2014-05-19 - FLASHPACK EK FROM 95.154.246[.]90 - LEY9NBU9C4C5R3OIE3819IT.NS1.BAYANDOVMECI[.]COM
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- More Operation Windigo with Cdorked/Onimiki redirection landing to Glupteba.
- The Java exploit is at least 2 weeks old, and the Silverlight exploit hasn't been modified since December 2013.
- For some reason, there's no CVE-2014-0322 traffic like we've seen from FlashPack EK previously on 2014-03-29 and 2014-04-03.
- I'm using the same VM configuration (IE 10, Flash 12.0.0.43, Java 7 update 13, Silverlight 5.1.10411), so I'm not sure why the traffic has changed.
PREVIOUS FLASHPACK EK TRAFFIC ON THIS BLOG:
- 2014-03-29 FlashPack EK from 31.31.196[.]12 - bkapaep35cp5h47qef1lpgl.fm.gen[.]tr
- 2014-04-03 FlashPack EK from 78.157.209[.]194 - dqpo63edlc6eurmpd42wbl9.forexforum.gen[.]tr
- 2014-04-12 FlashPack EK from 176.102.37[.]55 - kliftpres[.]com
- 2014-04-13 FlashPack EK from 176.102.37[.]55 - weoikcus[.]org
- 2014-04-17 FlashPack EK from 178.33.85[.]108 - 9iunfi0idsvtxk4ymdgr9j7.gecekiyafetleri.gen[.]tr
- 2014-05-06 FlashPack EK from 89.121.252[.]70 - 5tcq1yyzey8kafdq1nmvqtw.lchhmba[.]com
- 2014-05-11 FlashPack EK from 82.146.41[.]116 - dg9sdgykl.trade-e[.]com
- 2014-05-19 FlashPack EK from 95.154.246[.]90 - ley9nbu9c4c5r3oie3819it.ns1.bayandovmeci[.]com
CHAIN OF EVENTS
COMPROMISED WEBSITE:
- 02:27:26 UTC - 89.46.102[.]34 - hitcric[.]info - GET /
FLASHPACK EK:
- 02:27:28 UTC - 95.154.246[.]90 - ley9nbu9c4c5r3oie3819it.ns1.bayandovmeci[.]com - GET /index.php?s=dmpuc[long string of characters]
- 02:27:28 UTC - 95.154.246[.]90 - ley9nbu9c4c5r3oie3819it.ns1.bayandovmeci[.]com - GET /favicon.ico
- 02:27:29 UTC - 95.154.246[.]90 - ley9nbu9c4c5r3oie3819it529953c1805362f91a2d16b6d071fd5b0.ns1.bayandovmeci[.]com - GET /index2.php
- 02:27:29 UTC - 95.154.246[.]90 - ley9nbu9c4c5r3oie3819it529953c1805362f91a2d16b6d071fd5b0.ns1.bayandovmeci[.]com - GET /favicon.ico
- 02:27:30 UTC - 95.154.246[.]90 - ley9nbu9c4c5r3oie3819it.ns1.bayandovmeci[.]com - GET /tresting/avalonr/allow.php
