2025-10-02 (THURSDAY): ANDROID MALWARE
NOTES:
- Zip files are password-protected. Of note, this site has a new password scheme. For the password, see the "about" page of this website.
REFERENCES:
- https://www.linkedin.com/posts/unit42_phantomcard-activity-7378820202773299200-95tU/
- https://x.com/Unit42_Intel/status/1973054563469951480
- https://github.com/PaloAltoNetworks/Unit42-timely-threat-intel/blob/main/2025-09-25-IOCs-for-NFC-relay-Android-malware.txt
ASSOCIATED FILES:
- 2025-10-02-traffic-from-infected-Android-phone.pcap.zip 22.4 MB (22,419,678 bytes)
NOTES:
- This is a pcap of traffic and images from an Android malware infection based on information from late last month (see the above references for details).
IMAGES
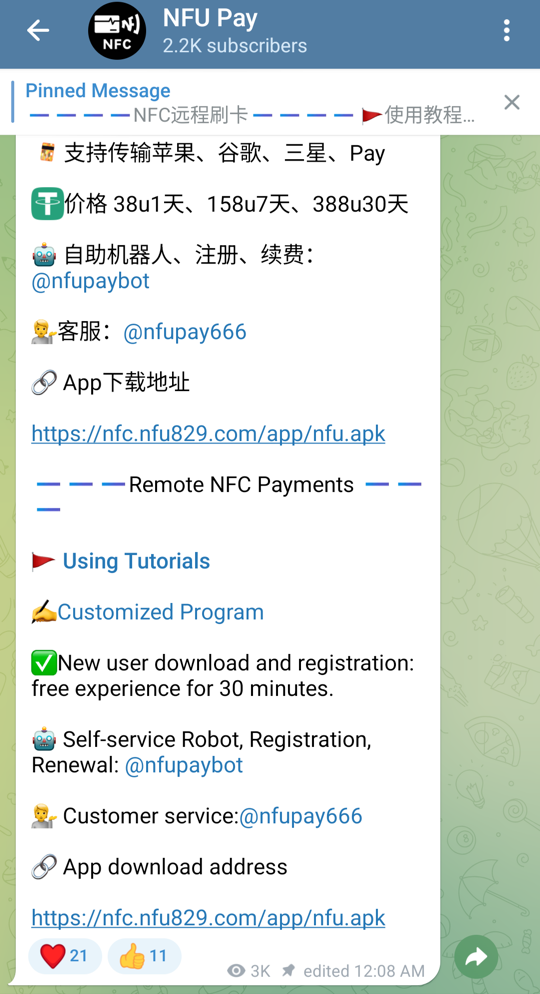
Shown above: Telegram channel where I downloaded the malware from.

Shown above: Screenshot of the app icon in the device's home screen after I downloaded it.
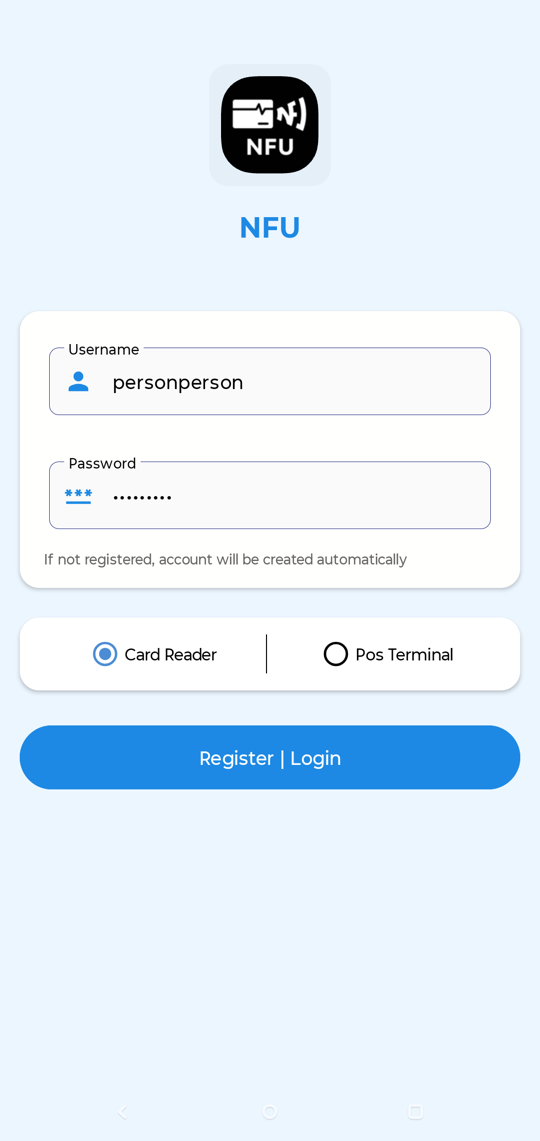
Shown above: Screenshot of the login screen that appears when you first open the app.
