2023-02-03 (FRIDAY) - DEV-0569 ACTIVITY: GOOGLE AD --> "FAKEBAT" LOADER --> REDLINE STEALER & GOZI/ISFB/URSNIF
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
NOTES:
- IOCs are listed on this page below all of the images.
ASSOCIATED FILES:
- 2023-02-03-IOCs-for-DEV-0569-FakeBat-activity.txt.zip 2.6 kB (2,637 bytes)
- 2023-02-03-DEV-0569-pcaps.zip 27.7 MB (27,651,779 bytes)
- 2023-02-03-DEV-0569-malware-and-artifacts.zip 19.0 MB (19,044,796 bytes)
IMAGES
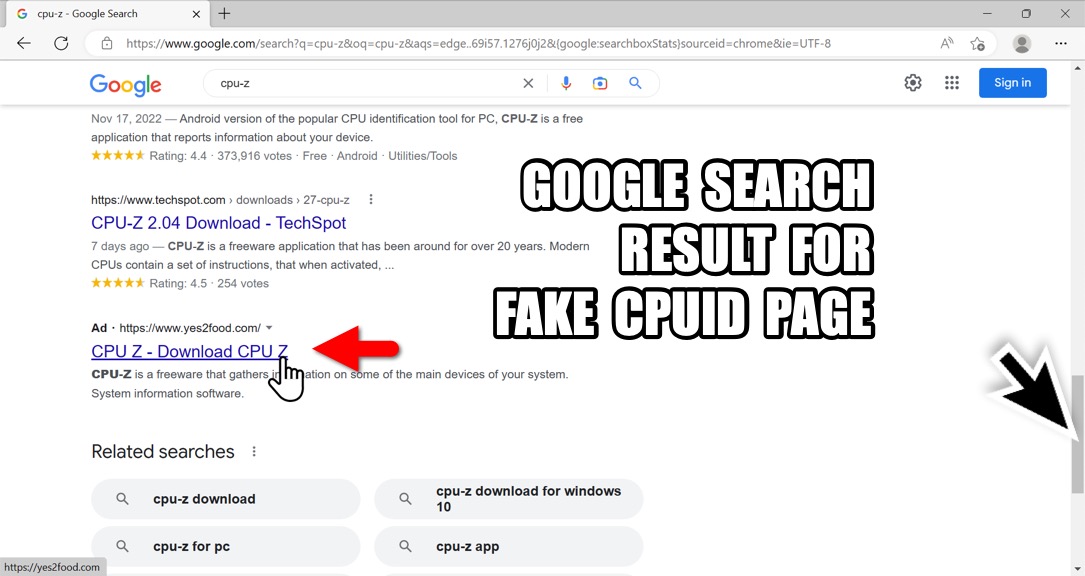
Shown above: Malicious Google ad.
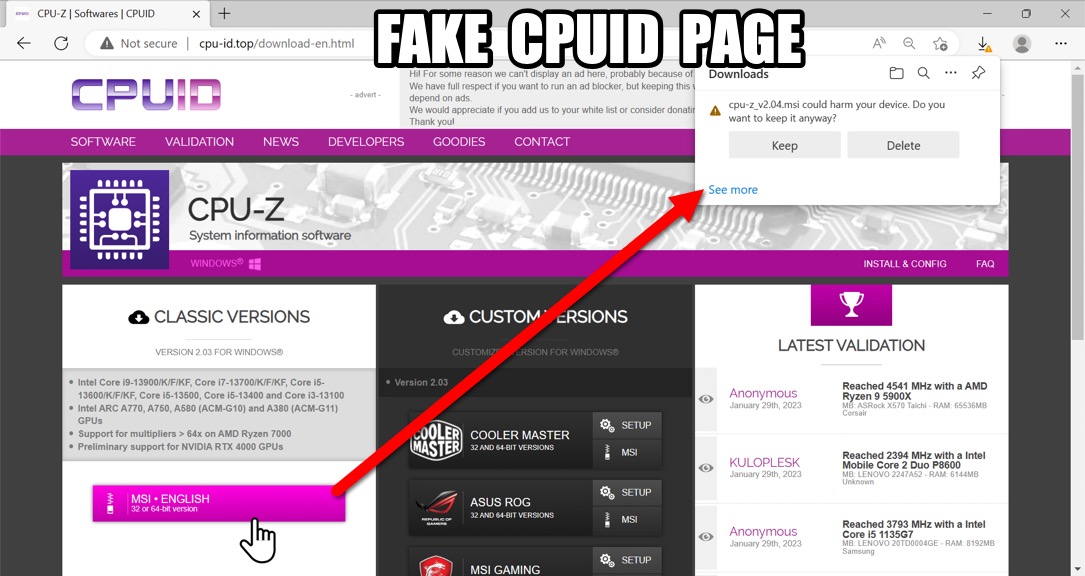
Shown above: Downloading .msi file from fake CPUID page.
