2025-07-02 (WEDNESDAY): LUMMA STEALER INFECTION WITH FOLLOW-UP RSOCKSTUN MALWARE
NOTES:
- Zip files are password-protected. Of note, this site has a new password scheme. For the password, see the "about" page of this website.
ASSOCIATED FILES:
- 2025-07-02-IOCs-from-Lumma-Stealer-with-Rsockstun-malware.txt.zip 2.0 kB (2,025 bytes)
- 2025-07-02-Lumma-Stealer-infection-with-Rsockstun-malware.pcap.zip 9.0 MB (9,046,206 bytes)
- 2025-07-02-malware-and-artifacts-from-the-infection.zip 61.9 MB (61,904,789 bytes)
2025-07-02 (WEDNESDAY): LUMMA STEALER INFECTION WITH RSOCKSTUN MALWARE NOTES: - Thanks to @netresec (https://infosec.exchange/@netresec), who identified the Rsockstun traffic for me. PATH TO LUMMA STEALER DOWNLOAD (TWO DOWNLOADS WITHIN A MINUTE OR TWO OF EACH OTHER): - hxxps[:]//www.facebook[.]com/media/set/?set=a.3164653780507169 - hxxps[:]//urluss[.]com/2wyPix - hxxps[:]//media.cloud839v3[.]cyou/fb+limiter+pro+cracked+full+version.zip - hxxps[:]//arch2.kot3jsd[.]my/bridge/u/lAoEVF3Q00zZLYmbh6o9om5J/fb%20limiter%20pro%20cracked%20full%20version.zip - hxxps[:]//www.facebook[.]com/media/set/?set=a.331497049494729 - hxxps[:]//8diaprinzpistpe.blogspot[.]com/?download=2wEjP9 - hxxps[:]//vittuv[.]com/2wEjP9 - hxxps[:]//media.cloud839v3[.]cyou/4K+Video+Downloader+v6.1.3.2079Setup+Cracks+full+version.zip - hxxps[:]//arch2.kot3jsd[.]my/bridge/u/loD59okQBxMndtxaeGW22GoK/4K%20Video%20Downloader%20v6.1.3.2079Setup%20Cracks%20full%20 version.zip DOWNLOADED MALWARE AND FILES FROM AN INFECTION: - SHA256 hash: f200b66b463f3f2113cbb0e2be62c4aec0fe988d6bee303576b85d9be44f45ea - File size: 18,046,739 bytes - File name: 4K Video Downloader v6.1.3.2079Setup Cracks full version.7z - SHA256 hash: 76bc9219d27617d41144139fb2314fef35c696a7fab70081b79fbf1f6d8bac58 - File size: 18,046,691 bytes - File name: fb limiter pro cracked full version.7z - File type: 7-zip archive data, version 0.4 - File description: downloaded, password-protected 7-Zip archives - Password for both archives: 8290 - SHA256 hash: 19745b9b67501a6779922cb746c106a5a7832ccc04167c98b068294f81b7a7ae - File size: 964,795,414 bytes - File name: 4k video downloader v6.1.3.2079setup cracks full version.exe - File name: fb limiter pro cracked full version.exe - File type: PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive - File description: Extracted Windows .exe files to install Lumma Stealer - SHA256 hash: e59f75caa14a428c035bd8e0ecf5d66d4c34ad1801060ece6690bcac1ea35590 - File size: 488,603 bytes - File location: C:\Users\[username]\AppData\Local\Temp\Theology.pot - File type: data - File description: Data binary used as a .cab archive - SHA256 hash: b44aa8efb8857c0b4b93f13efd2c53339810fb1a96507dc44771bf03dc0a1b6e - File size: 27,787 bytes - File location: C:\Users\[username]\AppData\Local\Temp\Johnson.pot - File location: C:\Users\[username]\AppData\Local\Temp\Johnson.pot.bat - File type: ASCII text, with very long lines (1446), with CRLF line terminators - File description: Obfuscated batch (.bat) file used to create AutoIt3.exe and .a3x script for Lumma Stealer - SHA256 hash: 1300262a9d6bb6fcbefc0d299cce194435790e70b9c7b4a651e202e90a32fd49 - File size: 947,288 bytes - File location: C:\Users\[username]\AppData\Local\Temp\437729\Batman.com - File type: PE32 executable (GUI) Intel 80386, for MS Windows - File description: Copy of AutoIt3.exe (beta) created from the .cab file content - SHA256 hash: 16366382c5ac839d541380c9b2ac9876a8020f811885a9e052a650ae4bf544c9 - File size: 487,064 bytes - File location: not found saved to disk (had to create from deobfuscated .bat file) - File type: data - File description: Binary for Lumma Stealer run as .a3x file by copy of AutoIt3.exe LUMMA STEALER C2 TRAFFIC: - 144.172.115[.]212:443 - ponqcf[.]top - TLSv1.3 HTTPS traffic FOLLOW-UP RSOCKSTUN MALWARE (SAME FILE SINCE FRIDAY 2025-06-27): - SHA256 hash: 9dc1872510d70d954662b42c0e3bedb80e719272554efc0051cb727241a6cacb - File size: 8,306,176 bytes - File location: hxxp[:]//86.54.25[.]40/sok.exe - File location: C:\Users\[username]\AppData\Local\Temp\Y9WF3LTVMPJIZV68AL8T53SRM2.exe - File type: PE32+ executable (GUI) x86-64, for MS Windows RSOCKSTUN MALWARE C2 TRAFFIC: - 185.117.90[.]230:16443 - eset-blacklist[.]net - TLSv1.3 traffic
IMAGES
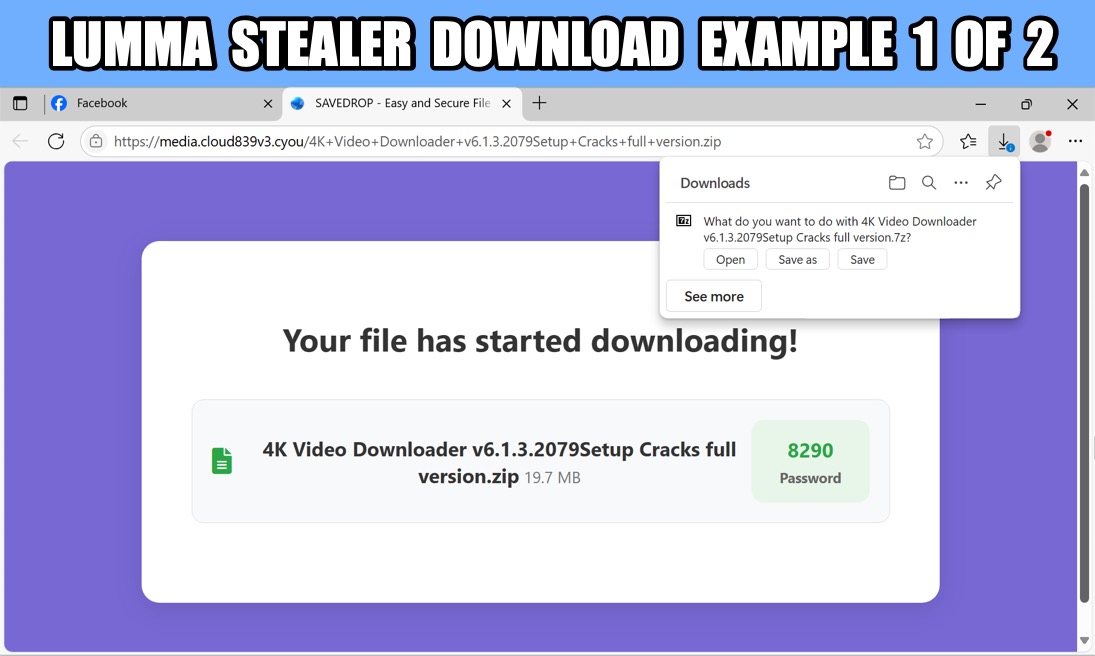
Shown above: Downloaded 7-Zip archive for Lumma Stealer, example 1 of 2.