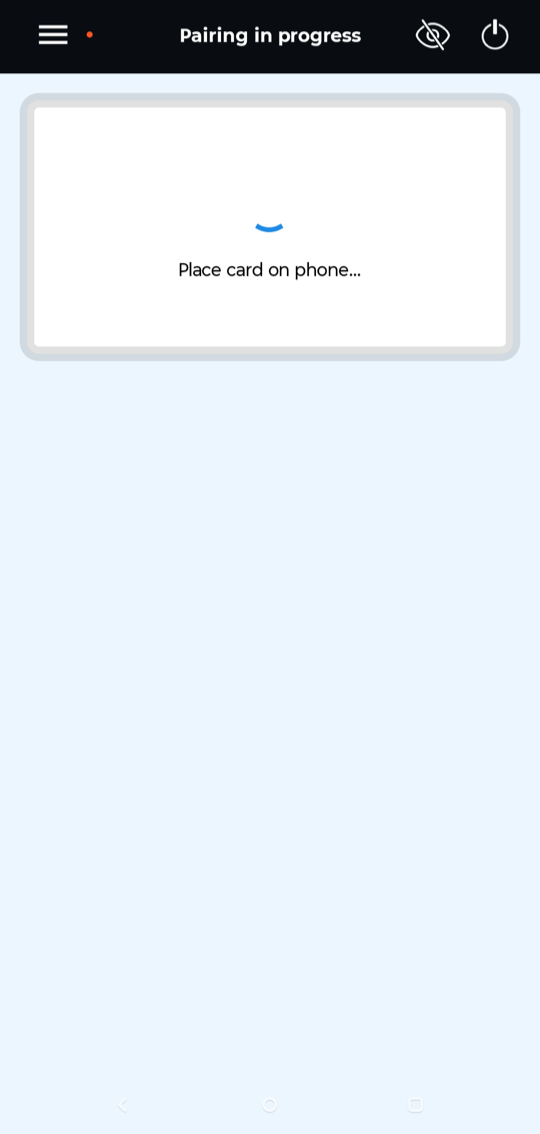
Shown above: Screenshot of the app after I logged in.
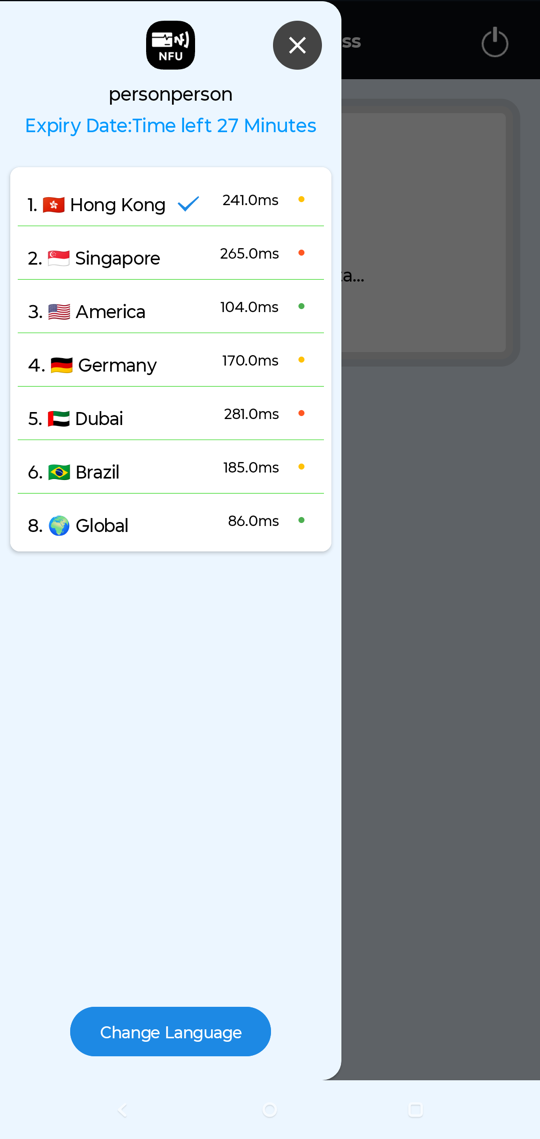
Shown above: I had the choice to change server locations.
