2025-06-13 - TRAFFIC ANALYSIS EXERCISE: IT'S A TRAP!
ASSOCIATED FILES:
- Zip archive of the pcap: 2025-06-13-traffic-analysis-exercise.pcap.zip 39.3 MB (39,323,449 bytes)
- Zip archive of some forensic analysis: 2025-06-13-traffic-analysis-exercise-forensic-analysis.zip 33.0 MB (32,970,676 bytes)
NOTES:
- Zip files are password-protected. Of note, this site has a new password scheme. For the password, see the "about" page of this website.
This is more a "traffic analysis opportunity" instead of a traffic analysis exercise. I'm just providing the traffic and some forensic analysis.
LAN SEGMENT DETAILS FROM THE PCAP
- LAN segment range: 10.6.13[.]0/24 (10.6.13[.]0 through 10.6.13[.]255)
- Domain: massfriction[.]com
- Active Directory (AD) domain controller: 10.6.13[.]3 - WIN-DQL4WFWJXQ4
- AD environment name: MASSFRICTION
- LAN segment gateway: 10.6.13[.]1
- LAN segment broadcast address: 10.6.13[.]255
If you've followed the tutorials I've linked to elsewhere on this blog, you should be able to answer the following:
- What is the IP address of the infected Windows client?
- What is the mac address of the infected Windows client?
- What is the host name of the infected Windows client?
- What is the user account name from the infected Windows client?
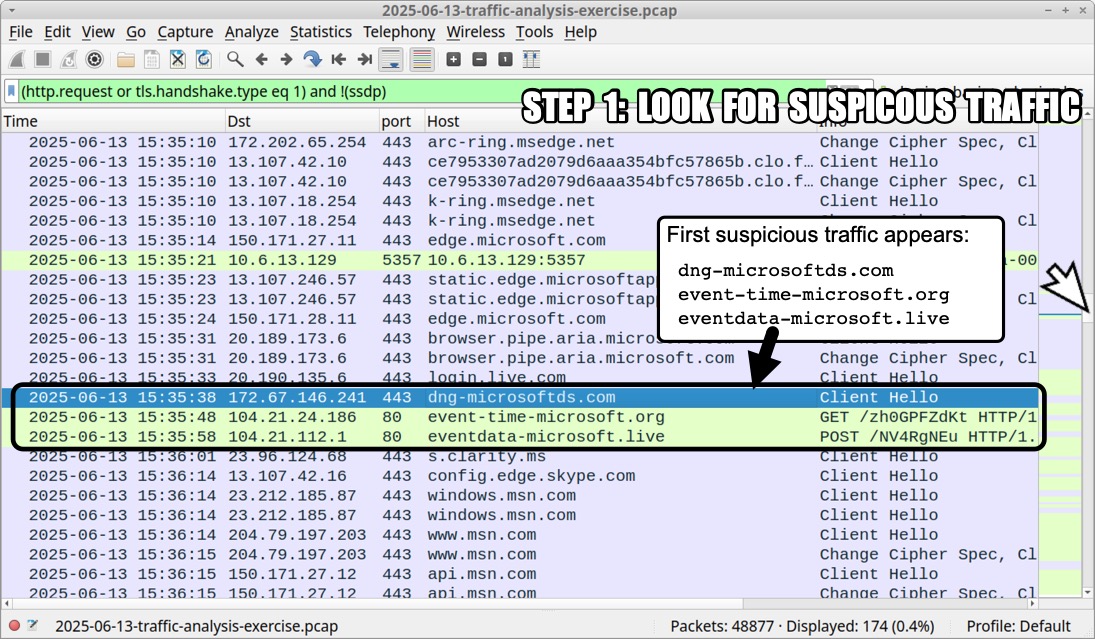
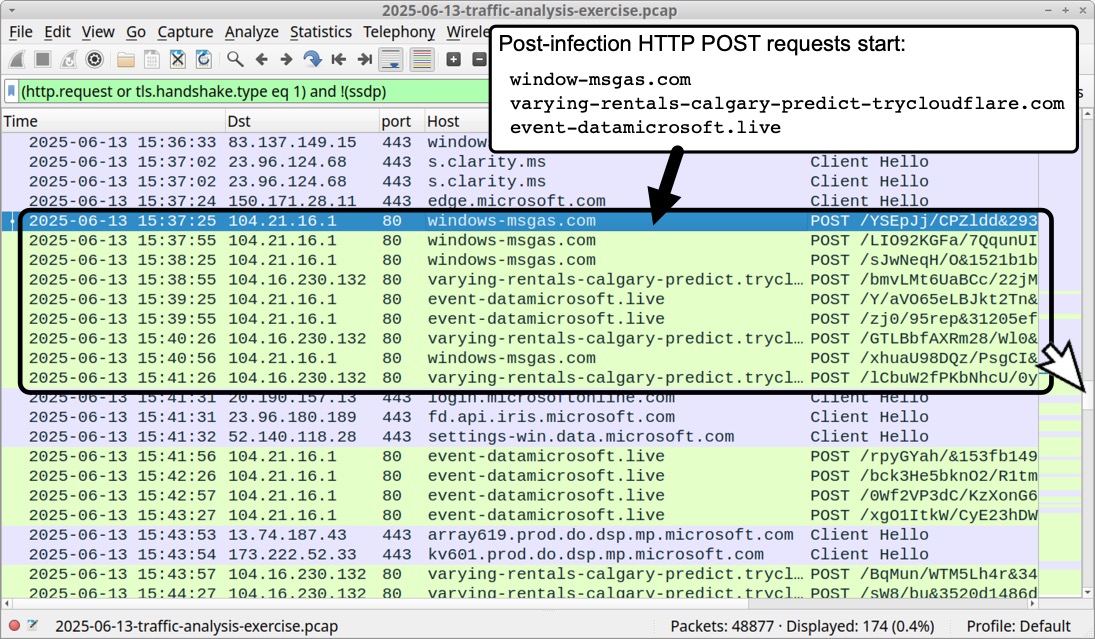
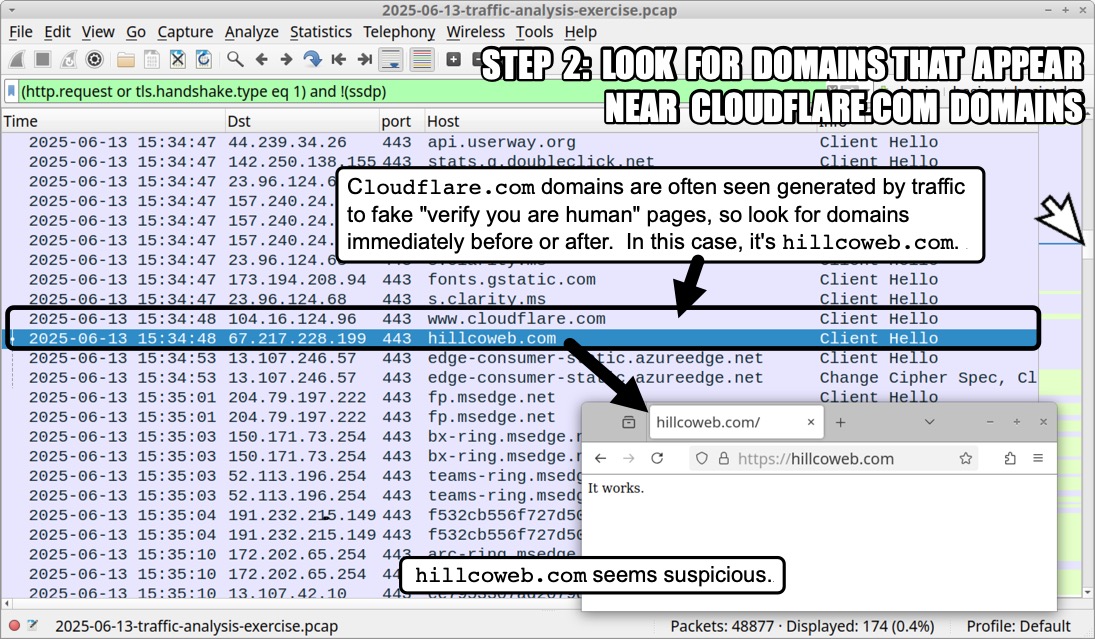
I'm not going to post any answers, so feel free to do what you will with the data. In the meanwhile, the following images illustrate some possible analysis techiques.