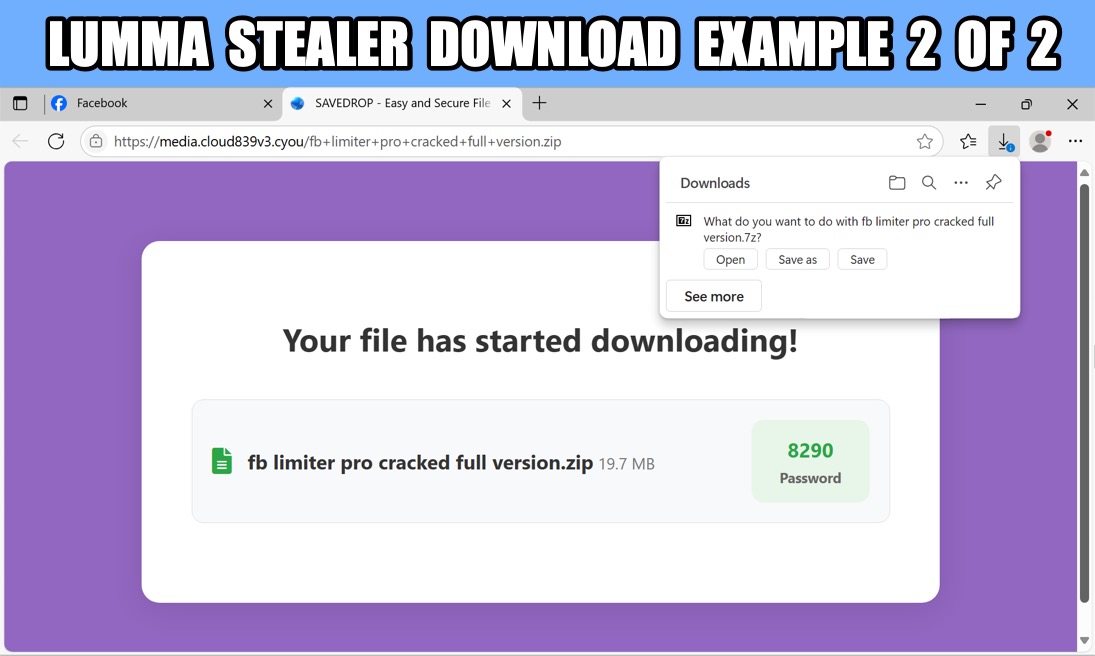
Shown above: Downloaded 7-Zip archive for Lumma Stealer, example 2 of 2.
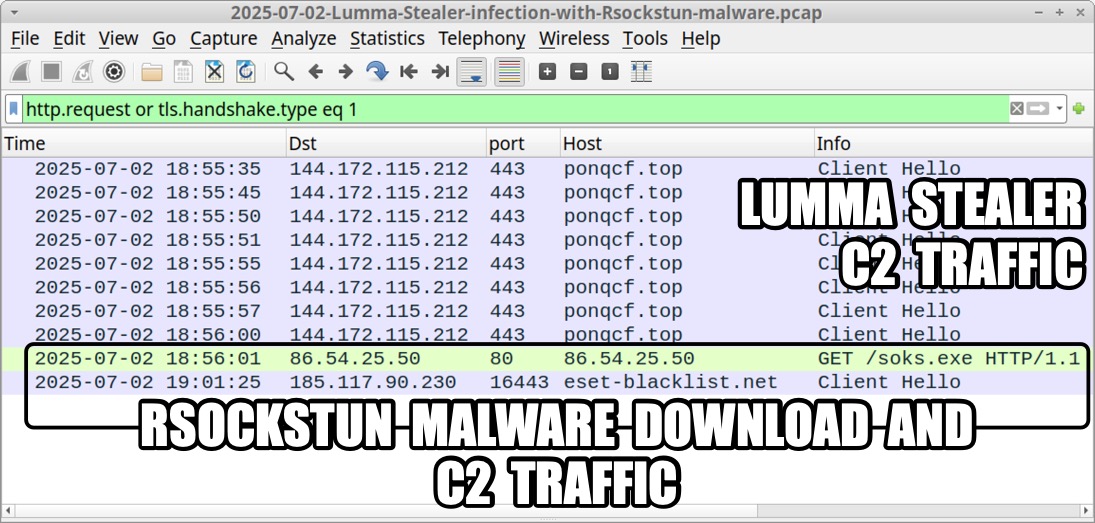
Shown above: Traffic from one of the Lumma Stealer samples, when I ran it in my lab environment.