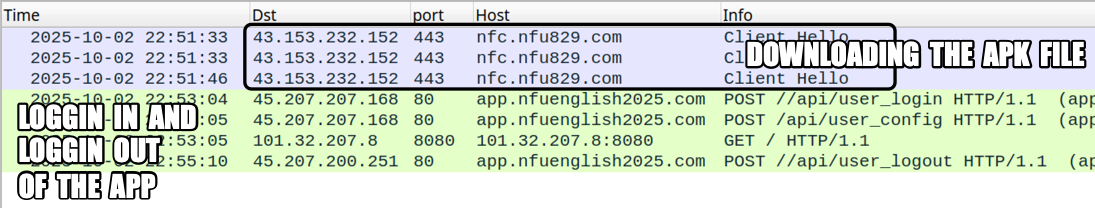
Shown above: Traffic from the Android device when I downloaded, opened, and logged into the malicious app.
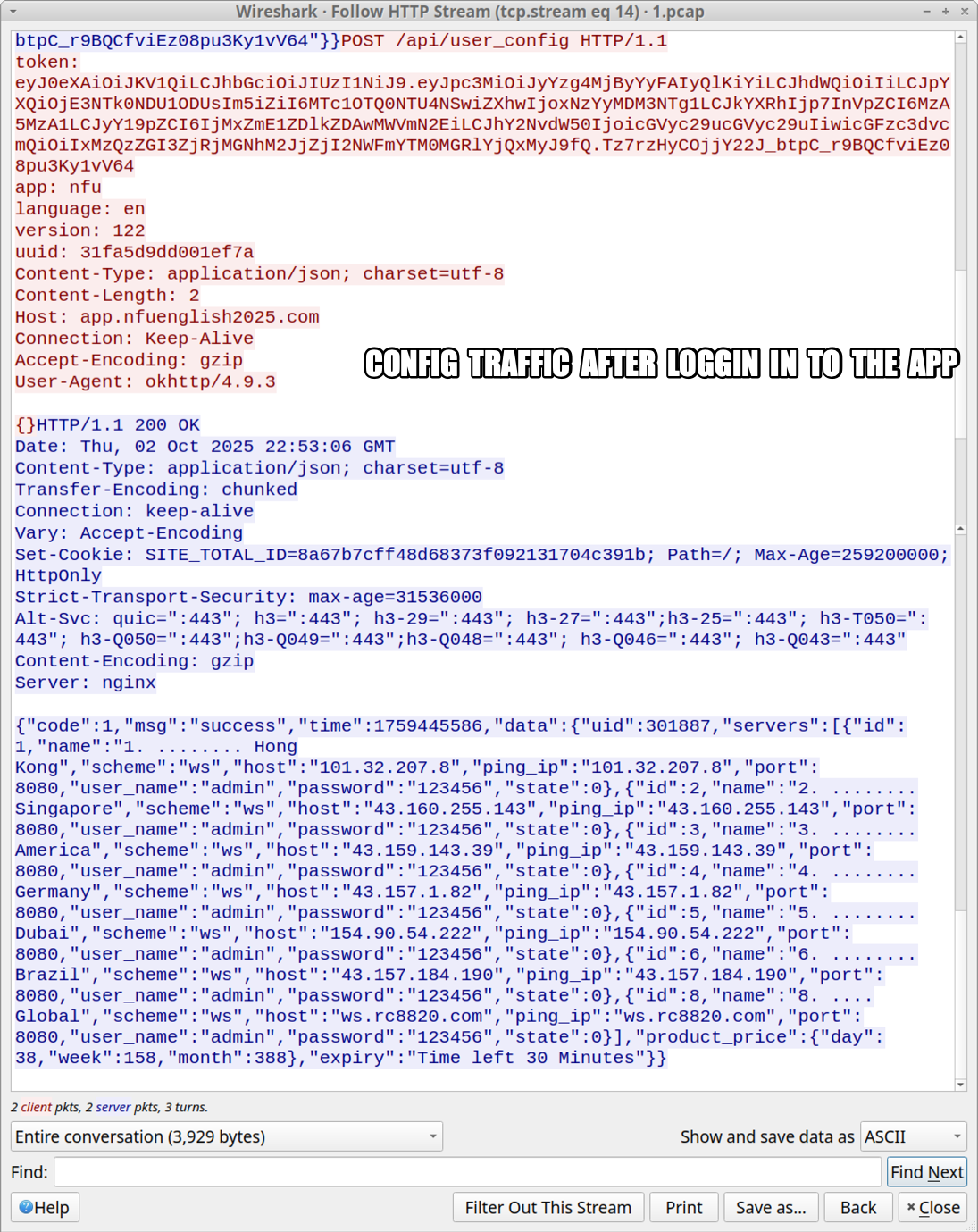
Shown above: TCP stream of configuration traffic after I'd logged into the malicious app.
