2025-09-24 (WEDNESDAY): LUMMA STEALER INFECTION WITH FOLLOW-UP MALWARE (POSSIBLE GHOSTSOCKS/GO BACKDOOR)
NOTES:
- Zip files are password-protected. Of note, this site has a new password scheme. For the password, see the "about" page of this website.
ASSOCIATED FILES:
- 2025-09-24-IOCs-from-Lumma-Stealer-infection.txt.zip 2.5 kB (2,458 bytes)
- 2025-09-24-traffic-from-running-Setup.exe.pcap.zip 16.2 MB (16,217,604 bytes)
- 2025-09-24-files-from-Lumma-Stealer-infection.zip 46.4 MB (46,353,200 bytes)
IMAGES

Shown above: Initial web page leading to fake software crack.
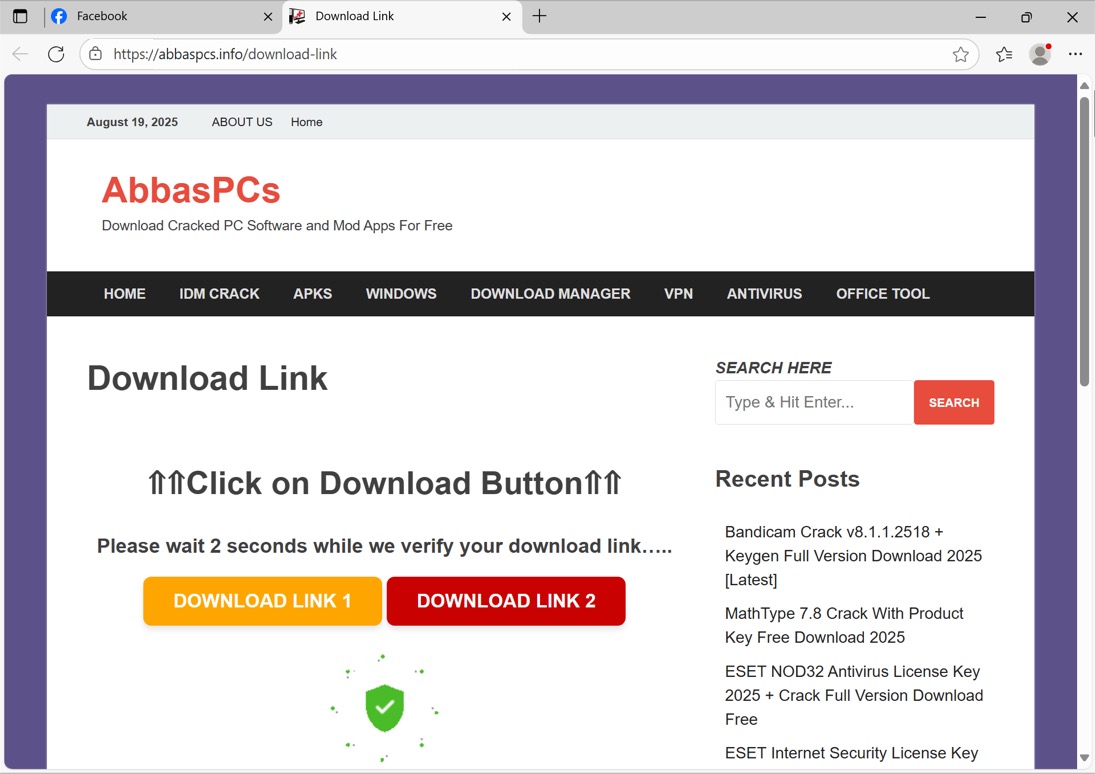
Shown above: Page for fake software crack.
