2025-05-06 (TUESDAY): RASPBERRY ROBIN ACTIVITY
NOTES:
- Zip files are password-protected. Of note, this site has a new password scheme. For the password, see the "about" page of this website.
ASSOCIATED FILES:
- 2025-05-06-IOCs-for-Raspberry-Robin-infection.txt.zip 2.9 kB (2,940 bytes)
- 2025-05-06-Raspberry-Robin-infection-traffic.pcap.zip 73.2 MB (73,212,723 bytes)
- 2025-05-06-Raspberry-Robin-malware-samples.zip 10.6 MB (10,642,127 bytes)
BACKGROUND INFO:
- Malpedia entry on Rasbpery Robin
- Malware-Traffic-Analysis.net: 2024-11-14: Raspberry Robin infection using WebDAV server
2025-05-06 (TUESDAY): RASPBERRY ROBIN INFECTION INFECTION CHAIN: - unknown source --> initial zip archives --> extracted .hta files --> retrieves .cab file from WebDAV server --> extracts Raspberry Robin DLL from the .cab file --> runs Raspberry Robin DLL NOTES: - The initial zip archives have a .7z file extension and contain a zip archive within. - Most extraction tools will directly extract the .hta files from these zip archives using this "zip in a zip" structure. 10 EXAMPLES OF INITIAL ZIP ARCHIVES WITH .7Z FILE EXTENSION: - a2ddc6a4bf22a232708cfee813be383fb5887ee3f21dcb85df4ff427e2cef15f - 766 bytes - 405_colors_color-modes.7z - 6070988468695accf6c6d2de1f28037714618882d70a232d7bdc4b6f91496bfc - 732 bytes - 531_offcanvas_context.7z - 77910d871e3f122b57ff95c68941f726d97e495f47c483fed99171e0093941b5 - 706 bytes - 04239_long_items.7z - d8d242ce3a27bbe20e9eac4d50687bb82f5caeb84742472c3fae0a2af341d9fe - 752 bytes - 30167_configure_last.7z - 156bc2fd68398fa7446b7b6abc63f17b5c8984e10f0e50766fc4ef07c1c7c33d - 726 bytes - 4169_resolver_paths.7z - 3a77017b2ee3ae1ddb631182263098234cf2ddd4fad1adaa0698f990f0e9d9d9 - 722 bytes - 9538601_spawn_streams.7z - e8797719d71ae84147c77deec6e4951825367c217b9a06cd549b15ee1b92c16e - 730 bytes - 7954_update_core.7z - b3cc2ab2d31a91b5933bfe1f33230a34307be4655858e577f934de8c17964c17 - 748 bytes - 601837_usage_alias.7z - 412bd99c58b3477c7206c4fc4798683e4b6ab9e82f518db9f0c9aa021dc3fab4 - 764 bytes - 3905_utils_file.7z - c9b1e68d75e805a92891feab0564e87c31c1b42e0401f8b26c0e7e7a69e56fff - 728 bytes - 8467109_owner_view.7z 10 ZIP ARCHIVES CONTAINED IN THE ABOVE INITIAL ZIP ARCHIVES: - 25065def52720f18a3e2c060b9837c00b3eb4ac60926a130b7e5ab58182c18e6 - 323 bytes - color-modes - 38448d46f5ab9cd77af8294b0886c19bb422f86e6f45925905b394269f486ec9 - 310 bytes - context - 5e50f1d7ee2ab78e906a6affff36e9f60f410411366d6c1a0086bedf15ff4920 - 299 bytes - items - 6bfa2a17490a327c1b1e96caca66a8decd42f7c0bd1d41b6800df114b0de78e2 - 323 bytes - last - d262ef9ceeb0bfa528fe1c437d50fff6a2b44f4ea27913b58ee8adfcef83519a - 309 bytes - paths - 02ab755cf4e35634068f8e630d3b80feb6c6c7cd94a9f4f1979df53902137d3c - 307 bytes - spawn - ffe88192b07aa4706fa554f0379eb43a8545b63e34ce843e778f76e06de05da2 - 310 bytes - update - 3c5a683e8a0248ead97d90417651d36f1a6029c2387f7cbe386d17c545e3ae0a - 320 bytes - usage - 84dc0a08aadfa26fff47026d2f355d3d3c282a127b36291b9c9a86cc09ef3b85 - 328 bytes - utils - 9cc8946aa76c30dc91e653484d8cd7b0d2f300764f3d351bced43d45f38bc8dc - 311 bytes - view 10 HTA FILE CONTAINED NI THE ABOVE ZIP ARCHIVES: - 1d0e0b21741112b47c0bfa2cb9f50d021533bcdd52c0266c27e7b9f3f1d3bb3d - 1,449 bytes - color-modes.hta - 3038497bdcb87c2eb914d7fa6205426853ebd0aec5e07d515f8166b292077d75 - 2,347 bytes - context.hta - 3eb8be187f160acae79e975d84ccea431b75599feb1795091dabed99b6e415a7 - 1,159 bytes - items.hta - cd1e236c256623cad5deceeff5aeca7ee0be08ff91c40d9d761bd4a19aa1a0f1 - 6,511 bytes - last.hta - 55fcc44b94ba05b3604a5eff0f20e7ee09b5b8ada8f256ade2b36f84e930a36b - 2,387 bytes - paths.hta - cf26d5a0a5441155f10254fb0b709ddf1902a1d5cde85f31ec177c45198e0214 - 4,577 bytes - spawn.hta - c3d2aae9c0b29615047b48a778658352a7f24b59a471a18e01373b399e6e74f8 - 2,283 bytes - update.hta - 