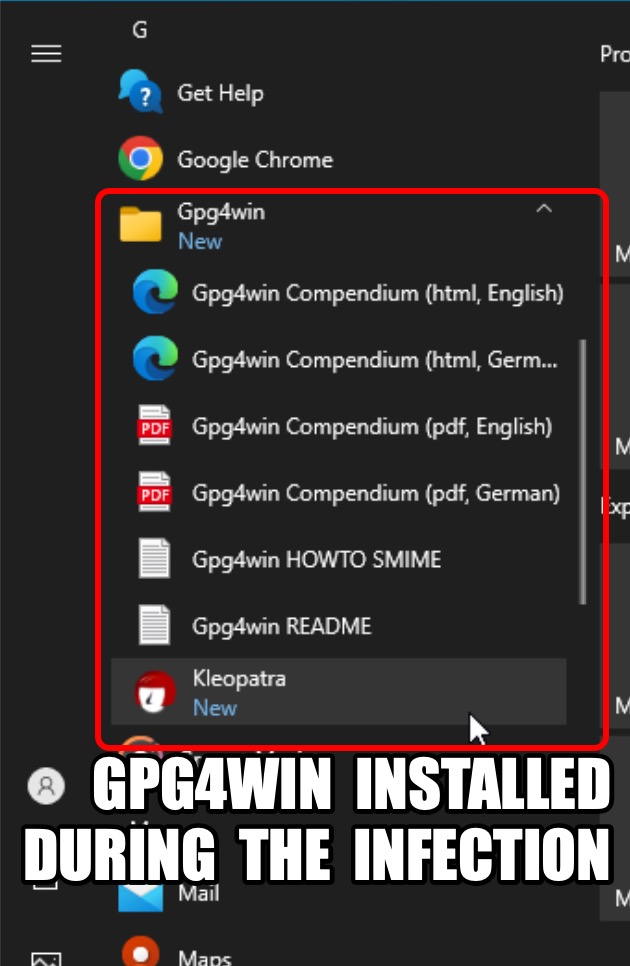
Shown above: The infection installs CPU-Z, and it also installs Gpg4win.