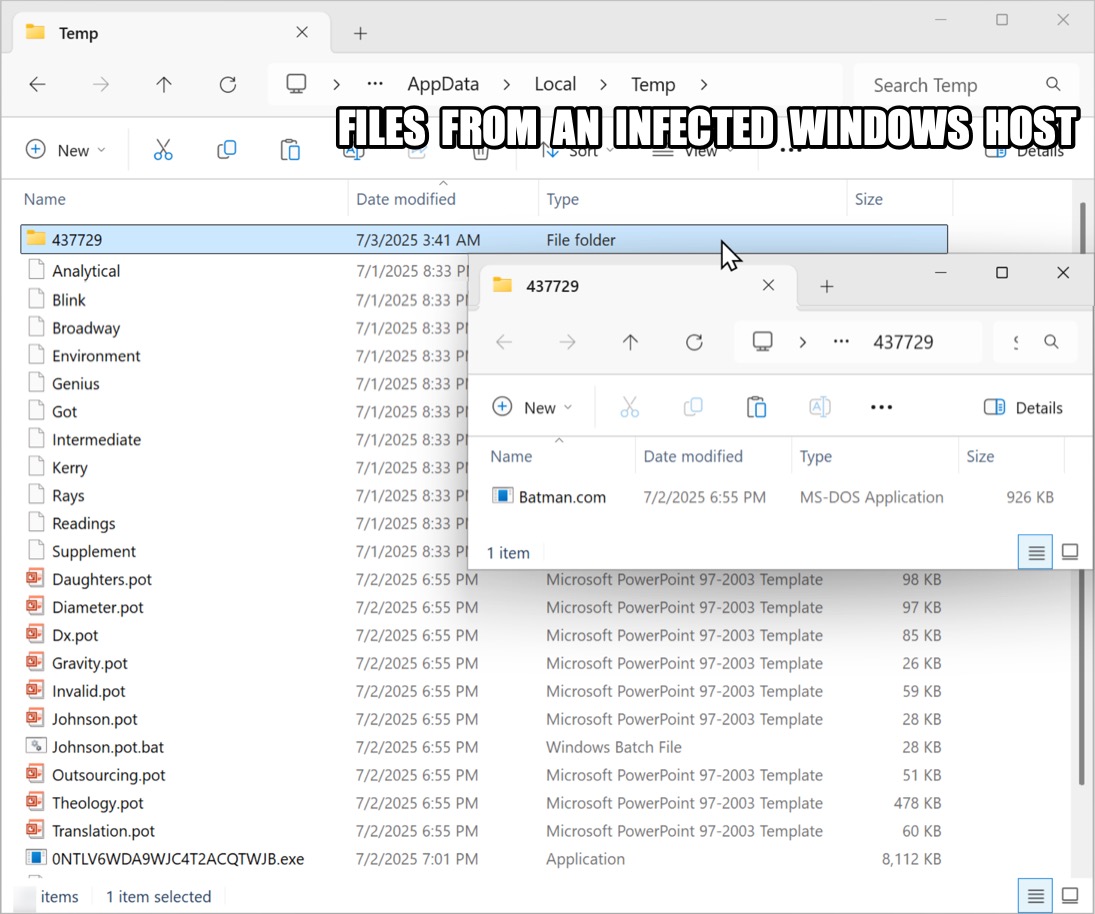
Shown above: Files dropped or saved under a user's AppData\Local\Temp directory on an infected Windows host.
Click here to return to the main page.