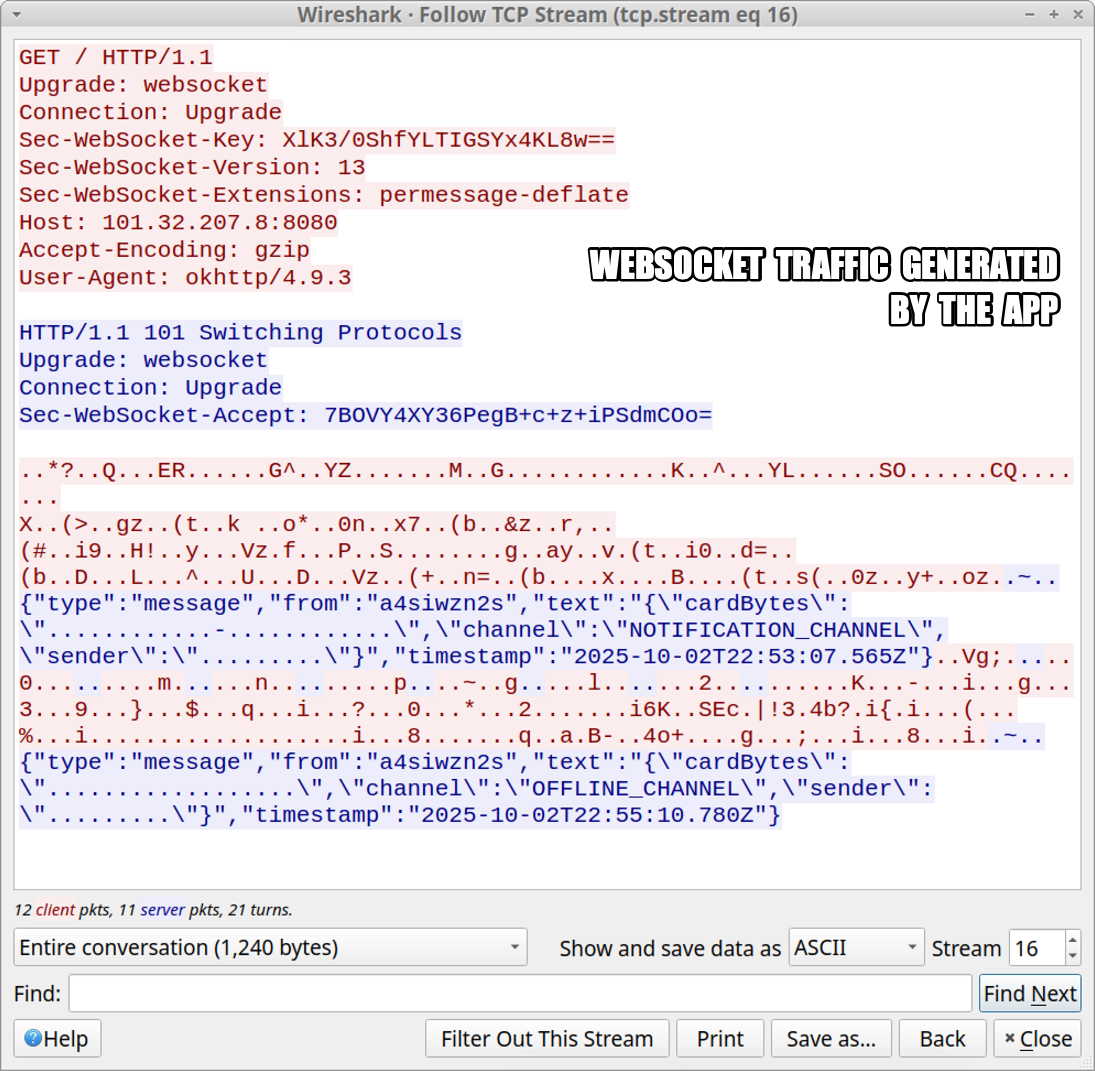
Shown above: TCP stream of websocket traffic generated by the app after logging in.
Click here to return to the main page.
