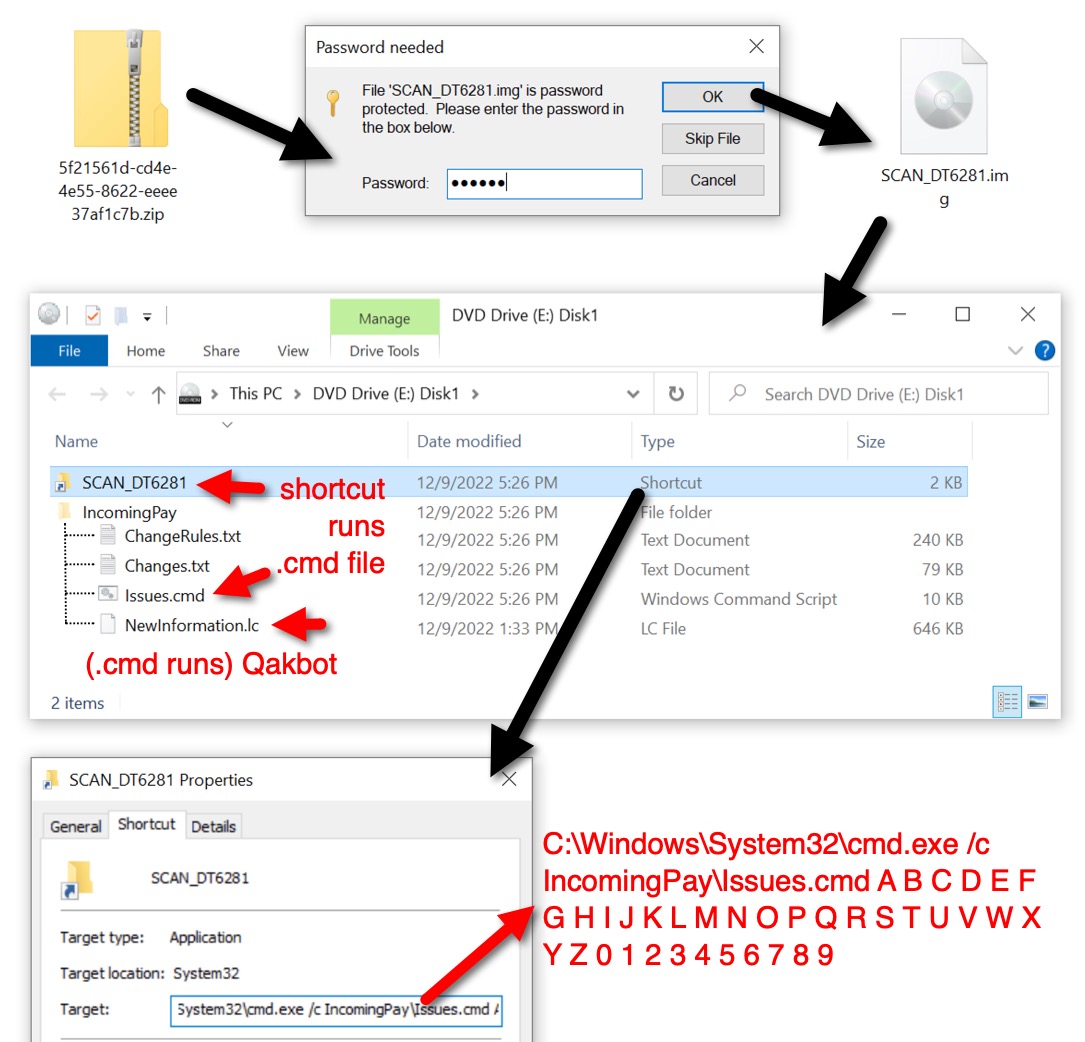
Shown above: Downloaded zip archive contains disk image with contents for Qakbot.
