2025-12-23 (TUESDAY): MACSYNC STEALER INFECTION
ASSOCIATED FILES:
- 2025-12-23-IOCs-for-MacSync-Stealer.txt.zip 1.0 kB (1,030 bytes)
- 2025-12-23-MacSync-Stealer-traffic.pcap.zip 83.4 kB (83,447 bytes)
- 2025-12-23-MacSync-Stealer-malware.zip 31.5 MB (31,547,913 bytes)
REFERENCE:
- From ClickFix to code signed: the quiet shift of MacSync Stealer malware by Jamf Threat Labs
NOTES:
- This post provides a pcap of the infection traffic seen after running the MacSync Stealer malware on a macOS system.
- I modified the pcap to corrupt the exfitrated zip archive from the C2 traffic so it doesn't give away my host info.
- The zkcall[.]net site also has downloads links for Windows malware (DonutLoader) and Linux (link didn't work).
2025-12-23 (TUESDAY): MACSYNC STEALER INFECTION
REFERENCE:
- https://www.jamf.com/blog/macsync-stealer-evolution-code-signed-swift-malware-analysis/
ASSOCIATED MALWARE:
- SHA256 hash: b591bfbab57cc69ce985fbc426002ef00826605257de0547f20ebcfecc3724c2
- File size: 31,476,506 bytes
- File name: zk-call-messenger-installer-3.9.2-lts.dmg
- Retrieved from: hxxps[:]//zkcall[.]net/api/download?fileId=350&versionId=5&os=MACOS_APPLE§ion=/download
- File type: Macintosh Disk Image, lzfse encoded, lzvn compressed
- File description: Downloaded DMG image for MacSync Stealer
- SHA256 hash: 173ff5ede7c28163ceaa9440de8a02cef26295f8be06b6b0f90b0a4284471bc2
- File size: 308,576 bytes
- File name: devupdatesuite-helper
- File type: Mach-O universal binary with 2 architectures: [x86_64:Mach-O 64-bit executable x86_64]
[arm64:Mach-O 64-bit executable arm64]
- File description: Mach-O executable for MacSync Stealer from the installer.app content extracted from the DMG file
TRAFFIC GENERATED BY THE MACH-O BINARY:
- Date/Time of the infection: 2025-12-23 03:52 UTC
- obsidiangate[.]space - HTTPS traffic (TLSv1.3)
- focusgroovy[.]com - GET /dynamic?txd=985683bd660c0c47c6be513a2d1f0a554d52d241714bb17fb18ab0d0f8cc2dc6
- focusgroovy[.]com - POST /gate
IMAGES

Shown above: Downloading the initial file, a DMG image.
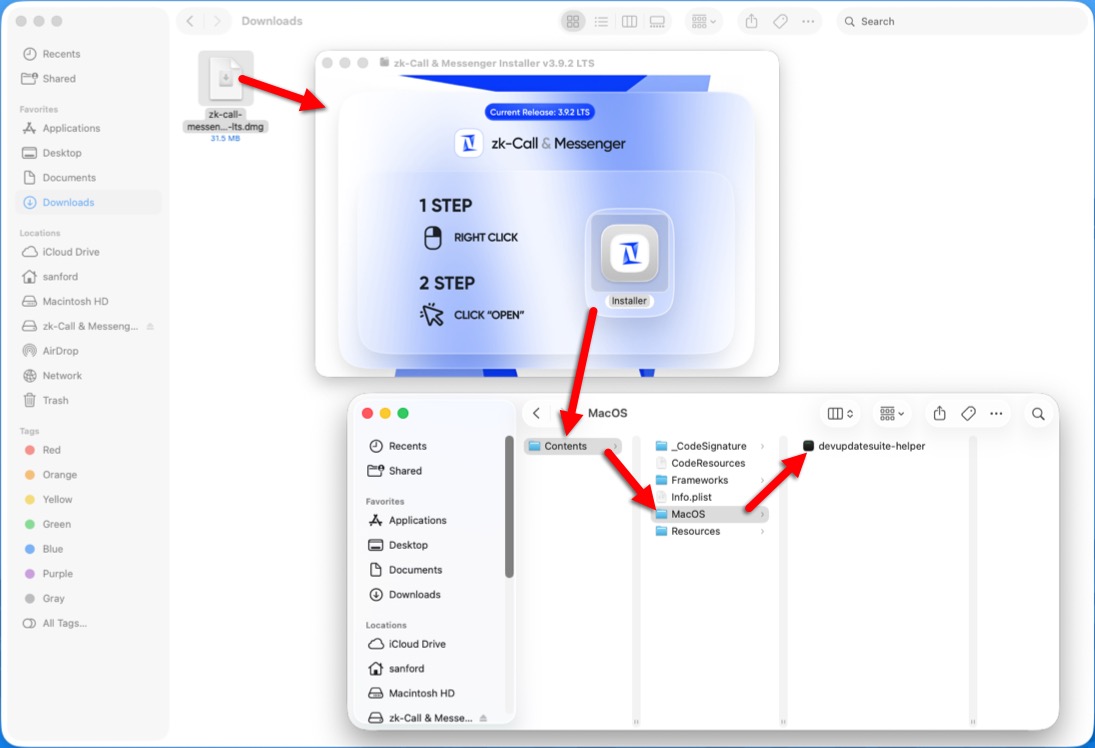
Shown above: From the DMG image to the malicious Mach-O file.