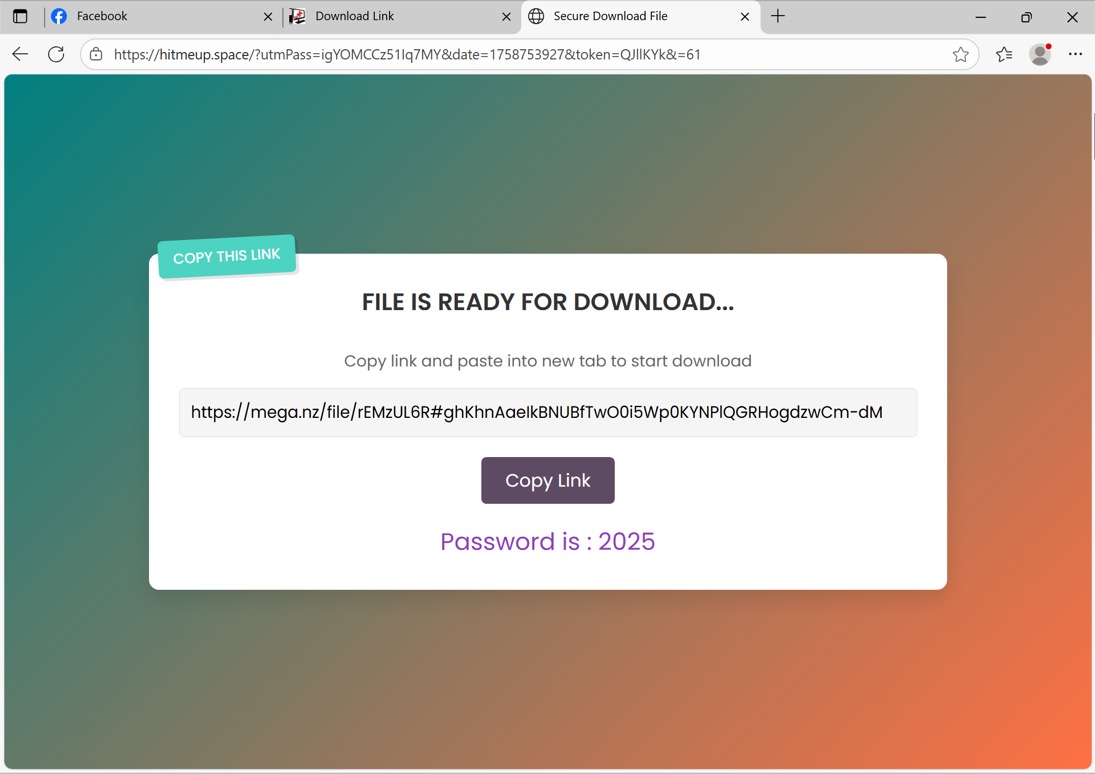
Shown above: Almost there!
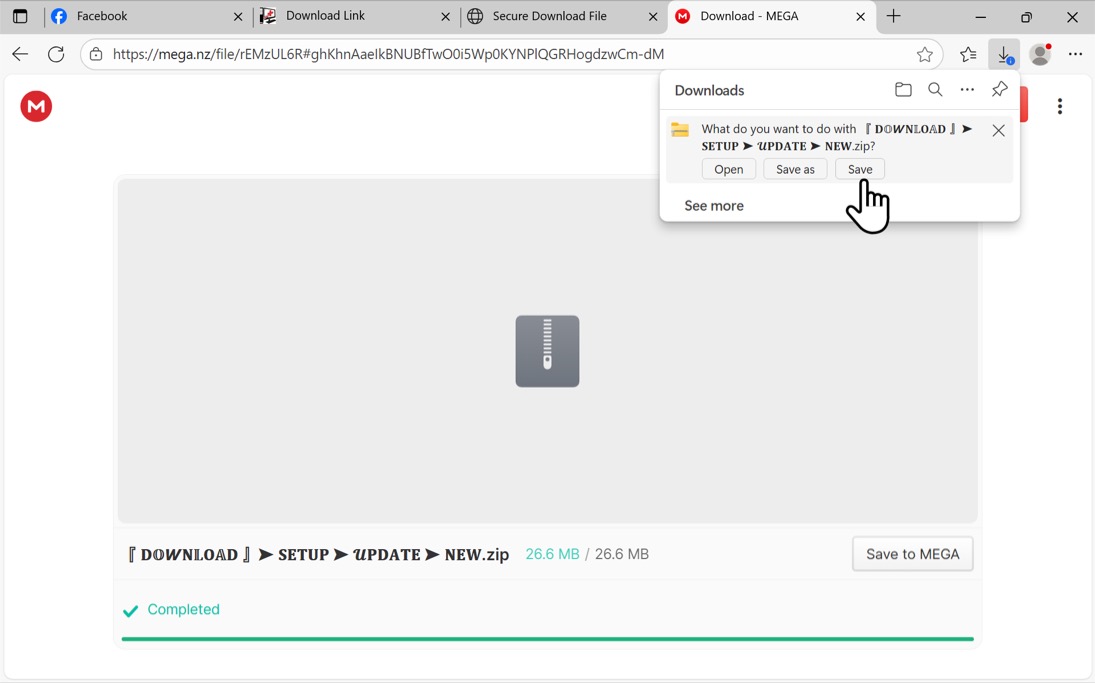
Shown above: Downloading the initial zip archive.