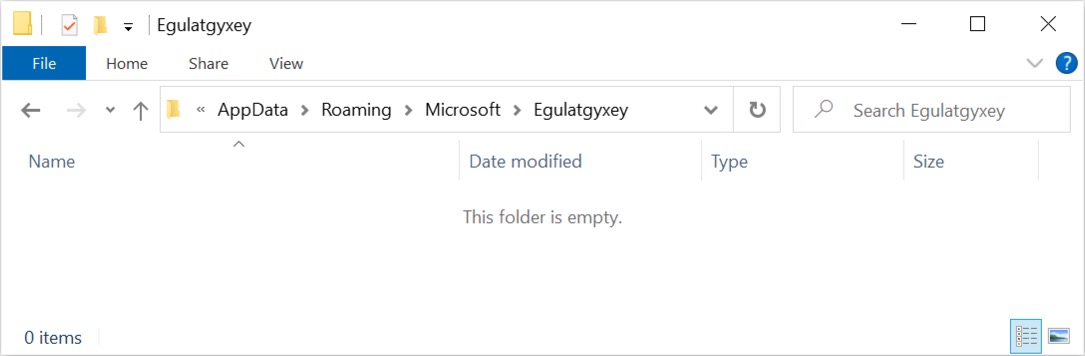
Shown above: Qakbot creates a folder named with random alphabetic characters under C:\Users\[username]\AppData\Roaming\Microsoft directory.
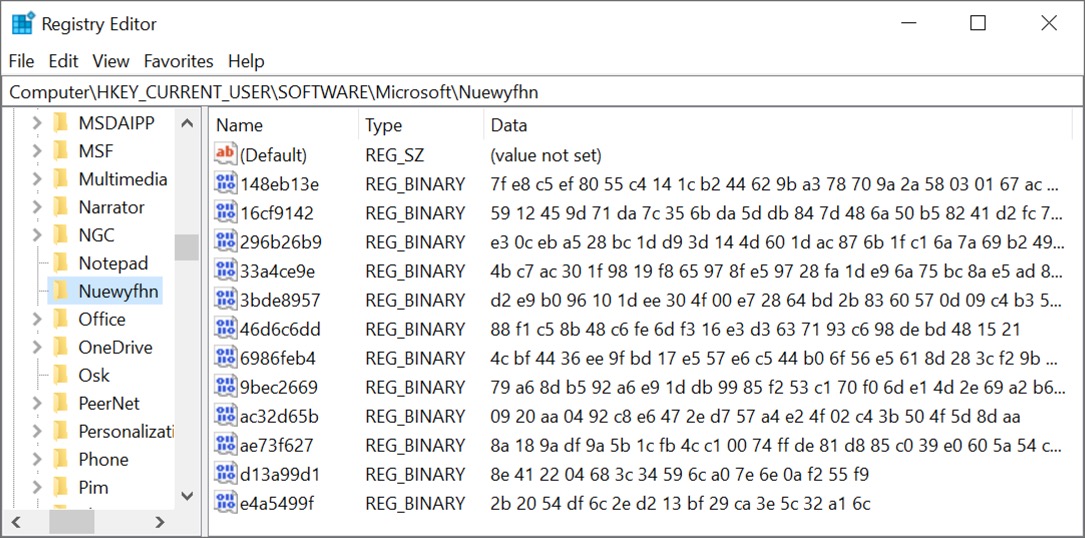
Shown above: Qakbot also creates a Windows registry key named with random alphabetic characters uder the HKCU\SOFTWARE\Microsoft.