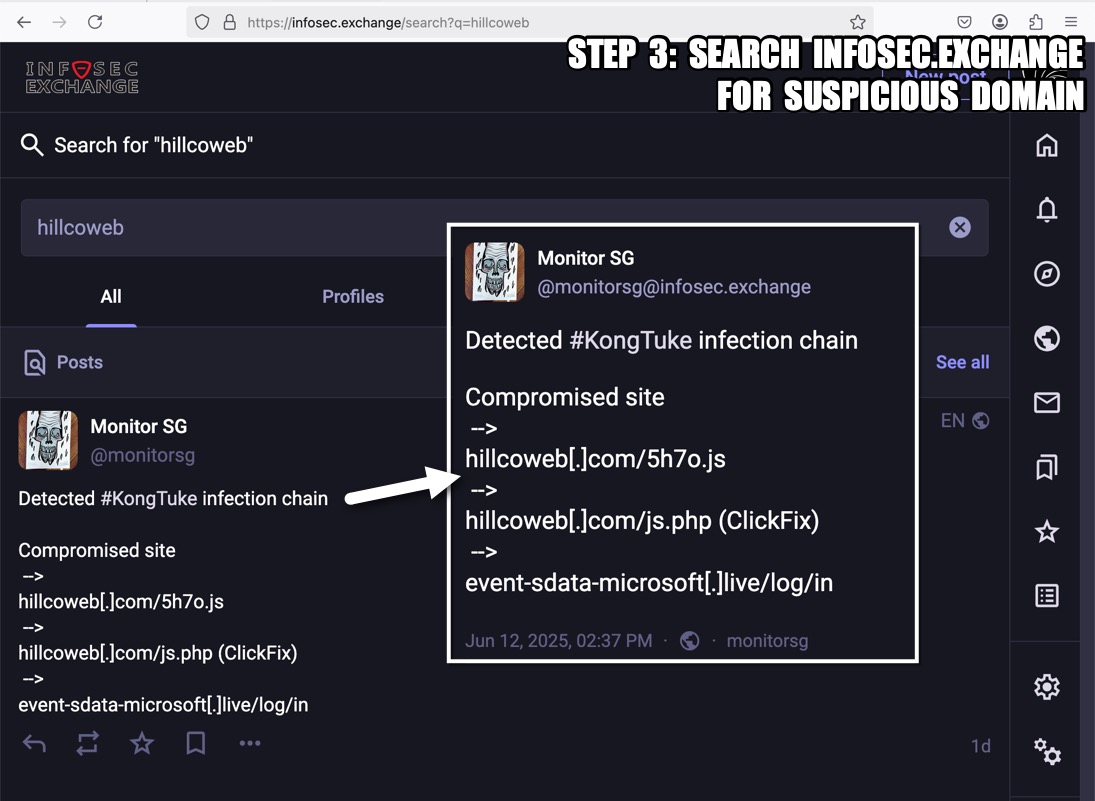
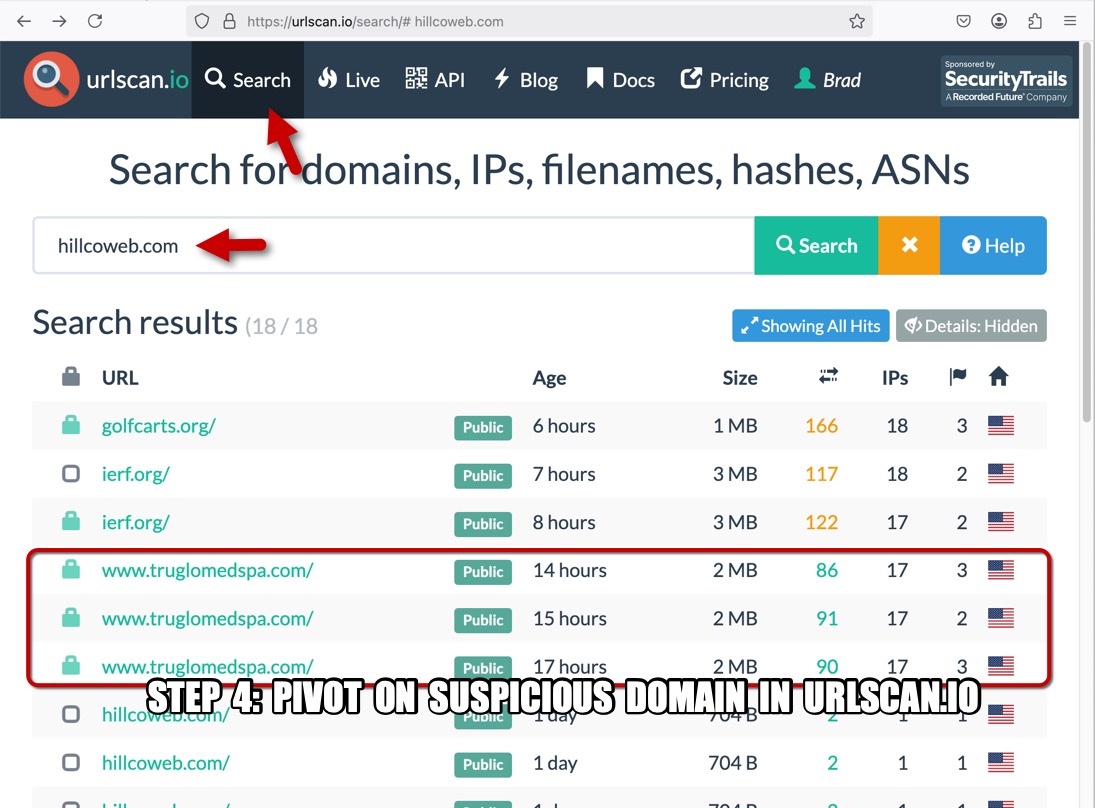