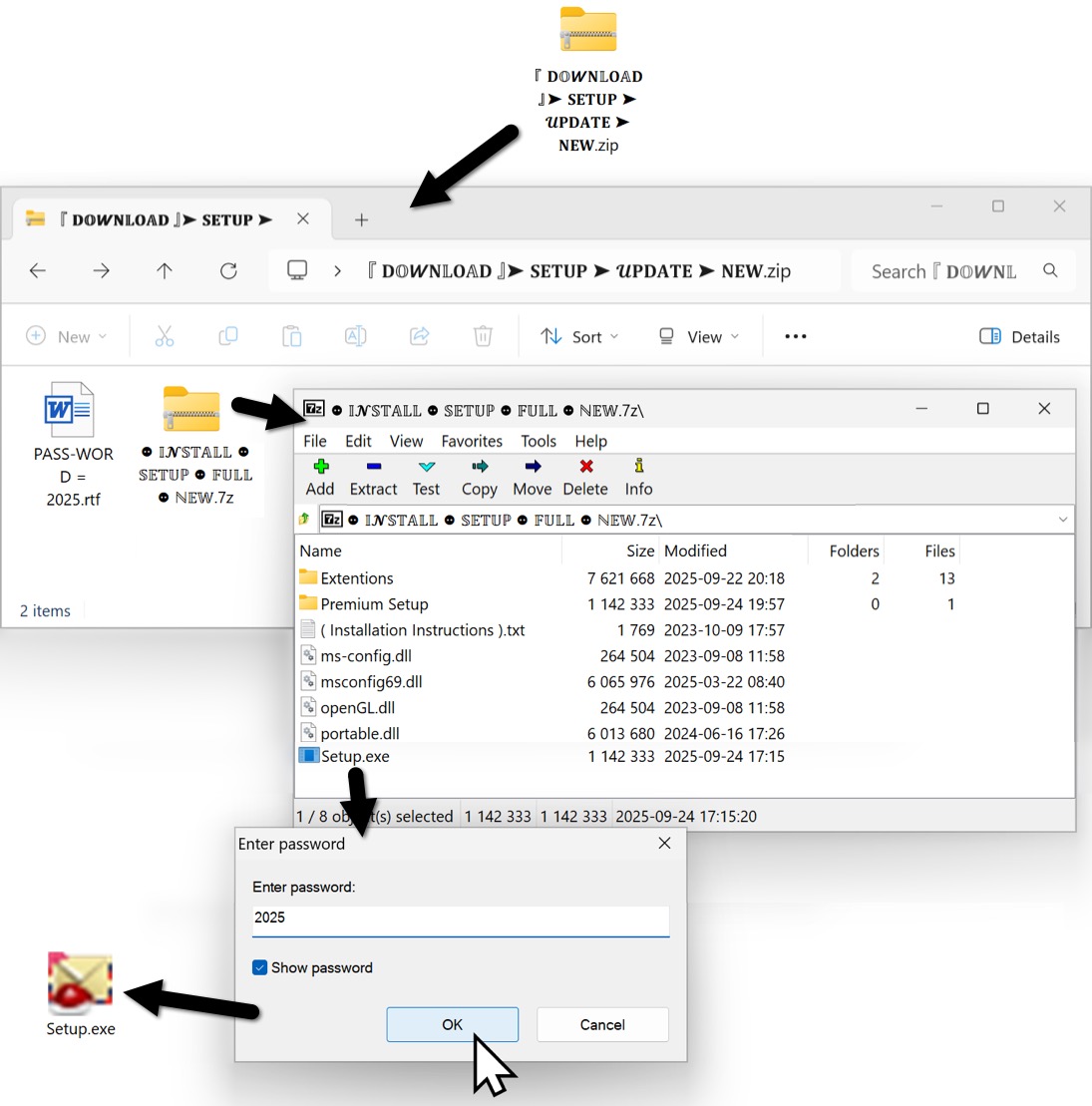
Shown above: Extracting the malware for Lumma Stealer.