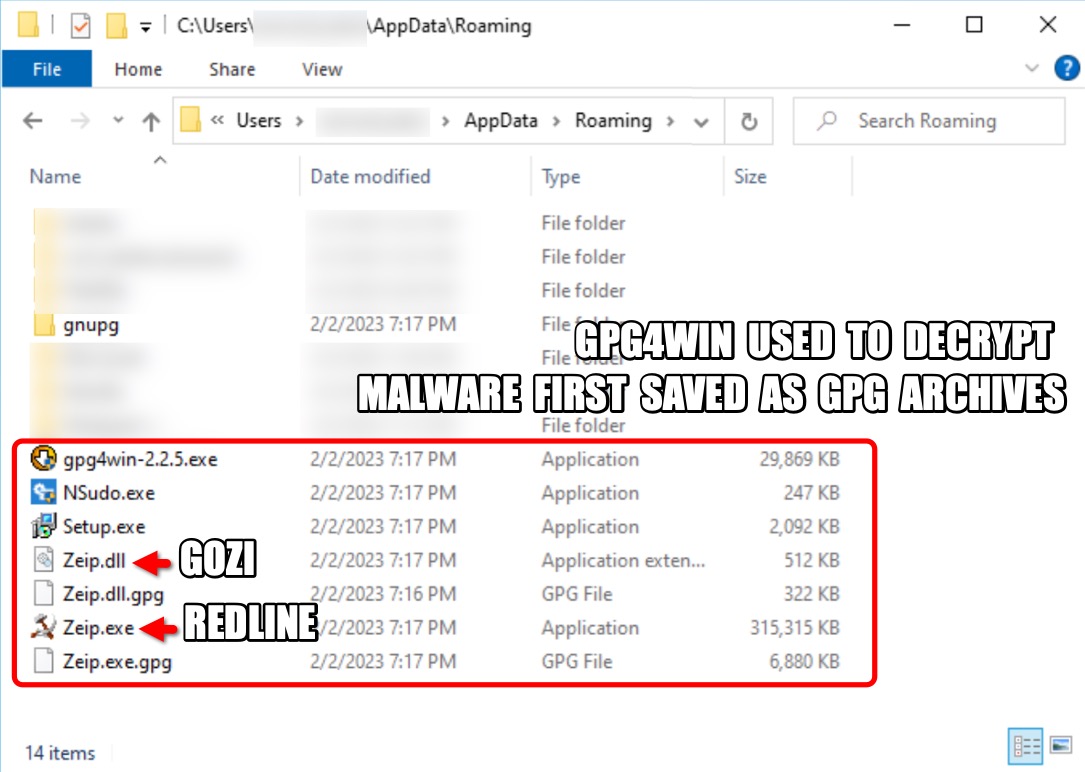
Shown above: Gpg4win is used (along with NSudo) to decrypt malware first saved ot the victim as encrypted GPG archives.
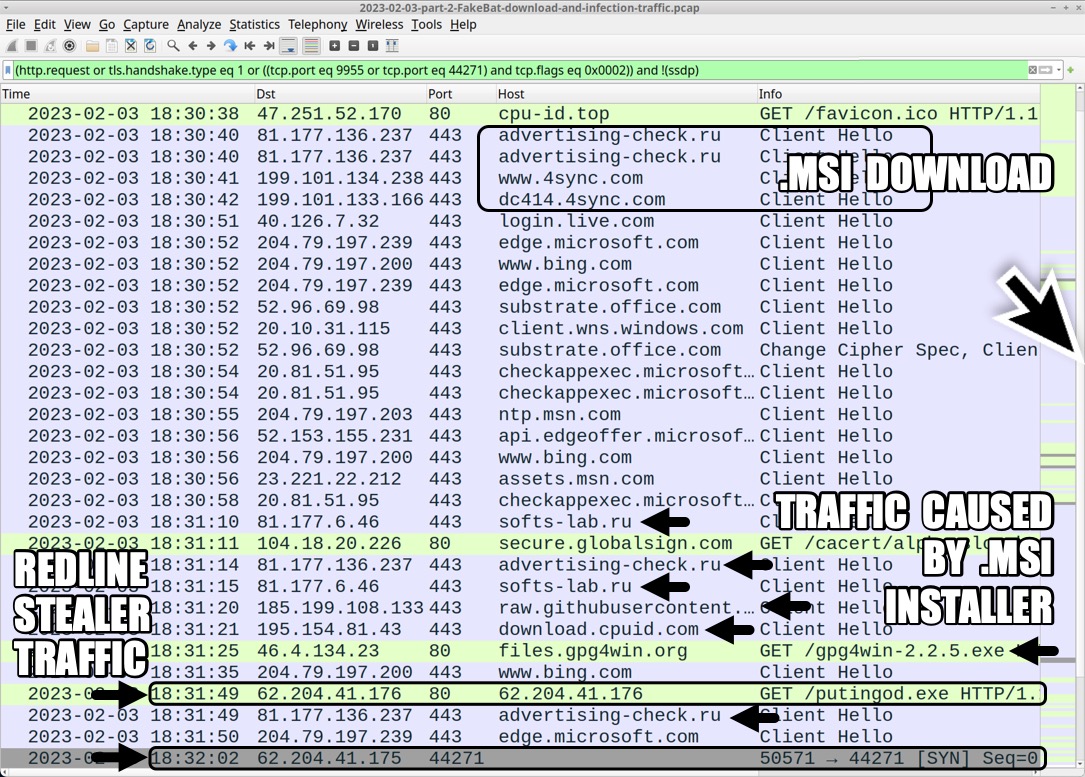
Shown above: Traffic from the infection, filtered in Wireshark (1 of 2).