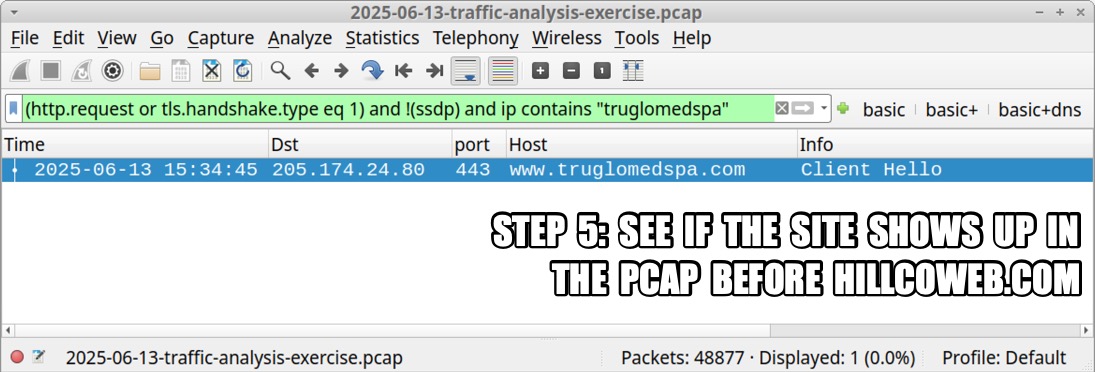
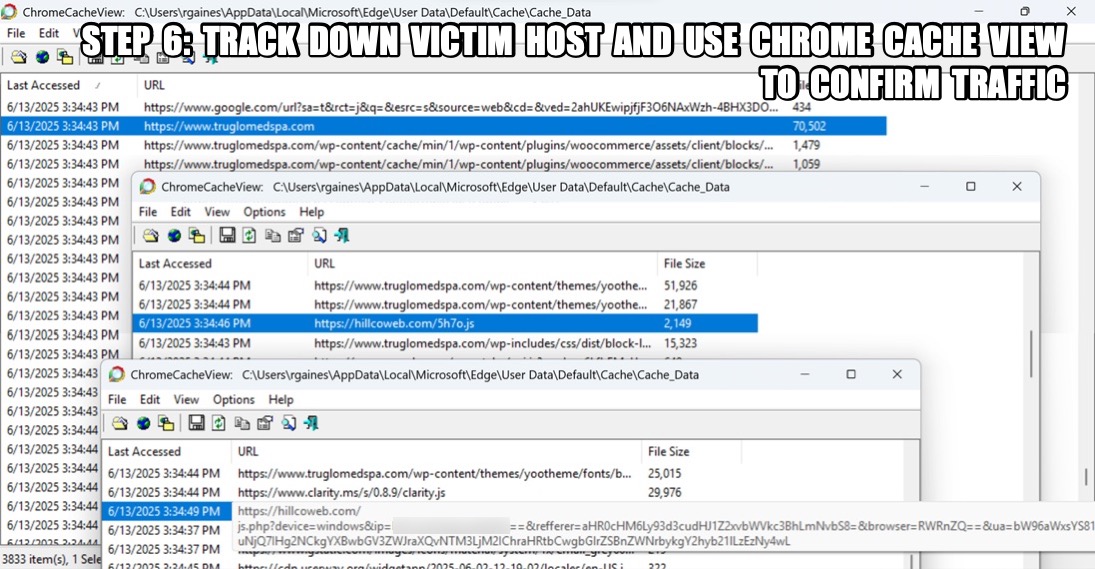
Click here to return to the main page.