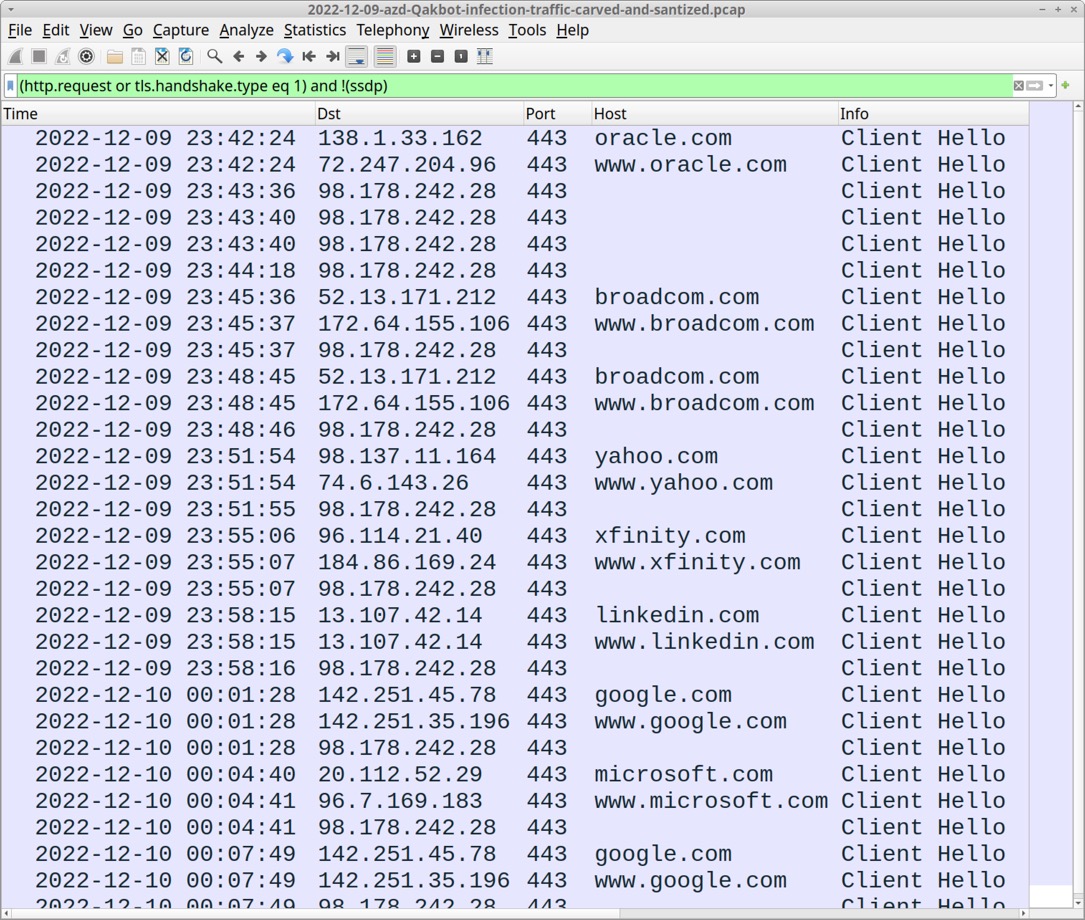
Shown above: Traffic (carved and sanitized) of the infection filtered in Wireshark.
Shown above: Active Qakbot C2 server viewed in Firefox web browser.
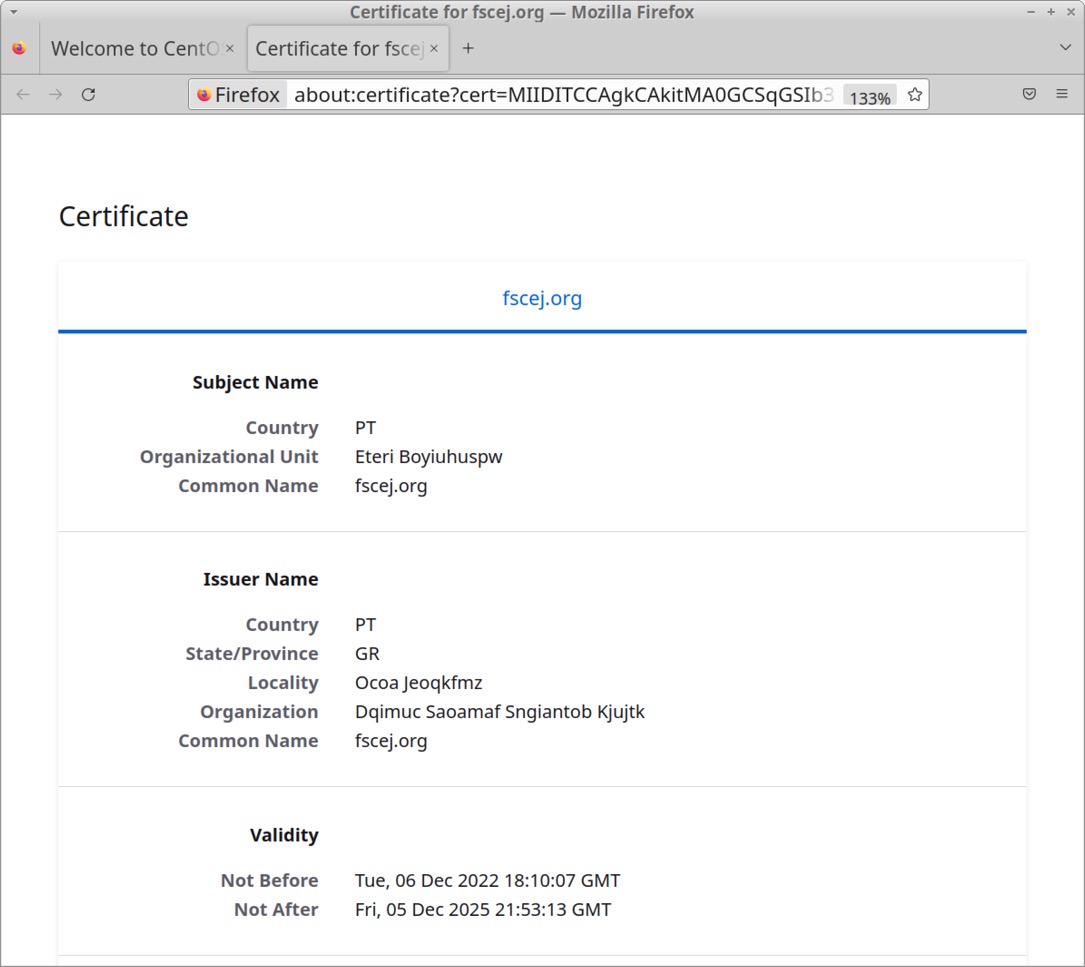
Shown above: Certificate data from Qakbot C2 server for HTTPS traffic shown in Firefox.