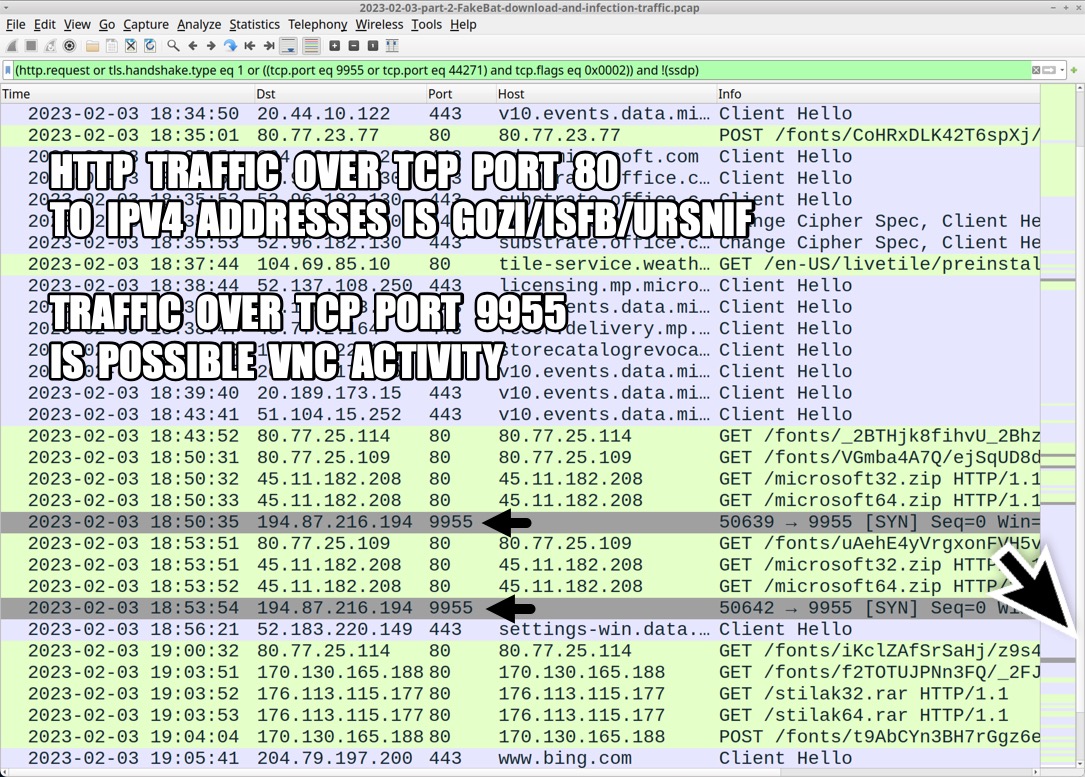
Shown above: Traffic from the infection, filtered in Wireshark (2 of 2).