3ca4af8ea679d23f64a9937f5fe59b541dc418162e15a8d22217ba7875cad0c1 - 3,073 bytes - usage.hta - 881642854f06d30b4ca1d7facc546f42310f7f12a37260125db3910d711edc40 - 5,811 bytes - utils.hta - 6fa2a0abeabf835a5b7938adb5957479b31f3d542620a33d00f1ee6cbc2fd31d - 4,747 bytes - view.hta 10 EXAMPLES OF URLS GENERATED BY THE ABOVE ZIP ARCHIVES: - hxxps[:]//df8e1e40.interelectrode[.]boats/264qv0qc3le67 - hxxps[:]//622557ff.interelectrode[.]boats/3h130snc3r307 - hxxps[:]//8d2f0347.concretively[.]homes/1h91pepc4b514 - hxxps[:]//201a41d5.interelectrode[.]boats/3ptqnhpc3h8hl - hxxps[:]//ae44e2d0.interelectrode[.]boats/3r85mmcc38lv4 - hxxps[:]//52083f3e.interelectrode[.]boats/7g01pic3bk2v - hxxps[:]//efbed253.interelectrode[.]boats/1ab4pgkc36te4 - hxxps[:]//2ffb9cba.interelectrode[.]boats/2n576mpc3qacp - hxxps[:]//0126c5f0.interelectrode[.]boats/24dokf6c318h4 - hxxps[:]//8e08d435.interelectrode[.]boats/23nl3tmc3ea0l SHARED DIRECTORY OF WEBDAV SERVER HOSTING CAB FILES CONTAINING THE RASPBERRY ROBIN DLL: - \\1p[.]si@ssl\t - Note: The file path and file name frequently change about every 10 to 15 minutes. Four examples: -- \\1p[.]si@ssl\t\w5\ro.2o_ -- \\1p[.]si@ssl\t\5\d.7 -- \\1p[.]si@ssl\t\n8\r.8 -- \\1p[.]si@ssl\t\mm\v~.h9h NOTE: I forgot to save examples of the above .cab files, but I did save three of the extracted 64-bit DLL files: THREE EXAMPLES OF 64-BIT DLL FILES FOR RASPBERRY ROBIN: - d63cc03d18e6e229d284d43cdecc0f61fa67f3189215a5572ff448f87e5a543a - 3,952,640 bytes - dw6e.l2w - bcb2be24eb38c8ded02e1dc4c61991a280997947e19470a25911ea23df8f9f07 - 5,808,128 bytes - i63x.xy5 - 9600509884e48fb6a5529b758f976a9c3f4891c6bfd9e188119bae3339b48a58 - 6,524,928 bytes - o6dc.cx6 POST-INFECTION TRAFFIC: - Various IP addresses over various ports - Tor traffic
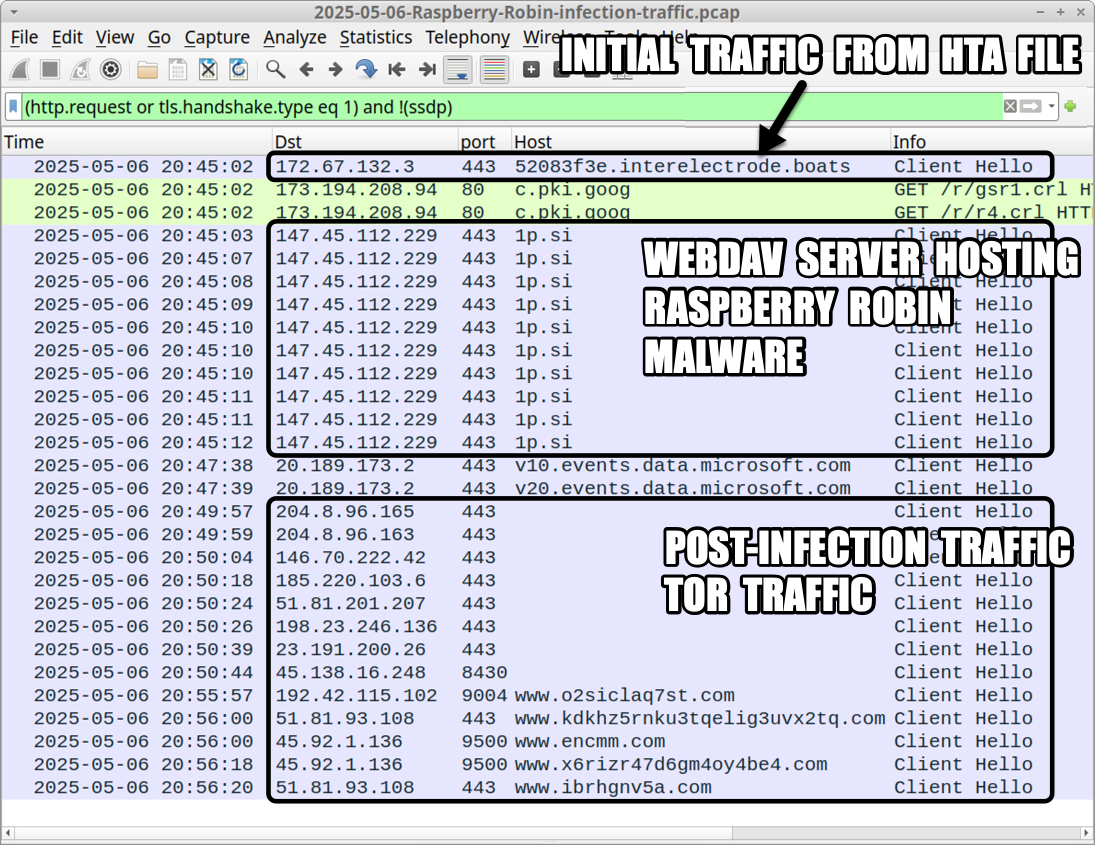
Shown above: Traffic from an infection filtered in Wireshark.
Click here to return to the main page.