2022-12-09 (FRIDAY) - HTML SMUGGLING FOR QAKBOT (QBOT) DISTRIBUTION TAG: AZD
DISTRIBUTION:
- Unknown source (email?) --> HTML file --> password-protected zip archive --> extracted ISO image with .img file extension
INFECTION FROM DISK IMAGE:
- Visible Windows shortcut runs --> .cmd file with obfuscated script, which runs --> Qakbot DLL
DISTRIBUTION FILES:
- SHA256 hash: 4efc4cc462a27245945ee90465caef589b71c41b33bf6d24ce2e6f74b75fdbe7
- File size: 1,287,748 bytes
- File name: SCAN_DT6281.html
- File description: HTML file used for HTML smuggling, generates password-protected zip archive
- SHA256 hash: b393d0b041aeb2299936d2362b67e324e7a8c6765a5bfacdabff3c4820c841c7
- File size: 369,344 bytes
- File name: 5f21561d-cd4e-4e55-8622-eeee37af1c7b.zip
- File description: Password-protected zip archive generated by above HTML file
- Password: 052333
- SHA256 hash: cc1fdbde529da88eeab58ff1695c80d2be68df600024860b3b9622c8a312affa
- File size: 1,056,768 bytes
- File name: SCAN_DT6281.img
- File description: Extracted from above zip, this is an ISO disk image with an .img file extension
DISK IMAGE CONTENTS:
- SHA256 hash: 1aa40f0bcf14d02d5aa184c70f2d9fb8e20532777a63094580abf1d79d2525e6
- File size: 1,972 bytes
- File name: SCAN_DT6281.lnk
- File description: Windows shortcut, only visible file in disk image
- Shortcut: C:\Windows\System32\cmd.exe /c IncomingPay\Issues.cmd A B C D E F G H I J K L M N O P Q
R S T U V W X Y Z 0 1 2 3 4 5 6 7 8 9
- SHA256 hash: 20e3441a46717fc6cd0ad5a4dca25246c211e8c355755dae067c45ff2d97f59b
- File size: 9,577 bytes
- File name: IncomingPay\Issues.cmd
- File description: In hidden directory, .cmd file run by above shortcut
- SHA256 hash: f4f8a14f76055dbe55422ba8754582ed8abf139b7ed33630fa656cb7e879bc7d
- File size: 660,992 bytes
- File name: IncomingPay\NewInformation.lc
- File description: In hidden directory, Qakbot DLL run by above .cmd file
- Qakbot version: 404.30
- Qakbot distribution tag/botnet: azd
- Run method: regsvr32.exe /s NewInformation.lc
- Analysis: https://tria.ge/221209-2j4zssee88
- File name: IncomingPay\ChangeRules.txt
- File description: Decoy text file in hidden directory (from psyhcology paper or publication)
- File name: IncomingPay\Changes.txt
- File description: Decoy text file in hidden directory (from psyhcology paper or publication)
QAKBOT C2 TRAFFIC:
- legitimate domains for connectivity checks before each attempt at C2 traffic
- 98.178.242[.]28:443 - HTTPS traffic for Qakbot C2
CERTIFICATE DATA FOR HTTPS TRAFFIC FROM QAKBOT SERVER AT 98.178.242.28:443:
- Subject Name:
- Country: PT
- Organizational Unit: Eteri Boyiuhuspw
- Common Name: fscej[.]org
- Issuer Name:
- Country: PT
- State/Province: GR
- Locality: Ocoa Jeoqkfmz
- Organization: Dqimuc Saoamaf Sngiantob Kjujtk
- Common Name: fscej[.]org
- Validity:
- Not Before: Tue, 06 Dec 2022 18:10:07 GMT