- 02:27:30 UTC - 95.154.246[.]90 - ley9nbu9c4c5r3oie3819it.ns1.bayandovmeci[.]com - GET /tresting/avalonr/js/pd.php?id=6c6579[long string of characters]
- 02:27:46 UTC - 95.154.246[.]90 - ley9nbu9c4c5r3oie3819it.ns1.bayandovmeci[.]com - POST /tresting/avalonr/json.php
- 02:27:47 UTC - 95.154.246[.]90 - ley9nbu9c4c5r3oie3819it.ns1.bayandovmeci[.]com - GET /tresting/avalonr/msie.php
- 02:27:47 UTC - 95.154.246[.]90 - ley9nbu9c4c5r3oie3819it.ns1.bayandovmeci[.]com - GET /tresting/avalonr/silver.php
- 02:27:47 UTC - 95.154.246[.]90 - ley9nbu9c4c5r3oie3819it.ns1.bayandovmeci[.]com - GET /tresting/avalonr/flash2014.php
- 02:27:47 UTC - 95.154.246[.]90 - ley9nbu9c4c5r3oie3819it.ns1.bayandovmeci[.]com - GET /tresting/avalonr/javadb.php
- 02:27:48 UTC - 95.154.246[.]90 - ley9nbu9c4c5r3oie3819it.ns1.bayandovmeci[.]com - GET /tresting/avalonr/include/add8dc99221ed3fa474c85b43f3262ed.eot
- 02:27:52 UTC - 95.154.246[.]90 - ley9nbu9c4c5r3oie3819it.ns1.bayandovmeci[.]com - GET /tresting/avalonr/include/1f55ea0e76576767cbd3d4e266e5dacf.eot
- 02:27:53 UTC - 95.154.246[.]90 - ley9nbu9c4c5r3oie3819it.ns1.bayandovmeci[.]com - GET /tresting/avalonr/loadsilver.php
- 02:28:07 UTC - 95.154.246[.]90 - ley9nbu9c4c5r3oie3819it.ns1.bayandovmeci[.]com - GET /tresting/avalonr/include/15c0b903a3d1f695e139a4ef3e8b3a1b.jar
- 02:28:07 UTC - 95.154.246[.]90 - ley9nbu9c4c5r3oie3819it.ns1.bayandovmeci[.]com - GET /tresting/avalonr/include/15c0b903a3d1f695e139a4ef3e8b3a1b.jar
- 02:30:17 UTC - 95.154.246[.]90 - ley9nbu9c4c5r3oie3819it.ns1.bayandovmeci[.]com - GET /software.php?05190230760256453
POST-INFECTION TRAFFIC:
- 02:28:05 UTC - 91.121.84[.]116:49105 - GET /stat?uid=100&downlink=1111&uplink=1111&id=00CC7ADD&statpass=bpass&version=20140515&features=30
&guid=fc5fe618-b57d-4366-a8b4-58a66ccab09c&comment=20140515&p=0&s= - 02:28:05 UTC - 91.121.84[.]116:21967 - Glupteba-style callback traffic throughout rest of the pcap file
- 02:29:03 UTC - 173.194.116[.]114 - www.google[.]com - GET /robots.txt
- 02:29:03 UTC - 174.143.144[.]69:25 - GET /
- 02:30:24 UTC - 195.2.253[.]38 - 195.2.253[.]38 - POST /
- 02:33:03 UTC - 173.194.64[.]27:25 - GET /
PRELIMINARY MALWARE ANALYSIS
JAVA EXPLOIT