2023-02-03 (FRIDAY) - DEV-0569 ACTIVITY: GOOGLE AD --> "FAKEBAT" LOADER --> REDLINE STEALER & GOZI/ISFB/URSNIF NOTES: - This threat actor has been tracked as DEV-0569 by Microsoft. See: https://www.microsoft.com/en-us/security/blog/2022/11/17/ dev-0569-finds-new-ways-to-deliver-royal-ransomware-various-payloads/ - The attack chain here mimics Batloader, but there is no .bat file during the infection process, so @lazyactivist192 and others are calling this "FakeBat" - I've reported on this before at: https://twitter.com/Unit42_Intel/status/1615470858067222568 MALICIOUS GOOGLE AD: - hxxps[:]//www.googleadservices[.]com/pagead/aclk?sa=L&ai=DChcSEwiGufrG2Pn8AhXXFNQBHd49DQUYABABGgJvYQ&ae=2&ohost=www.google.com &cid=CAASJeRosOoEI6ls5zSi9RHb4hCVQ_MhjKIc0VqOwbs4ohbHwzbnHmM&sig=AOD64_2Gqyp6QJi6H5xc9NfTzrrbjnyYCw&q&adurl& ved=2ahUKEwi7vfPG2Pn8AhW0lmoFHcYWBOgQ0Qx6BAgKEAE REDIRECT FROM ABOVE GOOGLE AD: - 141.136.41[.]216 - hxxps[:]//yes2food[.]com/?utm_source=google&utm_medium=cpc&utm_term=cpu%20z&utm_content=647039221421& utm_campaign=cpc&gclid=EAIaIQobChMIhrn6xtj5_AIV1xTUAR3ePQ0FEAAYASAAEgLtrvD_BwE FAKE CPUID WEBSITE TO DOWNLOAD MALICIOUS CPU-Z INSTALLER: - 47.251.52[.]170 - hxxp[:]//cpu-id[.]top/download-en.html LINK CHAIN TO DOWNLOAD MALICIOUS CPU-Z INSTALLER: - 81.177.136[.]237 - hxxps[:]//advertising-check[.]ru/0302cpuz.php?site=cpu-z - hxxps[:]//www.4sync[.]com/web/directDownload/v6VPdorJ/342jLuve.8965e4898f35a73954f5d870f9c3fd3a - hxxps[:]//dc414.4sync[.]com/download/v6VPdorJ/cpu-z_v204.msi?dsid=342jLuve.8965e4898f35a73954f5d870f9c3fd3a& sbsr=9ae9dae53fe99ceba29de07148ab0072ad2&bip=MTcyLjU2Ljg5LjE5&lgfp=40 MALICIOUS CPU-Z INSTALLER: - SHA256 hash: c6e79473526e0c70389c7cf6c31987ef23cd59b4012b614dcb545d085118ef80 - File size: 2,517,504 bytes - File name: cpu-z_v2.04.msi - File description: Malicious CPU-Z installer downloaded from fake CPU-Z website TRAFFIC GENERATED BY THE ABOVE .MSI INSTALLER: - 81.177.6[.]46 - hxxps[:]//softs-lab[.]ru/cpuz.gpg - 81.177.136[.]237 - hxxps[:]//advertising-check[.]ru/start.php - 81.177.6[.]46 - hxxps[:]//softs-lab[.]ru/Zeip.dll.gpg - 81.177.6[.]46 - hxxps[:]//softs-lab[.]ru/Zeip.exe.gpg - hxxps[:]//raw.githubusercontent[.]com/swagkarna/Bypass-Tamper-Protection/main/NSudo.exe <-- legitimate file - hxxps[:]//download.cpuid[.]com/cpu-z/cpu-z_2.03-en.exe <-- legitimate file - hxxp[:]//files.gpg4win[.]org/gpg4win-2.2.5.exe <-- legitimate file - 81.177.136[.]237 - hxxps[:]//advertising-check[.]ru/install.php FOLLOW-UP MALWARE & ARTIFACTS: - SHA256 hash: d67275e2cd7f5764d1d7fe088fa1683bc9aa873447e82d02fc2c6da2e11f01bc - File size: 329,374 bytes - File location: hxxps[:]//softs-lab[.]ru/Zeip.dll.gpg - File location: C:\Users\[username]\AppData\Roaming\Zeip.dll.gpg - File description: GPG-encrypted archive containing Zeip.dll installer for Gozi/ISFB/Ursnif - GPG archive password: putingod - SHA256 hash: 59efe4a482adfd9e8e7268f3c6a14bef578e07cba6ff42a8f7d59b5507530cb7 - File size: 524,288 bytes - File location: C:\Users\[username]\AppData\Roaming\Zeip.dll - File description: 32-bit DLL installer for Gozi/ISFB/Ursnif - Run method: rundll32.exe [filename],DllRegisterServer - SHA256 hash: 666e5755e21665e8fd2a26425563d05f1cbd0a5024ad763c71e6d62e68cac438 - File size: 7,044,895 bytes - File location: hxxps[:]//softs-lab[.]ru/Zeip.exe.gpg - File location: C:\Users\[username]\AppData\Roaming\Zeip.exe.gpg - File description: GPG-encrypted archive containing Zeip.exe installer for Redline Stealer - GPG archive password: putingod - SHA256 hash: c02db47d33f1c7f8bcf3ce5c6f0cdd4bbb0d15e2b36558b26cd628856379ae65 - File size: 322,882,560 bytes - File location: C:\Users\[username]\AppData\Roaming\Zeip.exe - File description: inflated 32-bit EXE (322 MB) installer for Redline Stealer - SHA256 hash: fba6b3f7909d608fca29e3159cb8b32129899c3b6f1e269ae509e8f8d95d15df - File size: 260,608 bytes - File location: hxxp[:]//62.204.41[.]176/putingod.exe - File description: 32-bit EXE for Redline Stealer retrieved by above installer REDLINE STEALER TRAFFIC: - 62.204.41[.]176 port 80 - hxxp[:]//62.204.41[.]176/putingod.exe - 62.204.41[.]175 port 44271 - TCP traffic for data exfiltration GOZI/ISFB/URSNIF TRAFFIC: - 80.77.23[.]77 port 80 - 80.77.23[.]77 - GET /fonts/[base64 string with backslashes and underscores].bak - 80.77.23[.]77 port 80 - 80.77.23[.]77 - POST /fonts/[base64 string with backslashes and underscores].dot - 80.77.25[.]114 port 80 - 80.77.25[.]114 - GET /fonts/[base64 string with backslashes and underscores].csv - 80.77.25[.]109 port 80 - 80.77.25[.]109 - GET /fonts/[base64 string with backslashes and underscores].csv - 80.77.25[.]109 port 80 - 80.77.25[.]109 - POST /fonts/[base64 string with backslashes and underscores].dot - 170.130.165[.]188 port 80 - 170.130.165[.]188 - GET /fonts/[base64 string with backslashes and underscores].csv - 170.130.165[.]188 port 80 - 170.130.165[.]188 - POST /fonts/[base64 string with backslashes and underscores].dot GOZI/ISFB/URSNIF MODULES OR RELATED MALWARE: - 45.11.182[.]208 port 80 - 45.11.182[.]208 - GET /microsoft32.zip - 45.11.182[.]208 port 80 - 45.11.182[.]208 - GET /microsoft64.zip - 176.113.115[.]177 port 80 - 176.113.115[.]177 - GET /stilak32.rar - 176.113.115[.]177 port 80 - 176.113.115[.]177 - GET /stilak64.rar - NOTE: The above URLs do not return .zip or .rar archives, but encoded or encrypted binaries. FOLLOW-UP TRAFFIC AFTER MICROSOFT64.ZIP MODULE: - 194.87.216[.]194 port 9955 - TCP traffic, possible VNC activity
Click here to return to the main page.