- Not After: Fri, 05 Dec 2025 21:53:13 GMT
120 QAKBOT C2 IP ADDRESSES EXTRACTED FROM THE DLL (BASED ON TRIA.GE ANALYSIS):
- 2.99.47[.]198:2222
- 12.172.173[.]82:22
- 12.172.173[.]82:465
- 12.172.173[.]82:990
- 12.172.173[.]82:993
- 12.172.173[.]82:995
- 12.172.173[.]82:50001
- 24.69.87[.]61:443
- 24.71.120[.191:443
- 24.142.218[.]202:443
- 24.206.27[.]39:443
- 27.109.19[.]90:2078
- 31.53.29[.]245:2222
- 38.166.226[.]185:2087
- 41.228.226[.]109:995
- 46.10.198[.]106:443
- 47.16.76[.]35:2222
- 47.34.30[.]133:443
- 47.41.154[.]250:443
- 50.68.204[.]71:443
- 50.68.204[.]71:995
- 50.90.249[.]161:443
- 64.121.161[.]102:443
- 66.85.236[.]205:2222
- 66.180.226[.]117:2222
- 66.191.69[.]18:995
- 67.61.71[.]201:443
- 69.119.123[.]159:2222
- 70.51.153[.]251:2222
- 70.66.199[.]12:443
- 70.77.116[.]233:443
- 70.115.104[.]126:995
- 70.121.198[.]103:2078
- 71.31.101[.]183:443
- 71.247.10[.]63:995
- 72.200.109[.]104:443
- 73.29.92[.]128:443
- 73.36.196[.]11:443
- 73.155.10[.]79:443
- 74.66.134[.]24:443
- 75.98.154[.]19:443
- 75.99.125[.]236:2222
- 75.143.236[.]149:443
- 76.80.180[.]154:995
- 76.100.159[.]250:443
- 78.69.251[.]252:2222
- 80.13.179[.]151:2222
- 81.229.117[.]95:2222
- 81.248.77[.]37:2222
- 82.9.210[.]36:443
- 83.213.192[.136:443
- 84.35.26[.14:995
- 84.113.121[.]103:443
- 85.7.61[.]22:2222
- 85.61.165[.]153:2222
- 86.96.75[.]237:2222
- 86.130.9[.]250:2222
- 86.165.15[.]180:2222
- 86.171.75[.]63:443
- 86.190.16[.]164:443
- 87.202.101[.]164:50000
- 87.221.197[.]110:2222
- 87.223.91[.]46:443
- 88.126.94[.]4:50000
- 90.4.193[.]117:2222
- 90.66.229[.]185:2222
- 90.79.129[.166:2222
- 90.104.22[.]28:2222
- 90.221.1.60:443
- 91.68.227[.]219:443
- 91.165.188[.]74:50000
- 91.169.12[.]198:32100
- 91.171.148[.]162:50000
- 91.180.68[.]95:2222
- 92.8.190[.]211:2222
- 92.27.86[.]48:2222
- 92.154.17[.]149:2222
- 92.189.214[.]236:2222
- 93.156.98[.]63:443
- 94.30.98[.]134:32100
- 98.145.23[.]67:443
- 98.147.155[.]235:443
- 98.178.242[.]28:443
- 98.187.21[.]2:443
- 99.229.164[.]42:443
- 99.251.67[.]229:443
- 100.8.168[.]108:443
- 103.71.21[.]107:443
- 108.6.249[.]139:443
- 109.11.175[.]42:2222
- 109.76.25[.]214:443
- 109.145.40[.]125:443
- 121.122.99[.]223:995
- 123.3.240[.]16:995
- 136.35.241[.]159:443
- 141.255.65[.]113:995
- 172.117.139[.]142:995
- 172.90.139[.]138:2222
- 173.18.126[.]3:443
- 173.239.94[.]212:443
- 174.104.184[.]149:443
- 176.133.4[.]230:995
- 178.191.21[.]187:995
- 184.189.41[.]80:443
- 184.68.116[.]146:2222
- 184.68.116[.]146:3389
- 184.68.116[.]146:50010
- 185.135.120[.]81:443
- 188.48.123[.]229:995
- 188.79.182[.]186:2222
- 190.24.45[.]24:995
- 193.32.212[.]114:443
- 193.253.100[.]236:2222
- 197.94.213[.]23:443
- 199.83.165[.]233:443
- 201.137.151[.]25:443
- 201.208.139[.]250:2222
- 208.180.17[.]32:2222
- 213.67.255[.]57:2222
- 217.128.91[.]196:2222
Click here to return to the main page.