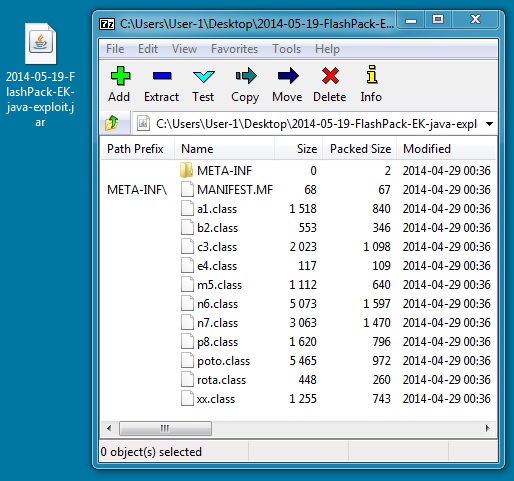
File name: 2014-05-19-FlashPack-EK-java-exploit.jar
File size: 10,408 bytes
MD5 hash: ad97fb241a7f8ec33d36a7735e5693d7
Detection ratio: 14 /53
First submission: 2014-05-06 05:54:17 UTC
VirusTotal link: https://www.virustotal.com/en/file/35e59f62804e8fe688c6536ce0007f7cf8b65dc7924fc6531b6b5d87603664f1/analysis/
SILVERLIGHT EXPLOIT (SENT AS FIRST .EOT FILE)
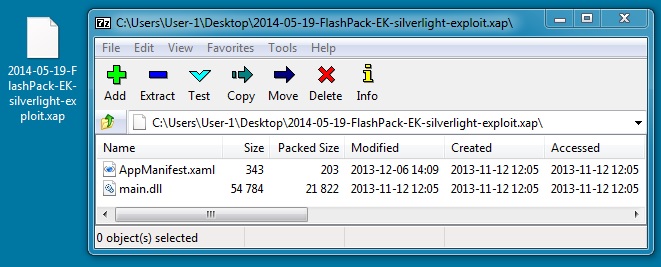
File name: 2014-05-19-FlashPack-EK-silverlight-exploit.xap
File size: 22,319 bytes
MD5 hash: 0fdf64c3cdd5d592fdb357fbba5efeec
Detection ratio: 32 / 52
First submission: 2014-03-13 18:36:49 UTC
VirusTotal link: https://www.virustotal.com/en/file/119fdd3aa3154ce53e8df0dcebfb9469fced6c76c1668cb0d8a1f98106a5ea98/analysis/
FIRST MALWARE FILE NOTED (SENT AS SECOND .EOT FILE)
File name: 2014-05-19-FlashPack-EK-additional-malware.dll
File size: 13,312 bytes
MD5 hash: cf2fa8cc3c623bb73f0c0b5e900caf1b
Detection ratio: 4 / 53
First submission: 2014-05-19 03:28:08 UTC
VirusTotal link: https://www.virustotal.com/en/file/022e6fafdd99615167b44de20a70b21751748f27c4b50e9bc8425dc583f9b5b5/analysis/
MALWARE PAYLOAD
File name: 2014-05-19-FlashPack-EK-malware-payload.exe
File size: 94,514 bytes
MD5 hash: 2c334e13dc255e9681fe6da907b94706
Detection ratio: 6 / 52
First submission: 2014-05-19 03:28:31 UTC
VirusTotal link: https://www.virustotal.com/en/file/6bd17b0439ff1605b420a866d155849d9fb140fe13ce5af9987db146e1518c95/analysis/
POST-INFECTION MALWARE DOWNLOADED
File name: 2014-05-19-FlashPack-EK-post-infection-malware.exe
File size: 136,536 bytes
MD5 hash: f5df5011d612471365edbd104862af6f
Detection ratio: 5 / 53
First submission: 2014-05-19 04:11:31 UTC
VirusTotal link: https://www.virustotal.com/en/file/3d9d1f64b013750aebd7d9395143baaa662dde16c1fde656e8cba8a61ba75307/analysis/
ALERTS
ALERTS FOR THE INFECTION TRAFFIC (from Sguil on Security Onion)
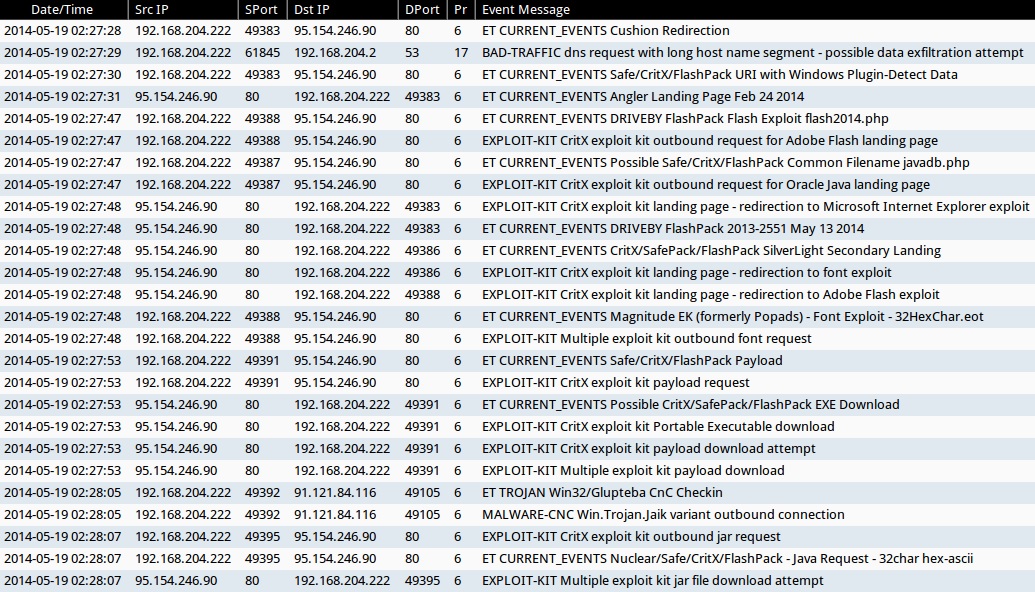
Emerging Threats events:
- ET CURRENT_EVENTS Cushion Redirection (sid:2017552)
- ET CURRENT_EVENTS Safe/CritX/FlashPack URI with Windows Plugin-Detect Data (sid:2017812)