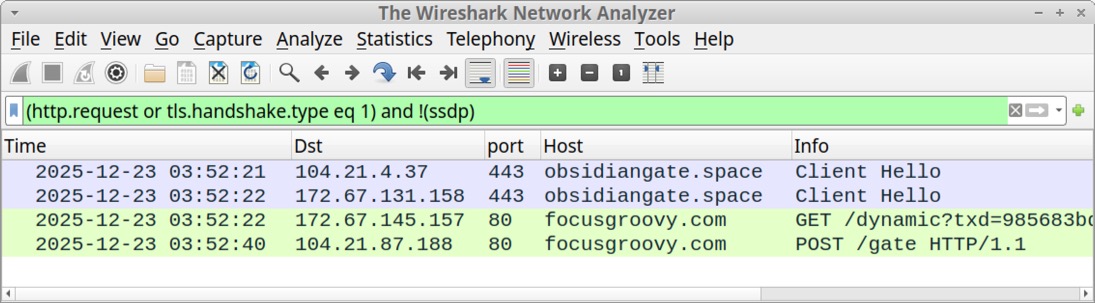
Shown above: Traffic generated by the MacSync Stealer malware.
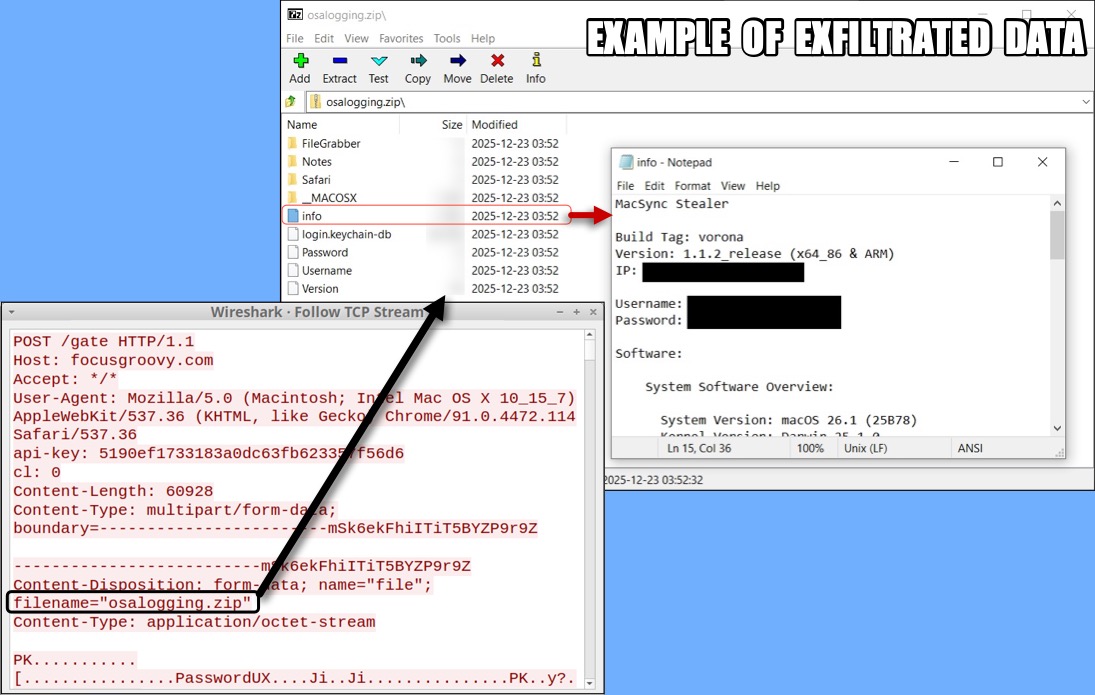
Shown above: Example of data exfiltrated through network traffic generated by the MacSync Stealer sample.
Click here to return to the main page.