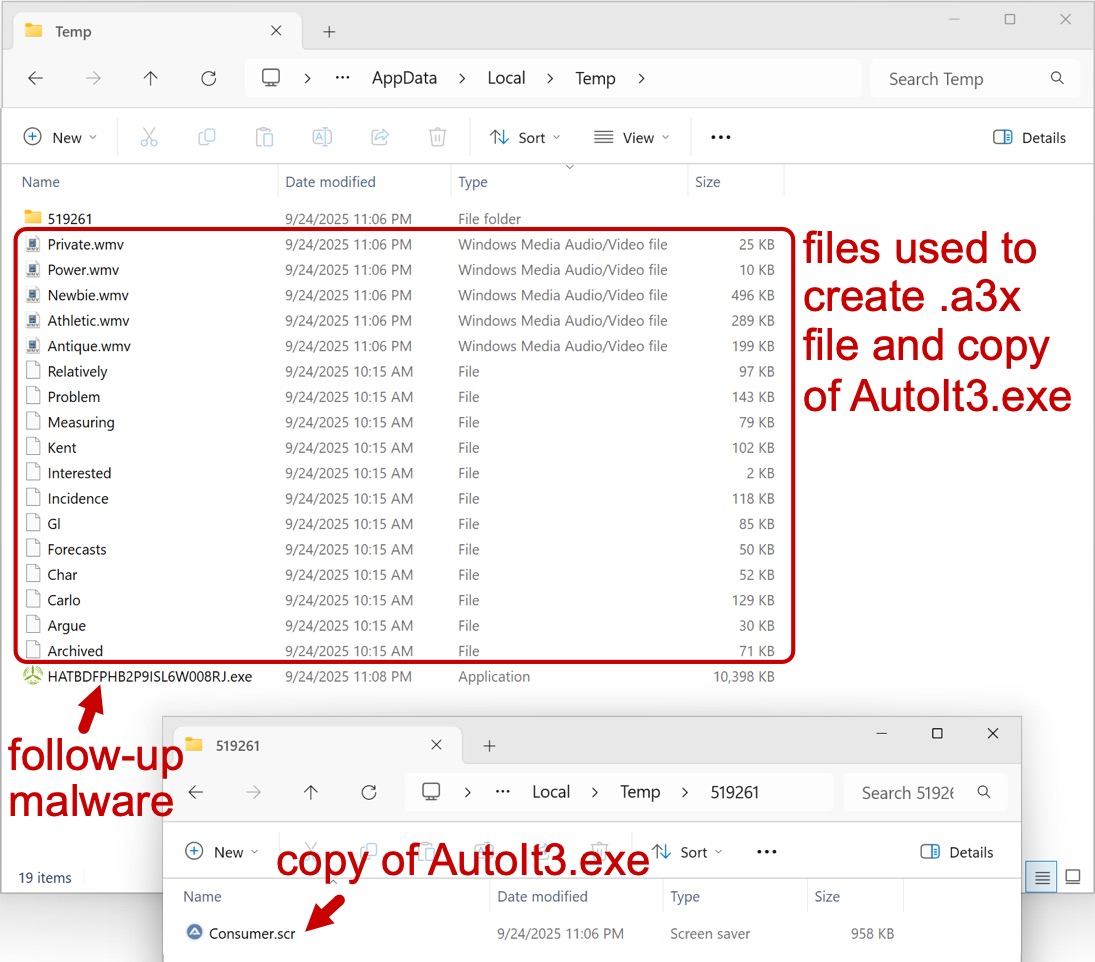
Shown above: Files from an infected Windows host.