- ET CURRENT_EVENTS Angler Landing Page Feb 24 2014 (sid:2018171)
- ET CURRENT_EVENTS Possible Safe/CritX/FlashPack Common Filename javadb.php (sid:2018238)
- ET CURRENT_EVENTS DRIVEBY FlashPack Flash Exploit flash2014.php (sid:201847)
- ET CURRENT_EVENTS CritX/SafePack/FlashPack SilverLight Secondary Landing (sid:2018236)
- ET CURRENT_EVENTS DRIVEBY FlashPack 2013-2551 May 13 2014 (sid:2018469)
- ET CURRENT_EVENTS Magnitude EK (formerly Popads) - Font Exploit - 32HexChar.eot (sid:2016155)
- ET CURRENT_EVENTS Possible CritX/SafePack/FlashPack EXE Download (sid:2017297)
- ET CURRENT_EVENTS Safe/CritX/FlashPack Payload (sid:2017813)
- ET TROJAN Win32/Glupteba CnC Checkin (sid:2013293)
- ET CURRENT_EVENTS Nuclear/Safe/CritX/FlashPack - Java Request - 32char hex-ascii (sid:2014751)
Sourcefire VRT events:
- BAD-TRAFFIC dns request with long host name segment - possible data exfiltration attempt (sid:30881)
- EXPLOIT-KIT CritX exploit kit outbound request for Adobe Flash landing page (sid:30970)
- EXPLOIT-KIT CritX exploit kit outbound request for Oracle Java landing page (sid:30971)
- EXPLOIT-KIT CritX exploit kit landing page - redirection to Microsoft Internet Explorer exploit (sid:30966)
- EXPLOIT-KIT CritX exploit kit landing page - redirection to Adobe Flash exploit (sid:30967)
- EXPLOIT-KIT CritX exploit kit landing page - redirection to font exploit (sid:30968)
- EXPLOIT-KIT Multiple exploit kit outbound font request (sid:30974)
- EXPLOIT-KIT CritX exploit kit Portable Executable download (sid:24791)
- EXPLOIT-KIT Multiple exploit kit payload download (sid:28593)
- EXPLOIT-KIT CritX exploit kit payload download attempt (sid:29167)
- EXPLOIT-KIT CritX exploit kit payload request (sid:30973)
- MALWARE-CNC Win.Trojan.Jaik variant outbound connection (sid:30977)
- EXPLOIT-KIT Multiple exploit kit jar file download attempt (sid:27816)
- EXPLOIT-KIT CritX exploit kit outbound jar request (sid:29165)
HIGHLIGHTS FROM THE TRAFFIC
Redirect from compromised web server:
The rest of the traffic is similar to my previous blog post on FlashPack EK dated 2014-05-11 (link).
Click here to return to the main page.