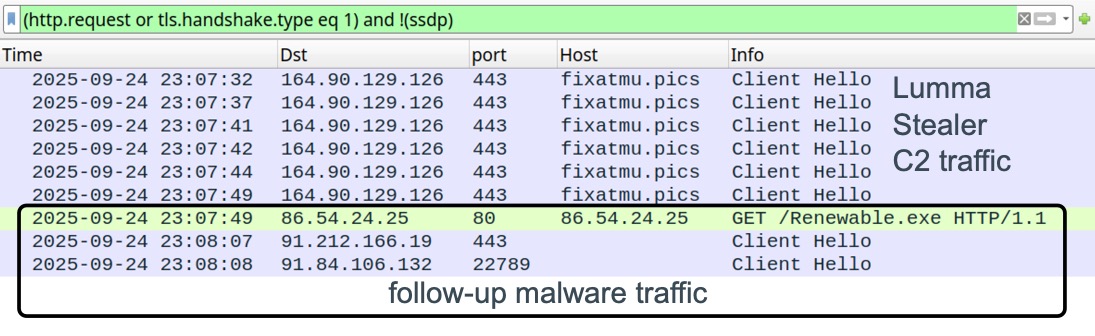
Shown above: Traffic from an infected Windows host.
2025-09-24 (WEDNESDAY): LUMMA STEALER INFECTION WITH FOLLOW-UP MALWARE (POSSIBLE GHOSTSOCKS/GO BACKDOOR) NOTES: - This is an example of Lumma Stealer distributed to people searching for cracked software. - This infection chain misuses the AutoIt scripting language to conceal malicious activity. - Obfuscated batch script, a .cab file, and misleading file extensions also help evade detection. PATH TO INITIAL ZIP ARCHIVE DOWNLOAD: - hxxps[:]//www.facebook[.]com/media/set/?set=a.745017525066326&type=3 - hxxps[:]//abbaspcs[.]info/download-link - hxxps[:]//4bind3[.]cfd/direct99?s=11 - hxxps[:]//hitmeup[.]space/?utmPass=igYOMCCz51Iq7MY&date=1758753927&token=QJllKYk&=61 - hxxps[:]//mega[.]nz/file/rEMzUL6R#ghKhnAaeIkBNUBfTwO0i5Wp0KYNPlQGRHogdzwCm-dM DOWNLOADED MALWARE AND EXTRACTED FILSE: - SHA256 hash: 7833707c8c589b667c5450ad4a66dcb63d5b2bbc727e48b120a7c0d6a93ecff3 - File size: 27,840,159 bytes - File name: 『 𝐃𝕆𝙒𝐍𝕃𝐎𝔸𝐃 』➤ 𝐒𝐄𝐓𝐔𝐏 ➤ 𝓤𝐏𝐃𝐀𝐓𝐄 ➤ 𝐍𝐄𝐖.zip - File type: Zip archive data, at least v2.0 to extract, compression method=deflate - File description: downloaded zip archive - SHA256 hash: 787bd213c2065da67b906716e08c6bada8cda63ce468efb7f5c3b2b5747dfe2d - File size: 4,517,837 bytes - File name: ⚉ 𝕀𝓝𝕊𝕋𝔸𝕃𝕃 ⚉ 𝕊𝔼𝕋𝕌ℙ ⚉ 𝔽𝕌𝕃𝕃 ⚉ ℕ𝔼𝕎.7z - File type: 7-zip archive data, version 0.4 - File description: One of the files extracted form the above zip archive, a password-protected 7-Zip archive - Password: 2025 - SHA256 hash: 706a49b55ba73d1294bdad8570017230a5c66a0e5d171d6ad20830226c096c50 - File size: 1,142,333 bytes - File name: Setup.exe - File type: PE32 executable (GUI) Intel 80386, for MS Windows - File description: One of the files extracted form the above 7-Zip archive, an EXE for Lumma Stealer LIST OF FILES FROM AN INFECTION: - C:\Users\[username]\AppData\Local\Temp\Antique.wmv - C:\Users\[username]\AppData\Local\Temp\Athletic.wmv - C:\Users\[username]\AppData\Local\Temp\Newbie.wmv - C:\Users\[username]\AppData\Local\Temp\Power.wmv - C:\Users\[username]\AppData\Local\Temp\Private.wmv - C:\Users\[username]\AppData\Local\Temp\Archived - C:\Users\[username]\AppData\Local\Temp\Argue - C:\Users\[username]\AppData\Local\Temp\Carlo - C:\Users\[username]\AppData\Local\Temp\Char - C:\Users\[username]\AppData\Local\Temp\Forecasts - C:\Users\[username]\AppData\Local\Temp\Gl - C:\Users\[username]\AppData\Local\Temp\Incidence - C:\Users\[username]\AppData\Local\Temp\Interested - C:\Users\[username]\AppData\Local\Temp\Kent - C:\Users\[username]\AppData\Local\Temp\Measuring - C:\Users\[username]\AppData\Local\Temp\Problem - C:\Users\[username]\AppData\Local\Temp\Relatively - C:\Users\[username]\AppData\Local\Temp\519261\Consumer.scr - C:\Users\[username]\AppData\Local\Temp\HATBDFPHB2P9ISL6W008RJ.exe FILES FROM AN INFECTION: - SHA256 hash: f01f40dfefb50202d4e83fe14d3dc9ec5eec1f5480702e8783462dfc2bfaa9e8 - File size: 9,953 bytes - File location: C:\Users\[username]\AppData\Local\Temp\Power.wmv - File type: ASCII text, with very long lines (433), with CRLF line terminators - File description: Obfuscated script to create copy of AutoIt3.exe and .a3x file for Lumma Stealer - SHA256 hash: 65194fff5b442e5b04473606feb4a2d9e00582028e4a3c60c4c3bafd2c815698 - File size: 507,824 bytes - File location: C:\Users\[username]\AppData\Local\Temp\Newbie.wmv - File type: data - File description: .cab file with content used to create copy of AutoIt3.exe - SHA256 hash: 3ec9740bedc683021cc3e94e4a33b3a9d3d6f9b9e96b1f04cc6534f551dd58c1 - File size: 980,064 bytes - File location: C:\Users\[username]\AppData\Local\Temp\519261\Consumer.scr - File type: PE32 executable (GUI) Intel 80386, for MS Windows - File description: Copy of AutoIt3.exe created from above .cab file content - SHA256 hash: 323eeece9d4bc731917865e36c47ece6d21a74f79bdc67b11a51eb3339c6ae7a - File size: 524,409 bytes - File type: data - File description: .a3x file for Lumma Stealer created by the installer - Sandbox analysis: https://app.any.run/tasks/2315f695-ab53-482e-94a6-9a24fd50f682 - SHA256 hash: f9716135b3eb5b91e697cb02fda30a5c1d0de0867382d9f5b99ac576d9bacf48 - File size: 10,647,040 bytes - File type: PE32 executable (GUI) Intel 80386, for MS Windows - File location: hxxp://86.54.24[.]25/Renewable.exe - File location: C:\Users\[username]\AppData\Local\Temp\HATBDFPHB2P9ISL6W008RJ.exe - File description: Follow-up malware from the infection, possible GhostSocks/Go Backdoor LUMMA STEALER C2 TRFFIC: - 164.90.129[.]126:443 - fixatmu[.]pics - HTTPS traffic (TLSv1.3) C2 TRAFFIC FROM THE FOLLOW-UP MALWARE: - 91.212.166[.]19:443 - HTTPS traffic (TLSv1.3) - 91.84.106[.]132:22789 - HTTPS traffic (TLSv1.3)
Click here to return to the main page.
